#2023蓝桥杯复现
Misc 蚁剑流量 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 z = "c e f l 9 c c e - 4 d a 1 a d 7 5 e - - 5 3 f c } 0 f c 5 4 2 g b - { e 8 0 b e 9 9" order = "10 9 1 2 33 32 39 6 14 38 27 7 25 3 15 20 31 18 24 29 16 23 11 30 42 37 41 36 12 21 34 4 13 19 5 8 26 28 22 35 17 40" char = z.split() print(char) order_list = list(map(int, order.split())) print(list(map(int,order.split()))) char_dict = {} for i in range(len(char)): char_dict[order_list[i]] = char[i] for key in sorted(char_dict.keys()): print(char_dict[key], end=' ') for key in sorted(char_dict.keys()): if char_dict[key] != ' ': print(char_dict[key], end='')
zip
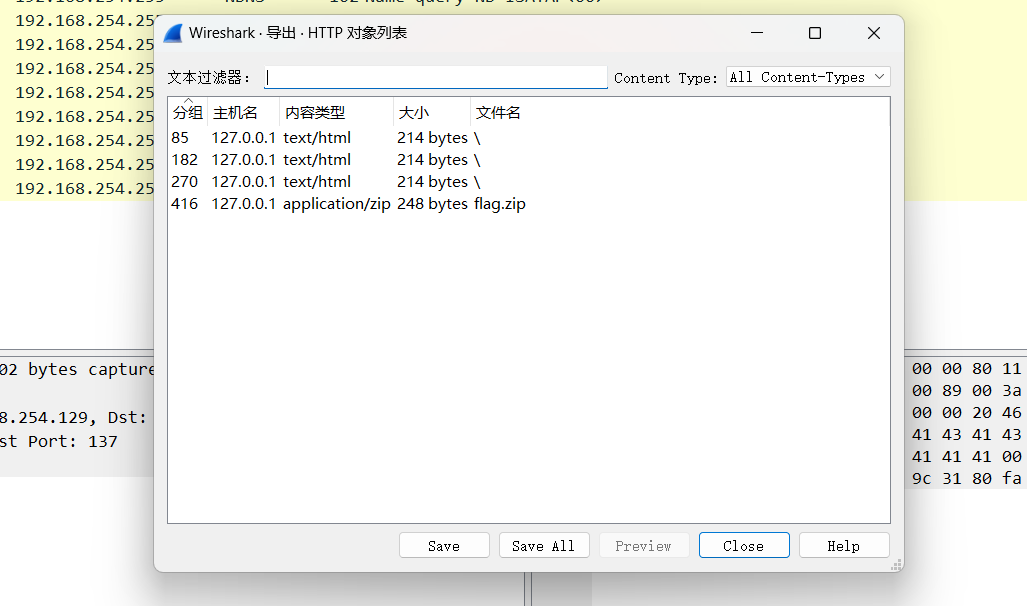
小蓝同学有一个加密的压缩包,里面藏着一些秘密,他把它上传到了一个网站上。但是之后不小心把本地的文件删除了,他想重新下载它,可却再也访问不了那网站。万幸的是,他用wireshark记录了他之前下载压缩包的网络流量,并把它保存下来了。你能帮他从流量中恢复出压缩包吗?
导出一个flag.zip
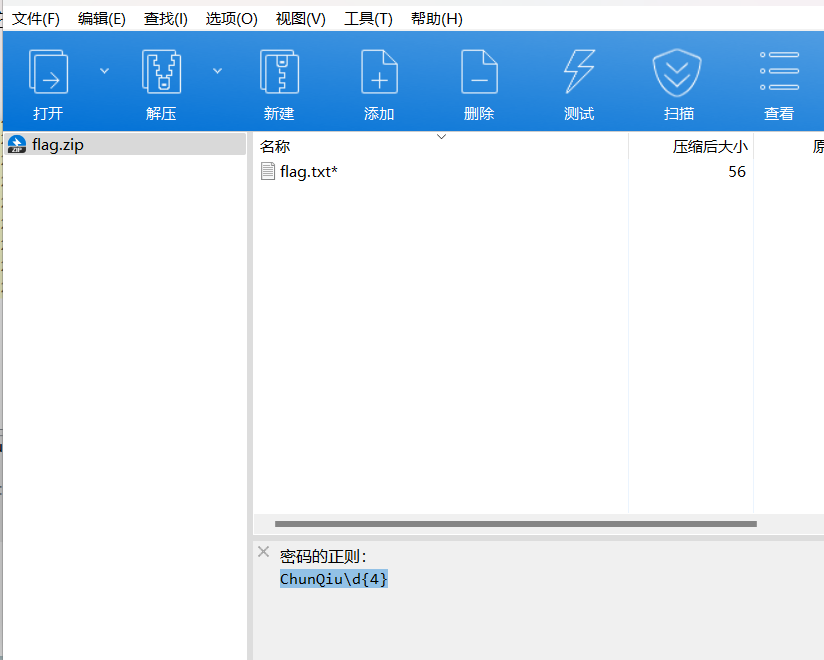
密码的正则:
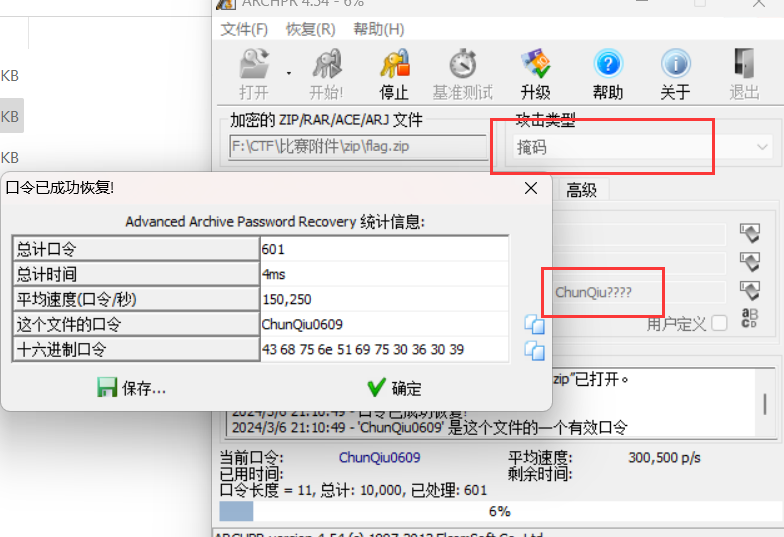
写个脚本爆破
掩码爆破flag{48a4b6f1-7812-417b-9e1f-e17450ef0c43}
CyberChef 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 import base64 base=["DqblD3xoC2M3R2JmCc02RHU1PXU4RHExCqNnCW01QnYcDnCaRdQ1DXh9","ErcmE3ypD2N3S2KnDd02SIV1QYV4SIFyDrOoDX01RoZdEoDbSeR1EYi9""FsdnF3zqE2O3T2LoEe02TJW1RZW4TJGzEsPpEY01SpAeFpEcTfS1FZj9","GteoG3arF2P3U2MpFf02UKX1SAX4UKHaFtQqFZ01TqBfGqFdUgT1GAk9" ,"HufpH3bsG2Q3V2NqGg02VLY1TBY4VLIbGuRrGA01UrCgHrGeVhU1HBl9" ,"IvgqI3ctH2R3W2OrHh02WMZ1UCZ4WMJcHvSsHB01VsDhIsHfWiV1ICm9" ,"JwhrJ3duI2S3X2PsIi02XNA1VDA4XNKdIwTtIC01WtEiJtIgXjW1JDn9" ,"KxisK3evJ2T3Y2QtJj02YOB1WEB4YOLeJxUuJD01XuFjKuJhYkX1KEo9" ,"LyjtL3fwK2U3Z2RuKk02ZPC1XFC4ZPMfKyVvKE01YvGkLvKiZlY1LFp9" ,"MzkuM3gxL2V3A2SvLl02AQD1YGD4AQNgLzWwLF01ZwHlMwLjAmZ1MGq9" ,"NalvN3hyM2W3B2TwMm02BRE1ZHE4BROhMaXxMG01AxImNxMkBnA1NHr9" ,"ObmwO3izN2X3C2UxNn02CSF1AIF4CSPiNbYyNH01ByJnOyNlCoB1OIs9" ,"PcnxP3jaO2Y3D2VyOo02DTG1BJG4DTQjOcZzOI01CzKoPzOmDpC1PJt9" ,"QdoyQ3kbP2Z3E2WzPp02EUH1CKH4EURkPdAaPJ01DaLpQaPnEqD1QKu9" ,"RepzR3lcQ2A3F2XaQq02FVI1DLI4FVSlQeBbQK01EbMqRbQoFrE1RLv9" ,"SfqaS3mdR2B3G2YbRr02GWJ1EMJ4GWTmRfCcRL01FcNrScRpGsF1SMw9" ,"TgrbT3neS2C3H2ZcSs02HXK1FNK4HXUnSgDdSM01GdOsTdSqHtG1TNx9" ,"UhscU3ofT2D3I2AdTt02IYL1GOL4IYVoThEeTN01HePtUeTrIuH1UOy9","VitdV3pgU2E3J2BeUu02JZM1HPM4JZWpUiFfUO01IfQuVfUsJvI1VPz9","WjueW3qhV2F3K2CfVv02KAN1IQN4KAXqVjGgVP01JgRvWgVtKwJ1WQa9","XkvfX3riW2G3L2DgWw02LBO1JRO4LBYrWkHhWQ01KhSwXhWuLxK1XRb9","YlwgY3sjX2H3M2EhXx02MCP1KSP4MCZsXlIiXR01LiTxYiXvMyL1YSc9","ZmxhZ3tkY2I3N2FiYy02NDQ1LTQ4NDAtYmJjYS01MjUyZjYwNzM1ZTd9" ,"AnyiA3ulZ2J3O2GjZz02OER1MUR4OEBuZnKkZT01NkVzAkZxOaN1AUe9","BozjB3vmA2K3P2HkAa02PFS1NVS4PFCvAoLlAU01OlWaBlAyPbO1BVf9"] for text in base: decoded_text = base64.b64decode(text) print(decoded_text)
flag{dcb77abc-6445-4840-bbca-5252f60735e7}
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 #Cyber2 wp from Crypto.Cipher import DES, AES from Crypto.Util.Padding import pad, unpad key_des = b'0a0b0c0d' cipher = bytes.fromhex("416935cabeb8e30cd9b56db3aa6778fa25ad5c3a5105d1c6aad4cba5f109f18afeaf5edcb8fd4e80aca82d75b42d751c40337f08df6c5231140b8c0b947362812df3dd5b5666447043240728a23da1da5cb4c7b197523b960106960cdcb6d48578667aae17caf1cb") #print(cipher) import string import itertools table = string.digits #print(table) for i in itertools.product(table,repeat = 6): x=''.join(i).encode() iv_des = b"01" + x #print(iv_des) decipher_des = DES.new(key_des, DES.MODE_CBC, iv_des) decrypted_text_des = unpad(decipher_des.decrypt(cipher), DES.block_size) #print("DES Decrypted text:", decrypted_text_des) try: tmp1 = bytes.fromhex(decrypted_text_des.decode('utf-8')) except: continue #print(tmp1) key_aes = b'0102030405060708' iv_aes = b'0807060504030201' decipher_aes = AES.new(key_aes, AES.MODE_CBC, iv_aes) decrypted_text_aes = decipher_aes.decrypt(tmp1), AES.block_size flag = decrypted_text_aes[0] #print("AES Decrypted text:", flag) if flag.startswith(b'fla'): print(flag) print(iv_des) else: continue print("end") ''' b'flag{8a860a81-0370-42be-9b7d-78208c5d1f9c}\x06\x06\x06\x06\x06\x06' b'01070309' end '''
通过sqlmap的tamper模块的unmagicquotes.py脚本完成了注入攻击
1 sqlmap.py -u "url" --batch --tamper=unmagicquotes.py -D security -T users -C "username,password" --dump